Introduction
SELinux is a mandatory access control (MAC) module residing in the kernel level of linux systems. It’s a joint development of Redhat and NSA released around 1998 and still being maintained by an enthusiast community. By default, Ubuntu uses AppArmor and not SeLinux, which is similar in terms of performance but rather popular in terms of simplicity. However, SeLinux is known to be quite secure due to the involvement of a government agency. SELinux is an open source application which protects the host by isolating each application and confining its activities. By default, processes are blocked from doing any activities unless the explicit permission is granted. The module natively provides two global level management rules: Permissive and Enforcing which respectively logs each violated rule, and denies access to a particular request sent from a process. This tutorial demonstrates how to use it on Ubuntu with ease.
How to Install and Enable
SeLinux is a very tricky application to install, because if it’s not properly configured prior to the first reboot, it will make the entire operating system unbootable, meaning anything beyond the initial booting screen will be virtually unreachable by normal means.
Also as stated earlier, Ubuntu already has a sophisticated high level mandatory access control system known as AppArmor, and therefore it has to be disabled prior to installing SeLinux to avoid any conflicts. Use the following instructions to disable AppArmor and Enable SeLinux.
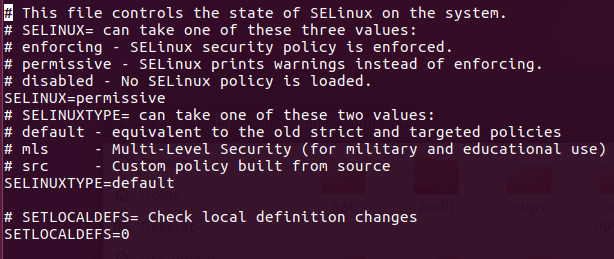
sudo /etc/init.d/apparmor stop apt-get update && upgrade –yuf apt-get install selinux nano /etc/selinux/config ‘set SELINUX to permissive, SELINUXTYPE to default’ reboot
This file config can be opened with any text editor to make changes. The reason for assigning permissive rule to SETLINUX is making the operating system accessible while leaving SeLinux enabled. It’s highly recommended to use the permissive option as it’s hassle free, but it logs violated rules set in SeLinux.
Available Options
SELinux is a complex and a comprehensive module; hence it contains a lot of the features and options. That being said, most of these options may not be useful for everyone due to their exotic nature. The following options are some of the basic and useful options in this module. They are more than enough to get SELinux up and running.
Check the status: The status of SELinux can be checked directly through the terminal window, which shows the basic information like whether SeLinux is enabled, SELinux root directory, loaded policy name, current mode etc. After rebooting the system after installing SeLinux, use the following command as root user with sudo command. If it states SeLinux is enabled in the status section, it means it’s up and running in the background.
root@ubuntu:/home/dondilanga# sestatus
Change The Global Permission Level: The global permission level states how SELinux behaves when it stumbles upon a rule. By default, SeLinux sets itself to enforcing which effectively blocks all the requests, but it can be altered to permissive which is kind of lenient towards user as it allows access, but logs any violated rules in its log file.
nano /etc/selinux/config ‘set SELINUX to permissive or enforcing, SELINUXTYPE to default’
Check the Log File: The log file which states the violated rules by each request. This only keeps logs if SeLinux is enabled.
grep selinux /var/log/audit/audit.log
Enable and Disable Policies and What Protections They Offer: This is one of the most important options in SeLinux, as it allows to enable and disable policies. SeLinux has a large number of prebuilt policies which determine whether the specified request is allowed or not. Some of the example of this are allow_ftpd_full_access which determines the ability of FTP service to log in to local users and read write all files on the system, allow_ssh_keysign which allows keys to be used when login to SSH, allow_user_mysql_connect which allows users to connect to mysql , httpd_can_sendmail which determines the ability of HTTP service to send an email etc.. In the following code example, it installs policycoreutils-python-utils which actually helps in listing out each policy in a descriptive manner, next it lists out all available policies to terminal, finally it teaches how to set a policy on or off, the allow_ftpd_full_access is the policy name as shown in the terminal returned by semanage,
apt-get install policycoreutils-python-utils semanage boolean -l setsebool -P allow_ftpd_full_access ON
Advanced Options
The advanced options are options which help in extending the functionalities in SELInux. There is tremendous amount of combinations out there due to the comprehensive nature of SeLinux, so this article lists out some of the prominent and useful ones among them.
Role Based Access Control (RBAC): RBAC allows administrators to switch to a role based way to confine the permission of applications. What it means is a user of a particular user group is allowed to execute or perform certain predefined actions. As long as the user is part of the role it’s okay. This is the same thing as switching to root when installing applications on Linux with administrative rights.
semanage login -a -s 'myrole' -r 's0-s0:c0.c1023' <username>
Users can switch their role with the following command.
sudo -r new_role_r -i
Users can also remotely connect to the server via SSH with the role enabled at the startup.
ssh <username>/[email protected]
Allow A Service to Listen to a Non-Standard Port: This is quite useful in customizing a service, for instance when a FTP port is changed to a non-standard one in order to avoid unauthorized accesses, SELinux has to be informed accordingly to allow such ports to pass through and function as usual. The following example allows the FTP port to listen to 992 port. Likewise, any service returned by semanage port –l can be replaced. Some of the popular ports are http_port_t , pop_port_t, ssh_port_t.
semanage port -a -t <port to allow> <protocol> <port number> semanage port -a -t ftp_port_t -p tcp 992
How to Disable
Disabling SELinux is easier as it’s enabled and installed. Basically there are two ways of disabling it. Either temporarily or permanently. Disabling SeLinux temporary makes it disable for a while until the next boot, and as soon as the computer is turned on again the state is restarted. On the other hand, the permanent disable of SeLinux shuts it down completely exposing it to threats out there; hence it’s a wise choice to restore Ubuntu’s default AppArmor at least for the sake of security of system.
The following command on the terminal turns it off temporarily:
setenforce 0
To permanently disabled edit /etc/selinux/config and set SELINUX to disabled.