How Tunneling Works?
Tunneling is a mechanism that protects different services by disabling them to be accessed directly from outside the network. It involves receiving traffic at one port and forwarding it to another port and can be done both locally or remotely. Tunneling is a Port Redirection technique that uses encrypted tunnels within the SSH protocol. Tunneling is a type of communication between two network devices using an SSH connection. SSH catches the service request from the client to the host, then creates a connection that carries the request to the other side of the connection. On the other side of the SSH connection, the request is decrypted to be sent to the application server on the remote system.
Rinetd
Rinetd is a utility that allows the user to forward the network traffic from one port to another port. It is one of the most common ports forwarding utilities because of its easy-to-use nature.
For instance, consider a scenario where the RDP server (192.168.0.10) at port 3389 is inaccessible due to a blockage on all outgoing traffic from the office system (192.168.0.15) except for port 80, and there is another Home system (192.168.0.20), as well.
The situation can utilize the Home system as a proxy with the help of Rinetd such that it will receive a connection from one IP address and port and will forward it to another IP address and port number. On the Home system, configure the rinetd config file as follows:
192.168.0.20 80 192.168.0.10 3389
At the office machine (192.168.0.15), try to connect to RDP at the IP:port (192.168.0.20:80). The Home system will receive the connection at (192.168.0.20:80), but due to the port forwarding, it forwards the connection to the RDP server (192.168.0.10) at port 3389. Hence, the RDP server is accessible from the office system even if all the outgoing traffic is blocked.
Ngrok
Ngrok provides real-time synchronization of what is running on one’s localhost. It allows the website that is running on our localhost behind NAT and firewalls to be accessed by the public via the internet over secure tunnels. Let’s say we are developing a website and testing it on our localhost on port 4444. We want to share it with someone else for demo purposes. We can share it via GitHub and other methods.
But it will take a long time to deploy, and changes will not take place in real-time at all places. With ngrok, any change at the localhost will send an update at everyone’s end. Ngrok is a multi-platform service available to download on its official website.
For instance, a website running on the localhost:8080 can be made publically accessible by anyone with a URL link. Use the following command to generate a public URL:
SSH Tunneling
SSH Tunneling is the best way to tunnel ports from a client system to a server system and vice versa. To use SSH to tunnel the ports, both client and server should have SSH set up. There are three types of SSH Tunneling, i.e., Local Port Forwarding, Remote Port Forwarding, Dynamic Port Forwarding.
Local Port Forwarding
Local Port Forwarding is a technique of making remote resources locally available. These resources might be banned or be placed behind a firewall to restrict local access.
Syntax:
Consider a scenario where a remote desktop needs to be integrated into a home computer from the office system. But port 3389(RDP) is blocked due to security reasons. To access the RDP port, use SSH tunneling to forward block ports to a different unblock a port number. This can be done by using the following command:
Now in the RDP configuration, localhost can be written in place of an IP or hostname with the 4444 port number column to access the home RDP.
Remote Port Forwarding:
Remote Port Forwarding is a technique for accessing local resources remotely. Let’s say a company wants an employee to work from the office, and it restricts office system remote access by blocking the RDP port (3389). In this case, remote port forwarding can come in handy. On the office system, use the following command:
This will establish a connection. Now the work computer can be accessed from the home system using RDP by entering localhost in place of an IP or hostname with 4444 port number column in the RDP configuration.
Dynamic Port Forwarding:
Dynamic Port Forwarding allows one to tunnel multiple ports. In this type of forwarding, SSH acts like a proxy server. Let’s say employees can access the web on port 80 from the office system due to a firewall restriction. Dynamic Port Forwarding can help surf the web on port 80 as from home. Use the following ssh command:
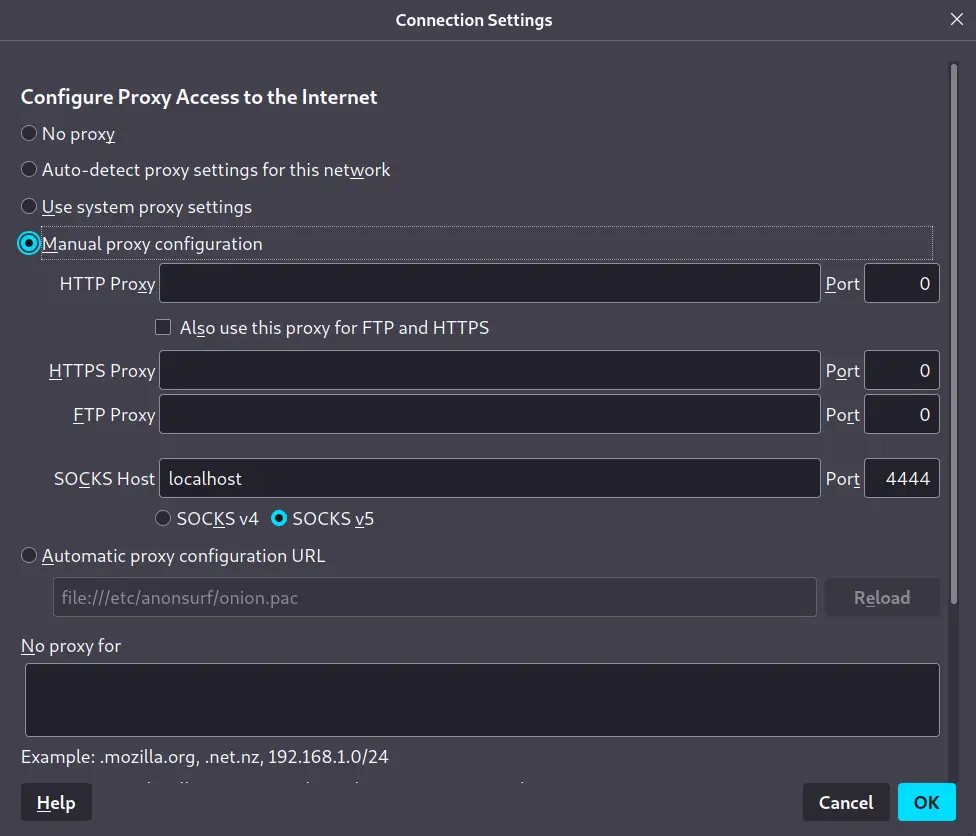
The above command creates a socks proxy, which requires web browser configuration. For Firefox, Go to settings and click “Open Proxy Settings”. Type localhost in the socks proxy column and the specified port number.
Whenever the address is typed in the URL bar, it will be sent to the port number specified through SSH Tunnel and received on our home system.
Conclusion
Tunneling and Port Forwarding can be used to access network traffic across firewalls securely. SSH Tunnels makes sure that the data in transit travel through a secure tunnel so that it can’t be eavesdropped on or captured. It also allows you to set up VPN connections and access the data anonymously or from a secure or inaccessible location due to a firewall. The article discusses different scenarios that require the use of a mechanism that helps access desired resources locally or remotely through Rinetd, Ngrok, and SSH Tunneling.