In this article, we will learn how to enable and enforce secure password policies on Ubuntu. Also we will discuss how to set a policy that enforce users to change their password at regular interval.
Note that we have explained the procedure on Ubuntu 18.04 LTS system.
A strong password should contain:
- Upper case letters
- Lower case letters
- Digits
- Symbols
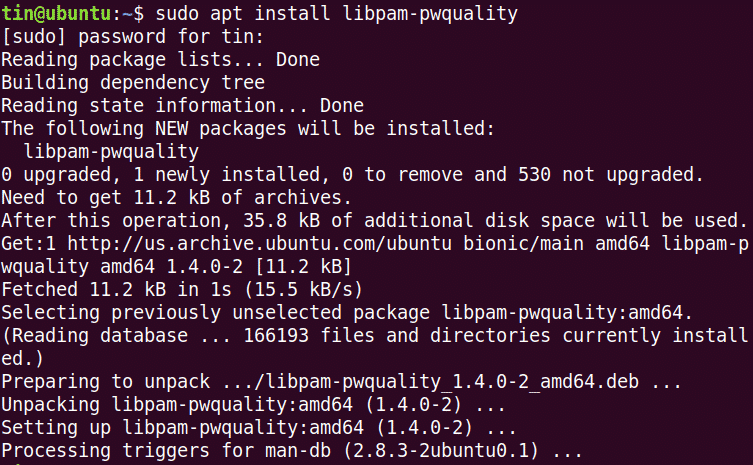
To enforce a secure password policy in Ubuntu, we will use the pwquality module of PAM. To install this module, launch the Terminal by using Ctrl+Alt+T shortcut. Then run this command in Terminal:
When prompted for the password, enter the sudo password.
Now first copy “/etc/pam.d/common-password” file before configuring any changes.
And then edit it for configuring password policies:
Look for the following line:
And replace it with the following:
pam_pwquality.so retry=4 minlen=9 difok=4 lcredit=-2 ucredit=-2 dcredit=
-1 ocredit=-1 reject_username enforce_for_root
Let’s see what the parameters in above command mean:
- retry: No. of consecutive times a user can enter an incorrect password.
- minlen: Minimum length of password
- difok: No. of character that can be similar to the old password
- lcredit: Min No. of lowercase letters
- ucredit: Min No. of uppercase letters
- dcredit: Min No. of digits
- ocredit: Min No. of symbols
- reject_username: Rejects the password containing the user name
- enforce_for_root: Also enforce the policy for the root user
Now reboot the system to apply the changes in the password policy.
Test the secure password policy
After configuring the secure password policy, it’s better to verify whether it is working or not. To verify it, set a simple password that does not fulfill the above configured secure password policy requirements. We will check it on a test user.
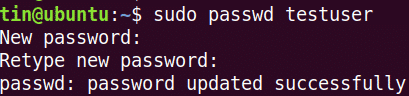
Run this command to add a user:
Then set a password.
Now try to enter a password that does not include:·
- Uppercase letter
- Digit
- Symbol
You can see none of the above-tried passwords has accepted, as they do not meet the minimum criteria defined by the password policy.
Now try adding a complex password that meets the criteria defined by the password policy (Total length: 8 with Minimum:1 uppercase letter, 1 lowercase letter, 1 digit and 1 symbol). Let’s say: Abc.89*jpl.
You can see that the password has now accepted.
Configure password expiration period
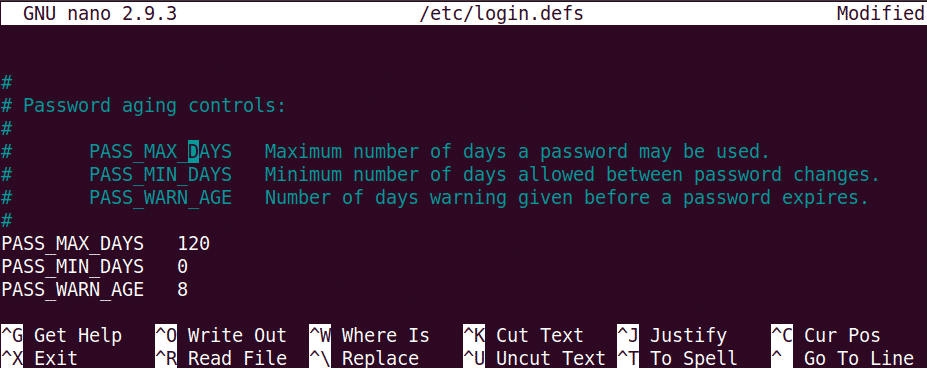
Changing the password at regular interval helps limits the period of unauthorized use of passwords. Password expiration policy can be configured through “/etc/login.defs” file.Run this command to edit this file:
Add the following lines with values as per your requirements.
To use chage command, syntax is:
Note: To execute the chage command, you must be the owner of the account or have root privilege otherwise, you will not be able to view or modify the expiry policy.
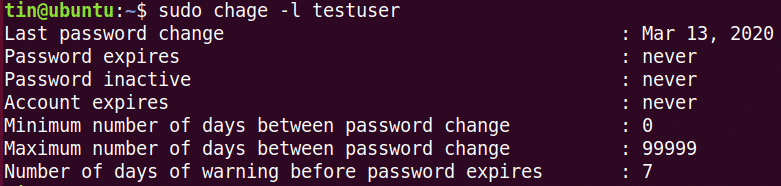
To view the current password expiry/aging details, the command is:
To configure the maximum No. of days after which a user should change the password.
To configure the minimum No. of days required between the change of password.
To configure warning prior to password expiration:
That is all there is to it! Having a policy that enforces users to use secure passwords and change them regularly after some interval is necessary to ensure system safety and security. For more information regarding the tools discussed in this article, such as pam_pwquality and Chage, see their man pages.