SSH or Secure Shell is a useful encrypted protocol to secure connections between the client and the server for different administrative tasks. It supports various types of authentication systems. Public key-based authentication and password-based authentication are mostly used. Key-based authentication is more secure than password-based based authentication. Authentication key pairs for the SSH are generated by the ssh-keygen tool that can be used for different purposes such as authenticating the host, automating login, etc. How this tool can be used in Ubuntu has been shown in this tutorial.
Syntax:
The syntax of this command has given below. It supports many options for generating authentication key pairs that have been described later.
[-t dsa | ecdsa | ecdsa-sk | ed25519 | ed25519-sk | rsa]
[-N new_passphrase] [-O option] [-w provider]
Different options of ssh-keygen:
The purposes of using different types of ssh-keygen options are explained below.
| Option | Purpose |
|---|---|
| -A | It generates the host keys with the default key file path, empty passphrase, default bits for the key type, and comment. |
| -b bits | It is used to define the number of bits in the key that will be created. |
| -C comment | It is used to define the new comment. |
| -c | It is used to request for changing the comment of the public and private key files. |
| -E fingerprint_hash | It is used to define the hash algorithm that will be used to display the fingerprints. |
| -e | It is used to read the private or public key file and print to the stdout. |
| -F hostname | [hostname]: port | It is used to search the particular hostname with the optional port number in the known_hosts file. |
| -f filename | It is used to define the filename of the key file. |
| -H | It is used to hash a known_hosts file. It will replace all hostnames and addresses with the hashed representations within the specified file. The original content will be moved to a file with the .old suffix. |
| -i | It is used to read an unencrypted private (or public) key file. |
| -L | It is used to prints the contents of one or more certificates. |
| -l | It is used to show the fingerprint of a specified public key file. |
| -N new_passphrase | It is used to provide the new passphrase. |
| -P passphrase | It is used to provide the old passphrase. |
| -t dsa | ecdsa | ecdsa-sk | ed25519 | ed25519-sk | rsa | It is used to define the type of key that will be created. |
Create keys using ssh-keygen:
You can create SSH key pairs by running ssh-keygen with options or without any option. Different ways to create the SSH key pairs have shown in this part of this tutorial. You have to log in to the server machine where OpenSSH has installed to create the keys
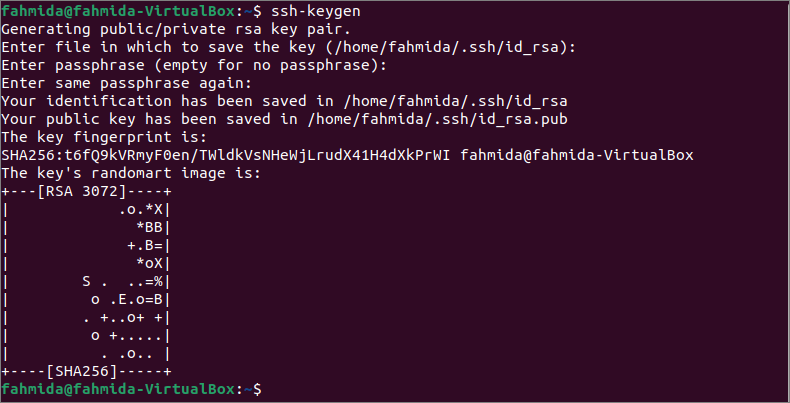
Generate the key pairs without any option:
The following command will create key pairs without using any option.
After executing the above command, you can provide the filename where the key will be saved or press the Enter key to save the default filename. Here, the Enter key has been pressed. Next, you can press Enter key again to set the empty password or set the password.
Generate the key pairs with a single option:
The following command will generate the key pairs of the rsa type mentioned in the command with the -t option.
Like the previous command, you can provide the filename or use the default filename for storing the key pairs and set the password or the empty password for the SSH connection.
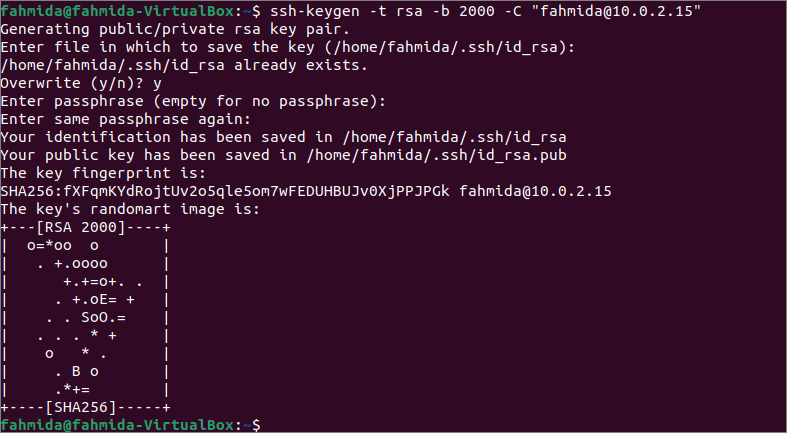
Generate the key pairs with multiple options:
Run the following command to generate the key pairs of rsa type with 2000 bits and the comment value, “[email protected]”.
Like the previous command, you can provide the filename or use the default filename for storing the key pairs and set the password or the empty password for the SSH connection. If you generated the key files before executing the above command, then it will ask you to overwrite the key file or not. If you type ‘y’, then it will overwrite the previously generated file with the new keys.
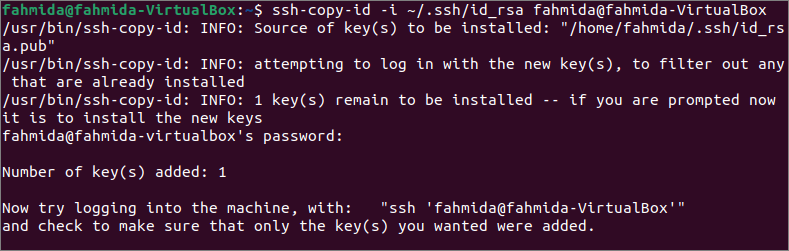
Copy the public key to the server:
Run the following command from the server machine to add the public key to the server machine. The command will copy the key to the server and configure it to add the key to the authorized_keys file to access the server.
The following output will appear if the public key didn’t add before into the server machine.
Modify the config file of the server:
You have to enable some options in the configuration file of the server machine if you want to set the password-based authentication and permit root user login of the server. The path of the server’s SSH configuration file is /etc/ssh/sshd_config. Open the file in any text editor. Run the following command to edit the file in nano editor.
Add or modify the file with the following lines to enable the password-based authentication and set permission for root user login.
PermitRootLogin yes
Save and close the file. Run the following command to restart the SSH service.
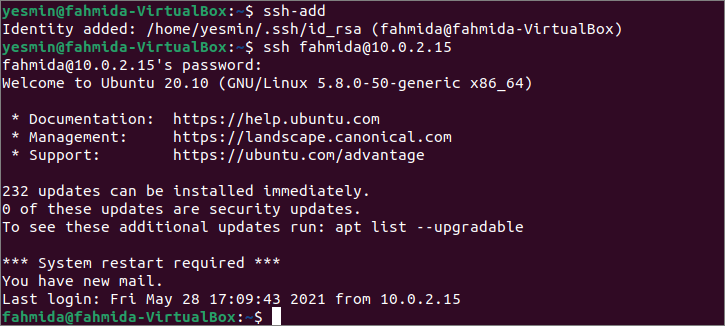
Login from the SSH client:
Login to the client machine from where you want to connect with the server to check whether the SSH connection is working. Open the terminal and run the following command to add the identity of the server machine.
Run the following ssh command to connect with the server machine from the client machine. The password authentication and root login have been enabled in the SSH configuration file of the server in the previous part of this tutorial. So, the user has to provide the valid root password of the server machine to establish an SSH connection successfully.
The following similar output will appear after establishing an SSH connection to the server from the client.
Conclusion:
The ssh-keygen uses to generate SSH key pair in different ways have been explained in this tutorial. I hope the Ubuntu user will generate the SSH keys by using ssh-keygen for establishing an SSH connection after reading this tutorial.