This tutorial explains how to use SSH public key authentication instead of the most widely used password login method.
After reading this tutorial, you will know how to configure your SSH access using key authentication. After the practical instructions, you can find information on the key authentication process, advantages and disadvantages over password authentication.
Configuring SSH Key Authentication on Linux
To begin, you need to generate public and private keys. Private and public keys are generated simultaneously by the same device, and then shared with devices you want to allow connections between.
In this example, we will generate authentication keys from a client using the ssh-keygen command, and then we will send the public key to the server to allow connections between them.
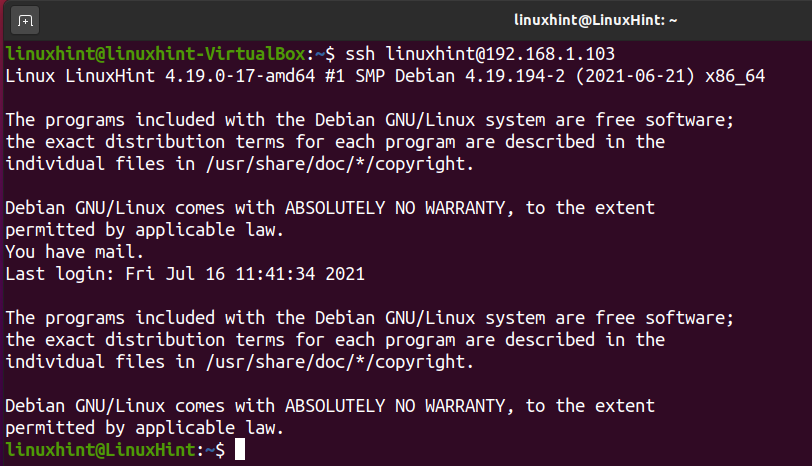
To generate the keys, you need to login as the user allowed to connect. In this tutorial, the user created both in server and client is linuxhint.
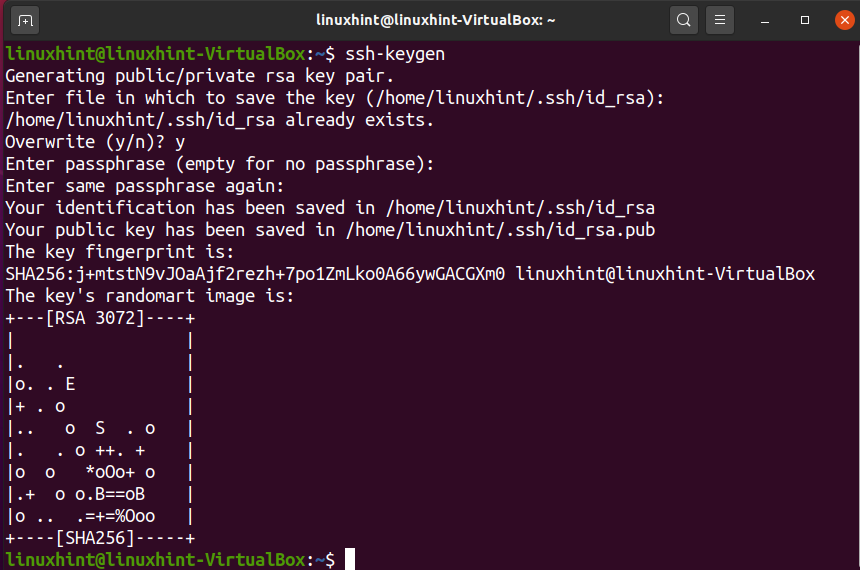
After executing the ssh-keygen command, the process will ask you in which file you want to save the key, press ENTER to leave the default location (~/.ssh/id_rsa).
You also will be asked for a passphrase to encrypt your key. This is recommended but most key authenticated devices don’t use it. You can type a passphrase and press ENTER, or you can just press ENTER, leaving the field empty to avoid encrypting your key.
To generate both public and private keys, run the command below.
Note: In the example below, you can see in my case I already had key authentication, and the process asks me if I want to overwrite the previous key. If you had not a previous key you can ignore it.
As you can, see the keys were generated correctly.
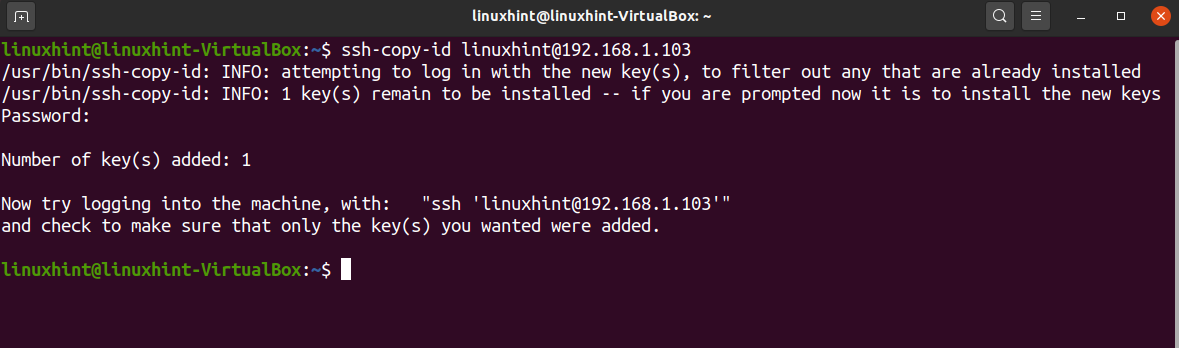
As explained previously, after generating your keys from the client, you need to send the public key to the server you want to be able to connect to. To share the public key with the server, you can use the ssh-copy-id command followed by the username you want to connect as, and the server IP address as shown below.
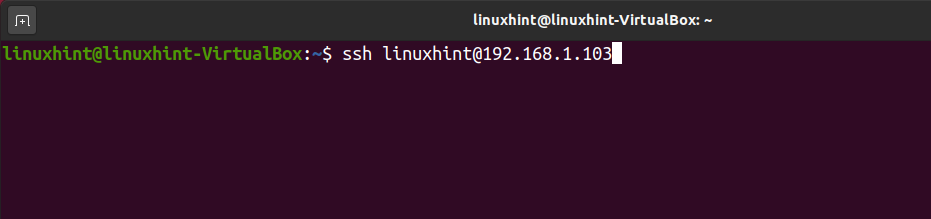
The key was properly installed on the server. Now, you can connect using ssh followed by the username and server IP address as shown below.
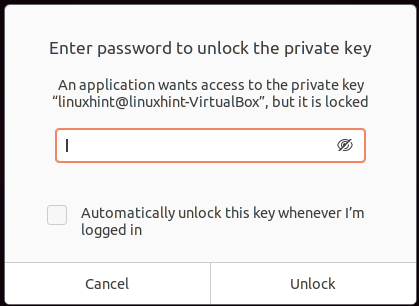
In my case, I typed a passphrase when generating keys. Thus when trying to access a key, I’m requested to type the passphrase. If you also typed a passphrase when generating keys, fill the field and press Unlock to connect.
As you can see in the following screenshot, the connection was established successfully.
Disabling Password Authentication
Now you enabled SSH public key authentication on Linux, you should disable the password authentication method. To achieve it, you need to edit the SSH configuration file /etc/ssh/sshd_config.
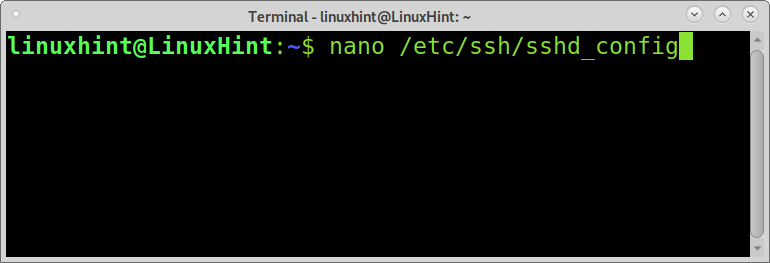
You can use the following command to edit /etc/ssh/sshd_config using nano text editor.
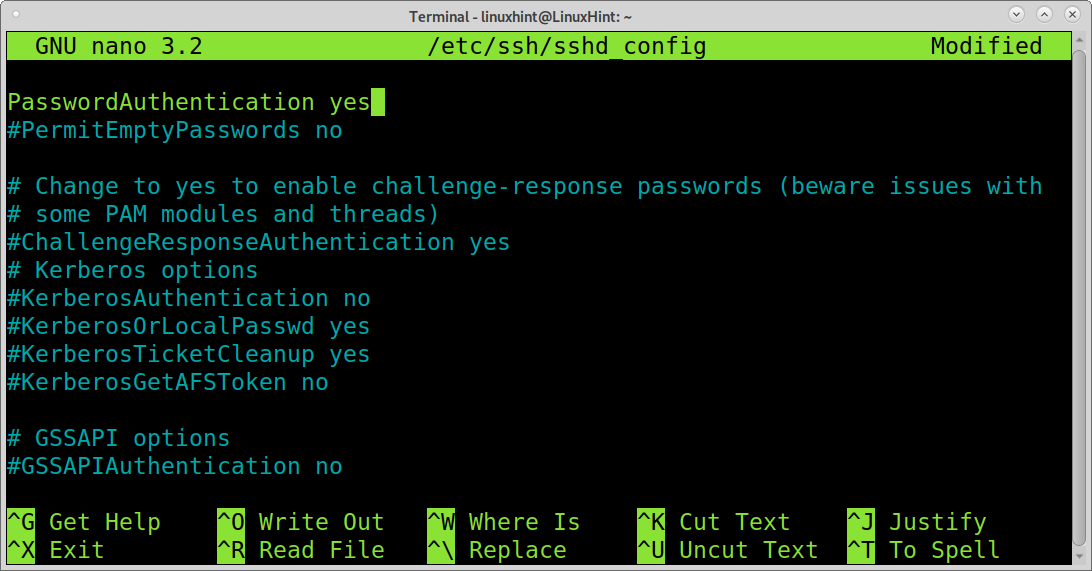
Find the line containing PasswordAuthentication yes shown in the screenshot below.
Edit the line,
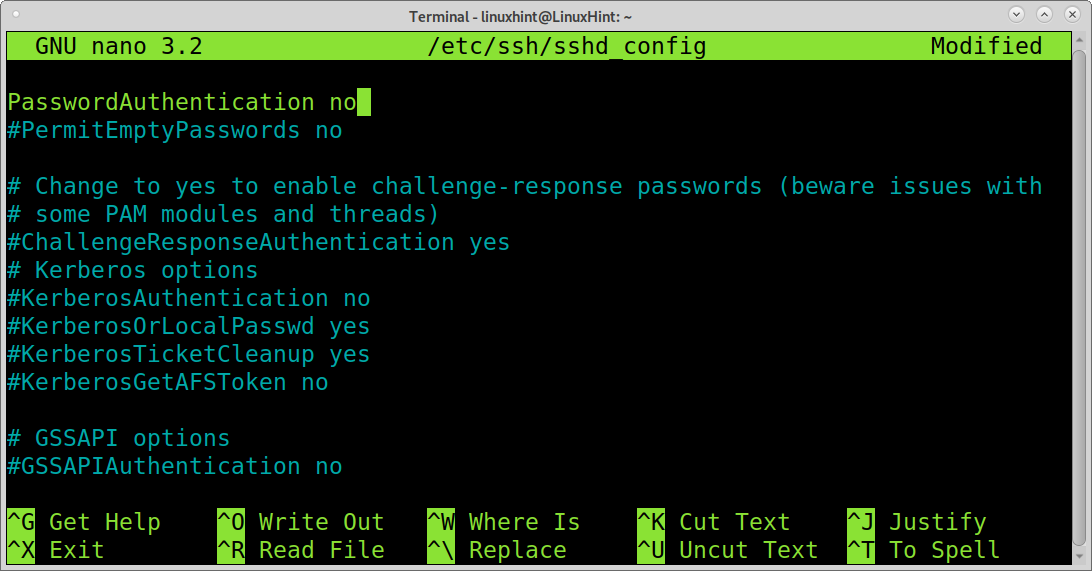
Change it to:
Save and exit the file. If you used nano to edit the file, you can press CTRL+X to exit saving changes.
To apply the changes, you need to restart the SSH service. To do it, run the command below.
Your password login is disabled and you can connect using key authentication.
Disabling Root Login
Disabling root login is also a great way to increase your system security. The root user is universal and vulnerable to brute force attacks. In this way, you can prevent anyone from brute forcing the root, or to login remotely with privileges.
You can disable root login by editing the same file /etc/ssh/sshd_config as shown below.
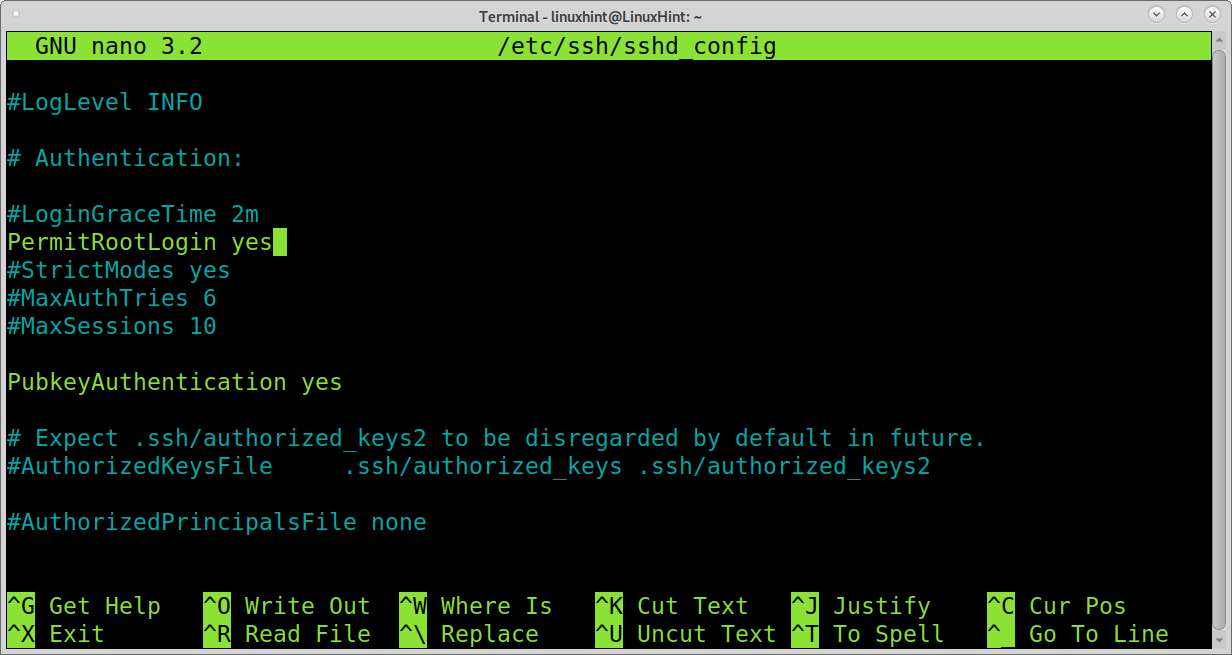
Find the line which contains PermitRootLogin yes shown below.
Edit the following line:
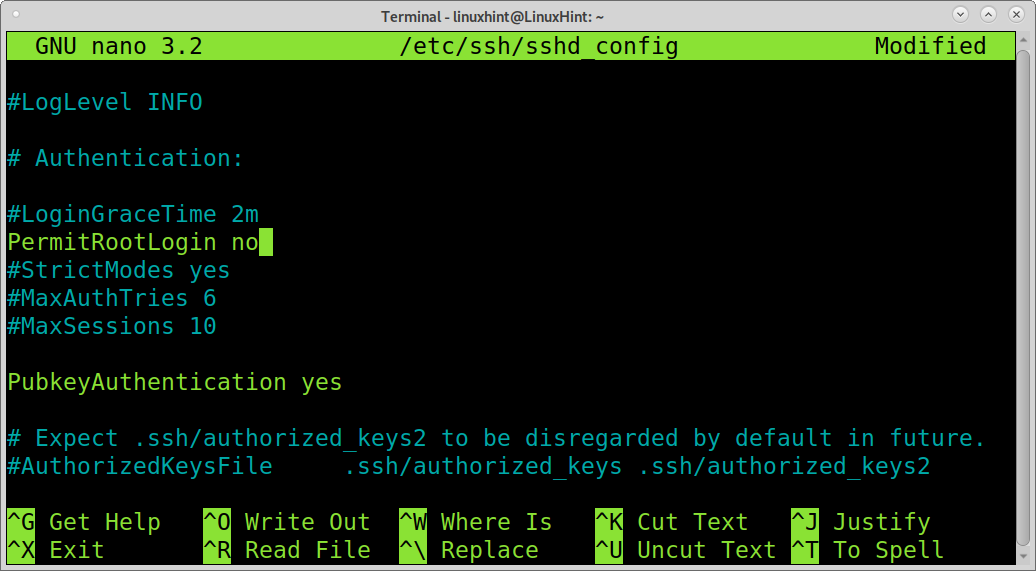
Change it to:
Exit saving changes by pressing CTRL+X.
Restart the SSH service:
Your root login is disabled.
Password vs Key Authentication Methods
As you can see, the key authentication process is easy to implement. When you login to the server you want to connect to, your private key remains safe in your system and is not sent to the server. Instead, the server sends its public key to the client where the authentication takes place.
There are reasons why some users opt for key authentication and others for password login.
Some users will choose a key authentication method because it automatically generates keys that are stronger than human-made passwords. Additionally, private keys are not delivered to the server. They are not vulnerable to man-in-the-middle attacks. When using key authentication, only devices with the private key are allowed to connect, increasing security.
On the other hand, some users will choose password login because they are allowed to connect from any device. Password credentials are also easier to distribute if you have many users to administrate.
Conclusion
As you can see, increasing your system security by replacing password login with key authentication is a very pretty easy process including a few commands to generate the key and share it. Additionally, disabling password authentication only requires replacing a yes with a no in the SSH configuration file and restarting the service. Other methods to increase your SSH security can be learned at Disable root ssh and Linux Two-factor Authentication tutorials.
I hope this tutorial explaining how to use SSH public key authentication on Linux was useful.