Also known as ping packets, ICMP echo requests are sent or received using the ping command. An ICMP echo request often means that the host to which the message is addressed should reply directly to the packet using an echo reply.
Normally, an echo request often includes a set of data that you can specify using the ping command. When a host makes an echo reply, all the data in the ICMP echo request will be sent back.
The ping command provides the users with all the modalities of sending the ICMP echo requests and ICMP echo replies. Among the specifications that you may have to make are the source and the destination addresses. Besides, you will also need to set the other modalities in the IP Header section.
When to Use Echo Request and Echo Reply Messages
Notably, whenever the basic connectivity operations fail, one of the most basic tests that the users opt to perform is to verify if the remote system attached to their client machines is up and running. This is where the ICMP query messages come into play. These messages are vital tools for network testing and troubleshooting applications.
The user sends an ICMP Echo Request message to the remote destination system, with the system replying with an ICMP Echo Reply message to deliver the feedback. According to RFC 1122, each host must implement the ICMP Echo server, making this service mandatory.
While this sounds pretty straightforward, this may sometimes not happen automatically. Firewalls, often available for security reasons, can block the packets. Besides, there could also be the failure of packet deliveries for various reasons.
Again, according to RFC 1122, all hosts should endeavor to have an end-user-accessible app interface designated for sending Echo Request messages to any other hosts within the network. This interface is referred to as ping or the ping command and should be present in all computing environments with a TCP/IP stack including the most basic models.
How to Use ICMP Echo Request and Echo Reply Query Messages
Also already indicated, the ICMP (Request and Reply) Echo messages are ideal for network connectivity testing. They can also be used for network troubleshooting purposes.
Using the ping command, you can test the Layer 3 network connections between the host computer and another host device. The host generates and sends an Echo Request message. The computer or device that the host sent an Echo query message to receives the request, process it, and send back an ICMP Echo Reply to the host.
In the previous illustration, the first arrow shows an ICMP Echo Request (Type-8 Code-0) while the second arrow signifies an Echo Reply, often Type-0 Code-0. An ICMP Echo Reply Message often indicates the Type, Code, Checksum, ID, and Sequence.
The Identifier (ID) and Sequence attributes for ICMP messages help to match the Echo Request messages with their respective Echo Reply messages. The data payload for Echo Request packets, which are in ASCII characters, are ideal for padding. Besides, each Echo reply message must come with the same data payload specifications as its corresponding Echo Request.
Sending an ICMP Echo Message
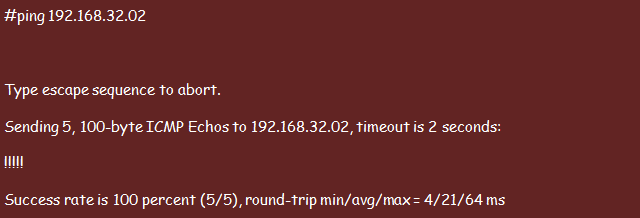
You can send an Echo Request using the following ping command, whereby the IP address is the machine that you are planning to ping.
Your host machine creates an echo message and sends it to the specified device. The device will, in return, create an echo reply and sends it back to the requesting host.
Conclusion
The ICMP command is applicable in an array of network management functions. While this article focused on ICMP echo request and reply query messages, it also comes in handy for troubleshooting purposes.