Many important applications like database servers, web servers, file transfer services, etc., use dedicated ports. To harden the security of system/servers, system administrators usually secure these ports by either denying access to them by unknown users/services or changing the default port number to some other value.
In computer networks, knowledge of port management is a very vital task for administering server security. This guide will study various methods of analysing a port on a Linux Ubuntu 20.04 system.
What will we cover?
In this guide, we will use the following tools for analysing ports on our Ubuntu server.
- Telnet
- Nmap
- Netcat
We will use a Ubuntu server to act as a remote server and Fedora 34 workstation as a client machine to connect to the server. Let’s get started now.
Prerequisites
- User account with ‘sudo’ access.
- Basic knowledge of computer networking.
- Internet access
1. Using the Telnet command to check for open port
TELNET is a client/server application for remote login to a server with virtual terminal capability across a network. It uses TCP’s port number 23 over a TCP/IP network. RFC 854 defines the specification for the TELNET protocol.
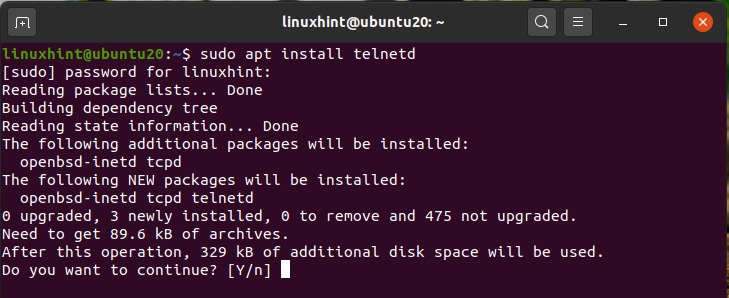
To install the TELNET server on our Ubuntu server, use the below command:
‘telnetd’ daemon is a telnet server program that is started by the inetd daemon.
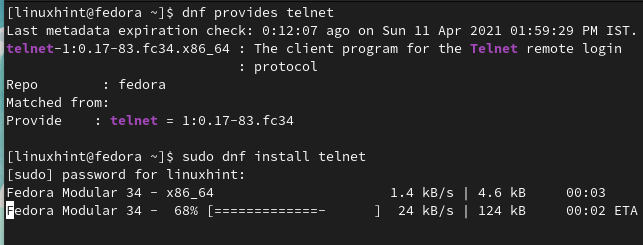
We will use the Fedora 34 workstation as a telnet client. To install telnet client on Fedora, use the command:
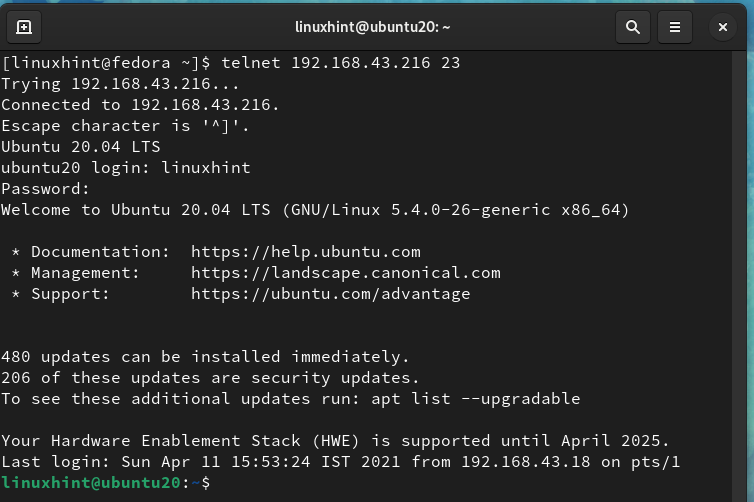
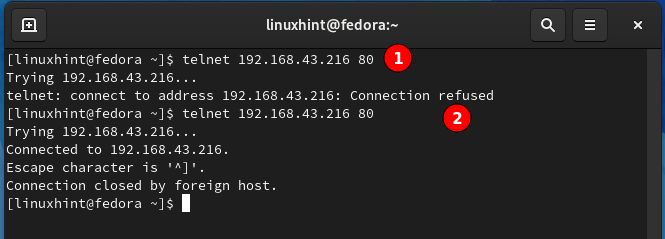
Now we will use the telnet client on Fedora 34 to check for open ports on the Ubuntu system running the telnet server. Go to Fedora 34 workstation and open up the terminal and type the command:
Here ‘192.168.43.216’ is the IP of the Ubuntu server and ‘23’ is the default port for the telnet daemon running on this server.
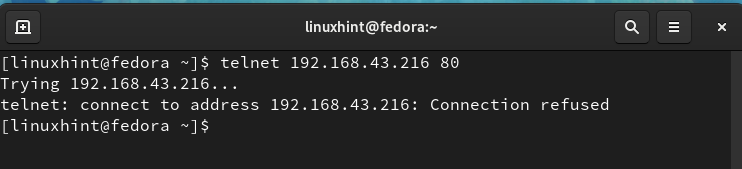
A successful login means that port 23 is an open port on our Ubuntu server. Now let us try another port number ‘80’ with telnet:
We can see that port 80 is not open for making a telnet connection; hence it is closed right now.
Let us install the Apache webserver on the Ubuntu server. Apache, by default, uses port 80 for its http services. Again run the command:
From label 2 in the above figure, port 80 is now listening and open for http connection but closed for other types of connection.
Telnet does not provide encryption for the data being transferred; the password will be transmitted in plain text format.
2. Using Nmap to check for open port
Nmap is one of the most popular and advanced network scanner tools. It is open-source and freely available for Unix and Windows systems. NmapFE is a graphical version of the terminal-based nmap command. It has a vast feature set of operations like port scanning, protocol scanning, OS fingerprinting (OS detection), etc.
Let us install Nmap on our Fedora 34 client machine and scan for the ports on the Ubuntu server. To install nmap on Fedora 34, use the command:
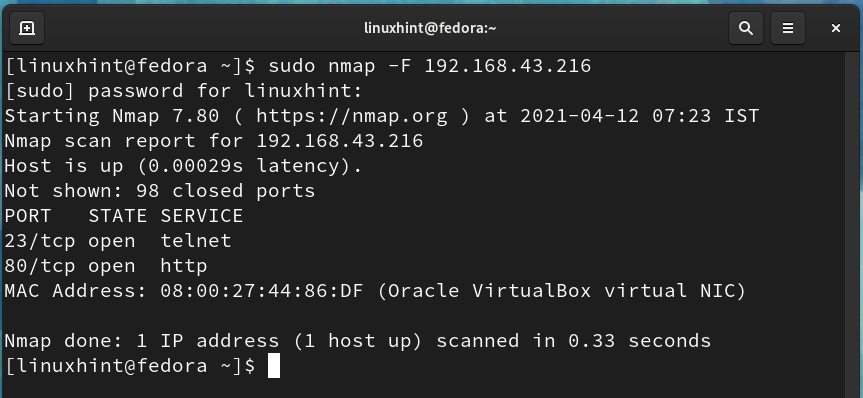
After installing Nmap, open a terminal on the Fedora system and scan for the ports using:
For e.g., in our case, the IP of the remote server (Ubuntu) is 192.168.43.216, so the command will be:
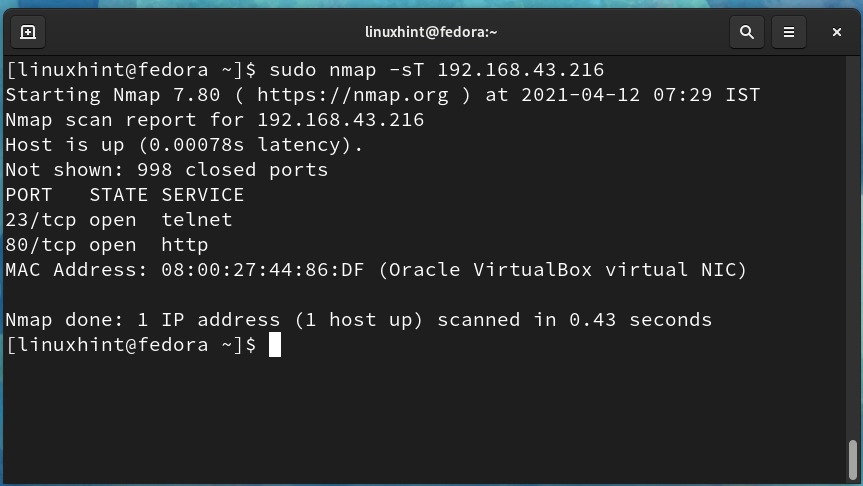
The output of the above command shows that port 23 and port 80 are in an open state. We can also use the below command for open port detection:
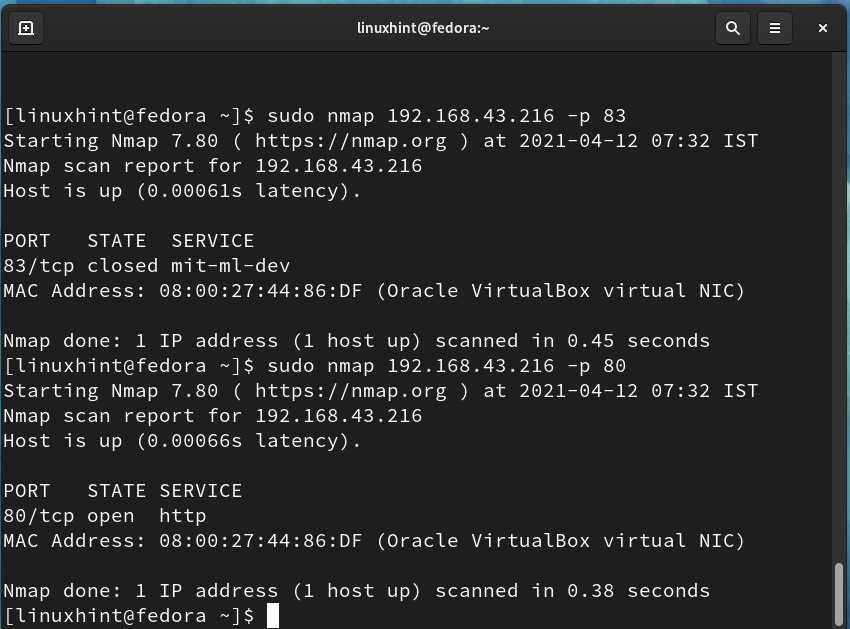
With Nmap, we can also check for a specific port status. To check the status of port 80 running apache service and a random port 83, use the command:
$ sudo nmap 192.168.43.216 -p 80
From the above picture, port 83 is closed, and open port 80 is open for listening to apache http requests.
3. Using the nc (netcat) command to check for open port
Netcat is another tool that can be used for port scanning. It can also be used for opening TCP connections, sending UDP packets, etc. Netcat comes shipped with nmap:
To check a port using netcat, run the following command:
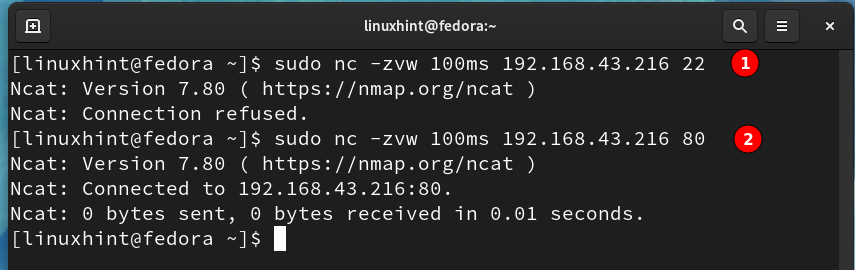
For example, to check port 22 and port 80, we will use:
$ sudo nc -zvw 100ms 192.168.43.216 80
We can see that port 22 is closed as the connection is refused. In the case of port 80 netcat connection is successful because Apache is installed on the Ubuntu server.
Conclusion
In this guide, we have explored various methods of port scanning on a remote system. Please be cautious while running these commands because scanning other networks without their permission is a legal offense.