Also known as Secure Socket Shell, this protocol is a security application for Linux users connecting to remote servers. The framework allows users to transfer files, run command lines and graphical programs, and create secure virtual networks over the internet.
The framework has an SSH command to secure remote connections and data transfers between clients and hosts. The utility ensures encryption of all communications.t
The command works by transferring client inputs to the host. Once done, the command returns the output from the host to the client and often executes through IP/TCP port 22. This encrypted connection is also used in port forwarding, Linux server, tunneling, and many more.”
Components of the SSH Command
Like every other computing command, the ssh command has syntax. The syntax for this command is as shown in the below image;
And as shown in the command, the following make the components of the ssh comma;
- ssh command-The command provides instructions to machines to create secure encrypted connections with the host network or system.
- User Name– This is the name of the Linux client or user accessed by your host machine or system.
- Host– This is the machine that the user accesses or establishes a connection with and domain names or IP addresses. Ideally, hosts can either be routers or computers.
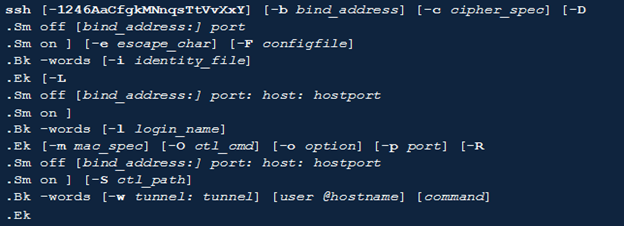
The ssh Command Synopsis and Flags
The image below illustrates the ssh command synopsis;
The ssh command tags are as follows;
| Tag | Description |
| -1 | Compels ssh to try only the version 1 protocol |
| -2 | Forces ssh to test only the version 2 protocol |
| -4 | Makes ssh to use only IPV4 addresses |
| -6 | Forces ssh to only use IPv6 addresses only |
| -A | It initiates authentication agent connection forwarding. Usually, you can specify this flag on a per-host basis. Notably, you should enable agent authentication forwarding with a lot of caution. Those with the authority to bypass file permissions on remote hosts can often access the local agent through a forwarded connection. While attackers may not access key material from the agents, they can use the keys to perform operations and authenticate using identities within the agent. |
| -a | Disables the authentication agent connection forwarding |
| -b bind_address | You can use bind_address on local machines as the source address of the connection. This flag only comes in handy for systems with multiple devices. |
| -C | It is used for requesting compression of all data. It uses the same algorithm used by gzip to compress data, including stdout, stdin, and stderr. |
| -c cipher_spec | It chooses the cipher specification to use during the encrypting session. Protocol version 1 only allows the specification of one cipher. But for protocol version 2, a comma separates the list of ciphers beginning with the most preferred. |
| -D –Xo | It controls the Sm off and Sm on components. It specifies the local dynamic for port forwarding at the application level. Notably, it allocates a socket that listens to the port on your local system. Every connection through this port is forwarded over the system’s secure channel. |
| -e escape_char | This tag helps to set escape characters for sessions with pty. |
| -F configfile | It specifies the configuration file for each user. |
| -f | The flag initiates a request for ssh to return to the background before executing a command. This is handy when the user wants the password or passphrase requests to happen in the background. |
| -g | Establishes connections between remote hosts and local forwarded ports |
| -i identity_file | Selects the system file from which your machine will read the identity for DSA or RSA authentication. |
| -k | Disables delegation or forwarding of GSSAPI credentials and identities to the server |
| -L -Xo | Controls the Sm off and Sm on components by specifying that the port provided on the client/local host should be forwarded to your port and host on the remote machine. |
| -l login_name | It directs the user to log in on the remote side. |
| -M | It puts the client into a master mode to enable connection sharing. There can be multiple –M options to place an ssh client on master mode and require confirmation before the system accepts slave connections. |
| -m mac_spec | This is an additional flag for protocol version 2. It provides a comma-separated list of message authentication code (MAC) algorithms. |
| -N | Instructs users not to commit remote commands. |
| -n | It redirects the stdin data from /dev/null and prevents its reading. It is only useable when ssh runs in the background. |
| -O ctl_cmd | It controls an active connection from multiplexing the master process. |
| -o option | This flag is often used to provide options in the exact format used in your configuration file. |
Conclusion
This article is an elaborate introduction to the Secure Socket Shell or SSH. It has described the ssh command alongside its syntax and the relevant flags. Hopefully, you can use the above information to initiate your interaction with the SSH protocol.
Sources
- https://help.ubuntu.com/community/SSH
- https://www.tutorialspoint.com/unix_commands/ssh.htm
- https://www.javatpoint.com/ssh-linux
- https://phoenixnap.com/kb/ssh-to-connect-to-remote-server-linux-or-windows
- https://www.ucl.ac.uk/isd/what-ssh-and-how-do-i-use-it
- https://www.techtarget.com/searchsecurity/definition/Secure-Shell
- https://support.huawei.com/enterprise/en/doc/EDOC1100205274