Imagine you must remember the IP address of each website or service you want to connect to; that’s why DNS is described as a translator or a phonebook that finds the IP address of domain names or hosts.
For example, when someone creates a new website, he needs to update the DNS records with the server’s IP address the new domain will be hosted at.
Now let’s assume someone migrated his server; he doesn’t document data on the previous server, even not its IP address. For some reason, he must point the domain name back to the old IP server, but he doesn’t know the old IP address. He can search the DNS history; several resources are described in this tutorial to research DNS history for an IP address or domain name. This tutorial shows how to research the target DNS history using Spyse and SecurityTrails.
On DNS records:
A Record: this record links to the server (IPv4)
AAA Record: this record links to the server (IPv6)
MX Record: this record specifically links to mail servers.
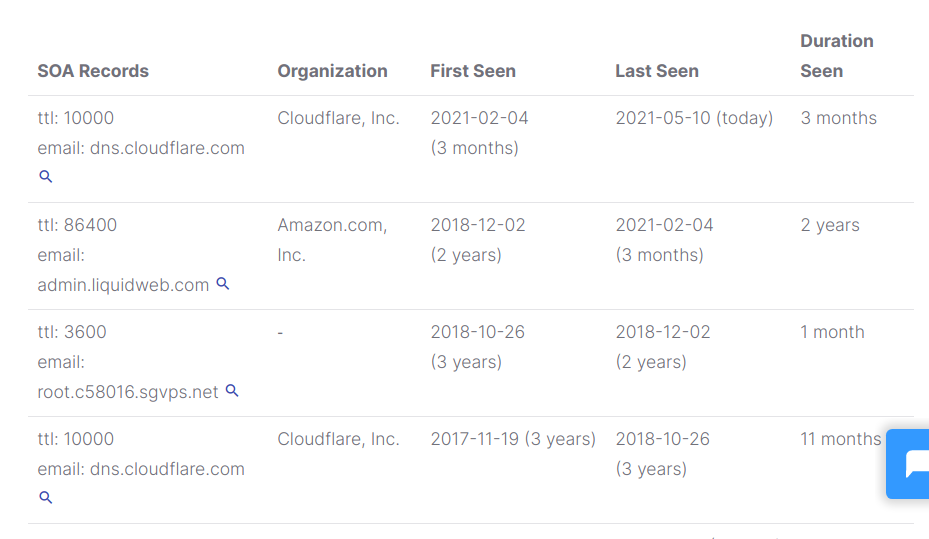
SOA Record: this record shares zone transfer information.
NS Record: Specify the servers sharing information for DNS.
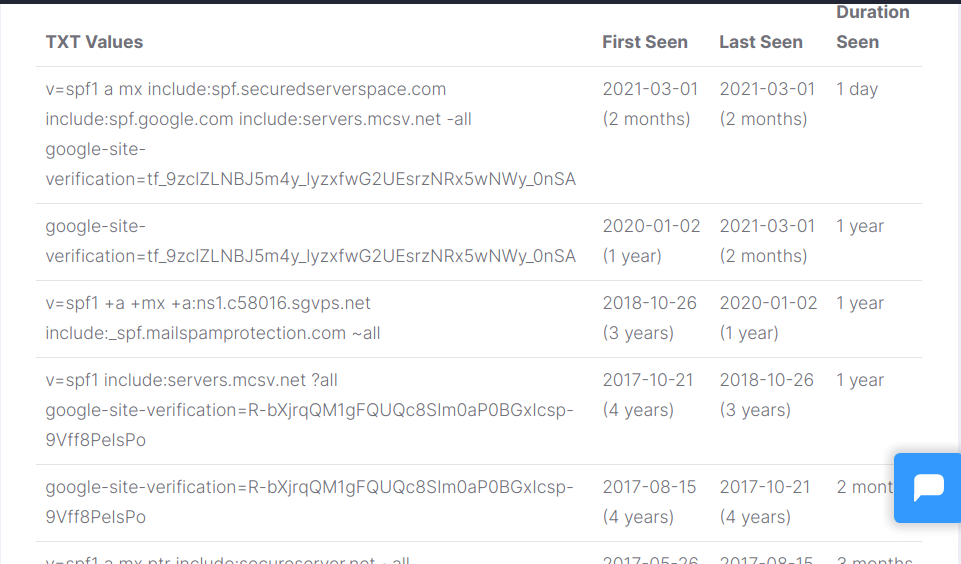
TXT Record: Mostly used to verify ownership on domain names, SPF records, etc.
You can read more on DNS here.
Searching DNS history using Spyse:
Spyse is described as “… a search engine built for a quick cyber intelligence of IT infrastructures, networks, and even the smallest parts of the internet.”. It offers a lot of free multipurpose tools.
Spyse includes a DNS history search engine which will be used for the first example in this tutorial.
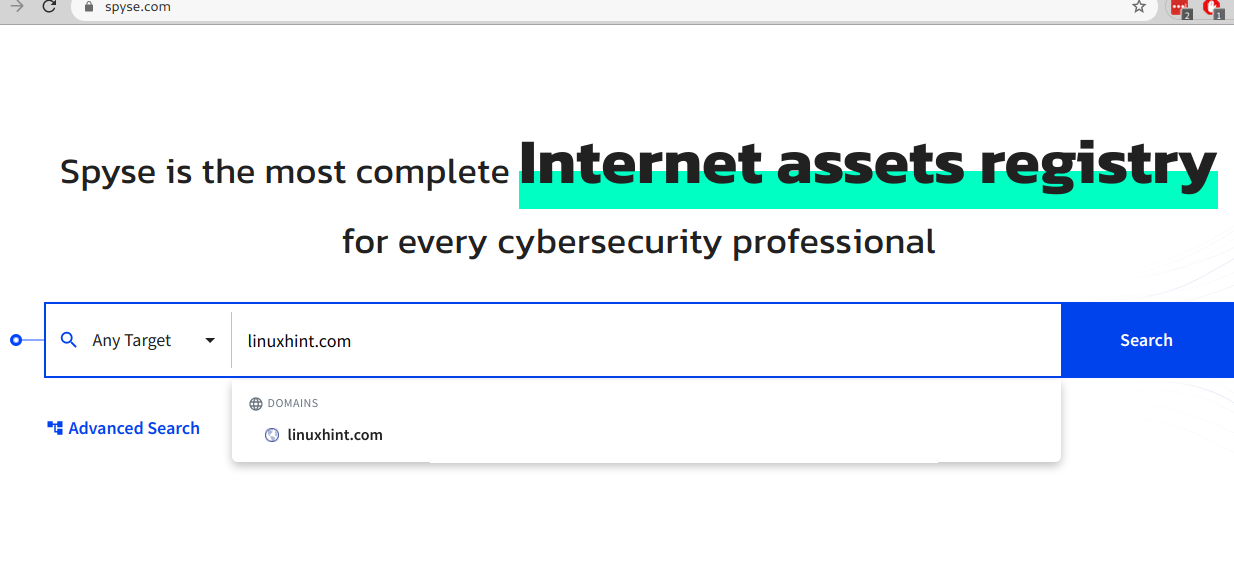
To start, visit https://spyse.com/ and write the domain name or IP address you want to research, as shown in the screenshot below, and press on the blue Search button.
The next screen will display a left menu with the option DNS History (6° item); press it.
DNS History displays a table with 5 tabs, one for each DNS record type: A, AAA, MX, NS, and TXT. Each tab contains a table with information on the specific record.
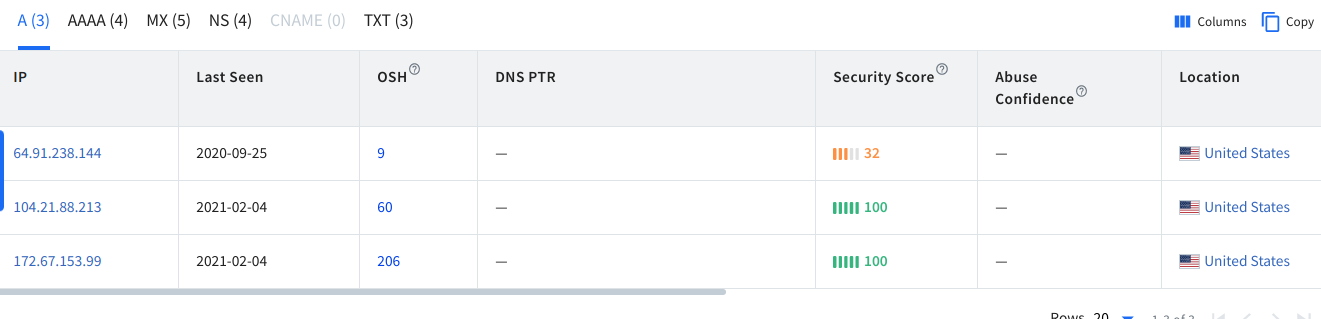
The first tab (A records) contains a table with 11 columns:
IP: This column contains the server’s IP history.
Last seen: This column shows when a server was migrated.
OSH: (On the Same Host) – Total number of hosted domains on the same IP.
DNS PTR: A DNS pointer record (PTR) shares the domain name associated with an IP address. A DNS PTR record is exactly the opposite of the “A” record, which provides the IP address associated with a domain.
Security core: Security Score analyzes found vulnerabilities and indicates a lower or higher risk level of the potential attacks.
Abuse Confidence: The level of confidence that the IP or host is involved in abusive activities.
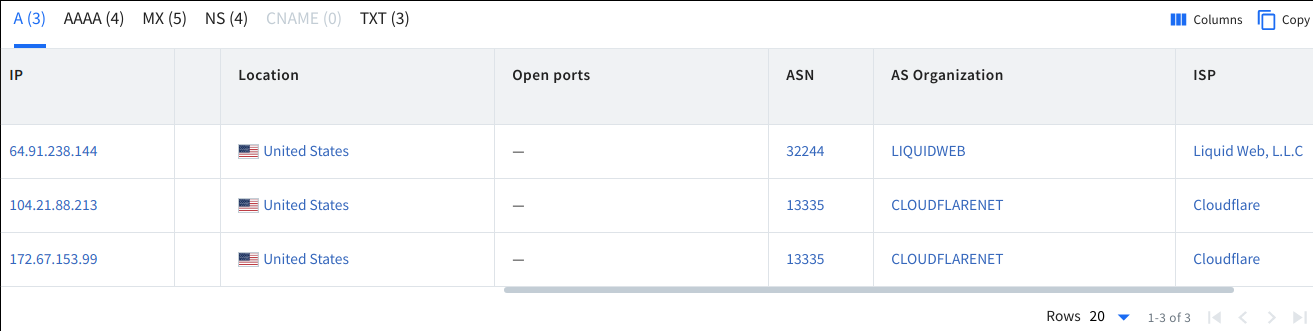
Location: IP or host location.
Open ports: Information on ports if available.
ASN: ASN lookup serves to stretch out recon flexibility for analyzing organizations’ autonomous systems.
As Organization: The authority sharing the records.
ISP: Internet provider.
NOTE: The screenshot was snapped for better resolution.
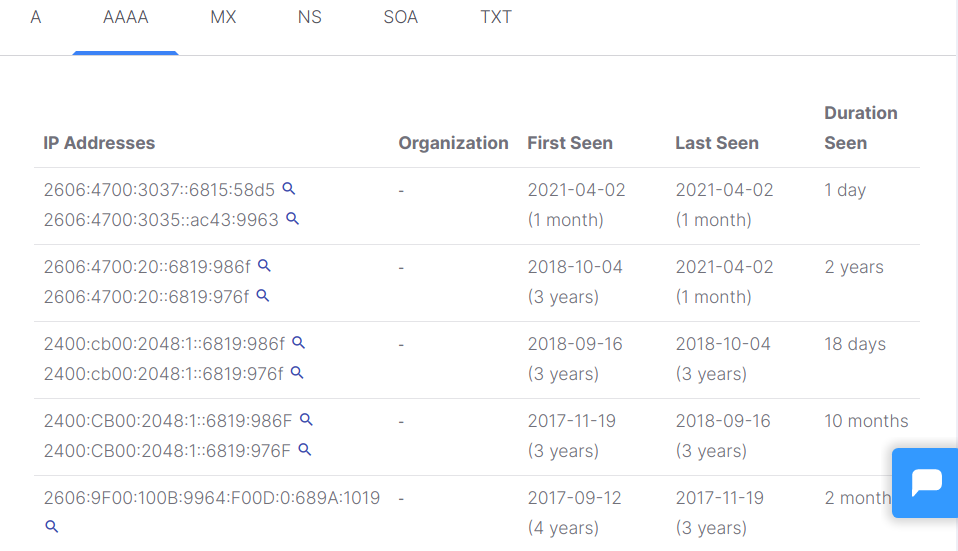
The tab showing AAA records is similar to A records but for the IPv6 protocol.
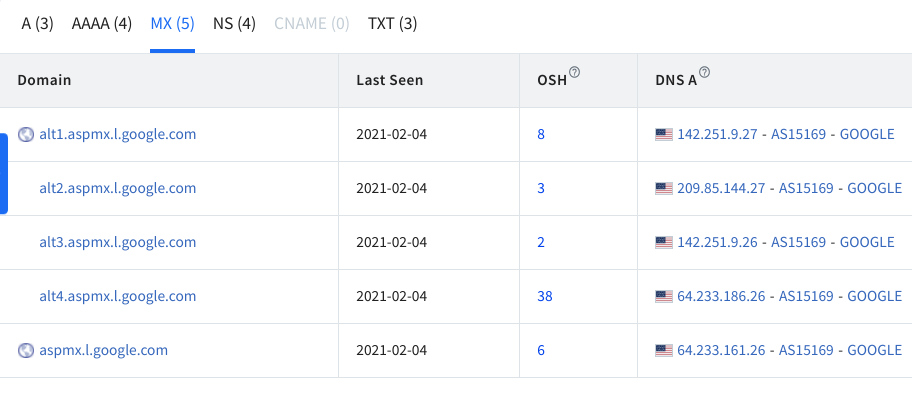
The tab MX displays information on mail servers’ history.
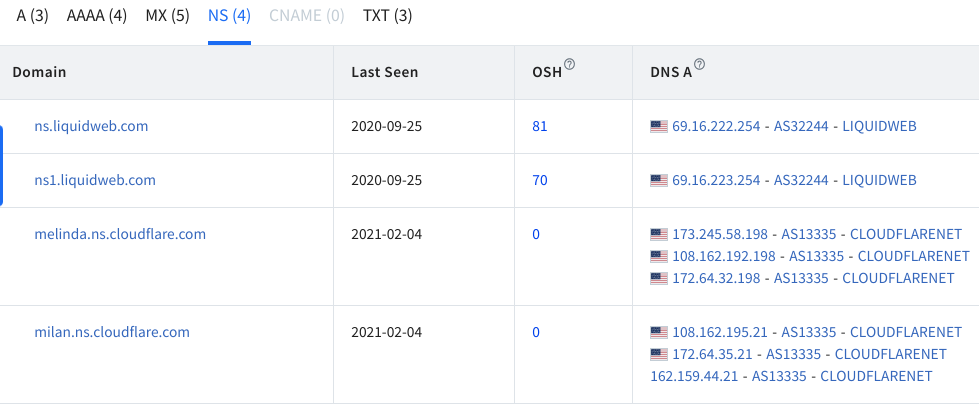
Under NS, you can find historical data about DNS servers.
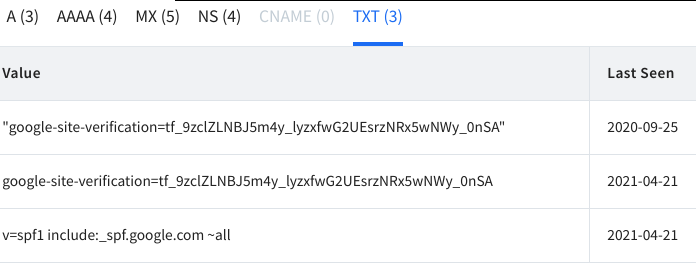
Records TXT are arbitrary, usually used to verify domain ownership.
Searching DNS history using SecurityTrails:
SecurityTrails is a company that offers historical DNS records, reverse DNS, IP blocks, domain names, associated domain names, WHOis historical data, open ports, SSL Certificate Transparency logs, and much more. This tutorial shows how to use the historical DNS records feature for free.
To start, fill the registration form at https://securitytrails.com/app/signup
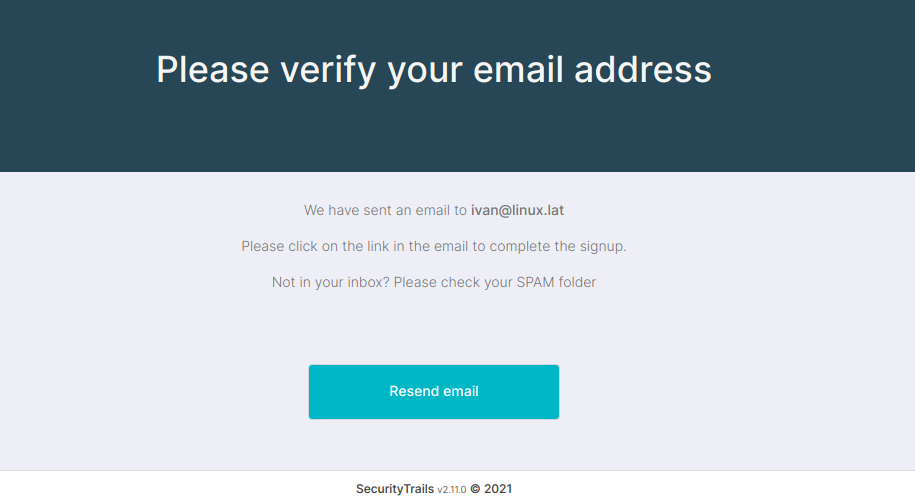
After sending the form, you’ll be asked to verify your mail address.
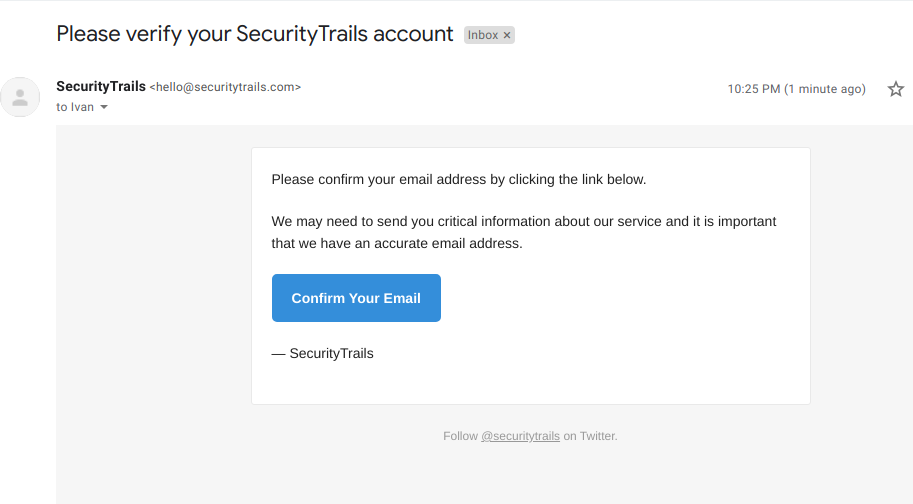
Verify your mail by clicking on the link sent to your mail address.
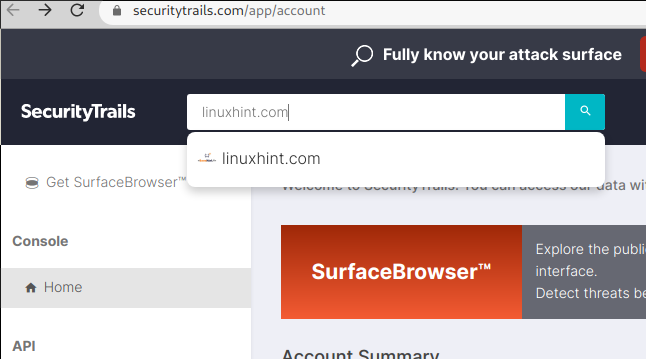
The confirmation link will redirect you to securitytrails.com. In the search box on the top, write the domain name, IP address, or host you want to research:
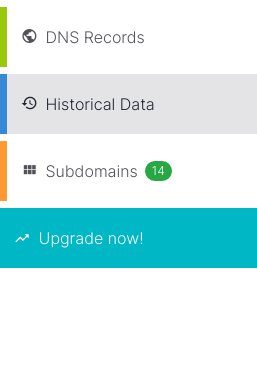
The next screen contains a left menu; Historical Data is the second item you need to click on.
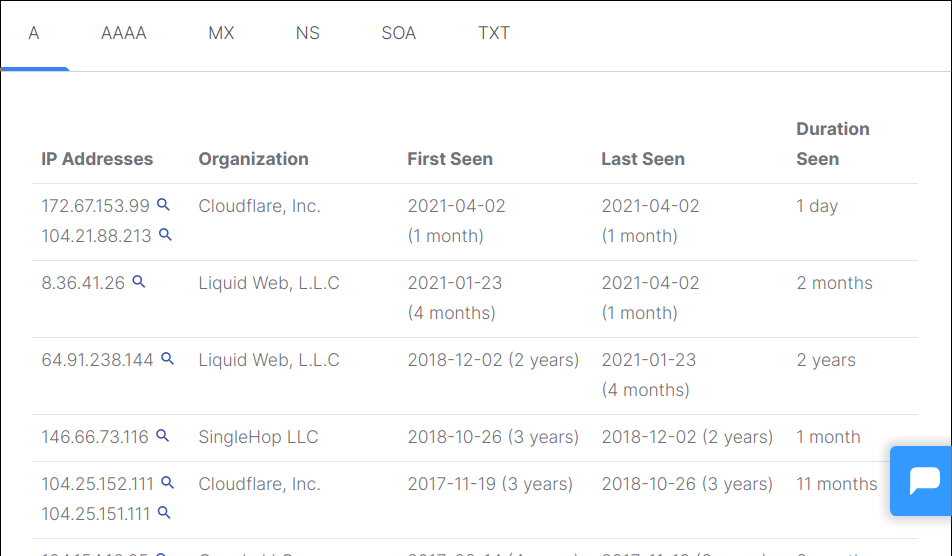
The main screen will display a table with columns A, AAA, MX, NS, SOA, and TXT. “A” records are displayed by default, as shown below.
As you can see, all records contain historical data on IP addresses, when the record appeared and when it disappeared if the site was migrated to a different server.
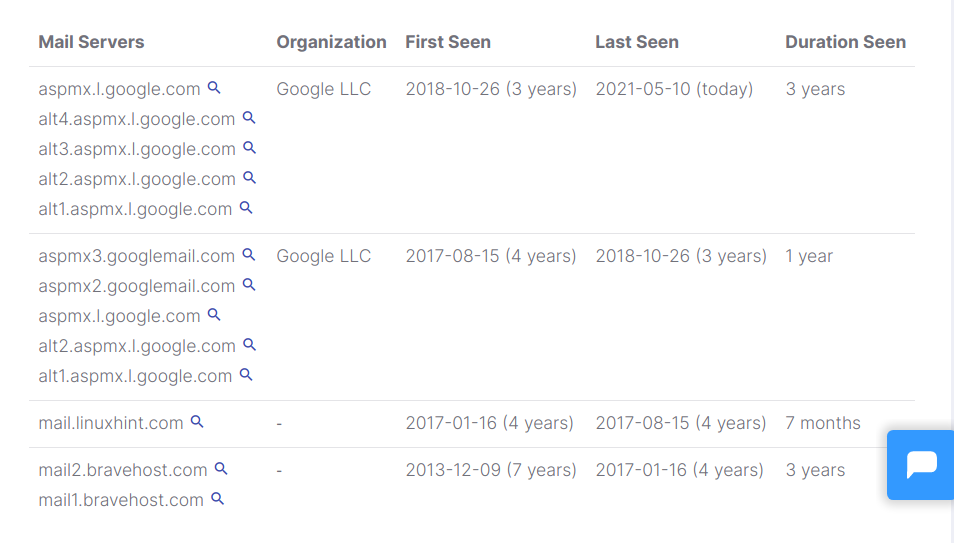
The column Mx shows mail servers’ DNS history; we see Linux Hint started using Bravehost in 2013 and migrated to Google servers.
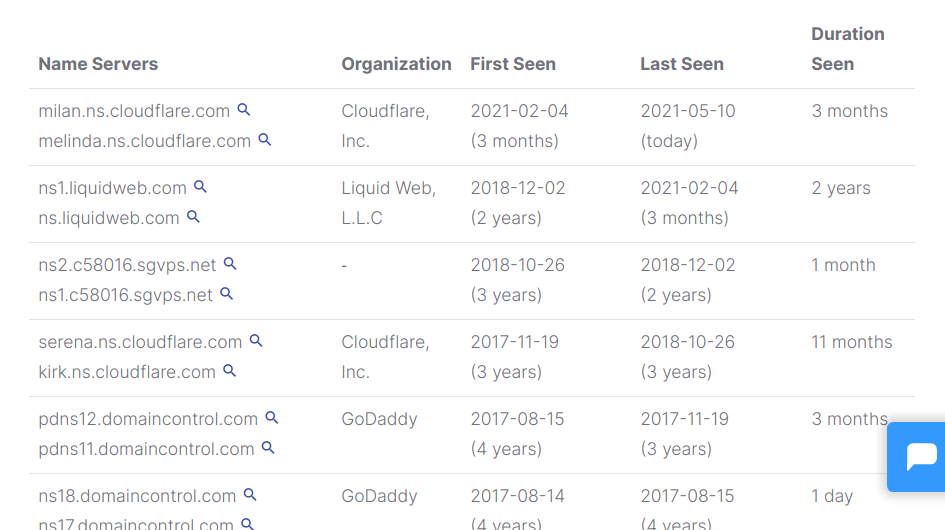
The NS column should display DNS servers; you can see Linux Hint uses Cloudflare since 3 years ago.
The SOA record will display contact information on different authorities responsible for sharing the DNS information.
The last column shows txt records, usually for domain verification or spf records.
Conclusion:
Both Spyse and SecurityTrails are very useful free tools for DNS history research. Spyse is faster to access because it doesn’t require registration. Both platforms have additional interesting features related to data research, pen-testing, and more. Both tools are simple and intuitive with sophisticated AI algorithms.
I hope you found this article on DNS history research useful. Keep following Linux Hint for more Linux tips and tutorials.