- They produce hash values that are practically impossible to invert. Hence, they are unique. It is computationally impossible to find two files with the same MD(message digest) value.
- If we slightly change the original message, the new MD value will significantly change.
There are many message digest algorithms, such as MD2, MD4, MD5, SHA, and SHA-1. The MD series was developed by Ronald Rivest. In 1993, NIST and NSA introduced the SHA and further revised it in 1995. The SHA-1 algorithm is a 16-bit message digest and is a successor of SHA. For 128, 192, and 256-bit message digest, SHA-256, SHA-384, and SHA-512 are used.
Comparison of Variants of SHA
Although SHA is slower as compared to MD5, it is more secure. Many companies have abandoned the use of SHA-1. Since it is vulnerable to Collision Attacks, SHA-2 comprises SHA-256, SHA-384, and SHA-512 appears as the successor of SHA-1. It is considered more secure than SHA-1. Most organizations are now deploying SHA-256.
Here, we have listed the SHA variants:
SHA-256 — generates a digest of 32 bytes
SHA-384 — generates a digest of 48 bytes
SHA-512 — generates a digest of 64 bytes
Hands-On With the Shasum Command
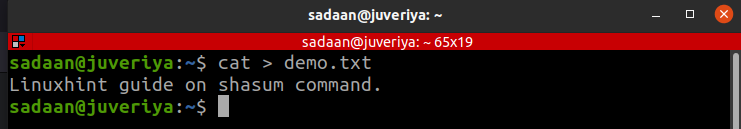
Let us now turn our attention to the ways of using shasum. Let us create a new file and apply various shasum operations to it.
We are using the “cat” command to create and insert a sample text to it:
With our demo file ready, we will now perform the different shasum operations:
1. To calculate the SHA checksum for a file, use the format:
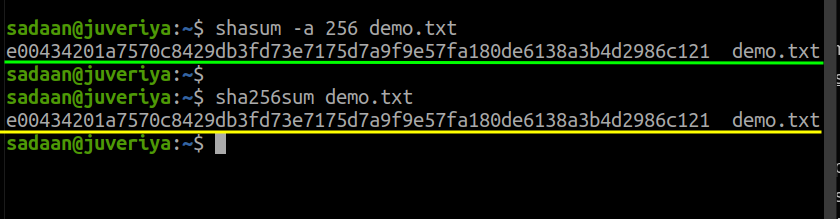
By default, the previous command generates a sha1sum. So for our demo.txt file, the following two commands will generate the same checksum value:
$ sha1sum demo.txt
As you can see in the previous image, both the checksums are the same.
2. To calculate SHA checksum for algorithms beside the sha1sum, use the “-a” option and specify the SHA to use. For example, to use SHA-256 with the demo.txt, the command will be:
Alternatively, we can also use:
Similarly, we can specify other variants of SHA.
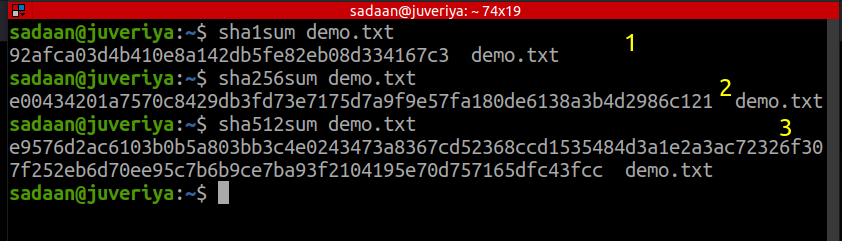
3. The size of checksum value keeps on increasing as we go higher on SHA variants. For example, consider the three checksum values for demo.txt with SHA-1, SHA-256, and SHA-512:
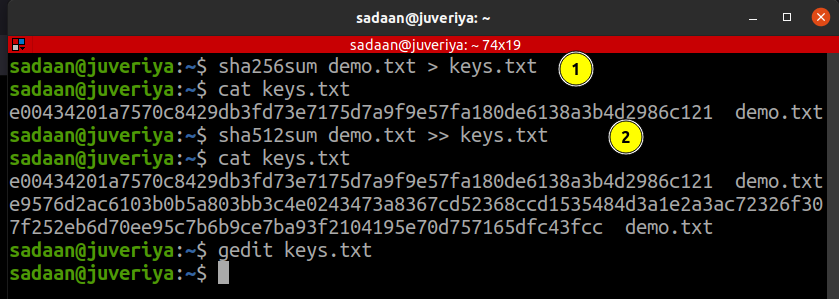
Therefore, it is a good idea to save these values to some files. It is very easy to accomplish this by simply modifying the previous commands as:
Verify the contents of the file using the cat command:
In the same way, we can save multiple values to the previous file. For example, to add a SHA-512 value, modify the previous command as:
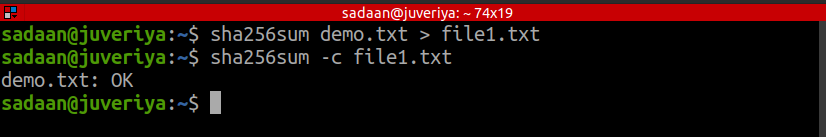
4. Verifying the integrity of a file: We can check if a file has been modified or not by looking at its sha checksum value. For our demo.txt file, create a checksum value and save it by using:
Now, check the integrity of the demo.txt file by running the following command:
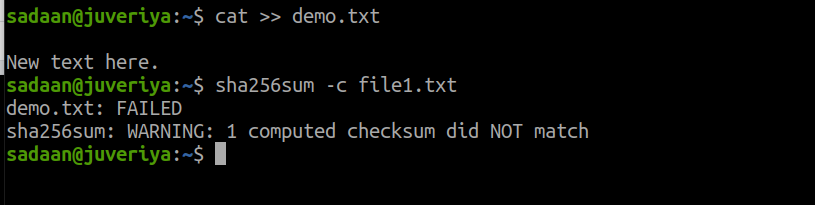
Till now, the file is intact and not modified. Now, let us append some data to the demo.txt:
Now, check the file integrity:
Now, the integrity check has failed for the file as it is modified.
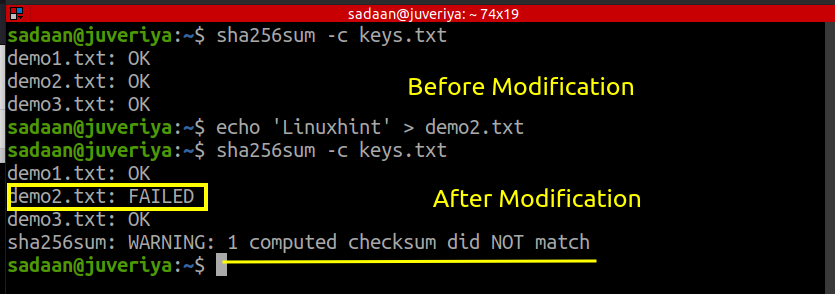
4. Checking the integrity of several files from a file containing their SHA checksums. Now, we will store the SHA sum values of different files in a common file and check for their integrity. Create the following three files: demo1.txt, demo2.txt, and demo3.txt.
Now, generate SHA256 sum values for each and store them in a file “keys.txt”.
Now, run an integrity check for the previous files:
Let us modify demo2.txt by adding some text to it and rechecking the integrity:
$ sha256sum -c keys.txt
We can see the checksum failed for the file demo2.txt after modifying it.
5. We can also use the text mode by using the “-t” option. In this manner, we can generate the SHA value for text on the console.
Now, enter the text and press “Ctrl+d” when you are finished.
Conclusion
In this guide, we discussed how to use the “shasum” command to check the integrity of a file. We have also covered the message digest and a brief comparison of variants of SHA. More information about shasum can be found on the man pages. We hope you found this article helpful. Check out other Linux Hint articles for more tips and information.