The kernel can allocate and restrict the resources that the processes running can access through the namespaces. The namespaces create isolation, and containers only view processes. To easily work with the containers and namespaces, the nsenter Linux command is required, and we will see how to use nsenter to inspect and execute programs in the namespaces.
How to Inspect Linux namespaces using nsenter
Before we dive into using nsenter, we need to understand Linux containers and namespaces.
What are Linux Containers?
With growing technology, the demand to develop more scalable and secure applications has stretched the need to use containers. Linux containers can best be said to be a technology that allows packaging and isolating applications and resources in their runtime environment, away from the system. Besides, you can also create containers containing namespaces for different processes on your Linux system using various tools, such as podman or docker.
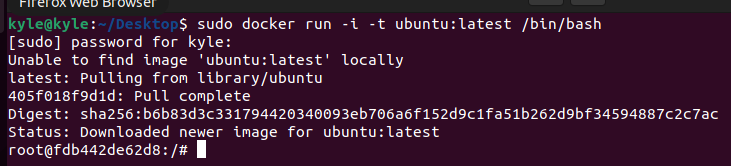
For this example, we will create a new container using docker, as shown in the image below.
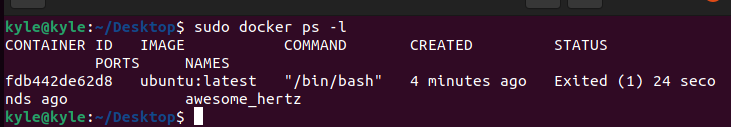
Exit the container and list the available containers from the host system. You will note that the container we created gets listed, including its container ID.
Alternatively, if you are using podman Red Hat offers a container in its catalog that you can access using the command below.
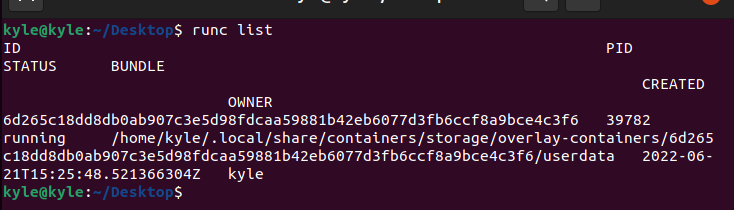
Once you have the container created, list the process id of the container created using the command below.
In the output, you should note the process id. In our case, the ID is 39782.
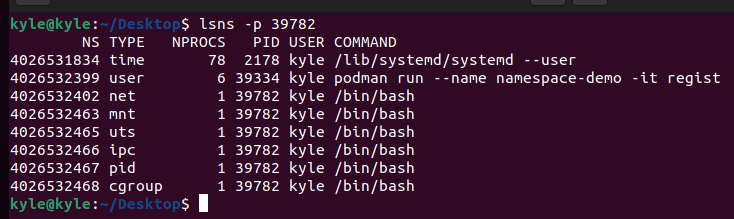
Using the process id above, you can get the namespaces associated with it using lsns or nsenter.
To use lsns, use the syntax below.
Unlike lsns, the nsenter offers more options, giving you more control.
Using nsenter with Linux namespaces
Some of the common options that you can use with nsenter include:
1. -t: this flag specifies the target process id.
2. -u: it is used to enter the process’s namespace, and if no namespace is entered, it will use that of the target process.
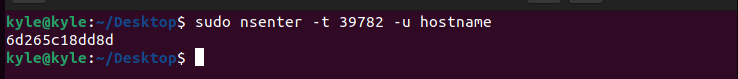
For instance, to get the hostname of the namespace with the id 39782, the command would be:
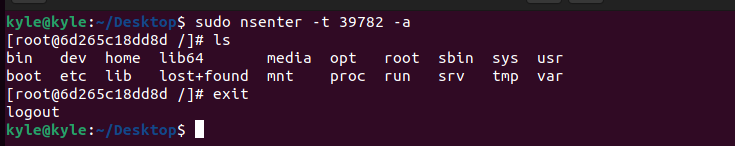
3. -a: used to enter all the available namespaces. In our case, we only have one. If we run the command below, you will note we are inside the container.
You can log out by typing exit.
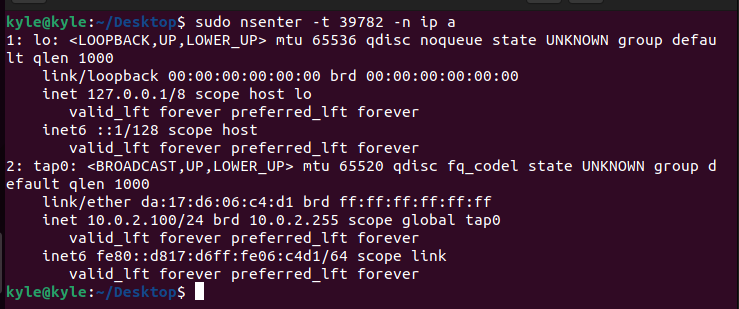
4. -n: the flag is used to enter the network namespace. Only the network information for the given namespace gets viewed.
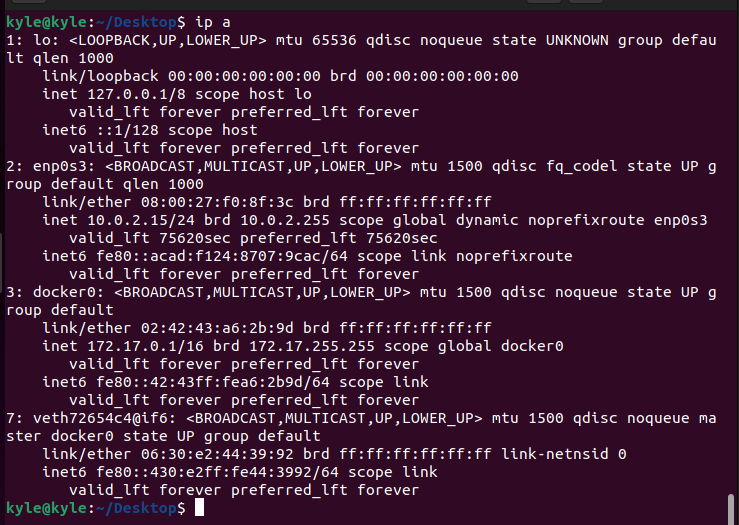
If you were to view the same network details from the complete system, you would notice that there is isolation.
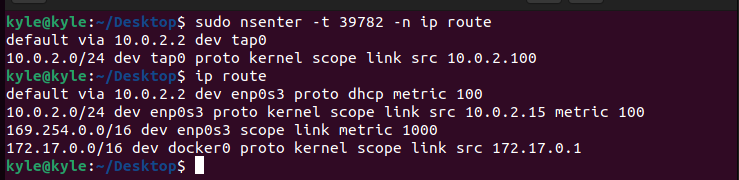
The isolation extends to the IP route, and we can also get the IP route for the namespace using the command below.
In the image above, you can notice how the first output is for the namespace of the given target process id, but the second output is the ip route for the complete system.
5. -p: using nsenter, you can also enter the PID namespace using the -p flag. For this to work, you should have the top or ps commands installed inside the container.
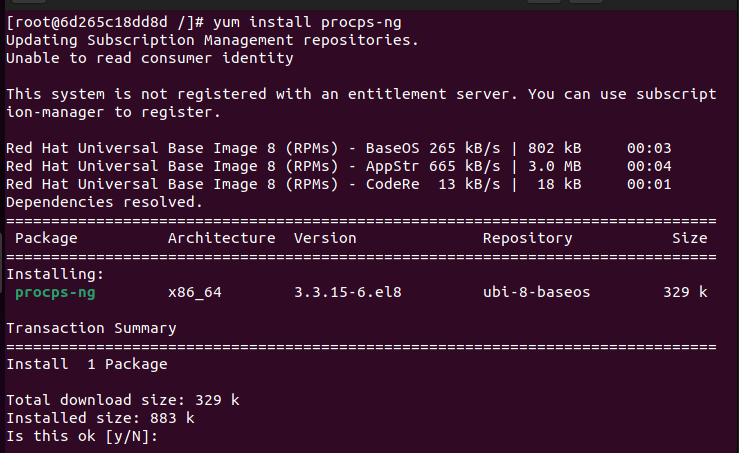
If you created the podman container, use the command below to install the procps-ng package, which installs top and ps to help view the currently running processes using the ps -ef Linux command.
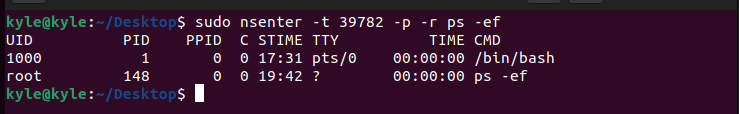
You can now enter the PID namespace using the command below.
The -r sets the root directory, and if none is specified, like in the command below, it uses that of the target process ID.
The output gives the currently running process in the container.
Conclusion
As a developer, you can’t evade using Linux containers. The best approach is to equip yourself with tools that enable you to interact with the different namespaces for processes in separate containers. Thanks to containers, the isolation of processes running on Linux is possible. We’ve covered how to use the nsenter Linux command to enter the namespaces of different processes in any container. Keep practising and trying other tactics to understand the tool better.