Linux file encryption involves rewriting the plaintext documents into a format that can only be accessed by those with the right password or decryption key. This is done to prevent the unauthorized access to delicate information. Linux supports a number of encryption methods including symmetric encryption which employs the very same key for encryption and decryption, filesystem-level encryption, and public-private key asymmetric encryption. Linux users frequently use GnuPG, OpenSSL, and dm-crypt as encryption tools. In this guide, we will use the GPG utility to encrypt the Linux files and decrypt them.
Update the System
The first thing to do is to update your system before the installation of any utility. The following command updates the package list on an Ubuntu system. Using the “sudo” command, the “omar” user runs the command with superuser rights. The system is connected to a package repository at “http://pk.archive.ubuntu.com/ubuntu” and is looking for updates.
Install the GPG
The GPG is the tool that is used in Linux to encrypt the files. The following command is used to install the “gpg” (GNU Privacy Guard) software package on the system. Run the command with administrative rights by typing “sudo.” A utility to manage the packages on Debian-based computers is called “apt-get.” The “install” command instructs the apt-get to set up the chosen “gpg” package. The output shows that the “gpg” package is already installed on the system and is the newest version (2.2.27-3ubuntu2.1). The package is also set to be manually installed which means that it is installed by a user rather than being a dependency of another package. The output also states that two packages, “libflashrom1” and “libftdi1-2”, are no longer required and can be removed using the “apt autoremove” command. Lastly, the output states that there are 0 upgraded packages, 0 newly installed packages, 0 packages to be removed, and 37 un-upgraded packages. No changes are made to the system’s packages and all packages are up-to-date.
File Encryption
To encrypt in Linux, we should have a file with some important content in it. Thus, we use the “touch” instruction to create a new file in the current working directory which is pass.txt.
The “ls” query of Linux shows that the newly created “pass.txt” file is listed in the current working directory.
Desktop Downloads new Pictures snap Videos
Documents Music pass.txt Public Templates
Make sure to add some content to your newly made file. We also add some information regarding our system user in the “pass.txt” file by manually opening it. The “Cat” instruction can be used to display the contents of any sort of file as shown in the attached command and output:
Password: Omar
The “gpg -c pass.txt” command uses the GNU Privacy Guard (GPG) tool to encrypt a file called “pass.txt” using the symmetric-key encryption. The “-c” option tells GPG to use the symmetric-key encryption and prompts the user to enter any passphrase to use as the encryption key. The encrypted file is created using the same title as the original file and the “.gpg” file extension.
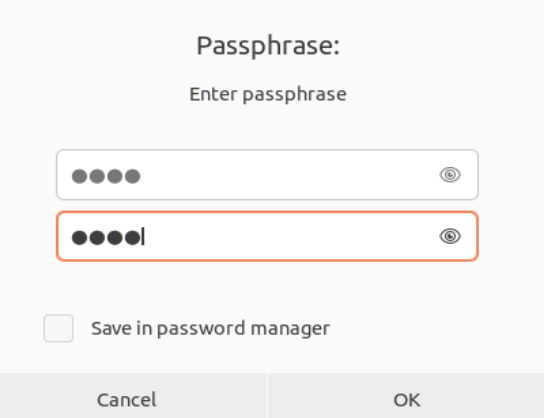
The dialog box appears on your screen which prompts you to enter the passphrase as shown in the image. We add the passphrase and tapp the “OK” button:
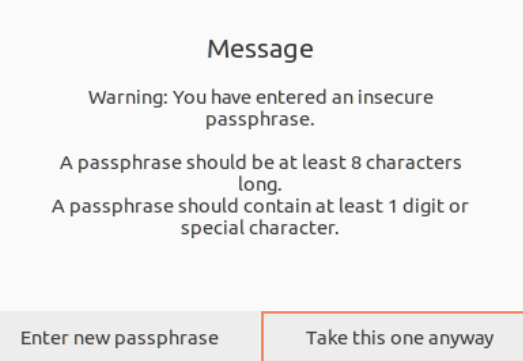
The very next screen shows a warning if you enter an insecure passphrase. Choose the “Take this one anyway” option to proceed.
The list instruction displays the encrypted “pass.txt.gpg” file which is listed with the other files in the current directory.
Desktop Downloads new pass.txt.gpg Public Templates
Documents Music pass.txt Pictures snap Videos
The “file” instruction is applied to establish the type of a “pass.txt.gpg” file based on its contents, rather than its file name or file extension. The output indicates that the “pass.txt.gpg” file is a GPG symmetrically encrypted file, and it’s encrypted using the AES256 cipher. The AES256 cipher is a symmetric key encryption algorithm. AES (Advanced Encryption Standard) is a widely used encryption standard, and 256 refers to the key size which means that it has a key size of 256-bit.
pass.txt.gpg: GPG symmetrically encrypted data (AES256 cipher)
Now, when you try to display the contents of an encrypted “pass.txt.gpg” file, we should get the following output using the “Cat” instruction along with the file name:
� ��7$�Z$��K��^��On���
����k.�K�{��dE�֛_���$�
��6ay�jȚ�N:�*�w�:�껎~��4j
After the encryption of a “pass.txt” file to a new file, there is no need to remain using the original file which is the pass.txt. Therefore, we remove it using the “rm” instruction.
File Decryption
It’s time to decrypt the original data from the encrypted “pass.txt.gpg” file. For this, we don’t need the original “pass.txt” file here since we already deleted it as per the “ls” command.
Desktop Downloads new Pictures snap Videos
Documents Music pass.txt.gpg Public Templates
To decrypt the encrypted “pass.txt.gpg” file, we cast off the following “gpg” instruction on the shell. It uses the “>” operator to pass the decrypted content to a “pass.txt” file that uses the GNU Privacy Guard (GPG) tool to decrypt a “pass.txt.gpg” file using symmetric-key decryption. The “–decrypt” option tells GPG to perform the decryption, and the “> pass.txt” redirects the output of the decryption process to a file called “pass.txt”.
The first output line indicates that the data in the pass.txt.gpg file is encrypted using the AES256 cipher in CFB(Cipher Feedback) mode. The second output line, “gpg: encrypted with 1 passphrase”, indicates that the pass.txt.gpg file is encrypted with a single passphrase. A passphrase is a sequence of words or other text that is used to encrypt a file, and it is required to decrypt the file.
gpg: AES256.CFB encrypted data
gpg: encrypted with 1 passphrase
Now, we have a pass.txt file back in the current working directory as per the following “ls” instruction output:
Desktop Downloads new pass.txt Pictures snap Videos
Documents Music pass.txt.gpg Public Templates
When you try to display the content of a pass.txt file on the Linux shell using the cat instruction, it displays the original content before the encryption of a file.
Password: Omar
Conclusion
The introduction demonstrates the use of encryption in Linux systems and discusses its types as well. To support the topic, we installed the GPG utility that is specifically designed for the encryption of Linux-based files. After its installation, we generated a simple text file and encrypted it using the “gpg” utility and added the passphrase for encryption as an example. Lastly, we tried the GPG utility to decrypt a file to its original form and display the original content on the shell.