Nmap (an acronym of Network Mapper) is an open-source command-line utility to securely manage the network. Nmap command has an extensive list of options to deal with security auditing and network exploration.
Nmap command can be used to scan the ports or hosts, list down the services on the network, get the list of all live hosts, check the open ports on the network, real-time information about the network, and much more. This article provides well-known use cases of the Nmap command on Ubuntu 22.04.
Prerequisites
To use the Nmap utility, the Nmap must be installed on your Ubuntu 22.04. Nmap is available on the official repository of Ubuntu 22.04. Before installation, it is a better practice to update the core libraries of Ubuntu 22.04 as follows:
After that, execute the below-mentioned command to install Nmap on Ubuntu 22.04:
To verify the installation, get the version of the newly installed Nmap:
The output of the above command ensures that the Nmap has been installed successfully.
How to use Nmap on Ubuntu 22.04
Nmap is the favorite utility of network administrators as they can use Nmap to scan the IP address, scan the host, find a live host, and much more like that. Firstly, make use of the following command to get the man page of Nmap:
The output of the command provides the purpose and the syntax of the Nmap command. We are listing the common fruitful usages of the Nmap command.
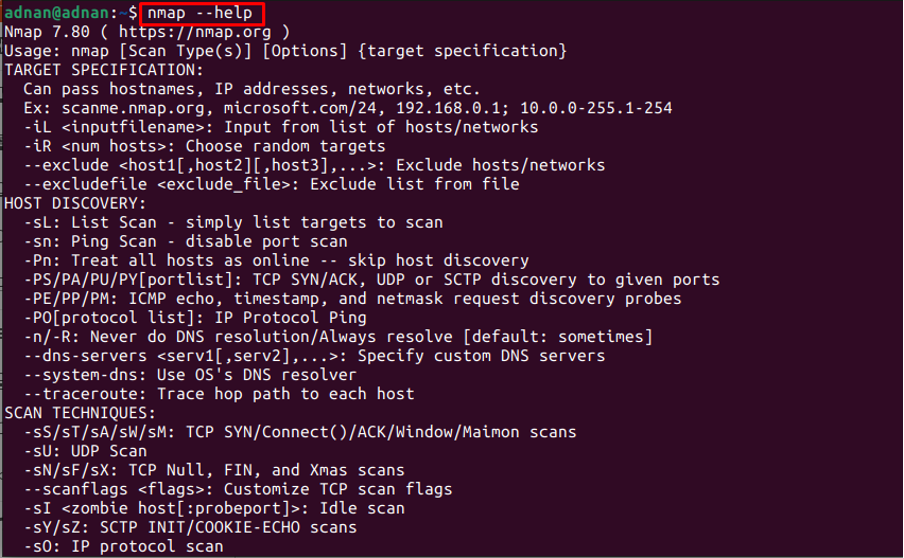
Moreover, you can also get the list of options supported by the Nmap command. To do so, make use of the following command:
It can be observed from the output that the Nmap has a wide range of options that can be used for IP address scanning, detecting the Operating System information, Firewall settings, and much more.
Syntax of Nmap command
The syntax of the Nmap command is given below:
The options supported by the Nmap command are provided in the above image. Moreover, the Nmap command intends the scanning operations on the IP or the web addresses.
How to use the Nmap command to scan for open ports
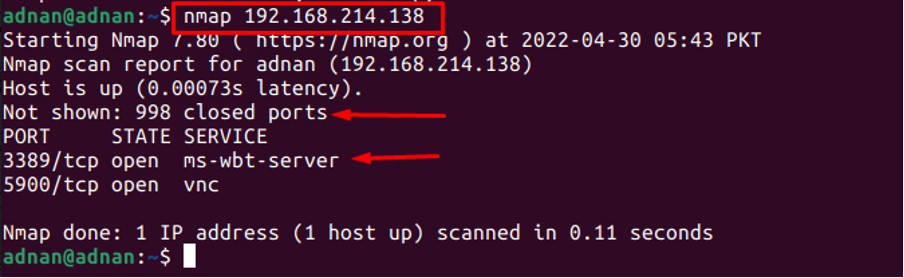
The Nmap command can be used to scan through the open ports of the host. For instance, the following command will scan the “192.168.214.138” for open ports:
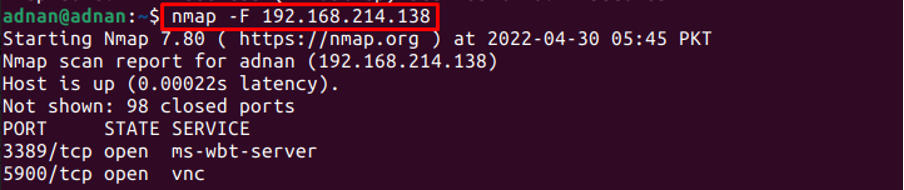
However, you can perform a fast scan by using the “F” option of the Nmap command:
The result of the command would be the same, but the “-F” option prints the results fast.
How to use the Nmap command to scan specific port(s)
By default, the Nmap scans through only 1000 most used ports (these are not consecutive but important). However, there are a total of 65535 ports. The Nmap command can be used to scan a specific port or all the ports.
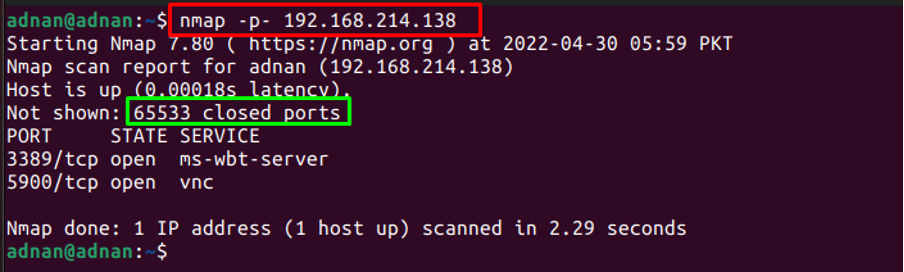
To scan all ports: The -p- flag of the Nmap command helps to scan through all 65535 ports:
The output shows that all the 65533 ports are scanned.
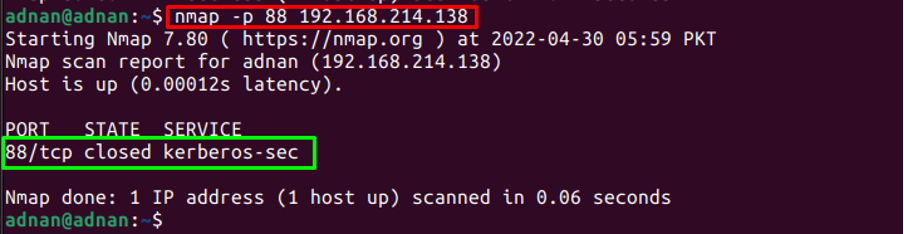
To scan a specific port: One can specify the port number as well. For instance, the following command will scan for port 88 only:
The output shows that the Nmap command has scanned only port 88.
How to use the Nmap command to get the OS information
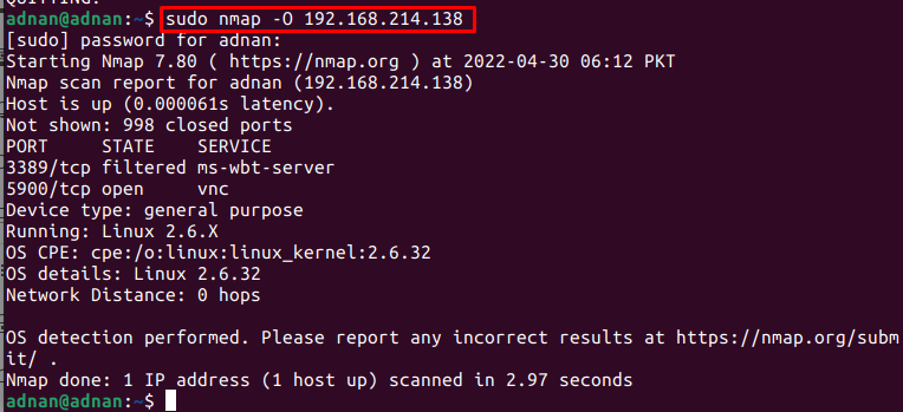
The Nmap command can be used to get the Operating System’s information. For instance, the following command will get the information of the OS associated with the IP address.
Note: It is to notice that this Nmap command requires root privileges to print this kind of information.
How to use the Nmap command to detect the firewall settings
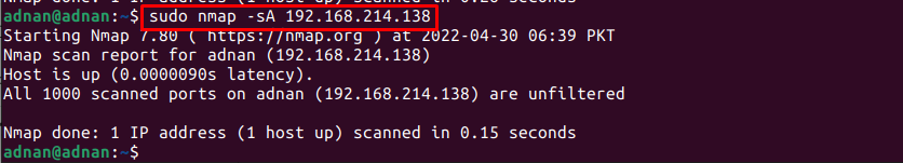
The Nmap command can also be used to get the firewall setting for a specific host. The “-sA” flag of Nmap will tell the status of the firewall on that host:
Note: You can use the “-v” flag (stands for verbose) with the Nmap commands to get the detailed output of the command.
How to use the Nmap command to exclude a specific host
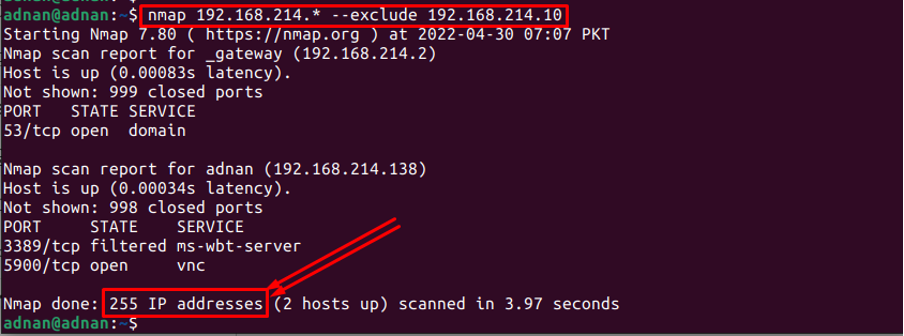
The Nmap performs some scanning operations of the host. However, if there are more than a hundred hosts and you do not need any one of them, you can do it by using the “–exclude” keyword as follows:
The output of the command shows that the Nmap has performed the scan on 255 IP addresses which states that the one IP address is ignored by the Nmap command.
How to use the Nmap command to perform a stealth scanning
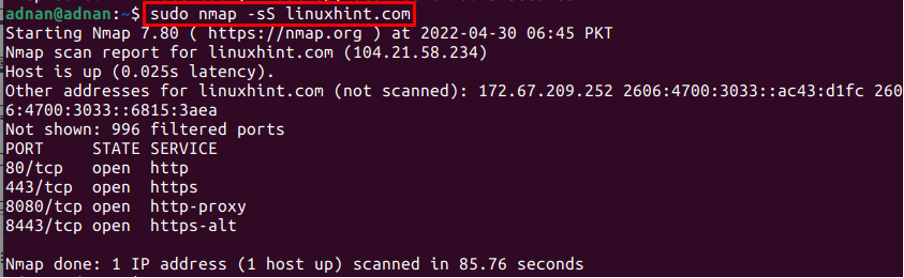
The Nmap command can be used to perform stealth scanning on the IP addresses or the web addresses. The stealth scanning is carried out to nullify the effect of the firewall and any other authentication. For instance, the following command applies a stealth scan on the host’ web address “linuxhint.com”
How to use the Nmap command to detect all up and live hosts
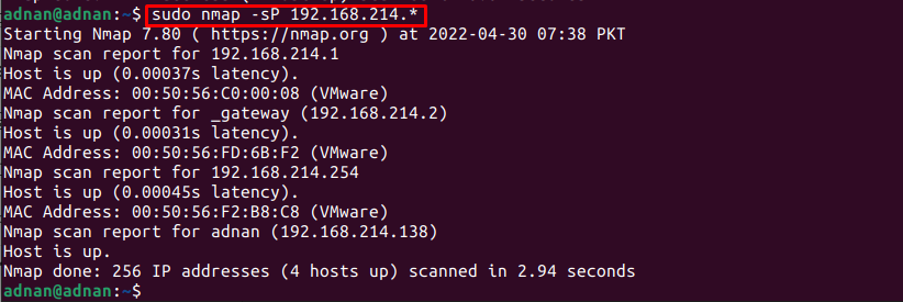
The Nmap command can also be used to get the list of all the live hosts on the specific range of IP addresses. For instance, the following command prints the IP addresses that are UP in between the IP range (192.168.214.0 to 192.168.214.255).
The output shows that among 256 hosts only 4 hosts are up.
How to use the Nmap command to get the service versions
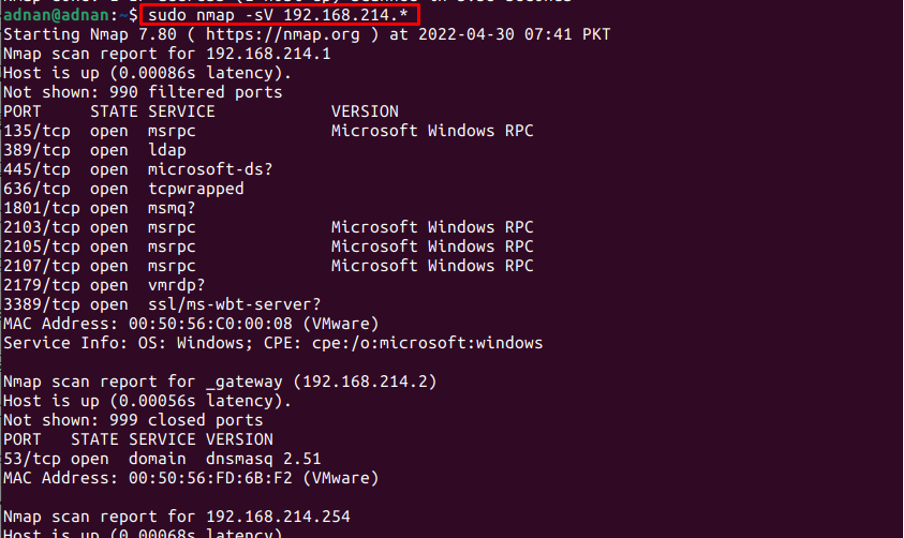
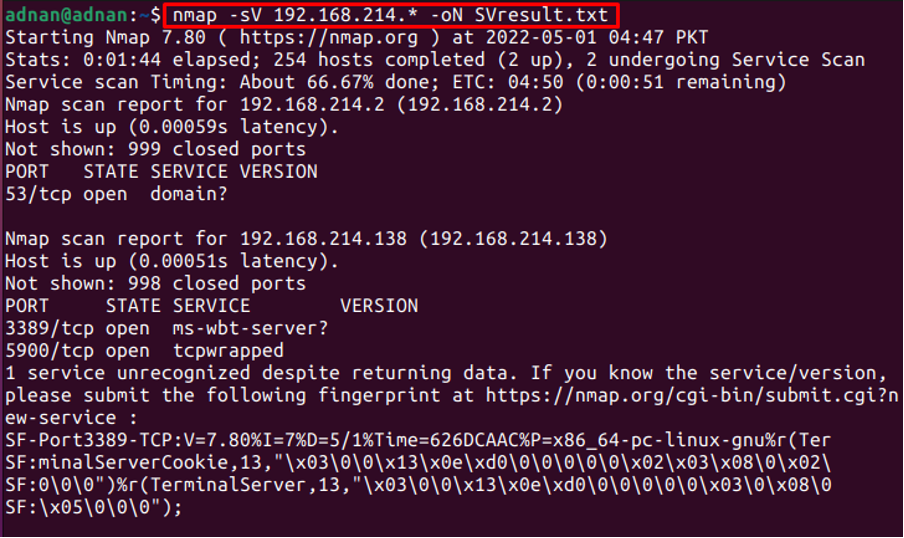
One of the notable uses of the Nmap command is to get the services list and the versions of services running on the specific IP address or addresses. For instance, we have executed the following command to get the versions of the services on the 256 IP addresses ranging from 192.168.214.0 to 192.168.214.255.
The output shows the list of services and their versions on the specified range of IP addresses.
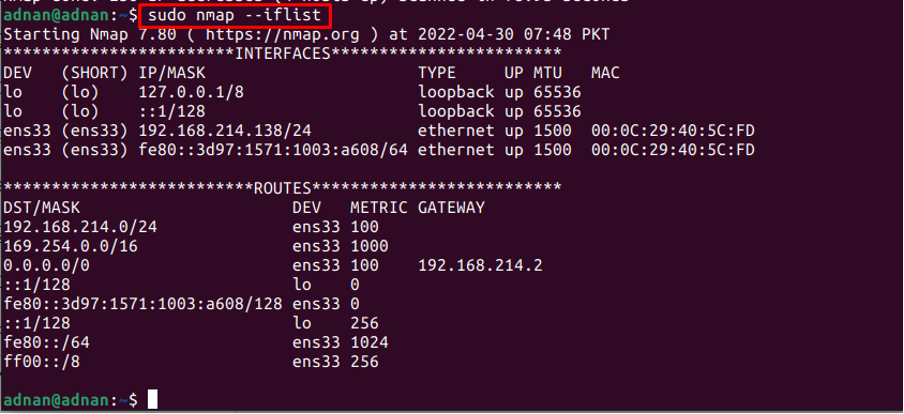
How to use the Nmap command to find the host interfaces
The Nmap command can be used to list down the network interfaces on the current IP address or the host. For instance, the following command returns the interfaces and routes of the IP address (192.168.214.138):
Bonus Tip: How to store the output of the Nmap command
The output of the Nmap command can be stored in a .txt file or in a .xml file. This process is quite helpful when you need to keep track of the historical data.
Get the output in a text file: The -oN flag of the Nmap command helps to save the output in a text file. For instance, the below-mentioned command retrieves the versions of services using the Nmap command and stores the result in a text file:
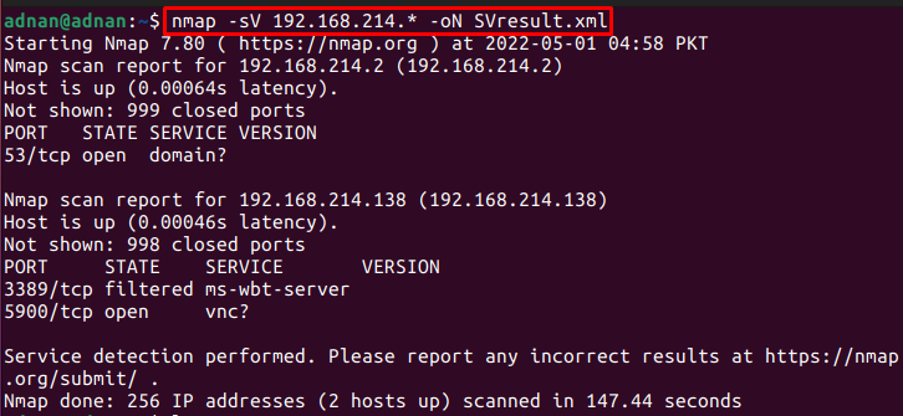
Get the output in an XML file: The -oX flag of the Nmap command helps to store the output in an XML file. For instance, the following command saves the output of services versions in an XML file:
Conclusion
Nmap (Network Mapper) is a command-line utility to get real-time information about the network. Nmap is a cross-platform utility and provides the same functionalities around various operating systems. Keeping in view the importance of the Nmap command, this article provides various use cases of the Nmap command on Ubuntu 22.04.