How to Update sudo Version on Linux
sudo is a command-line utility in Linux and other Unix-based operating systems that allows users to run commands with superuser privileges. The purpose of sudo is to allow non-privileged users to execute commands that would otherwise require superuser privileges, such as installing software, changing system settings, and managing system processes.
Even though sudo includes built-in safety mechanisms, there are still chances of vulnerability in the sudo command. This can happen if the version of sudo that is being used has a known vulnerability that has not been patched. The sudo version needs to be updated to protect against known vulnerabilities.
For example, one of the heap buffer overflow vulnerabilities found in sudo (CVE-2021-3156) can cause any unprivileged user to gain root access and bypass the password protection.
As sudo is widely available on many Linux distributions so any vulnerability in sudo will directly affect you.
How to Check sudo Vulnerability
To check if the sudo is vulnerable and need to be updated we can try two methods:
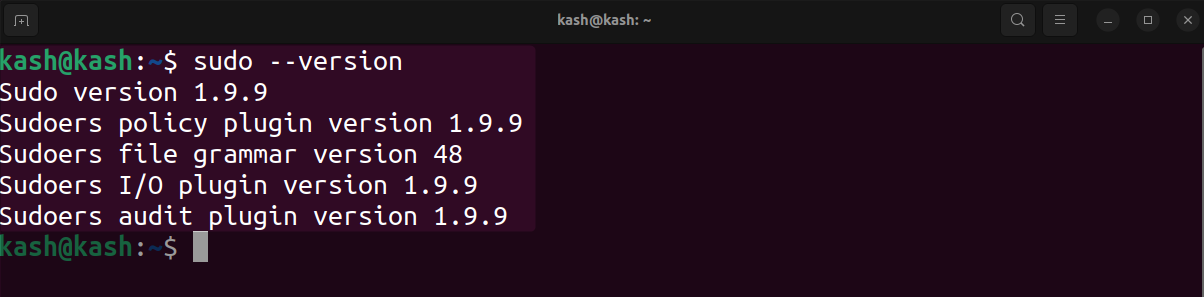
1: Check sudo Version
Check the sudo version and compare it against affected versions.
Run below command to check sudo version:
After knowing your sudo version you can check if it is affected or not.
For example, the sudo versions affected by CVE-2021-3156 are:
- All sudo legacy versions (1.8.2 to 1.8.31p2)
- All sudo stable versions (1.9.0 to 1.9.5p1)
If your sudo version is affected then it needs to be updated.
2: Test the Vulnerability of sudo Using Command Line
The sudo version alone is not enough to tell us whether it is affected with vulnerability or not as patches can be easily backported. We have to test the sudo vulnerability directly. Run following command to test sudo vulnerability:
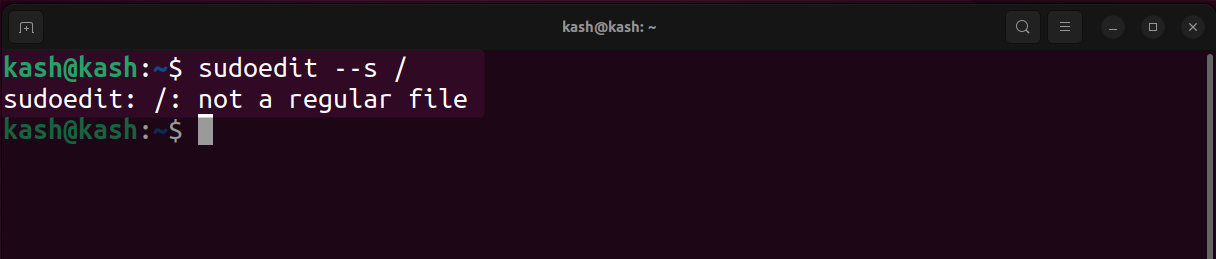
Open Linux as a non-root user run the given command in terminal:
If sudo version is vulnerable following message will be displayed:
“sudoedit: /: not a regular file”
In case if sudo is patched we will see a message that starts with “usage”.
Now as we know that sudo version is affected and needs to be updated.
Update sudo Version on Supported Linux Distros
After finding the sudo version is affected we can easily update it using the package manager of the Linux system. However, this will only work if the Linux distro you are using has not reached End-of-Life (EOL). Otherwise, you have to manually update sudo.
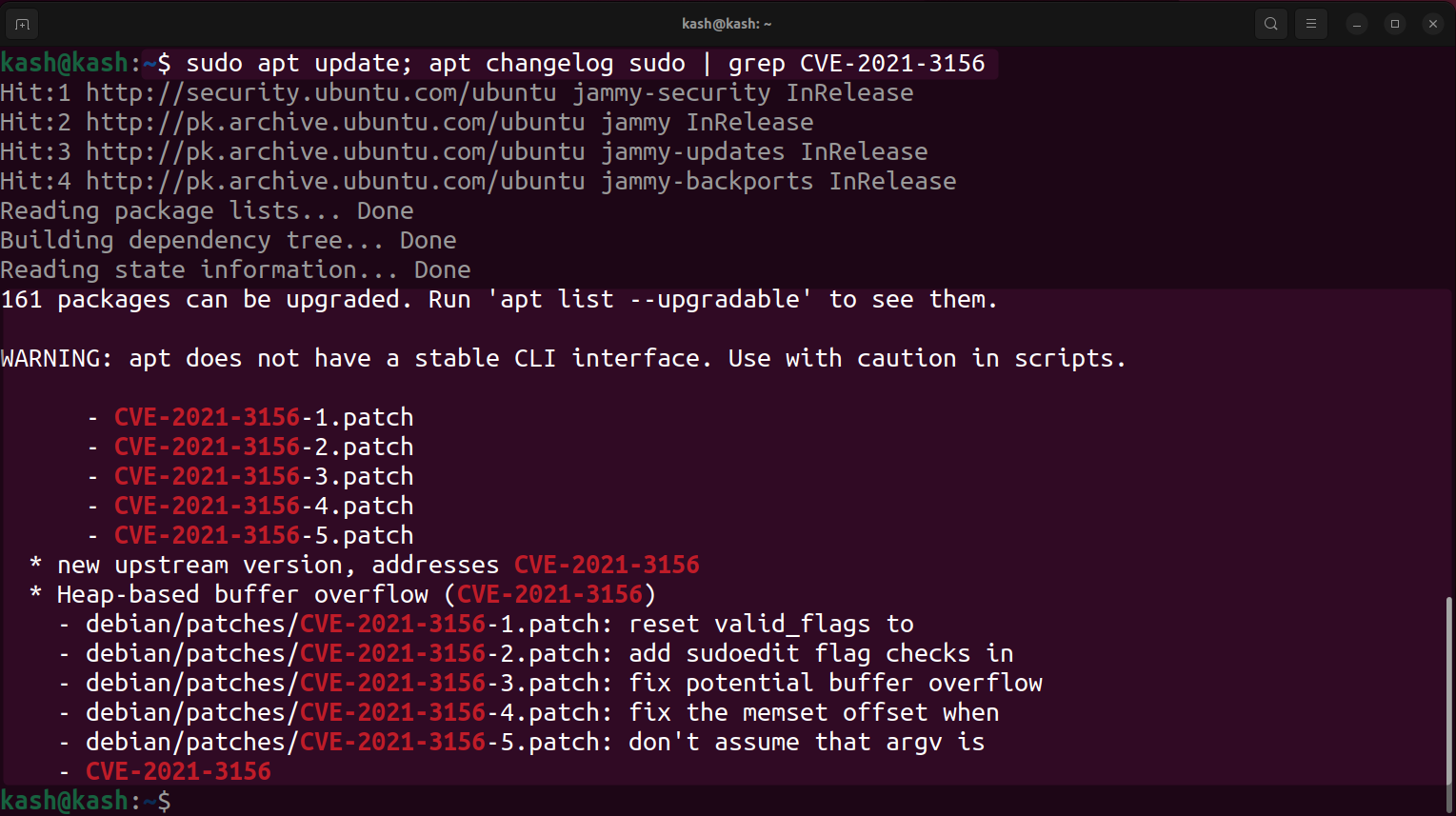
One step before we can update sudo to confirm whether sudo is patched for a certain vulnerability or not.
Here I have taken the CVE-2021-3156 vulnerability. If you upgrade sudo regularly you can skip this step.
sudo vulnerability patch can be confirm using:
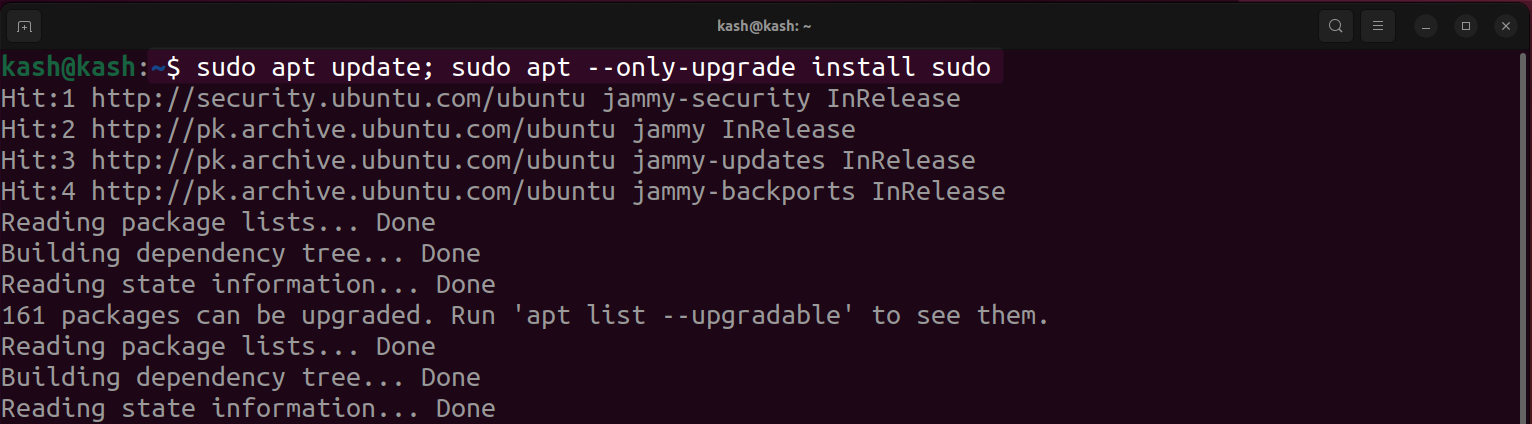
Run command once you confirm that the patch is available for sudo:
Note:
After the sudo is updated, the version may still be the same or one of the impacted versions. This is because most of the time a sudo vulnerability is backported to existing sudo. So, to verify if the patch is successfully installed, test the vulnerability as described in the first step.
It’s important to note that updating the version of sudo may require you to reboot the system for the changes to take effect. It’s also a good idea to make sure to back up your system before updating or upgrading any package.
Conclusion
Updating the version of sudo on a Linux system is a simple process that can be done using the appropriate package manager command. By keeping sudo up-to-date, you can ensure that your system is secure and protected against known vulnerabilities and bugs.