Types of Tables in iptables
A table is a collection of chains that performs a specific task. The NAT, Filter, and Mangle tables are the three main tables of iptables:
The NAT table is utilized for redirecting connections to other network interfaces.
The Filter table is the default filter used in iptables, which manages the packet flow from and to a system. It is also in charge of permitting and blocking the connections.
The Mangle table is used for changing the packets headers.
Types of Chains in iptables
Each of the iptables contains specific chains comprising a set of rules that are executed in a specific order. In iptables, we have five primary chains:
- Input: This chain handles incoming connections and packets to a protocol or service.
- Output: After a packet has been processed or processed, it is added to the output chain.
- Prerouting: When the packet enters the interface of your network, it is pre routed through the prerouting chain.
- Forward: This chain forwards is responsible for routing, or we can say that it forwards the incoming packets from their source to the destination.
- Postrouting: The routing decision is made before a packet leaves the network interface and is added to the post-routing chain.
Iptables is widely used to refer to kernel-level components. The kernel module that comprises the shared code section is known as x_tables. All four modules (eb, arp, v6, and v4) utilize this kernel module. It is also utilized for referring to the full firewall architecture.
Iptables are installed in the “usr/sbin/iptables” files in most Linux-based systems. It can also be located in “/sbin/iptables”. However, iptables also works as a service. That’s why “/usr/sbin” is the preferred location for it.
Now, we will demonstrate how you can configure iptables on CentOS. Before that, install iptables if you do not have it already on your system.
How to install iptables on CentOS
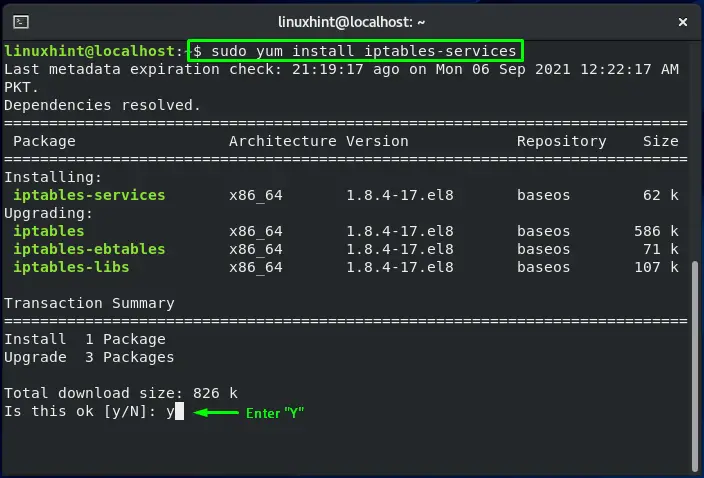
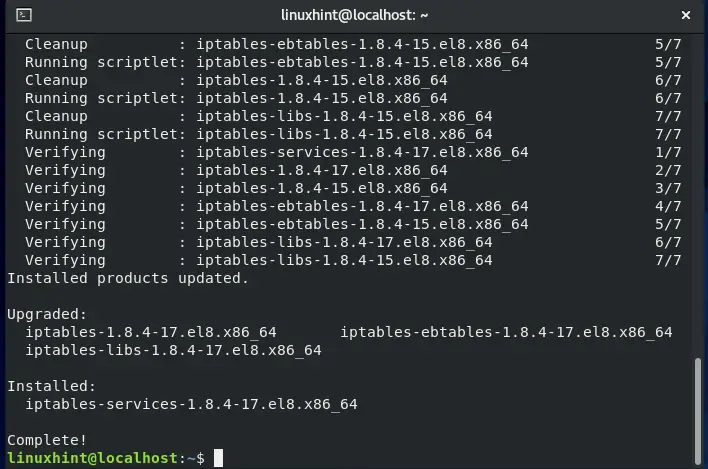
In your CentOS terminal, you can easily install iptables by executing the command given below:
The error-free output signifies that iptables utility is successfully installed.
How to enable iptables on CentOS
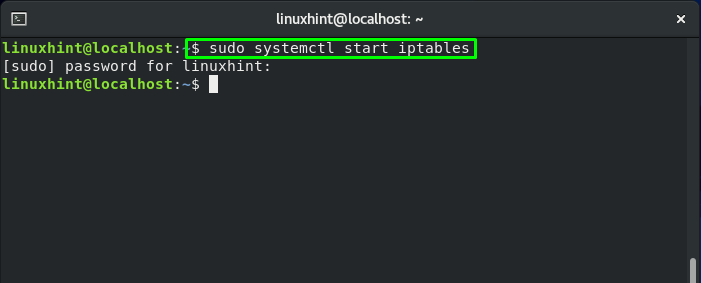
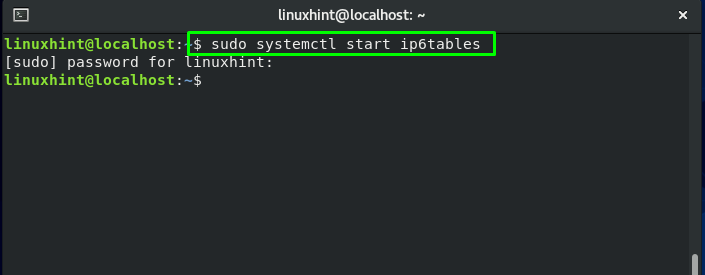
To follow up the procedure of enabling iptables service, the first step to do is to start its service:
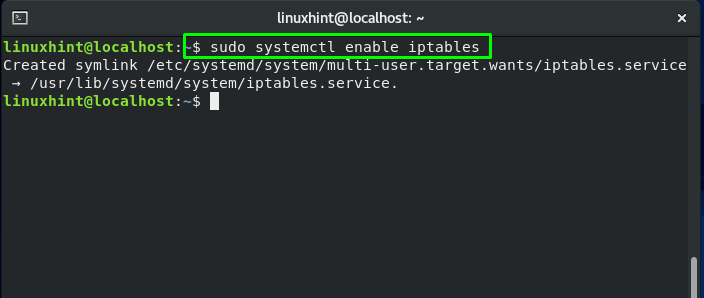
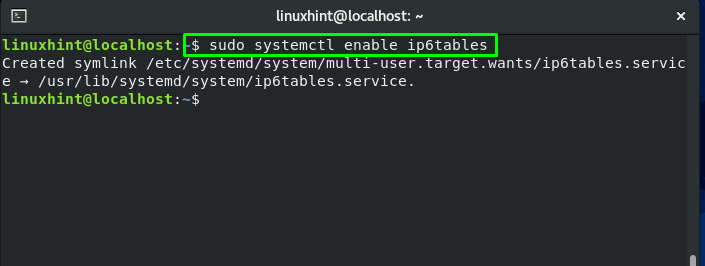
For enabling this service to start automatically on CentOS boot, write these commands in your system terminal:
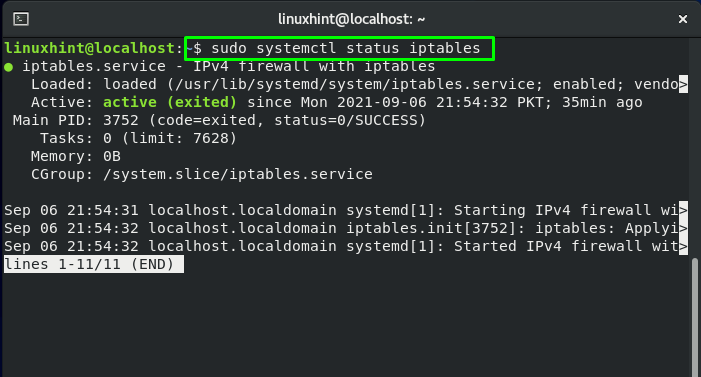
Execute the below-given systemctl command to verify the status of iptables service:
How to configure iptables on CentOS
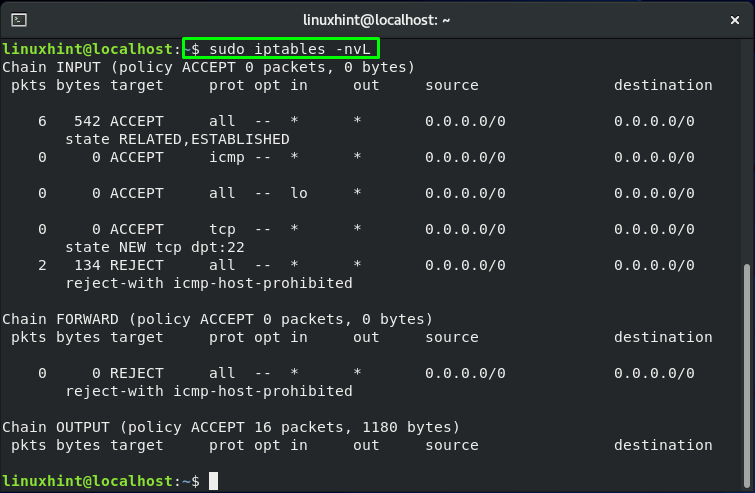
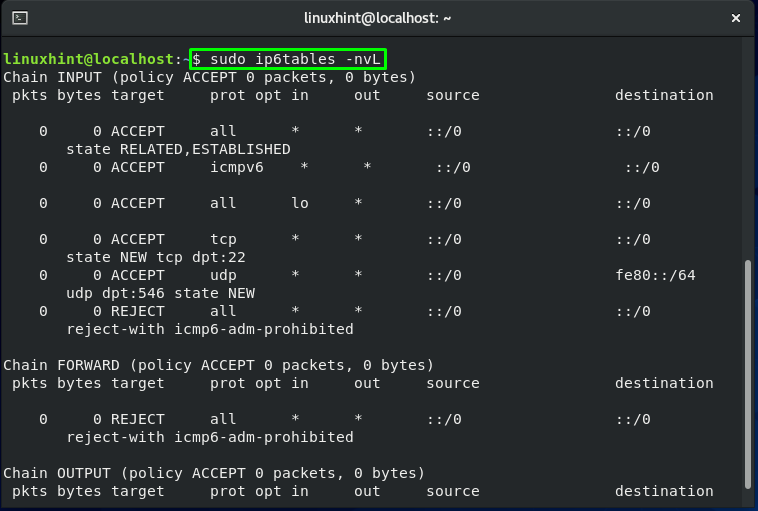
You can utilize the “iptables” command to review the current iptables rules by executing the below-given commands:
Here:
-n is added for numeric output. For instance, the port numbers and IP addresses are printed in numeric format.
-v is for verbose output. This option is added to list the information such as rule options, and interface names.
-L is utilized to list iptables rules.
The SSH port 22 is only open by default. You will get the output like this:
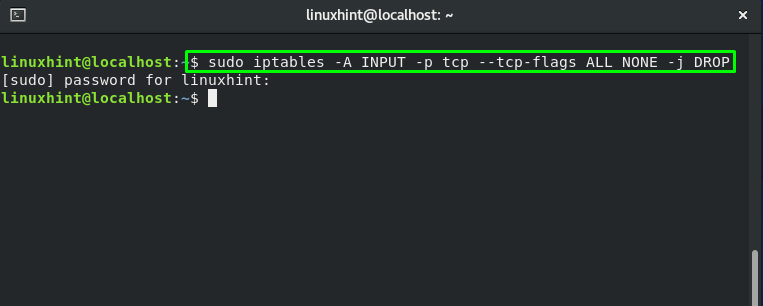
To block all the null packets over the network, execute the below-given iptables command:
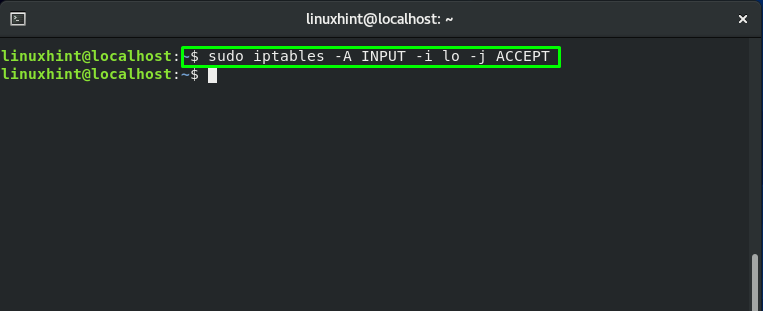
If you want to add your localhost to the firewall filter then execute this command:
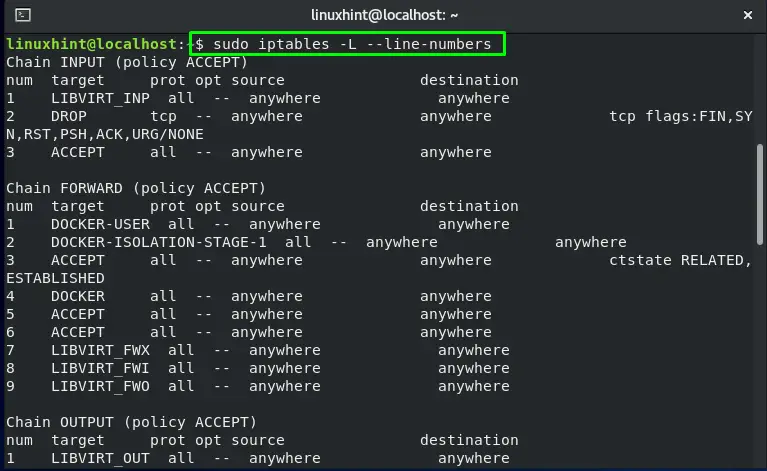
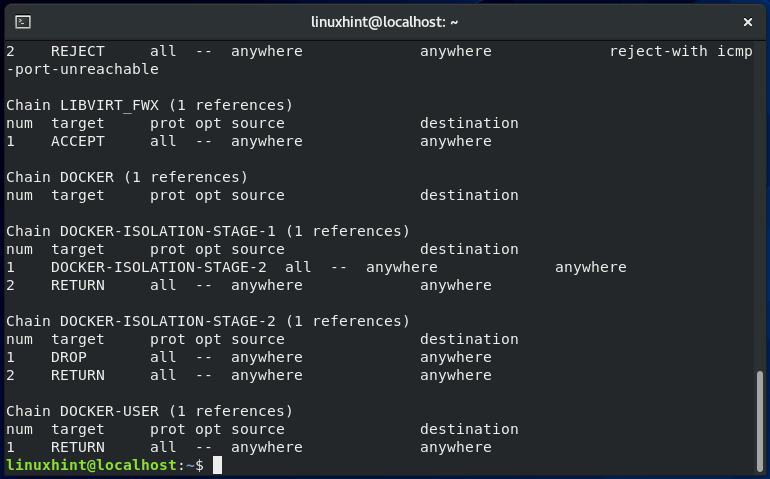
For listing the iptables chain rules with their index numbers, write out the below-given command in your CentOS terminal:
Here, the “-L” option is added to list chain rules and “–lines-numbers” for showing their index numbers:
What is FirewallD in CentOS
FirewallD is a firewall service that is managed via the “firewall-cmd”, a command-line utility. If you prefer the iptables command line syntax, you can disable FirewallD and return to the standard iptables configuration. In the next section, we will demonstrate the procedure of disabling FirewallD on a CentOS system.
How to disable FirewallD on CentOS
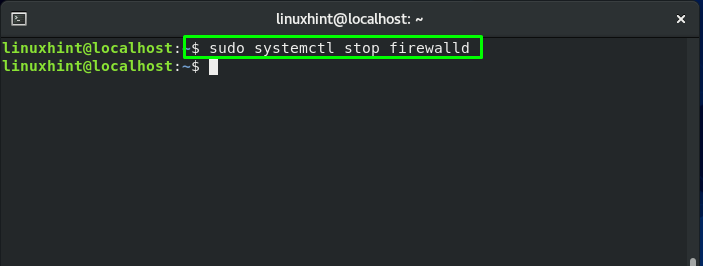
If you want to stop FirewallD on your CentOS, then open up your terminal by pressing “CTRL+ALT+T” and then execute the below-given command in it:
This command will stop FirewallD from performing its functionality:
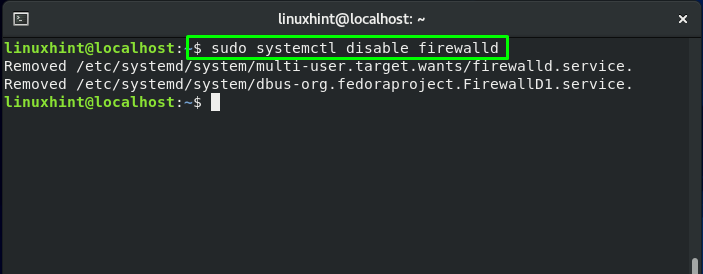
You should know that on system boot, FirewallD service starts automatically. To disable the FirewallD service, write out this command:
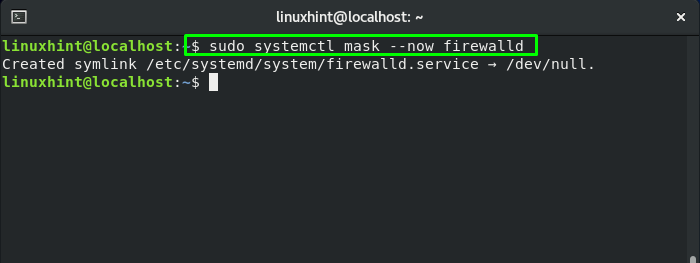
To restrict other services from starting the FirewallD service, mask the FirewallD service:
Conclusion
In Linux-based systems such as CentOS, iptables is a command-line firewall that permits system administrators to control incoming and outgoing traffic by utilizing configurable table rules. Each of these tables comprises a chain of user-defined or built-in rules. In this post, we provided you the method to install and configure iptables on CentOS. Moreover, we have also shown you the procedure of disabling FirewallD on your system.