You can get a free TLS/SSL certificate when you have a server using the Let’s Encrypt CA service. Let’s Encrypt lets you use Certbot, a software client, to secure your HTTP traffic via HTTPS, such that even when someone uses http://your-domain, their traffic will get redirected via HTTPS. So, how do you use Certbot to redirect HTTP to HTTPS? Let’s dig in!
Using Certbot to Redirect HTTP to HTTPS
A web server like Nginx allows HTTP traffic despite being configured to encrypt the traffic using the assigned certificate. To secure such a scenario, you should redirect all the HTTP traffic of your server to tunnel through HTTPS, and that’s possible using Certbot.
To use Certbot to redirect traffic, you must have a registered domain for your server. The domain will be added when executing the Certbot command to redirect the traffic using a web server of your choice. Moreover, the DNS records on your server should have a record pointing to the server’s public IP address.
First, let’s see how to install Certbot on Ubuntu 22.04.
Access your server running your website, then ensure you have snapd installed and updated using the following commands:
$ sudo snap refresh core
Certbot recommends removing any instance of an older version you were using before installing Certbot on your server and using the following command:
Next, install Certbot as a snap package.
With Certbot installed, it’s best to create a symbolic link to it for quick access and execution.
Certbot is now ready for use. However. You must first open your web server configuration file and ensure that the server block for Nginx, which is well configured for Certbot to configure SSL automatically.
Open the Nginx configuration file for your server’s domain.
Add the server block for the domain using the following syntax:
server_name your-domain.com <a href="http://www.your-domain.com/">www.your-domain.com</a>
}
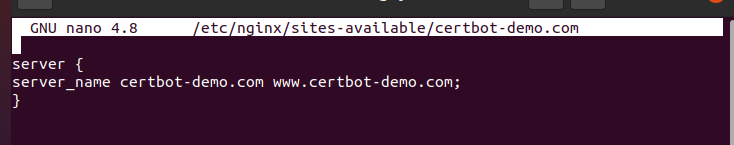
Here’s an example:
Save the configuration file, then check the status of the configuration file with the following command:
If it returns success, then reload nginx.
The next step is to configure the firewall to allow HTTPS.
Execute the following command:
At this point, you can invoke Certbot to provide an SSL certificate using its various plugins. The good news with Certbot is that it handles all the reconfiguring of your config file for Nginx to redirect HTTP traffic to HTTPS.
There are different ways you can invoke the Certbot plugin.
You can directly add the Certbot command followed by your web server.
Alternatively, you can use the -d option, then specify the domain for your server using the following syntax:
Certbot will create the SSL certificate and adjust the configurations where necessary. All that’s needed from you is to confirm the prompts and reload your website once Certbot is done.
A security indicator showing a padlock will confirm that your site’s HTTP traffic is secured.
You can test it by accessing your site’s domain using HTTP instead of HTTPS. You will note that the connection is secured as Certbot redirects HTTP to HTTPS.
Conclusion
Certbot offers plugins that facilitate redirecting HTTP to HTTPS by generating an SSL certificate and automatically editing the configuration file for your web server to redirect traffic. This guide details how to redirect HTTP to HTTPS using Certbot. We’ve covered everything from installing Certbot to using it to redirect HTTP to HTTPS.