When running the Ansible playbooks in verbose mode, therefore using the -v, -vv, -vvv, and -vvvv flags, the output from the playbooks can lead to a sensitive information exposure on the controller node.
This is where the no_log attribute comes into play. This attribute prevents Ansible from logging the tasks that handle sensitive data such as passwords, SSH keys, and API tokens.
In this post, we will learn what the ansible_log parameter does and how to use it in an Ansible playbook.
Ansible No_Log Attribute Functionality
In an Ansible playbook, if we set the value of the no_log attribute to true, it ensures that no data from the execution of that task is displayed on the controller node (stdout) or the log files.
Some common uses of this attribute include:
Masking Sensitive Data – When no_log is set to True, the output of that particular task is suppressed which ensures that a potentially sensitive data isn’t exposed.
Overriding Default Behavior – Ansible displays the output for each executed task by default. Using no_log helps override this default behavior for tasks.
Scope – The no_log attribute can be set at the play or task levels, giving us flexibility over which data to hide. If it is set at the play level, it applies to all tasks within that play.
Configure the No_Log Attribute
To use the no_log attribute, we can simply add it to a task or play the definition as demonstrated in the following example:
- name: no log example
hosts: localhost
tasks:
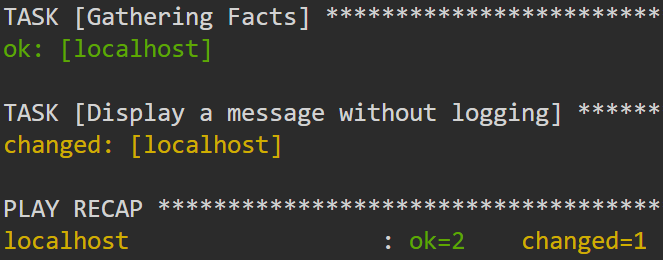
- name: Display a message without logging
command: echo "This won't be logged."
no_log: True
If we run the previous playbook, it should return no message as follows:
Configure No_Log with Variables
When working with variables, especially those that carry sensitive data, we might want to suppress their output as demonstrated in the following example:
- name: With variables
hosts: localhost
vars:
secret_password: "P@ssw0rd123"
tasks:
- name: A task that uses a secret variable
command: "create_user --password {{ secret_password }}"
no_log: True
If we run the previous playbook, we should get an output as follows:
Configure No_Log at Play
We can also set the no_log for an entire play as demonstrated in the following:
- name: no log the entire play
hosts: localhost
no_log: True
tasks:
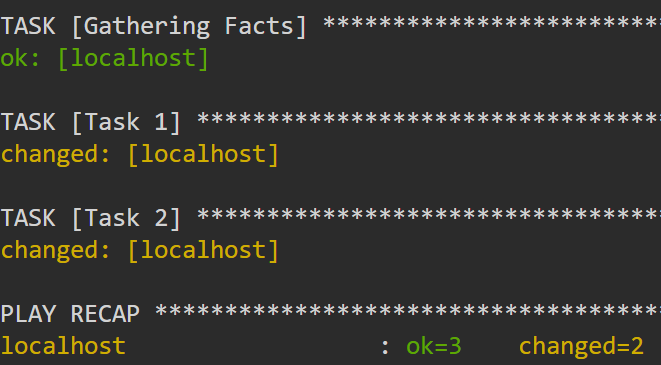
- name: Task 1
command: echo "This task's output will not be logged."
- name: Task 2
command: echo "Neither will this one's."
As you can guess, the previous output does not return any output:
Although the no_log parameter helps hide a sensitive information, it can become a hindrance when dealing with logging.
Similarly, it is good to remember that you can’t globally set the no_log across all playbooks or roles. Hence, you must define it in each play or task as needed.
Conclusion
You learned how to use Ansible’s no_log attribute to ensure the privacy and confidentiality of data during playbook execution.