The most crucial thing for a system administrator to understand is how PAM configuration files provide the link between services and PAMs that carry out the actual authentication activities. You don’t need to comprehend PAM’s inner workings. PAM could significantly alter your Linux system’s security. Incorrect settings may fully or partially prohibit access to your machine.
Interfaces of Linux-PAM in Ubuntu 20.04
Four different management groups handle the PAM authentication tasks separately. When a typical user requests a restricted service, these groups handle various portions of the request:
- Account: This module is used to determine whether the supplied account is valid under the current circumstances. Several factors are checked in this category, including account expiration, the time of day, or if the user has authorization to the relevant service.
- Authentication: In this module, the user’s identity is validated once all the basic information has been verified as accurate. The user’s identity is verified by allowing them to provide a login or any other particular piece of data that only they are required to know.
- Password: The authentication module is supposed to work in collaboration with this module, which assists the user in upgrading passwords. Both resonances provide the ability to enforce secure passwords.
- Session: This module outlines the activities that must be taken at the start and end of sessions, and it is not the least important of the modules that make up the order by which the overall PAM strategy completes the desired task. The session begins when the individual has successfully authenticated themselves.
How To Validate a Linux-PAM Program in Ubuntu 20.04
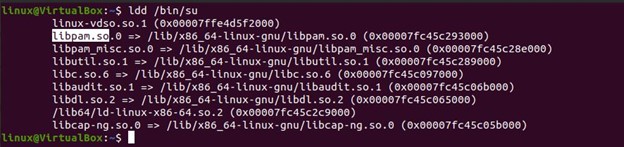
An application or program must be “PAM aware,” or expressly built and compiled to use PAM. Use the “ldd” command to see if a program was built using the PAM library to determine whether it is “PAM-aware” or not. When the command “ldd /bin/su” is executed, the file “libpam.so” is highlighted in the second line that supports the query. The validation is shown in the screenshot below:
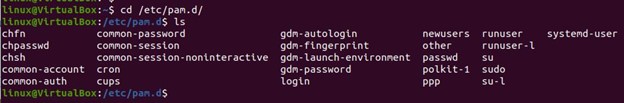
The directory /etc/pam.d/ contains the configuration for LINUX-PAM. Go to the PAM directory by entering the following command in your Linux operating system’s terminal:
The previous snapshot shows that one can examine the content by entering the “ls” command within the PAM directory. The sshd server must be installed if it isn’t listed as a service that implements PAM. SSH, also known as secure shell, is a networking application that encrypts data transmission and enables various computer types and users to connect safely and remotely across a network to various systems. The following command acquires the openssh-server package:
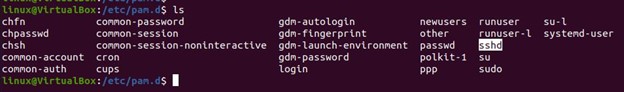
You may then re-enter the PAM directory, check for the services, and see the sshd has been added after it has finished installing all the files. The sshd service is highlighted in the “/etc/pam.d” directory.
How To Configure a Linux-PAM Program in Ubuntu 20.04
Every PAM module’s call results in either success or failure. The result is handled by PAM using control flags. The control flags specify the relative importance of each module’s success or failure to the overall objective of establishing the user’s identity with the service, and modules can be piled in a certain order. There are four preconfigured control flags available:
- required: For authentication to move forward, the package response must be successful. The user won’t be alerted if the attempt fails at this stage until all package tests its use that interface have finished running their findings.
- requisite: According to the arguments, if this breaks, everything else will as well. PAM will also be terminated, and a failure notice will be delivered.
- sufficient: If this module is successful and all earlier required modules are also successful, no further required modules are called.
- optional: Indicates that the module is not essential to whether the user’s service request is successful or unsuccessful. Its value is only considered in the absence of any conclusive successes or errors of earlier or later stacked modules.
- include: When the matching parameter is matched, every line in the configuration file is retrieved by this control flag.
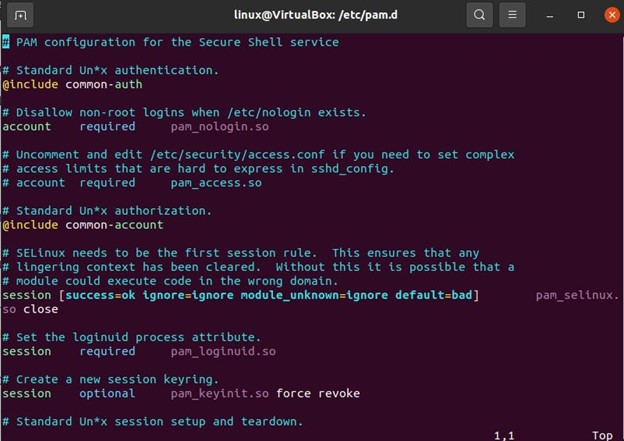
Just type the following command inside the PAM directory:
As you can see, the control-flags term, which we have described earlier in the following PAM file:
The following general guideline should be used while writing the main configuration:
- Service: the real name of the program
- Type: interface/context/type of module
- Control-Flag: if the module fails to complete its authentication task, the control flag determines how the PAM-API will behave
- Module: The PAM’s absolute or relative pathname filename
- Module-argument: Module parameters are a list of tokens that can be used to affect module functionality
If you wish to prevent root users from connecting to any system over SSH, you must restrict access to the sshd service. Furthermore, access to the login services is to be restricted.
Several modules limit access and grant privileges, but we can utilize the incredibly adaptable and feature-rich module /lib/security/pam listfile.so. Go to the /etc/pam.d/ directory, open the target service’s file, and make the necessary changes as follows:
The following regulation must be inserted into the file:
Previously, the module type is auth (or context). The control flag indicates that despite how well the other modules are performing, if the module is utilized, it must succeed, or the overall outcome will be a failure. A means to enable or deny services based on any file is provided by the PAM listfile.so module. onerr=succeed is an argument for the module. The item=user is a module argument describing the file’s contents that need to be verified. The sense=deny module option indicates the action to be taken if the item is located in the file. Otherwise, the opposite course of action is requested. File with one item per line is specified by the module option file=/etc/ssh/deniedusers.
The name root must be added to the file /etc/ssh/deniedusers after it has been created:
After making the necessary permissions, save the modifications and shut the file:
With the previous rule in place, PAM will be instructed to check the /etc/ssh/deniedusers and prevent any listed users from using the SSH and login services moving forward.
Conclusion
Programs that depend on authentication can ensure that only authorized applications are in a Linux operating system due to the robust high-level API known as PAM. It has a lot of power, but it’s also quite difficult to comprehend and operate. For applications and services running under Linux, PAM offers dynamic authentication support. The performance of a module can be evaluated using any of the control flags listed in this manual. PAM is often used in many secure systems because it is more user-friendly and dependable than the conventional password-and-username authentication mechanism.