The resource provides means for injecting sensitive information into containers, such as credentials, while keeping containers Kubernetes-agnostic. By standard, the resource generates a secret accessible to any pod in the chosen or default namespace. Secrets are protected objects that store sensitive information in your clusters. Secrets are more secure than textual ConfigMaps or Pod specs for storing confidential material. Secrets provide you control over how sensitive data is utilized and helps you to save money. There will be less risk of the Secret and its data being revealed during the process of generating, viewing, and updating Pods as Secrets can be established irrespective of the Pods that are using them. Secrets can also be used by Kubernetes and the apps that run in the cluster to take extra measures. When you alter a secret’s value, the value which is used by an already operating pod does not change dynamically. You must remove the original pod and build a new pod to update a secret.
You can define the kind of a Secret by using the type parameter of a Secret resource or certain comparable kubectl command prompt flags when creating one if available. The Secret category is used to make programmatic handling of various types of secret data easier.
For some typical use cases, Kubernetes has multiple built-in types. The validations performed and the limitations imposed by Kubernetes differ between these categories. “Opaque” is one of them, and it will be used in this guide. Let’s get started to create and update secrets in Kubernetes by using kubectl.
Note: The implementation of this article will be done on Ubuntu 20.04 Linux operating system with the help of the minikube cluster. Also, kubectl is already configured in the system. The choice of the operating system may vary from person to person.
Step 1: Start Minikube
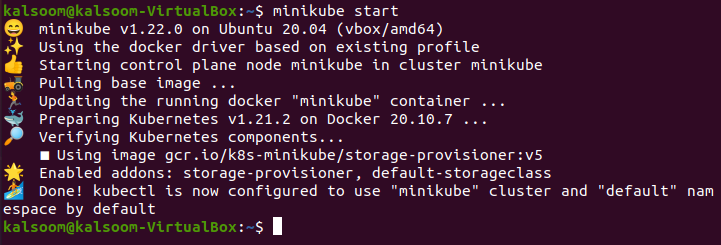
To get started, launch the Ubuntu 20.04 Linux operating system terminal by either checking it in the applications or by selecting “Ctrl+ Alt+T” altogether. Let’s start the minikube cluster with the help of the following appended command in the Ubuntu 20.04 Linux operating system terminal.
Step 2: Create “Opaque” Secret
As already defined, the “Opaque” secret will be created and updated in this guide. Opaque indicates that the details of this Secret are unorganized from the perspective of Kubernetes, and it can include arbitrary key-value pairs. To create an “Opaque” secret, use the following attached command in the Ubuntu 20.04 Linux operating system shell.
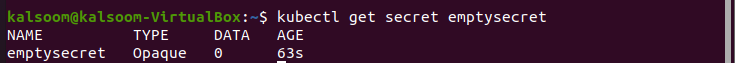
The output is displaying a success message. To display the newly created “Opaque” secret information, execute the below-shown command in Ubuntu 20.04 Linux operating system shell.
The output is the above-displayed relevant information. The quantity of data items confined in the Secret is presented in the DATA column. 0 specifies that we have established an empty Secret in this situation.
Step 3: Update Secret
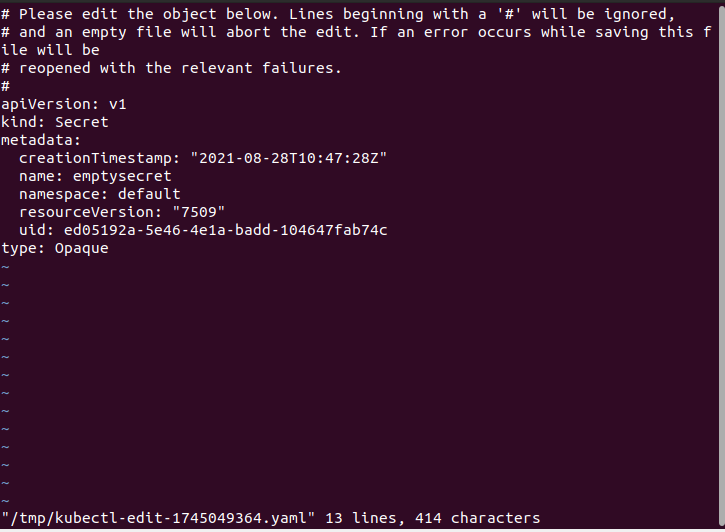
A secret can be edited or updated according to the requirement. The secret can be edited or updated with the help of the following listed commands in the Ubuntu 20.04 Linux operating system shell.
Upon executing this instruction mentioned above in the Ubuntu 20.04 Linux operating system terminal, it will launch the editor with the default settings, allowing you to update the base64 encrypted Secret values in the data field. You can update its fields as per your need.
Once it is updated, you can close this file.
Conclusion
This article has covered the basic idea of secrets in Kubernetes. Secrets could be exposed as the volume of data or exposed as environment variables so that a container inside a Pod can access them. Without even being explicitly exposed towards the Pod, secrets can be exploited by other system elements. Secrets, for instance, can store credentials that other portions of the system can use to communicate with external systems on their behalf. The process to create an “Opaque” secret and its updating is also presented in this guide.