PowerShell is a scripting language that provides task configurations and operations management. It is easy to use as well as having full control of the Microsoft Windows system. Hackers can use this to gain control of the system. However, users cannot avoid using PowerShell as it provides an interface for system administration.
This guide provides the most efficient way for securing PowerShell scripts.
How to Secure PowerShell Scripts?
Users can secure data by encrypting scripts on PowerShell. It balances the requirement using PowerShell and security issues with its usage. Encrypted data is not easy to read and understand so it secures scripts from attackers.
Step 1: Run PowerShell Script
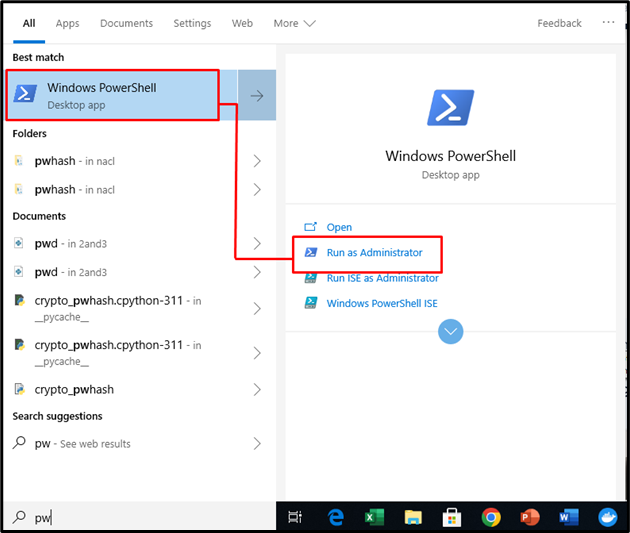
Initially, search for the Windows PowerShell through the Strat menu and hit the Run as Administrator:
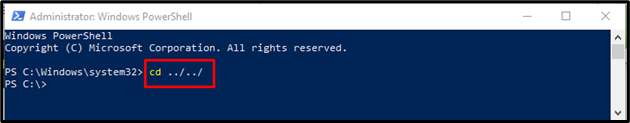
Step 2: Specify Location
Then, navigate to the particular script by specifying the location. User can create their folder in any other location:
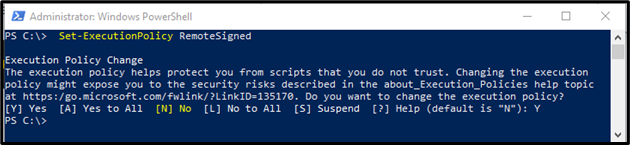
Step 3: Set Execution Policy
Then, set the computer’s execution policy using the following command and press Y to confirm the policy change:
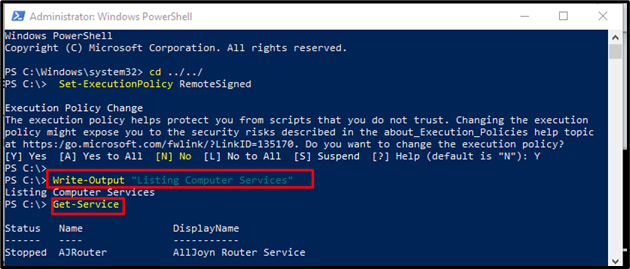
Step 4: Run PowerShell Scripts
To run PowerShell scripts, the user requires the script file inside “Get-Service”. For that purpose, execute the provided commands:
Get-Service
Step 5: Run Script
Move to the particular location where you stored your files, execute it, then the script files output will be displayed on the terminal:
.\myfirst.ps1
Encryption of Scripts
Scripts can be secured in PowerShell by using the below-mentioned steps.
Step 1: Open the Script File
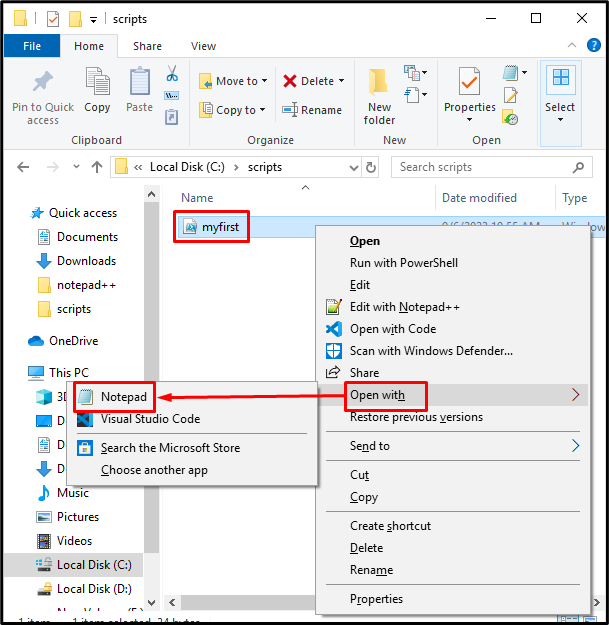
Open the script file with your desired text editor. In our case, we have opened it with “Notepad”. Users can edit and save files:
Step 2: Creation of Text File
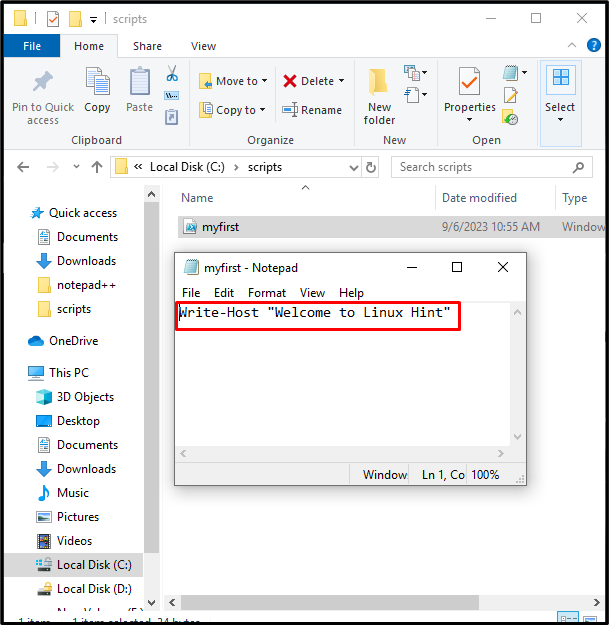
Select all the existing data from the script file and copy it into a new simple text file. Here, we have added in the “myfirst.txt” file:
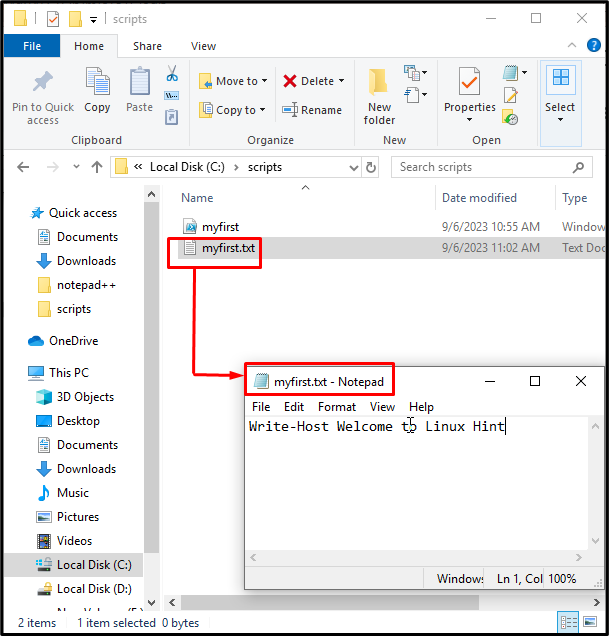
Step 3: Check the Text File
Open the “myfirst.txt” file and it will be identical to the “myfirst” file the only difference is it is saved in text format:
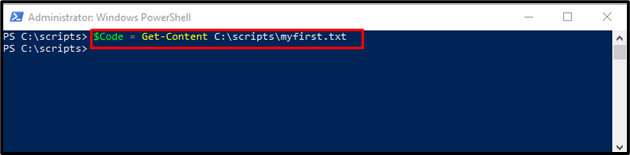
Step 4: Assigning Variable
Next, save the content of the text file(myfirst.txt) in the code variable:
Step 5: Display File Content
To display content that is stored, use the variable:
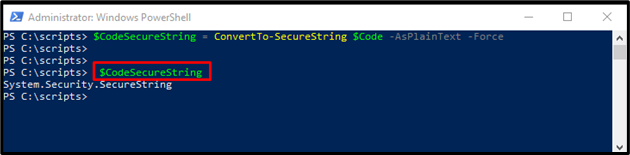
Step 6: Generate Secure String
Now, convert the content stored in the code into a secure string. Afterward, content stored in CodeSecureString will be hidden:
$CodeSecureString
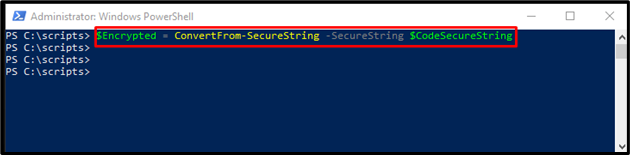
Step 7: Assign Variable
Next, the string that we have stored in the secure string variable named “Encrypted”:
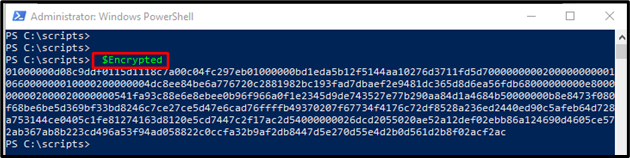
Step 8: Display Secure String
Print the secure string stored in the variable named “Encrypted”:
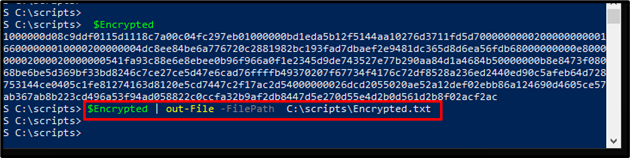
Step 9: Saving Secure String in Variable
Users can save the secured string in a text file named Encrypted.txt:
Decryption of Scripts
Scripts can be decrypted to ensure changes and use them further.
Step 1: Open Script File
This script file contains all the steps that we have completed previously, compile it again:
Step 2: Extraction of Files
We have obtained an Encrypted.txt and Runcode.ps1 file by running the above script so open Runcode.ps1 with Notepad:
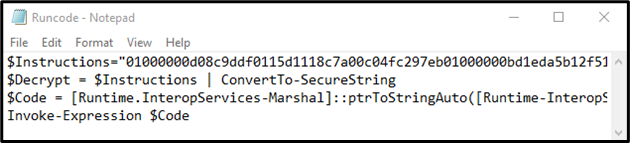
Step 3: Copy Data
Copy the secure string from the Encrypted.txt file and enter the instructions variable:
Step 4: Decrypting Script
Run the script file, the decrypted data will be displayed on the terminal:
Conclusion
In PowerShell are assigned to variables and then converted into a string named a secure string. Securing scripts using encryption is a common technique. It is very easy to change the script to the original type by decrypting the encrypted script. This blog provided detailed information about the secure PowerShell scripts.