It is often unsafe to download files from the internet, which is often dangerous. It is also necessary to download these files for some vital work. Thousands of such files are also downloaded by millions of people. Therefore, such files ought to be protected especially well.
This article will learn about checksum and verify the sha256 checksum of a file on Linux.
Prerequisites
- Terminal (non-sudoers can easily work there)
- Validate the checksum file (it is necessary)
- ISO file (downloaded)
What is SHA256?
According to the U.S. National Security Agency, this algorithm is part of the SHA2 family of algorithms. The acronym SHA stands for ‘Secure Hash Algorithm,’ and 256 is the number of bits used in these algorithms.
What is SHA256 Checksum?
It is a cryptographic signature of any file that it can use to identify or detect errors introduced during transmission or storage. A checksum measures the size of a block of digital data. It uniquely represents a file that is a string. Linux has several mathematical algorithms to generate a checksum for a file.
Typically, on the internet, the SHA256 checksum is provided as a string directly in the main file or as a text file in the download section. Through the original checksum file, we can verify the checksum with the Checksum Utility tool.
How to Generate Sha256 Checksum?
A checksum algorithm generates a checksum. There are various checksum algorithms.
- Secure Hash Algorithms and variants (SHA-1, SHA-2, etc.)
- MD-5 Algorithm
The secure hash algorithm generates a checksum value by breaking the file’s data into smaller chunks, creating a hash value for each part, and adding them.
SHA256 creates the digest or hash value of the file, and once the file is tampered with or modified, the original SHA256 digest value is changed.
How to Verify SHA256 Checksum with sha256sum
We can verify sha256 checksum in two ways,
- Command-line utility sha256sum
- GUI method
Command-Line Method
There are tools available in each Linux distribution for different checksum algorithms. We can verify and generate the checksum using these tools. Some command-line checksums are as follows.
Apart from all this, sha384sum, sha224sum, etc., are also available, which use similar command formats. Here we will verify the checksum with the help of sha256sum using “OpenSUSE Leap 15.2”.
Command-Line utility SHA256sum
We do not need to perform any installation for sha256sum as it is a part of GNU Coreutils. Checksum files are available for download from most distributions with ISO files.
We will download the OpenSUSE Leap 15.2 ISO file first and then download its checksum with the help of the wget command. It is worth noting that along with ISO files, the text file ‘SHA256SUMS’ is also provided and contains checksum values.
Once the checksum is downloaded, we can generate the checksum with the help of the below-mentioned command.
0fd2d4e630b6579b933b5cb4930a8100acca6b4e29cd2738c4b7a9b2f76d80e4 openSUSE-Leap-15.2-DVD-x86_64.iso
The command with the ‘-c’ flag is run to compare the checksum with the value in the SHA256SUMS file. The filename and checksum compare all the files in the directory with the corresponding filename and calculate each file’s checksum.
openSUSE-Leap-15.2-DVD-x86_64.iso: OK
sha256sum: WARNING: 14 lines are improperly formatted
Based on the ISO file’s checksum, we can see it matches the original file. We received OK in the output, which means that the file downloaded is not corrupted and tampered with. As a result, we can see that no files have been tampered with or modified during the download.
If ‘Fail’ is written in the output instead of ‘OK,’ it shows that our file is corrupted and tampered with while downloading it. We have to download the file back; otherwise, we cannot download the respective distribution.
GUI Method
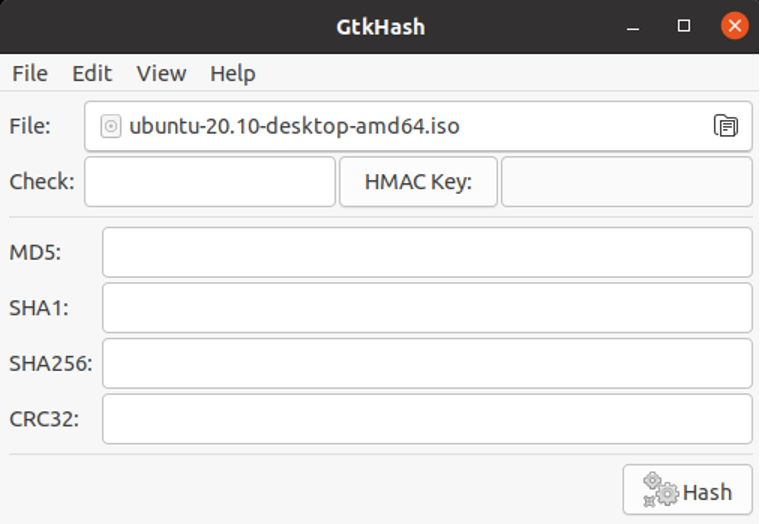
With the help of GtkHash, we can use a graphical method to verify the checksum. It can verify checksums by using GtkHash, which supports MD5, SHA, and other checksum algorithms.
Installing GtkHash on Ubuntu
We can easily install GtkHash in our Ubuntu system by simply running the command written below:
That’s all we need to do. Select the checksum algorithm of our choice.
- In the menu, select Edit > Preferences.
- Choose the ones we want to use.
- Click the Close button.
Using GtkHash
The application is relatively easy to use.
- The first thing we need to do is select the file to be reviewed.
- Afterward, enter the checksum value found on the website in the check box.
- Press the Hash button.
- It generates the checksum value with our chosen algorithm.
- If the check box matches any of them, it shows a small tick mark next to it.
Conclusion
In this article, we have seen how checksum accurately detects corrupt files. It is so accurate that if we replace or delete a character from any text file inside the ISO image, the checksum algorithm generates an entirely different value for that changed image. We hope that you have understood everything well from this article.