The IAM role allows the lambda function to access other AWS services within the AWS account. On the other hand, the resource-based policy is attached to the lambda function to allow other AWS services within the same or different accounts to access the lambda function. In this blog, we will see how we can manage lambda permissions by applying the IAM and resource-based policies.”
Managing Permissions Using the IAM Role
By default, the IAM role attached to the lambda function has only access to put the logs to the CloudWatch logs. You can always update the execution role to add further permissions to it. If you want to access the S3 bucket or you want to perform some action on an S3 bucket object, you need the S3 bucket and S3 object level access in the lambda execution role. In this section of the blog, we will update the IAM role permissions to allow lambda to interact with the S3 bucket.
First of all, navigate to the AWS lambda console and click on the lambda function you want to update the execution role for. Click on the configuration tab on the lambda function console. Then from the left side panel, select the Permissions tab, and it will show the lambda execution role there.
In the IAM role, either you can add an AWS-managed or Customer managed policy, or you can add an inline policy to grant the lambda function necessary permissions to interact with other AWS services.
Managing Permission Using Resource-Based Policy
Resource-based policies for the lambda function provide permissions to other AWS services within the same or different AWS account to access the lambda function. By default, there is no resource-based policy automatically attached to the lambda function, so no AWS service can access the lambda function. You can add and remove the resource-based policies anytime to your lambda function. In this blog, we will add a resource-based policy to the lambda function, which allows S3 to invoke the lambda function.
In order to add a resource-based policy to the lambda function, first, click on the lambda function and go to the permissions tab of the lambda function.
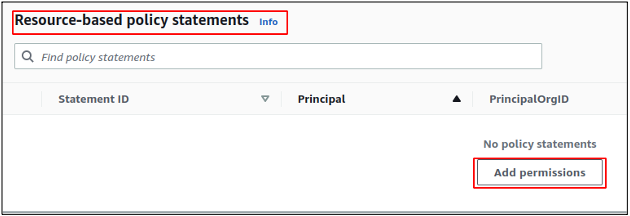
In the permissions tab, scroll down, and you will find a section for resource-based policies. Click on the Add permissions button in the Resource-based policy statements section of the console to add a new resource-based policy to the lambda function.
In the resource-based policy, there are three types of resources you can grant permission for the lambda function.
- Grant permission to AWS services
- Grant permission to another AWS account
- Grant permissions to invoke lambda function via URL
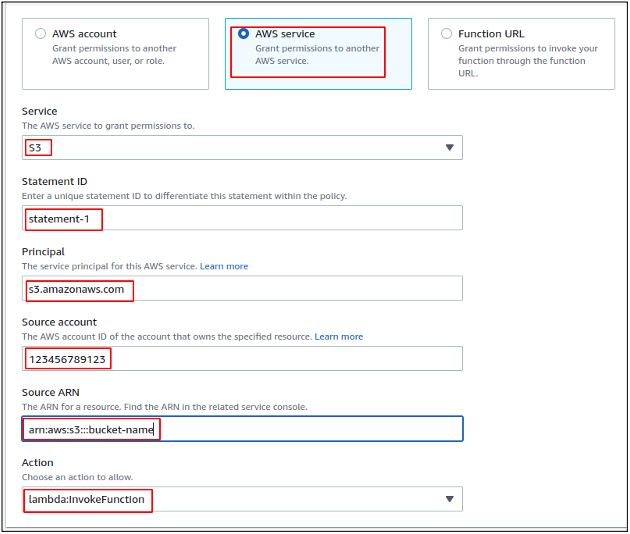
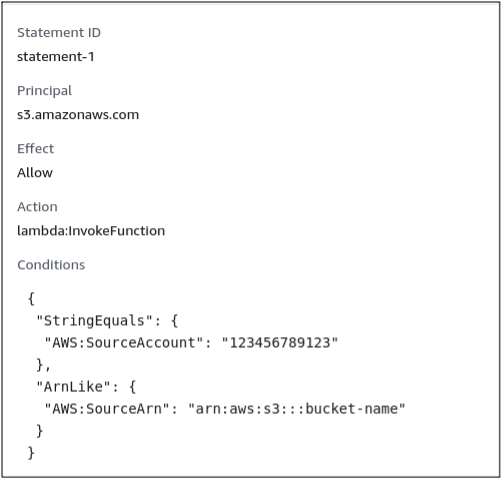
For this demo, we will be configuring an S3 bucket of the same account to invoke the lambda function whenever a new S3 object is uploaded to it. For this configuration, Select the AWS service and then select the S3 as the service. Enter the AWS account ID in which the S3 bucket exists, i.e., your own AWS account ID. After providing the account ID, provide the ARN of the S3 bucket, which will have permission to invoke the lambda function, and then select lambda:InvokeFunction as action as we are going to invoke the lambda function from the S3 bucket.
After adding all this information, click on the save button to add the resource-based policy to the lambda function. You can also have a look at the JSON format of the resource-based policy attached to the lambda function.
From the resource-based policy section in the permissions tab, click on the newly created resource-based policy, and it will display the policy in JSON format.
Removing Resource-Based Policy
You can remove the resource-based policy when you further do not need to allow other AWS services to access the lambda function. Keeping the resource-based policy attached to a lambda function can be harmful as it grants other AWS services access to the lambda function.
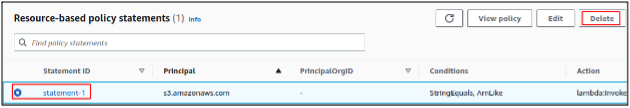
In order to remove the resource-based policy, go to the resource-based statements section of the permissions tab. Select the resource-based policy you want to remove and click on the Delete button, and it will delete the resource-based policy from the lambda function.
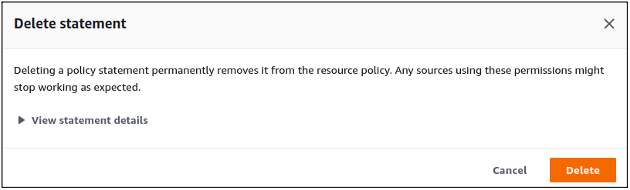
It will ask for confirmation before removing the resource-based policy, and you can confirm the deletion by clicking on the delete button.
Conclusion
In this blog, we have studied how to manage permission with the AWS lambda function. There are two types of permissions that can be assigned to lambda; one is lambda IAM role-based permissions that allows AWS lambda to access other AWS services, and the other one is resource-based permissions that allow other services to access the lambda function. In this blog, we studied the difference between both types of policies and saw how we could update both policies to grant permissions.