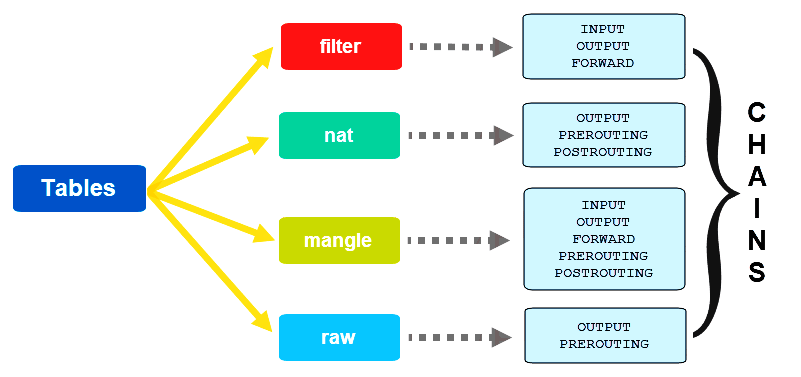
In iptables, a chain is a list of rules that determine how to handle the traffic that matches a specific criteria. Iptables has several built-in chains including the INPUT, OUTPUT, and FORWARD chains. Each chain contains a series of rules that determine how to handle the traffic that matches the criteria that are defined by the rule.
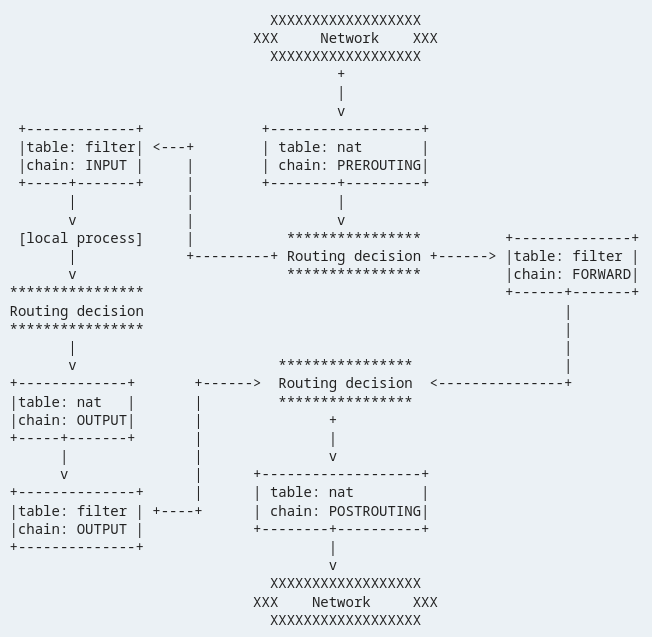
When a data packet arrives at a system, the iptables checks the packet against the rules in the appropriate chain to determine how to handle the packet. If the packet matches a rule, the iptables takes the action that is specified by the rule. If the packet does not match any rule, the iptables continues to the next chain until it finds a matching rule.
Types of Iptables Chains
There are two types of iptables chains: built-in chains and user-defined chains.
Iptables has several built-in chains that are used to control the incoming and outgoing traffic.
These chains include:
INPUT Chain: This chain is used to control the incoming traffic to the system. It contains rules that determine how to handle the traffic that is destined for the system.
OUTPUT Chain: This chain is used to control the outgoing traffic from the system. It contains rules that determine how to handle the traffic that originates from the system.
FORWARD Chain: This chain is used to control the traffic that is forwarded through the system. It contains rules that determine how to handle the traffic that is not destined for the system, but is being forwarded through the system.
User-Defined Chains
Iptables allows the system administrators to create their own custom chains. The user-defined chains are used to group a set of rules together that are related to a specific function or service. This makes it easier to manage and maintain the firewall rules on a complex system.
Creating User-Defined Chains
Step 1: Create a New User-Defined Chain
Run the following command to create a user-defined chain:
This command creates a new chain with the name “chain_name”. Once the chain is created, you can add rules to the chain to control the traffic that matches a specific criteria.
Step 2: Add Rules to the Iptables Chains
Once you created a chain, you can add rules to the chain to control the incoming and outgoing traffic.
Add new rules to the created chain by running the following command:
- The -A option specifies that the rule should be appended to the end of the chain.
- The [options] specifies the conditions that must be met for the rule to be applied.
- The -j option specifies the action to be taken if the conditions of the rule are met.
Note: Here are some common options that can be used when adding rules to the iptables chains:
- -p : It specifies the protocol (e.g., tcp, udp, icmp) that the rule applies to.
- –dport : It specifies the destination port number that the rule applies to.
- –sport : It specifies the source port number that the rule applies to.
- -s : It specifies the source IP address or range of IP addresses that the rule applies to.
- -d : It specifies the destination IP address or range of IP addresses that the rule applies to.
- -i : It specifies the input interface that the rule applies to.
Note: The following are some common actions that can be taken when adding rules to the iptables chains:
- ACCEPT: Allows the traffic to pass through the chain
- DROP: Drops the traffic without sending a response to the source
- REJECT: Rejects the traffic and sends a response to the source
- LOG: Logs the traffic to a log file without taking any other action
- SNAT: Performs source network address translation
- DNAT: Performs destination network address translation
Other Functions in Iptables
The following are some examples on how to use the iptables chains to control the network traffic:
Blocking the Traffic to a Specific Port
Suppose you want to block the incoming traffic to port 22 on your Linux-based system. You can add a rule to the INPUT chain that drops all traffic to port 22.
Run the following command to block the incoming traffic on port 22:
This command allows you to add a rule to the INPUT chain that drops all TCP traffic to port 22.
Allowing the Traffic from a Specific IP Address
Let’s say you want to allow the incoming traffic from a specific IP address (e.g. 192.168.1.100) to your Linux-based system. You can add a rule to the INPUT chain that allows the traffic from that IP address.
Run the following command to allow the traffic from IP (192.168.1.100):
This adds a rule to the INPUT chain that accepts all traffic from the IP address 192.168.1.100.
Conclusion
The iptables chains are a very useful tool to control the network traffic and secure your system. Understanding how the different chains work and how to create your own rules can be a bit challenging at first, but with practice and a good understanding of the core concepts, you can easily create a customized firewall that meets your specific needs. By following the best practices and keeping your firewall up-to-date, you can greatly improve the security and stability of your network.