Managing and maintaining a Linux LDAP server can be very intimidating, particularly if you are going through it for the first time. However, this procedure should not send shivers down your spine. For the record, managing a Linux LDAP server is not as complicated as it often seems.
Getting started with Linux LDAP begins with understanding the OpenLDAP command line. Firstly, Linux LDAP often comes with three primary objectives. It can authenticate, interrogate, and finally update and control your systems. And to meet these functional capabilities, the LDAP C-API has the tools or commands that cover all the categories.
Thus, this article will discuss the basic Linux LDAP commands. More importantly, the write-up will show you how to use various commands to achieve the three LDAP commands.
1. ldapadd Command
If you want to add entries into the directory, the ldapadd command is the ideal tool. This command reliably opens a connection to your directory to authenticate. It comes in handy in two ways. Firstly, you can use it to open the .ldif file and add entries one at a go. It can also create a file from which ldapadd will read. The ldapadd syntax is:
Example:
The above command will add kenbrian as a user in your LDAP directory. Notably, LDAP directory files will automatically be saved as users.ldif in the home directory. The ldapadd command also allows you to add multiple users all at once by listing the user credentials one after another before issuing the command above.
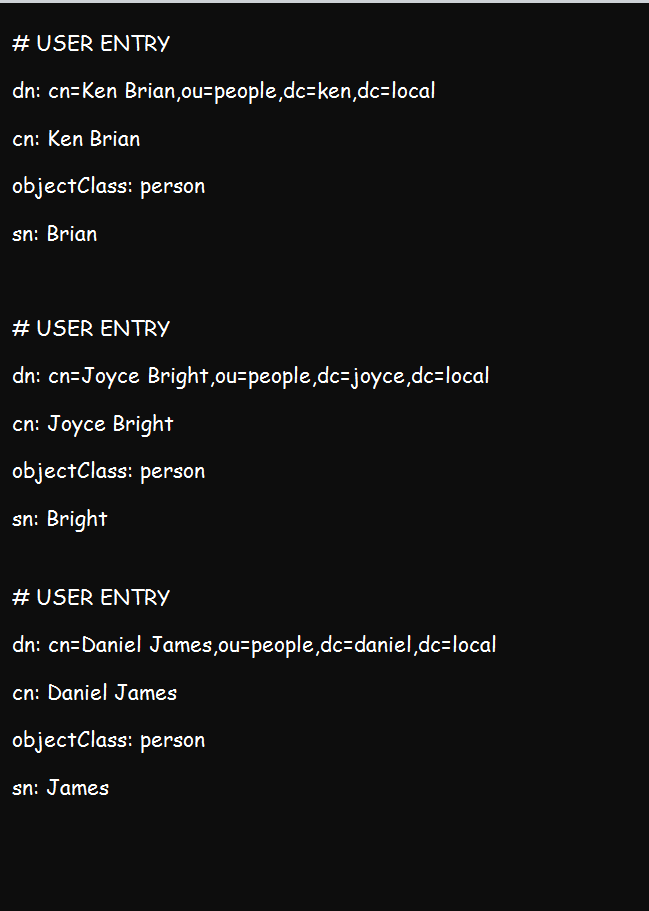
An entry file for multiple users will look like what we have below. But for a single user entry, just one set of credentials will do.
You can add as many entries as you wish.
2. ldapmodify Command
The ldapmodify command changes the credentials in an existing entry. This command is pretty interactive. Thus, using it involves the following steps:
- Issue a ldapmodify command
- Inform the command of what you intend to modify
- Make modifications to the data
- Exit using CTRL-d.
- Confirm the changes effected by ldapmodify
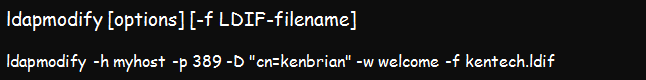
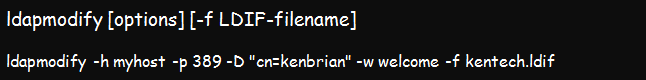
The syntax is;
The file fetches the LDIF file due for modification and changes the LDAP entries specified by the modification request file. This command uses a modified version of the .ldif file. Utilize the changetype component within the file to select the change type you want to implement. The four various kinds of changes that you can effect include:
- add– Used for adding a new entry
- Modify– Can add, delete, or replace an attribute to change an existing entry
- delete– Used for deleting a current entry
- modrdn– Used for modifying the RDN component of an existing entry
Example:
The command above implies that user kenadmin is authenticating to the myhost directory, which exists at port 389. The utility will open the kentech.ldif file and modify the relevant directory entries as requested.
3. ldapsearch Command
If you are looking for specific entries from your LDAP directory, the ldapsearch command will help you search successfully. And like most LDAP commands, ldapseach begins by opening a connection to the directory and authenticating whoever performs the search before searching the requested entry and printing the result.
Of course, the command will also publish the results in the specified format.
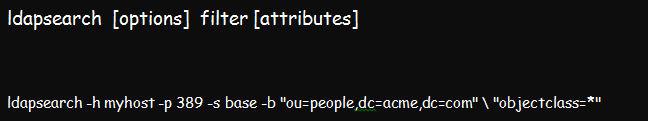
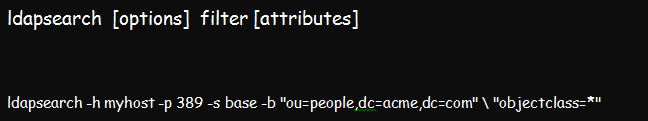
The command’s syntax is:
Example:
In the above example, the search targets myhost server, located within port 389. The base is the –s (scope) of the search, and the base DN –b, is the section being searched.
4. ldapbind Command
This command has two primary objectives. Firstly, you can use it to authenticate to your directory server. Again, the ldapbind tool also comes in handy in determining if your server is up and running.
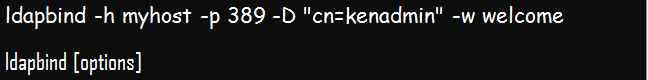
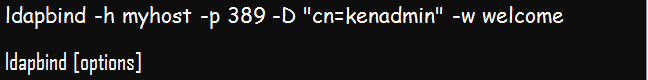
Below is the ldapbind syntax:
Example;
The above command authenticates kenadmin to myhost directory server, located at port 389. The password for the authentication is welcome.
5. ldapdelete Command
The ldapdelete tool comes in handy in removing leaf entries from the directory. It works by creating a connection to the directory server, authenticating the user, and finally deleting the specified entries.
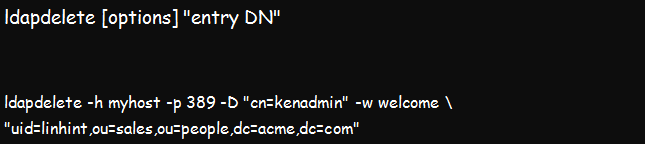
The command’s syntax is:
Example:
The command above aims to authenticate kenadmin to the myhost directory. It will then delete the requested items. For example, it will get rid of the entry uid=meryl,ou=sales,ou=people,dc=team,dc=com.
6. ldapmoddn Command
The ldapmoddn tool also has two functions. Firstly, you can use this command to change RDN entries. You can also use the utility to move a subtree or an entry to a different location within the directory.
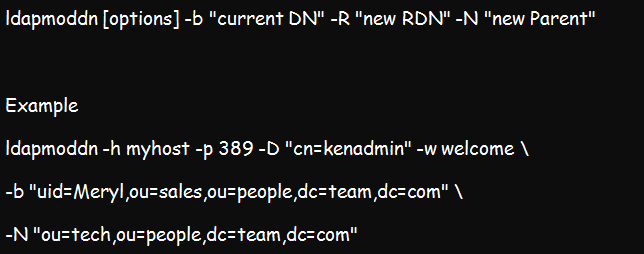
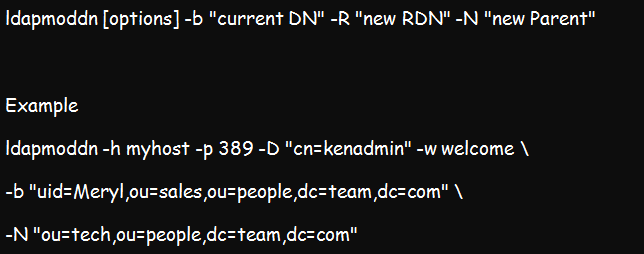
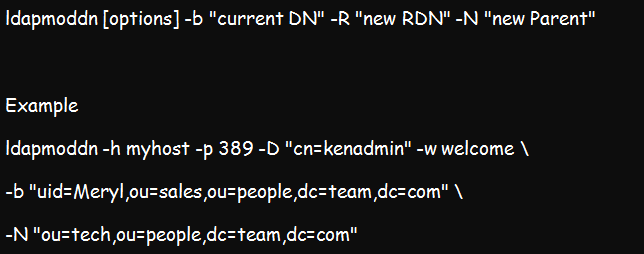
Its syntax:
Example:
The above command aims to authenticate kenadmin to the myhost directory. Once authenticated, it will assign the “uid=meryl,ou=sales,ou=people,dc=team,dc=com” \ to a new parent entry, which will be “ou=tech,ou=people,dc=team,dc=com”.
Understanding the LDAP Command Line Tools
The following command-line options are essential:
- -h – Stands for the directory server’s hostname
- -p – Port number
- -D – This is the bind DN
- -w – Stands for the bind password
- -W – The wallet authentication for one-way or two-way SSL authentication
- -P – The wallet password
- -U – Defines the SSL authentication modes (1 means no authentication, 2 for single-way authentication, and 3 for two-way authentications)
- -b – The base DN for the search
- -s – The scope of the search
- -f – The .ldif file bound for addition, modification, or deletion
- -R – A new RDN
- -N – A new parent for a subtree or an entry after removal
Conclusion
This article is an introduction to the various LDAP commands. With these illustrations, you now have an idea of the critical functional aspects of LDAP. Open your LDAP and attempt some of these commands since practicing is the best way to improve your knowledge and skills.