The Importance of Keeping Metasploit Updated
Before we jump into the practical instructions, it’s vital to understand the significant importance of keeping Metasploit updated. The field of cybersecurity is always evolving, and new vulnerabilities emerge frequently. To effectively combat these threats, it’s imperative to maintain the currency of Metasploit’s arsenal of exploits and payloads. Here are some compelling reasons why you should never overlook the task of updating Metasploit:
Stay Ahead of Cybercriminals: Cybercriminals are perpetually on the lookout for fresh avenues to exploit vulnerabilities. By ensuring that your Metasploit is up-to-date, you effectively position yourself one step ahead in the ongoing cybersecurity race.
Enhanced Exploitation: The latest updates frequently bring refinements in exploit techniques, simplifying the process of identifying and capitalizing on vulnerabilities.
Improved Compatibility: Newer modules tend to be more harmonious with your target systems, amplifying your chances of conducting a successful penetration test.
Bug Rectification: Updates also tackle glitches and issues from previous versions, guaranteeing a smoother and more efficient testing experience.
Updating the Metasploit Framework
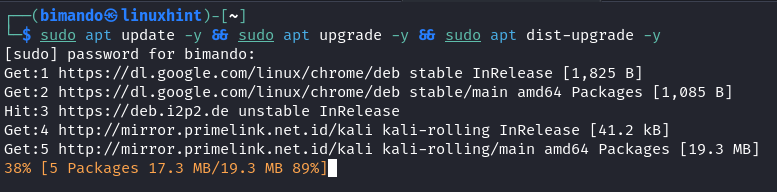
The Metasploit Framework repository is integrated with the latest Kali Linux system repo. To do so, run the following command:
Identify the Metasploit Framework Modules Directory
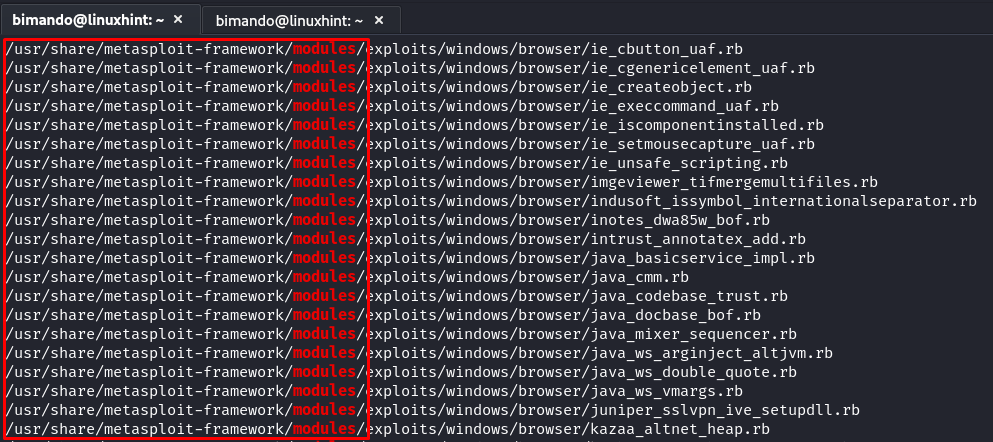
In general, the fundamental mechanism to add modules to our Metasploit Framework is by storing the module file in our local Metasploit directory. Let’s find out where the Metasploit Framework module directory is located by running the following command:
In our Kali Linux, the modules directory is located in /usr/share/Metasploit-Framework/modules/. Please take note of that location.
Adding Modules to Metasploit
Step 1: Find the Module
To begin, you should locate the module that you wish to include. Metasploit possesses a vast collection of modules that you can access via its official website or from a variety of community sources like Exploit-DB, GitHub repositories, or even personal blogs.
Step 2: Download the Module
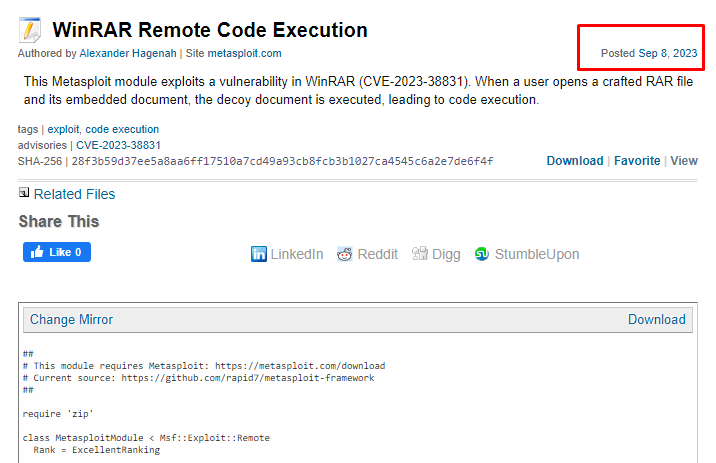
In this tutorial, we use the newest exploit based on a vulnerability in the WinRAR Remote Code Execution (CVE-2023-38831). This exploit is posted a day before this blog is written.
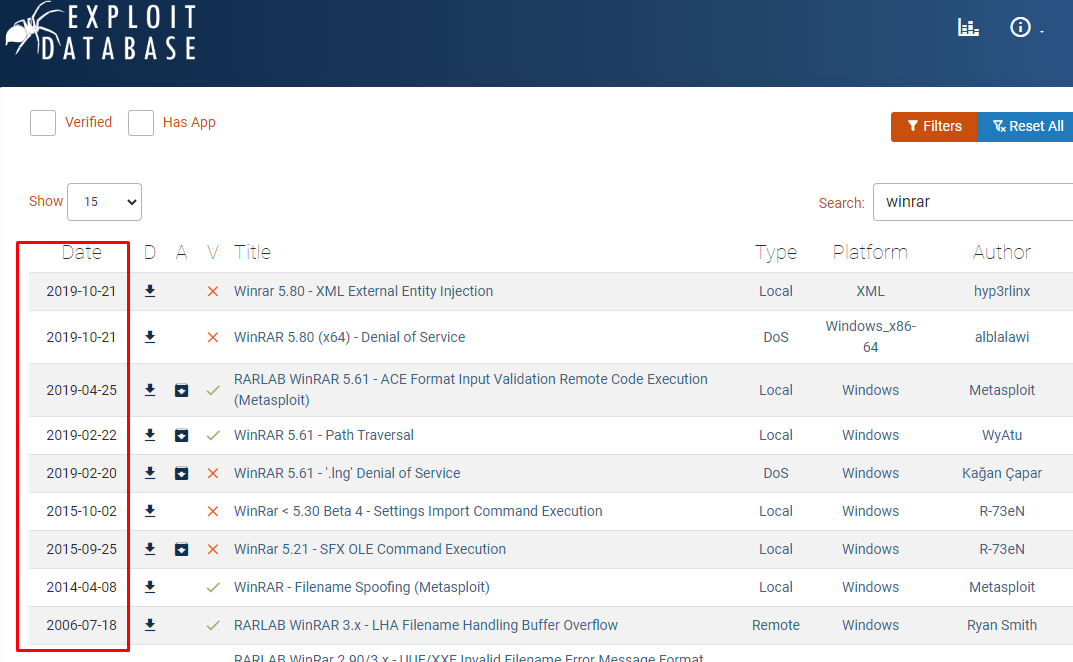
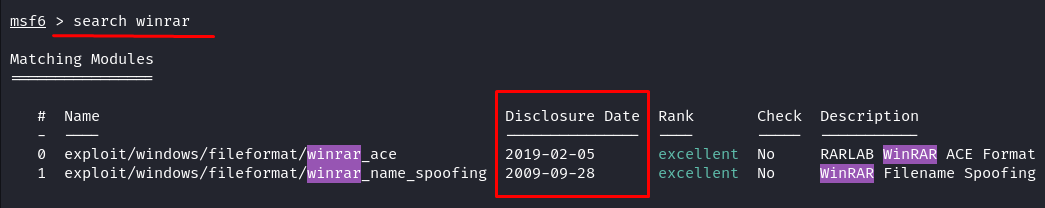
Even the Exploit-DB and the official Metasploit Database haven’t made this module available as of now. Refer to the following image for confirmation:
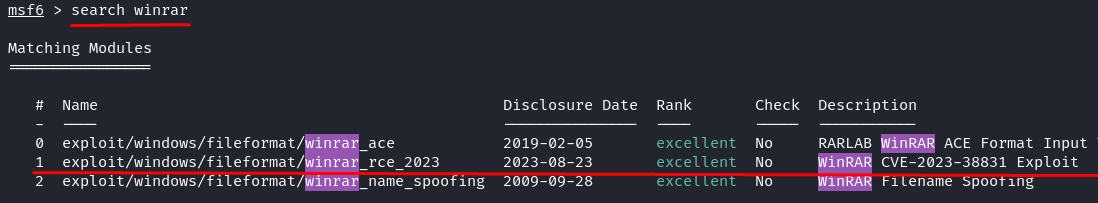
Both Exploit-DB and the Metasploit database have only the old-day exploit module. But our fresh module was disclosed on September 08, 2023. You can download the module at this Packet Storm Security website or jump into the raw file here. Once you downloaded the module, rename it to “winrar_rce_2023.rb”.
Step 3: Move the Downloaded Module into the Metasploit Framework Directory
Once you downloaded the module, move it to /usr/share/metasploit-framework/modules/exploits/windows/fileformat/. If you wondering why we save it there, it is because the other WinRAR exploits are stored there, so it would be easy to organize.
Now, let’s check the module again, still in the msfconsole search, for available WinRAR modules.
That’s it! Your module is successfully installed. You can use it now.
Step 4: Load the module
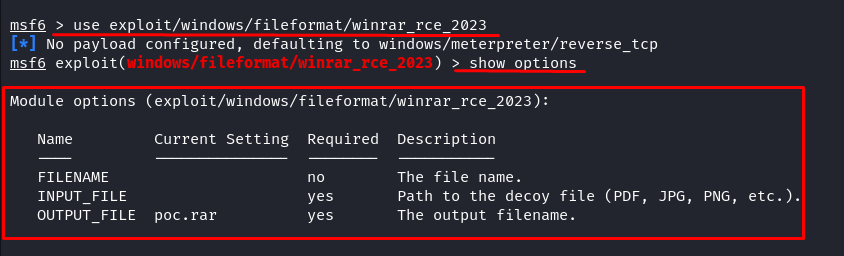
Now, it’s time to load the module that you downloaded into Metasploit. In the Metasploit console, type the following command:
Step 5: Configure the Module
Type “show options” to display the required setting. As you can see in the previous image, this module needs an input file, anything which will then be crafted into a malicious “.rar” file.
Step 6: Exploit
Once the module is configured, you can proceed to exploit the target system. Use the “exploit” command to launch the attack.
Conclusion
In summary, this comprehensive guide provided you with a step-by-step process of updating and integrating the modules into Metasploit, ensuring that you have access to the latest cyber security tools. We emphasized the significance of keeping Metasploit current to stay ahead of evolving cyber threats. You gained insights into identifying the Metasploit Framework modules directory, locating the modules that you wish to add, downloading and relocating the modules, loading them into Metasploit, configuring the module, and exploiting the target system. By following these procedures, you can bolster your cybersecurity arsenal and effectively protect your systems and networks from potential threats.