Like every authentication tool, Kerberos Linux also features an array of commands that every user should know. If you use Kerberos on Linux to authenticate users within your platform, these commands and utilities will always come in handy. Of course, knowing and understanding these commands will make using the Kerberos on a Linux OS a breeze.
This article discusses the common Linux Kerberos commands.
1. Kinit (/usr/bin/kinit)
Kinit is arguably the most popular Kerberos command. The command helps in obtaining/renewing and caching the ticket-granting tickets. The synopsis for this command is: [-V] [-l lifetime] [-s] [-r] [-p | -P] [-f or -F] [-a] / [-A] [-C] [-E] [-v] [-R] [-k [-t] [-c cache_name] [-n] [-S] [-T armor_ccache] [-X [=value]] [principal].
Kinit examples include:
Using Kinit to obtain renewable tickets.
![]()
Using Kinit to request valid credentials.
![]()
Using Kinit to request original/initial tickets.
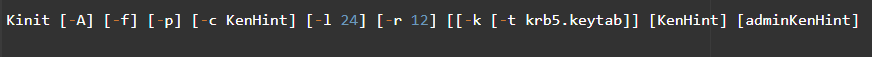
Using Kinit to renew tickets.
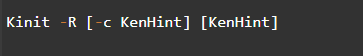
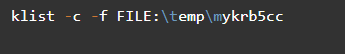
2. Klist Command (/usr/bin/klist)
The Klist command comes in handy in displaying the details of Kerberos tickets as they are at that particular moment. It can also display the details of a key tab file. The Klist Synopsis is klist [-e] [[-c] [-l] [-A] [-f] [-s] [-a [-n]]] [-k [-t] [-K]] [cache_name | keytab_name] and a ticket will normally look like what is in the following figure:
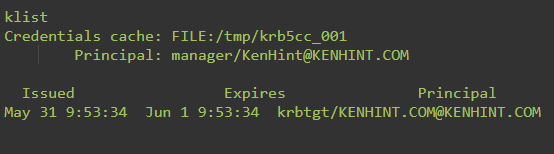
Notably, common Klist command examples include:
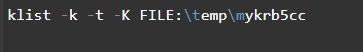
Using Klist to list entries in the key tab file.
Using Klist to list entries in the credential cache.
3. FTP Command (/usr/bin/ftp)
The Kerberos Linux command is a File Transfer Protocol. It minimizes the possibility of leaking your passwords, data, and files. Configuring FTP with Kerberos authentication on a Linux platform entails adding a server principal and a user principal as in the following figures:

4. Kdestroy Command (/usr/bin/kdestroy)
The kdestroy command destroys Kerberos authorization tickets. It does this by overwriting and deleting the user’s credentials cache that contains the tickets. This command destroys any default credentials cache if you do not specify the credentials cache to be deleted. The syntax for this command is [-A] [-q] [-c cache_name] [-p principsl_name] and it runs within the DEFCCNAME KRB5 environment variable. Examples include:
Using the kdestroy command to destroy the user’s default credentials cache.

Using kdestroy to destroy all credentials cache for users.

5. Kpasswd Command (/usr/bin/kpasswd)
The kpasswd utility changes the Kerberos user or principal’s password. It does this by prompting you to enter your current password first. It then provides you with an interface where you will enter your new password twice to finally change your password. The user or principal’s password needs to meet the specific policy in terms of length. Its synopsis is: kpasswd [-x] [-principal <username>] [-password <user’s password>] [-new password <new password>] [-cell <cell name>] [-servers <explicit list of servers>+] [-pipe] [-help].
Examples include:
Changing the principal’s password.
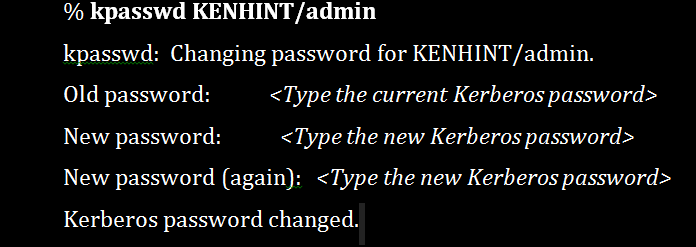
Changing the user’s password.

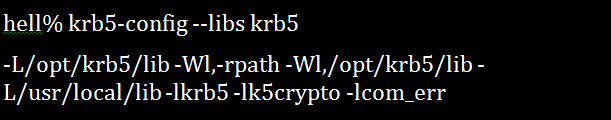
6. Krb5-config Command
If you are going to compile and link the programs in Kerberos Linux, this is the utility. It shows the application program what flags should be used for the compilation and installation processes against the installed KBR5 libraries. The synopsis for this command is krb5-config [–help | –all | -version | –vendor | -prefix | –exec-prefix | -defccname | –defktname | -defcktname | –cflags | -libs [libraries]].
An example of a Kerberos installation running in /opt/krb5/ but using the /usr/local/lib/ libraries for the text localization gives the following output:
7. Ksu Command
The ksu Kerberos Linux command has two objectives. First, it can create new security contexts. Second, ksu, can securely change the effective and real UID to that of your target user. Ksu works both in authorization and authentication. The ksu command synopsis is ksu [ targetuser ] [ -n target_principalname ] [ -c sourcecachename ] [ -k ] [ -r time ][ -p/ -P] [ -f | -F] [ -l lifetime ] [ -z | Z ] -q ] [ -e command [ args ] ][ -a [ args ] ].
For example:
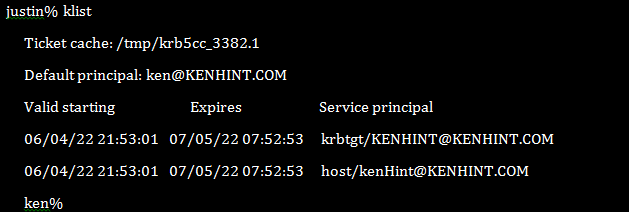
Justin has put Ken’s Kerberos principal in his k5login file. Ken can use ksu to become Justin in an exchange that would look like the following:

However, Ken’s new ticket would take the shape of the following screenshot and contain Justin’s UID in the filename with “.1” beside it.
8. Kswitch Command
The kswitch comes in handy when the cache collection is available. This command transforms the specified cache into a primary cache for collection. It uses the kswitch {-c cachename|-p principal} synopsis.
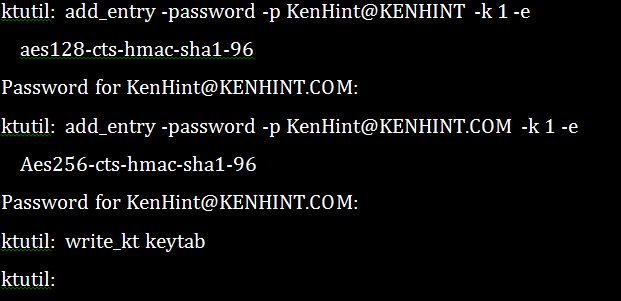
9. Ktulil Command (/usr/bin/ktutil)
Ktulil command provides the administrators with an interface to read, write and edit any entries in the key tab files.
The following is an example of a ktulil Linux Kerberos command:
10. Rcp Command (/usr/bin/rcp)
The rcp Kerberos Linux command has the ability to copy the files remotely. It can effectively transfer files between the local and remote hosts or transfer the files between two remote hosts. The syntax for the rcp command is: rcp [ -p] [ -F] [ -k realm ] [-m] { { User@Host:File | Host:File | File } { User@Host: File | Host: File | File | User@Host: Directory | Host: Directory | Directory } | [ -r] { User@Host: Directory | Host: Directory |Directory } { User@Host: Directory | Host: Directory | Directory } }
You can effectively use this command to copy one or more files between hosts. These hosts can be a local and a remote host, the same remote host, or between two remote hosts.
Examples include:
Copying a remote file from a remote host to another remote one.
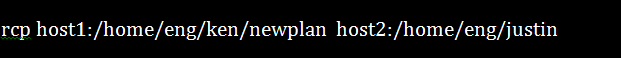
Copying a local file to a remote host.
![]()
11. Rdist Command (/usr/sbin/rdist)
The rdist Linux Kerberos command helps maintain the similar files in an array of different hosts. It does this while preserving each file’s owner, mode, group, and modified time. Besides, it can occasionally update the running programs.
Examples include:
Copying files to KenHint from src but leaving out those with “.o” extensions.

Indicating the host files due for updating.
![]()
12. Rlogin Command (/usr/bin/rlogin)
This Linux command enables you to log in to the other machines within your network. You can do so using these following steps:
Type the following command:
![]()
Note that the machine name is the name of the remote machine in your system that you want to log in to.
Type the remote machine’s password once prompted and press Return. However, you will not need to type a password if your machine name already appears on the remote machine’s /etc/hosts.equiv file.
13. Rsh Command (/usr/bin/rsh)
This command makes it possible to execute a command in a remote machine within your systems without logging in to the remote machine. You do not need the rlogin command if you know that you only want to execute a single objective on the remote machine.
This command syntax should help you achieve this mission:
1 | rsh machinename command |
14. Kadmin Command (/usr/sbin/kadmin)
The kadmin command is a command-line interface to Kerberos 5 administration system. It enables the maintenance of KBR5 principals, policies, and key tables.
Examples include:
Getting the attributes of a principal.
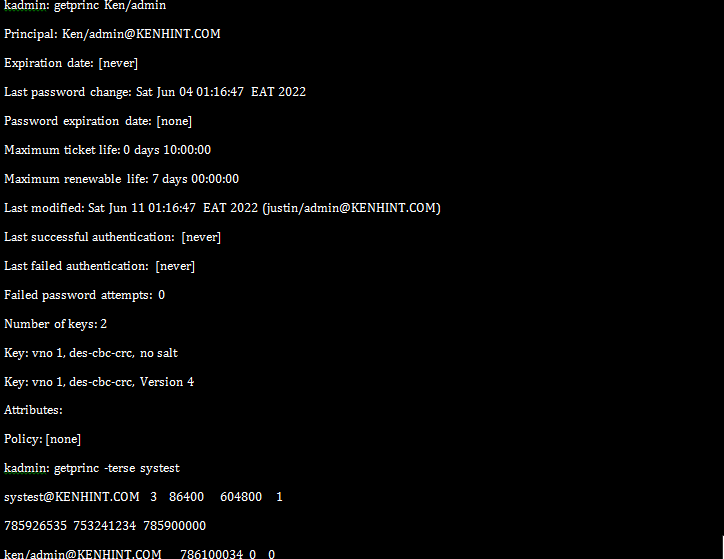
Listing the principals.

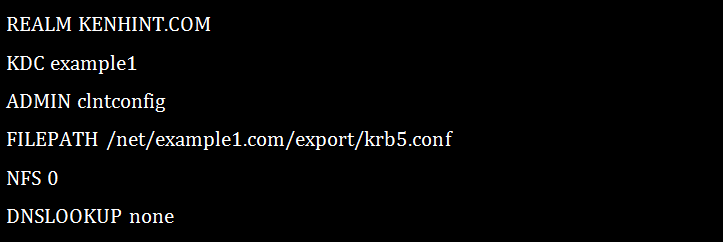
15. Kclient Kerberos Command (/usr/sbin/kclient)
The Kerberos kclient command comes in handy in an array of functions. It can configure a machine to do the kerberized NFS, copy the master files from the specified path names, set up the machines to maps realms, add the principal to a local host, etc.
An example of a Kerberos Client set up using the profile option:
Conclusion
The above Linux Kerberos commands will help you use the Kerberos protocol in a Linux environment more conveniently and securely. We provided the illustrations to make your work a breeze.
