Consumer desktop computers are mainly dominated by Windows and macOS operating systems. On the other hand, Linux has its own unique market value. It is not as dominated as other operating systems on desktop computers. However, it is rapidly growing. It has many diverse functions, and it is used everywhere, whether your car, home appliance, smartphone, or television. Linux is the preferred operating system for setting up a server at an organizational level because of its flexibility and robust security system.
Linux kernel is free to use, modify, and redistribute. Therefore, there are many Linux distributions, and some major Linux distributions are Ubuntu, Kali Linux, Fedora, and Debian. Every Linux distribution is available for free through the GNU General Public License. GNU stands for GNU’s Not Linux, a project by Richard Stallman to distribute free software through a common source. It is a collection of free software that can be bundled with the distributions.
The well-known environments are GNOME and KDE, with the widely used X window-system or Wayland.
Linux was initially designed for x86 architecture but later ported to many other platforms, especially smartphones. The most widely adopted mobile operating system, Android, is Linux-based. Moreover, Chrome OS kernel is also Linux-based, and it holds a decent market share. Linux is in smart homes, smart televisions, embedded systems, and even in gaming consoles.
Linux is a perfect example of how an open-source project is perfectly organized and successfully maintained.
Many people believe that Linux is not a reliable or professional operating system. However, it is far from reality. In fact, Linux is one of the preferred operating systems to set up a network server.
Linux is also called “The Clone of Unix” because there are many similarities between Linux and Unix. The difference is Linux has its own code. The Linux source code is free to access, whereas Unix is proprietary. The primary goal of designing Linux is to make it available for everyone. Many Linux features make it a preferable choice over Unix, such as faster threat detection, support of multiple desktop environments, free usage, the flexibility of customization, and portability.
Linux is a superior operating system due to its countless significant features.
- Linux Command Line
- Editing in the Command Line Interface
- Managing Command History in Linux Shell
- Modifying the History Size in Linux Shell
- Filename Expansion in Linux Shell
- Redirection in Linux Shell
- Pipes in Linux Shell
6. The Shell Scripting and Programming
- Creating a Variable in Shell Scripting
- Conditional Statements in Shell Scripting
- Loop Structures in Shell Scripting
7. Linux Files and Directories
11. Linux System Administration
1. What is Linux?
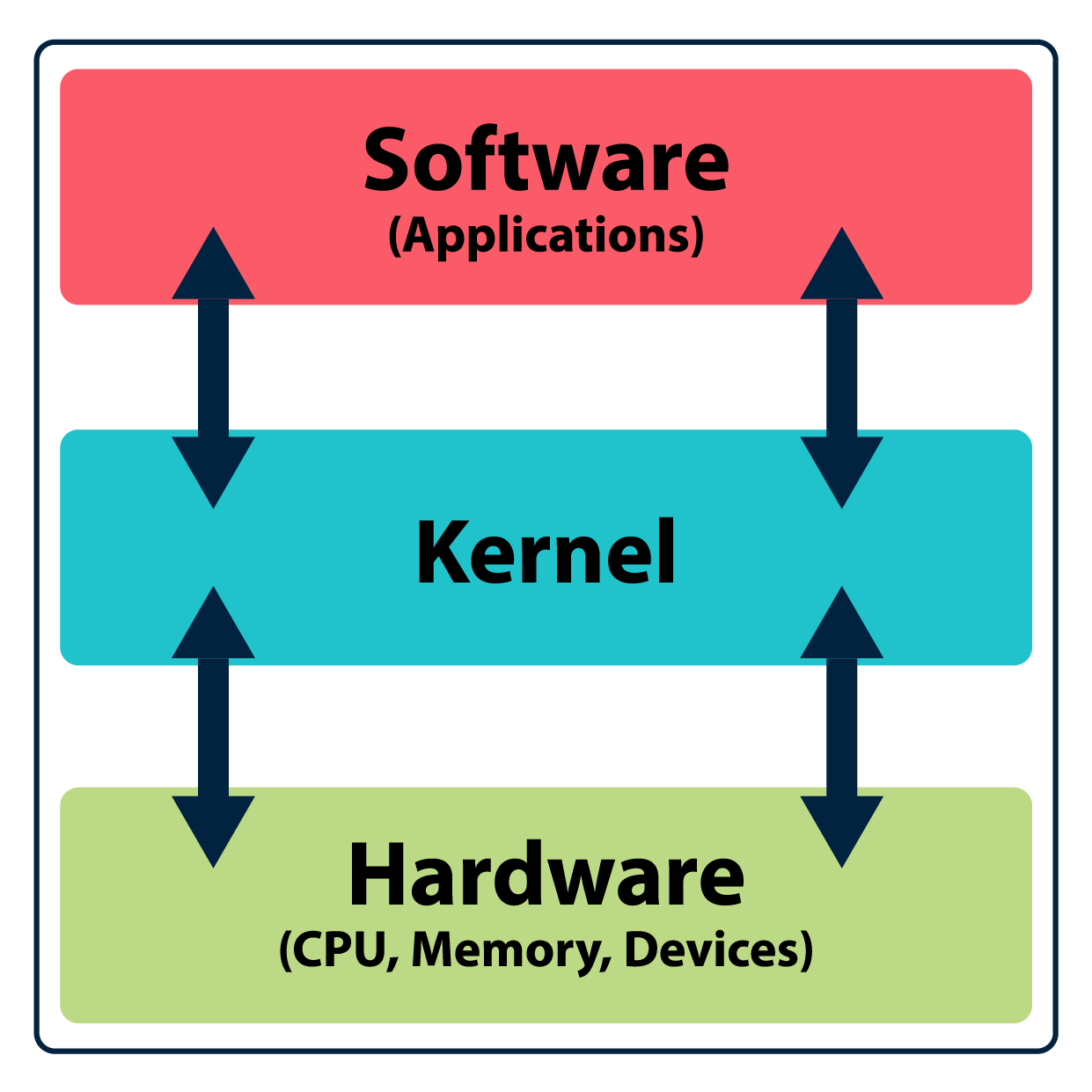
Linux is usually referred to as an operating system that manages hardware resources connected to your computer. It is the kernel that controls the communication between the system software and the hardware. To be precise, Linux is a kernel that is a core element to an operating system and developed by Linus Torvalds. A kernel is a small program that resides in your system’s memory and manages everything, whether it is your CPU, memory, or any other attached hardware. It handles the main processes of a computer and loads before the boot sequence.
A kernel has to manage many crucial operating system processes, including resource allocation, memory management, process management, disk management, device management, and security management.
Linux is essentially a kernel that is a crucial element of an operating system. When a kernel combines with an interface for performing various tasks, it becomes an operating system. The interface could be a minimalist command line interface or fully graphical. So whenever you hear about Linux, it would be mostly about operating systems or distribution that has Linux as its kernel.
Linux is free to use, study, modify, and distribute because it falls under the GNU General Public License. It is distributed in different desktop environments with a large number of free applications. Perhaps, the open-source nature of Linux distinguishes it from the other operating systems that are proprietary, and it cannot be modified and redistributed.
Linux is a diverse operating system, and it is constantly evolving, thanks to the open-source community of developers creating free software that bundles with many Linux distributions. You will get a free alternative to every premium app of other operating systems in Linux. And these applications are no less than the paid applications and perform equally well. There are multiple sources to acquire Linux applications such as SourceForge, KDE Apps, etc. Linux also has powerful capabilities when it comes to networking since it provides many utilities to set up and maintain a server.
1.1 Linux Distributions:
We have already mentioned multiple distributions of Linux. Let’s dive deep and learn about different distributions.
There is, in fact, only one version of Linux but multiple distributions that use the Linux kernel. There are more than 600 Linux distributions. Different companies have packaged Linux kernels in different ways, which can be accessed from kernel.org. Some well-known distributions are Debian, Red Hat, Ubuntu, OpenSUSE, and Fedora.
Many distributions are designed for a specific purpose or task; for instance, Kali Linux is specially designed for penetration testing, such as Nmap, Maltego, Aircrack-ng, and Metasploit Framework. Kali Linux is normally opted by cybersecurity experts and beginners who are interested in learning penetration testing. Similarly, Ubuntu is specifically designed for users new to Linux and switching from other operating systems. For more details about the older and the most recent Linux distributions, visit DitroWatch. Simply keep in mind, the distributions can have different ways of installing and managing packages.
1.2 Linux and the Operating System:
Now, let us review the difference between Linux and the operating system in a broader aspect. An operating system is a program that manages communication between the connected I/O devices and software. The operating system is designed to handle repetitive tasks, such as file systems, executing programs, etc. An operating system can be a simple command line interface (CLI) or graphical user interface with menus and a file system.
Operating systems perform many tasks such as running an application, editing a document, image, video, and perform other calculations. Moreover, it manages the loading of applications because they need to be loaded in the memory to function. Like Unix, Linux has always been a multi-user operating system. In comparison, Windows introduced it after Windows XP. Every distribution has a default environment for ease of use.
2 History of Linux:
The Linux operating systems are similar to Unix that uses a free kernel called Linux, released in 1991. Many operating systems use Linux kernel, and these operating systems are also termed as distributions. Linux kernel is free to use, which means anyone can modify it, make an operating system, and distribute it. The aim of developing Linux was to provide a free operating system for personal computers. However, later it was ported to many other systems, such as smartphones, smart TVs, home automation systems, Chromebooks, and tablets. Currently, there are millions of devices in the world that run Linux.
Linux is rapidly growing, approximately 90% of cloud computing infrastructure uses Linux, and 70% of smartphones is Linux-based. So, how did Linux gain such popularity, and how did the voyage begin? To get it, let’s peek into its background first:
2.1 Background:
The background of Linux strongly links with the history of the development of Unix. So before we discuss how Linux was developed, let’s have a brief background about the operating system’s development.
In the late 1960s, AT&T, General Electric, and MIT conducted joint research and developed an operating system called MULTICS. MULTICS stands for Multiplex Information and Computing Service, which introduced features like file management, multitasking, and multi-user interaction. The development of MULTICS was a massive milestone toward the creation of a modern operating system.
The primary aim behind the creation of MULTICS is to introduce a multipurpose computer operating system to allow many users to connect to a system simultaneously. Therefore, it is also called a time-sharing utility. For detailed information about the features of this revolutionary operating system, visit MULTICIANS.ORG.
Though it was a concerted effort of the three leading tech giants, AT&T left the project in 1969, and General Electronics sold its shares to Honeywell. Then, Honeywell used MULTICS as a commercial product. It was a success and, more importantly, a big step towards the beginning of an advanced operating system.
2.2 The Rise of Unix:
In 1969, the efforts of Ken Thomson, Dennis Ritchie, and other researchers at AT&T Bell Laboratory brought forth a new operating system called Unix. Ken Thomson was one of the members of the MULTICS project, so Unix included many features of MULTICS. Unix stands for UNiplexed Information and Computing, designed to run on minicomputers. The affordability and ability of multitasking gave immense popularity to Unix.
Unix quickly became one of the widely used operating systems replacing MULTICS. The MULTICS project was canceled in 1985, and there were many reasons. However, the primary cause can be attributed to the “second-system effect” that allowed Unix to rise and become a commercial success.
After getting accepted by many researchers, Dennis Ritchie and Ken Thomson rewrote the Unix operating system in the C language. Then, it was sold to Novell and IBM. Unix was also distributed for free to the computer science departments of many universities because Unix was mainly used for research purposes. Many features were added by the researchers at the University of California, Berkeley. Thus, the university later released its own version of Unix called BSD or Berkeley Software Distribution. BSD also quickly gained success and was adopted by DARPA.
In the mid-1980s, there were two central operating systems: Unix, developed by AT&T and Berkley’s BDS Unix. Both operating systems had various releases with more advanced features.
2.3 Genesis of Linux:
The portability of Unix gave it popularity and commercial success. In the 1990s, AT&T filed a lawsuit against the developer of BSD, which halted further development. And then, the emergence of Richard Stallman’s GNU initiative to develop a free Unix-like operating system, but unfortunately, it failed to get community support. By the end of the 1990s, there was enough material for a developer to create his/her operating system kernel.
In 1991 a Finnish computer scientist Linus Torvalds revealed a new operating system kernel was in development. It was a hobby and personal project of Linus Torvalds. In 1987, a Unix-like operating system called MINIX was released to target the educational institutions. The MINIX code was accessible for research, but any modification and redistribution were not allowed, which pushed Linus Torvalds to work on his operating system for the 80386 processor.
Torvalds released the first version of Linux and distributed it on the internet. Linux was widely implemented by the open-source community and refined over the years. The contribution of the open-source community cannot be belittled because the open-source developers ported the desktop environments, file management system, FTP support, internet browsers, and a lot of free tools for Linux. Even being open-source, Linux becomes one of the most concise, stable, and secure operating systems.
Linux is also called a Unix-like operating system, though it was open-source and still strictly followed the Unix standards. The official standard of Unix-like operating systems is termed POSIX. The standard defined how a Unix-like operating system needs to function with specific sets of rules. So, Linux was built by following POSIX standards.
Linux is currently managed by Linux Foundation, and Linus Torvalds is associated with this company for the improvement and development of the kernel.
2.4 The Linux Mascot (Tux):
Linux is one of the most remarkable technological achievements of modern computer science. It is a feat built by the efforts of the open-source community. The official mascot of Linux is a penguin called Tux, which is also an open-source image and drawn by Larry Ewing in 1996. It was Alan Cox who visualized penguin to be an official mascot of Linux. Alan Cox was one of the developers of the Linux kernel. Larry Edwin took clues from Alan Cox and drew an image of a penguin in an open-source program called GIMP. The name Tux was coined by James Hughes and derived from “Torvalds’s Unix”.
3 Epitome of Linux:
Every modern operating system consists of three main components:
- Kernel
- Environment
- File structure
Similar to Unix, Linux also has these three components. The kernel, a core program of a computer, manages the hardware and execution of the programs. The kernel runs the commands fed by the user through the environment’s interface. At the same time, the file structure manages files and directories stored on the memory. Each directory can have subdirectories and may contain multiple files.
The kernel controls everything in your system. It is a small program that stays in memory and facilitates the communication between the hardware and software.
The environment is a graphical interface that makes it easier for the users to interact with the kernel. A user can create any directory, plus install and execute a program without directly interacting with the kernel through the command line interface. Graphical user interfaces do these tasks quite conveniently. There are many environments for Linux such as KDE, GNOME, and MATE. Distributions can deploy in any environment, while the user can change and modify it with any restriction.
The file structure is also a vital element of an operating system. Directories in Linux are usually in a hierarchical structure. Some folders in Linux are reserved for the operating system. A user can also create, move, and delete directories and subdirectories. All the directories originate from the root folder, and details are mentioned in the later section.
4 Getting Started with Linux:
Easy-to-use graphical user interface and graphical login system have made the use of Linux quite convenient. For many people, a simple command line interface is more convenient to use because it is much more straightforward compared to GUI, and many prefer a fully graphical environment.
Installation of most modern Linux distributions is easy because of the graphical installation process, and it only takes a few minutes to get a Linux distribution on your system. There are many distributions of Linux, but most of them have a similar procedure to install.
Another notable feature of Linux is that it provides extensive documentation for help. You can access online manuals and use the terminal to get detailed information about any utility. Moreover, the entire set of manuals provided by the Linux Documentation Project (LDP) also comes with your system distribution.
4.1 Accessing Linux through GUI:
When you first access Linux, the bootloader loads the kernel into the memory and then the graphical user interface. A login screen will appear to enter your username and password to access and use the Linux. This task is done through the display manager. Display managers provide graphical login capabilities, and apart from that, it monitors user’s sessions and login authentications, loads the display server and environment just after successful login. At the same time, a display server manages the graphical environment and interaction with the files in Linux. X is the commonly used display server, but it can be Wayland, a modern display server with additional capabilities.
The user interface depends upon the distribution. Most of the distributions use GNOME Display Manager (GDM) or KDE Display Manager (KDM). If any problem occurs while using a user interface, you can exit it by pressing CTRL+ALT+BACKSPACE keys or switching to the CLI (command line interface) CTRL+ALT+F1 keys. After solving the issue, you can switch back to GUI by pressing CTRL+ALT+F7.
4.2 Accessing Linux through CLI:
If you are accessing Linux through CLI, the procedure is pretty much the same as GUI. The minimalist interface will prompt you to enter your login details. If the entered credentials are wrong, the CLI will display an error. Note that while typing your password, the CLI will not display anything to protect your password from being accessed by others. However, you can erase the password by pressing BACKSPACE.
Once you successfully logged in, CLI will show that you are in the “home” directory, and it will wait for the command from the user. The CLI will prompt the “$” sign, which means the user is a regular user. If it is the number “#” sign, the user is the root user.
If you are accessing Linux through CLI, then everything will be operated through the terminal commands. Similarly, to log out, shut down, or reboot your system, you have to type the related command.
For switching user, log out:
For shutting down, use:
To force the system to shut down, press and hold “CTRL” and “ALT” keys and then press “DEL”.
5 The Linux Shell:
The shell is the key component of Linux. A small program, also known as a command interpreter, receives the command as input and sends it to the kernel to perform the commanded operation. The CLI can be accessed in both GNOME and KDE environments through an app called terminal. The shell allows a user to interact with the system’s kernel directly. Moreover, you can also use sets of commands in a Bash script to perform a task.
There are many types of shells, such as:
- Bourne Shell
- Bourne Again Shell
- Z-Shell
- Korn Shell
- C-Shell
Though there are multiple shells, the widely used shell is Bourne Again Shell or Bash because it contains the prominent features of both Korn Shell and C shell, and it comes as a default shell with many Linux distributions.
5.1 Linux Command Line:
The command line interface gets input in the text form and interprets it for the kernel. Upon launching the CLI, there will be a dollar sign “$” (“%” for the C-Shell). You can type the command next to the “$” sign.
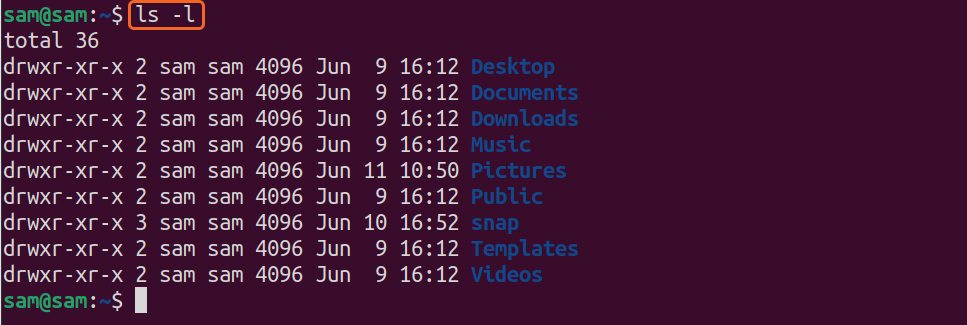
If you type “ls” after the “$” sign, the terminal will display files and folders in the current directories. Many commands have their own set of options, also called flags. Flags are added with the commands to enhance their basic functionality.
For more elaborated output, various options can be used, such as “l”, the options or flags will always begin with a dash “-”:
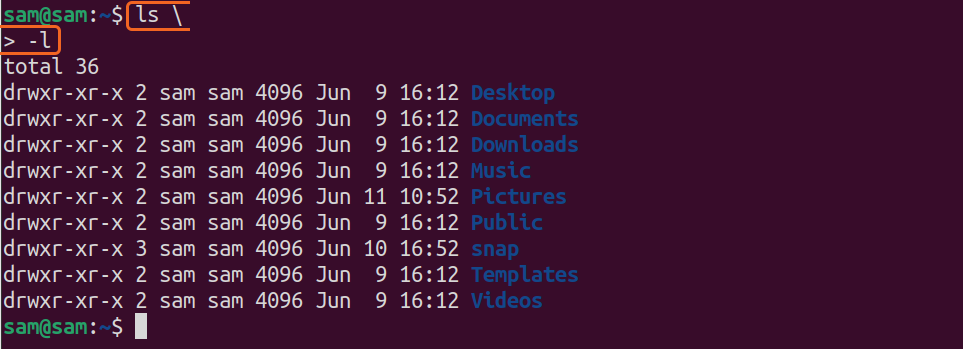
Commands can be entered on multiple lines by using backslash “\”.
>-l
Similarly:
>my_folder
The “rm” command erases any folder or file.
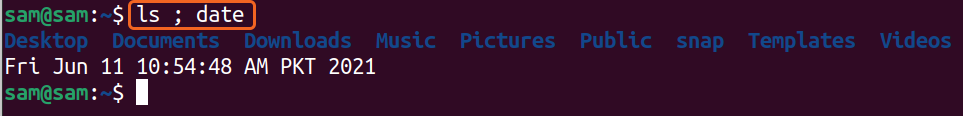
Several commands can also be executed simultaneously by using the semicolon “;”.
The above command will give a list of the files and the date in the standard output. You can interrupt any running command by pressing “CTRL+C”.
5.2 Editing in the Command Line Interface:
Editing and modifying commands in the Bash shell are relatively simple compared to the other shells. Every command you enter can be modified before executing. You can move anywhere in the command line, delete or insert any word or character, particularly in complex commands. There are specific keys; for instance, to move forward by a character, use “CTRL+F” or the “RIGHT” directional key, and to move backward by a character, use “CTRL+B” or “LEFT” directional key.
Likewise, to delete a character, use the “CTRL+D” or “DEL” key, and to delete a character before the cursor, use “CTRL+H” or “BACKSPACE”.
Navigate the cursor to a point where you intended to add the text, navigate the cursor to the point where you want to insert the text. To cut a character, use “CTRL+W” or “ALT+D”; then, to paste it, use “CTRL+Y”. To edit the characters in the commands, the “CTRL” key will be used, and to modify the word in the shell, “ALT” versions of the commands will be used. In addition, to execute any command, press the “ENTER” key. The keys associated with editing the commands are stored in “/etc/inputrc”. Any user can modify the command line editing keys by modifying “/etc/inputrc” file. Commonly used keys to edit commands in shell are mentioned in the following table:
| Movement Control keys | Action |
| CTRL+F, RIGHT-ARROW | To move the pointer ahead by one character |
| CTRL+B, LEFT-ARROW | To move the pointer back by one character |
| CTRL+A or HOME | To move the pointer to the beginning of the command |
| CTRL+E or END | To move the pointer to the ending of a command |
| ALT+F | To navigate ahead by a word |
| ALT+B | To navigate back by a word |
| CTRL+L | To clear everything |
| Editing Keys | Action |
| CTRL+D or DEL | Removes the character the pointer is on |
| CTRL+H or BACKSPACE | Removes the character before the pointer |
| CTRL+K | Cut the remaining line after the pointer |
| CTRL+U | Cut the entire line before the position of the pointer |
| CTRL+W | Cut the previous word |
| CTRL+C | Cut the entire line |
| ALT+D | Cut the remainder of the word |
| ALT+DEL | Cut the word from pointer to the beginning |
| CTRL+Y | Paste the cut text |
| CTRL+V | To insert quoted text |
| ALT+T | Transpose two adjacent words |
| ALT+L | Lower case the current word |
| ALT+U | Upper case the current word |
| ALT+C | Capitalize the word |
There is another notable feature of the Bash shell that auto-completes commands and paths. The auto-completion of the command can be performed using the Tab key. If multiple directories or files start with the same name, double press the Tab key; the shell will prompt all the directories starting with the text string mentioned in the command. The auto-complete function also works with users, variables, and hosts.
For instance, auto-complete the directory, type “Dow”, and then press the Tab key, the shell will auto-complete it.
$ls Downloads/
If there are multiple directories with the same name, only one letter may not auto-complete upon a single Tab press. Press the Tab key one more time to check the possible files. To list possible auto-completion in the shell, press CTRL+R.
| Keys | Action |
| Tab | Auto-completion |
| Tab Tab | List of possible completion |
| ALT+/ , CTRL+R+/ | File name completion, normal text |
| ALT+$, CTRL+R+$ | Variable completion |
| ALT+~, CTRL+~ | Username completion, ~ for auto-completion |
| ALT+@, CTRL+R+@ | Host name completion , @ for auto-completion |
| ALT!+, CTRL+R+! | Completes the command and text |
5.3 Managing Command History in Linux Shell:
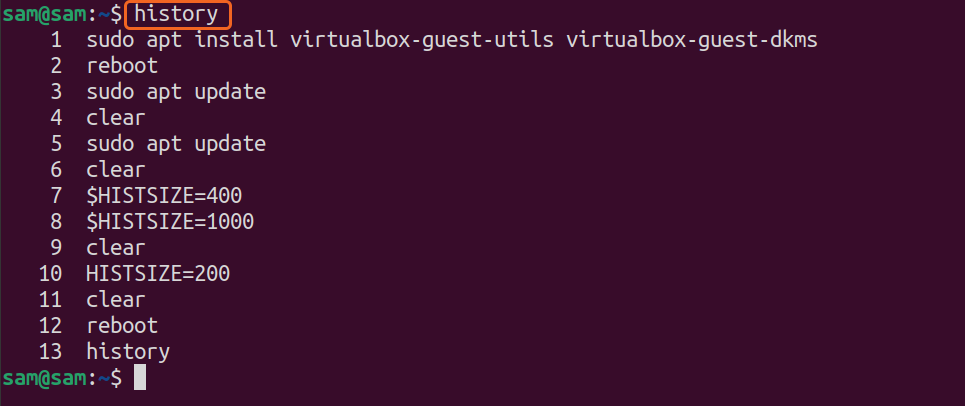
Bash shell also keeps the history of the previously executed commands. Any user can browse through the executed command using the UP and DOWN key. The default size of commands that the shell keeps is 500. To check the recently executed commands, type “history” in the command line interface:
A list of keys to use to browse through the history of commands are mentioned below:
| Key | Action |
| CTRL+P, UP KEY | Browse up in the event list |
| CTRL+N, DOWN KEY | Browse down in the event list |
| ALT+< | Displays the first event |
| ALT+> | Displays the last event |
| CTRL+R | Reverse increment search |
| !<CommandNumber> | Displaying and executing a command by index number |
| !! | Displaying/reference the previous command |
| !< character> | Reference the command starting with a specific character |
| !?pattern? | Reference a command starting with a specific pattern |
| !- CMD# CMD# | Displays a range of events |
The events can also be referenced using the “!” sign; you can use the command number. If you don’t remember it, simply type the first few letters of the command. For example:
Or:
Referencing can also be done using a negative number. For instance:
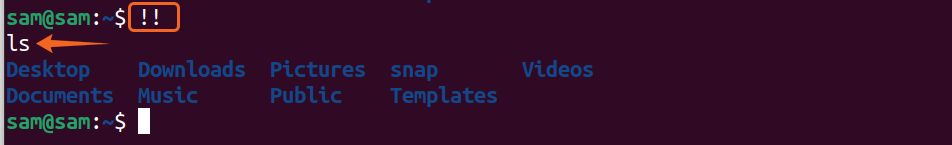
If there are ten commands, the output would be the fifth command from the end of the history list. And to reference the last command, use “!!”:
History can be edited by referencing the event; the commands in the history can also be termed as an event. There are two main approaches to edit commands: 1. You can reference and edit in the command line with its editing capabilities, or 2. You can also use the “fc” command to open the referenced events in the text editor. The “fc” command assists in opening, modifying, and running the multiple commands.
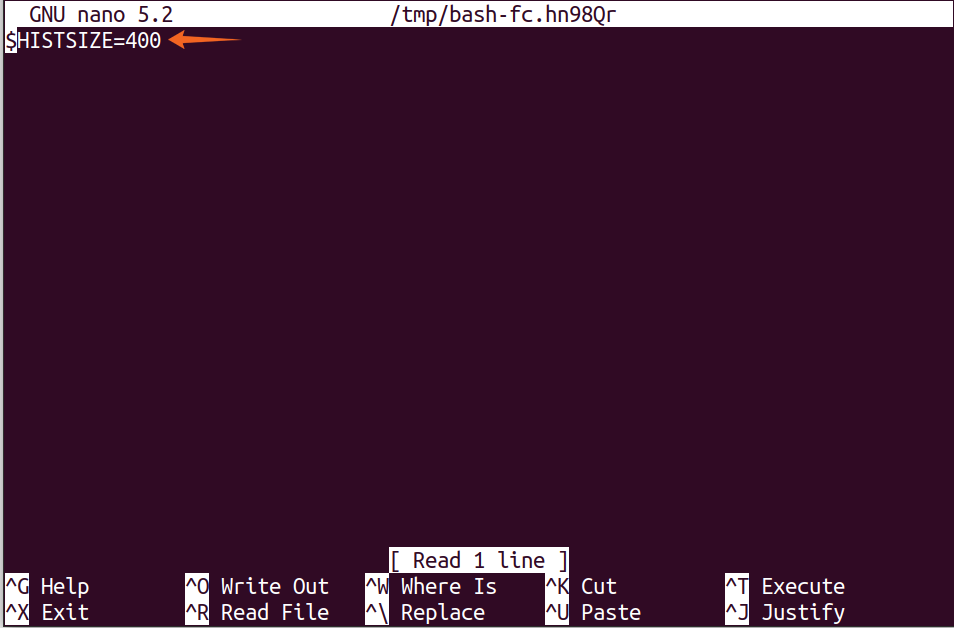
In the command-line editor, many hotkeys can be used to edit the command, as mentioned above. Let’s understand how to edit the referenced commands using “fc”. The “fc” command lists different commands in the editor and executes them:
The above command is referencing the third command in history, which is “$HISTSIZE”. It will open the command in the default text editor, where you can modify the command. Upon saving, the commands will execute, and a range of commands can also be selected:
The above command will open a range of commands from numbers 3 to 5 in the default text editor.
5.3.1 Modifying the History Size in Linux Shell:
The number of events that can be kept in the history is assigned to a variable called “HISTSIZE”, and the default size is 500. However, the size can be changed to any size by assigning the new value:
The above command will limit the number of events saved in the history to 200.
5.4 Filename Expansion in Linux Shell:
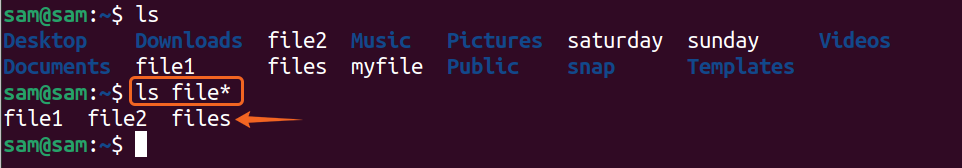
Your system may contain hundreds of files, and it is impossible to remember the name of each file. In this particular case, file globbing can help. The shell comes with a set of special characters, also known as wildcard characters. And these characters are asterisk “*”, question mark “?”, and square brackets “[]” that facilitate in searching the display in the file containing a specified string of characters.
The asterisk “*” can be used anywhere, either at the start of the text or ending. For example:
The asterisk can also be used with the combination of the characters:
Files can also be listed by their extension using asterisk “*”. For example, there are multiple images in a directory, and to display images of a specific extension, use the command:
The asterisk can also be used to remove multiple files at a time.
The question mark “?” is more specific compared to the asterisk “*”. The “?” is used to match exactly one character. For example:
And the square brackets “[]” are used to match the characters inside the brackets:
For range:
| Special Character | Action |
| * | Matches zero or more characters |
| ? | Matches one character exactly |
| [] | Matches a class of possible characters |
Wildcard characters can be part of the file name; in this situation, use slash “\” or simply quote (“”) with the name:
myfile?
myfile?
In many cases, the directories contain space in their names. The command line does not recognize space and gives an error. To overcome it, use the either slash “\” or quotes. For example:
The above command will give you an error. To rectify, use:
Or:
5.5 Redirection in Linux Shell:
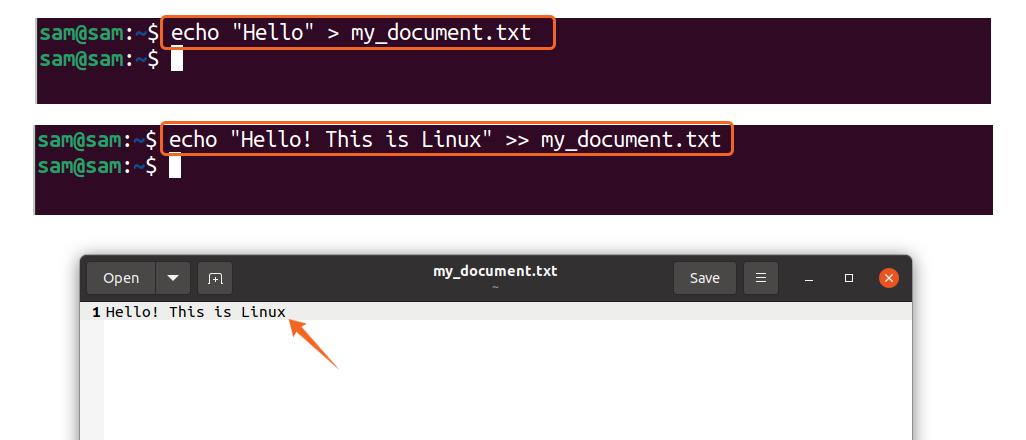
Redirection is another noteworthy utility of Bash. To redirect input, output to a file, or a command, redirection operators are used:
The above command will create a text file if it does not already exist in the directory and put the text “Hello Linux” in it. If the “my_document.txt” is already in the directory and contains the text, the new text will overwrite the older text:
In the above command,“>>” is used to append text to the existing files. There is some other redirection operator that are mentioned in the table below:
| Redirection Operator | Action |
| > | Redirects the standard output and overwrites the existing content |
| >> | Redirects the standard output and appends the existing content |
| < | Redirects the standard input |
| 2> | Redirects standard error |
| 2>> | Redirects and appends the standard error |
5.6 Pipes in Linux Shell:
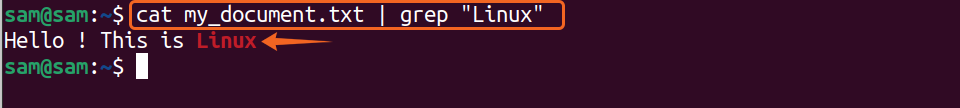
The pipe is used to send the output of one command as input of the second command, and the sign “|” is called the pipe operator, which can also be used for filtering:
The above command will send the output of the “cat” command to the “grep” command, which will search the specified text from the output of “$cat my_document.txt” and display it as standard output.
6 The Shell Scripting and Programming:
The shell commands can also be used to run in the form of a script. If you need two or more commands to execute and perform a specific task, a shell script can be used. The shell can assist in handling repetitive tasks. Shells provide different tools for programming, such as defining a variable, assigning a value to a variable. Moreover, the shell also provides loops, conditional, and tools for user interactivity. All the tools work the same as any other programming language works.
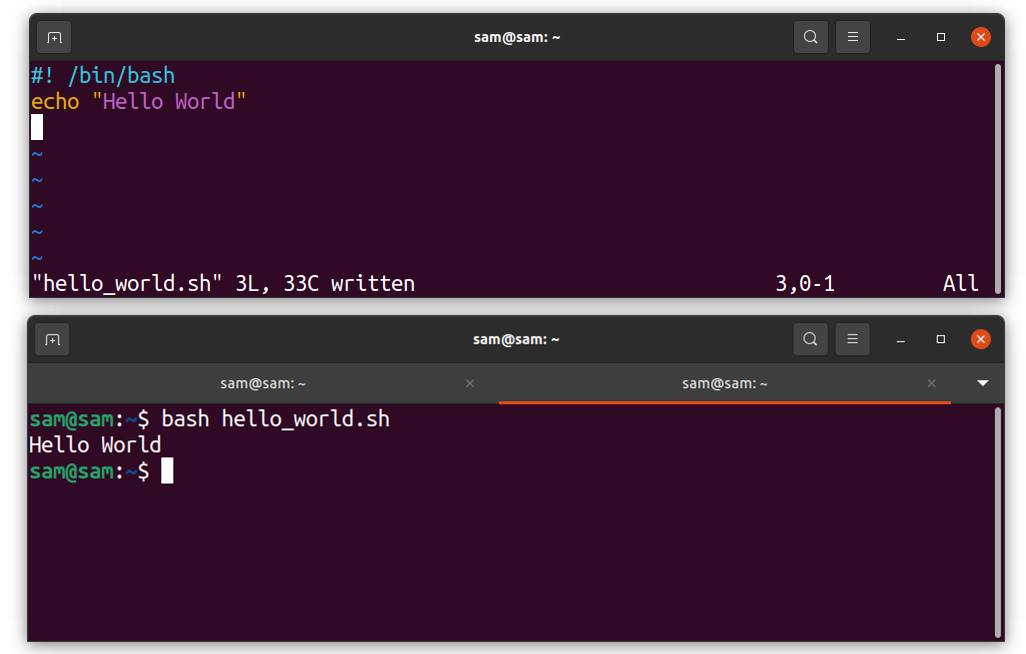
echo “Hello World”
The Bash scripting does not need any specific editor. Use any editor, for instance, nano or vim. Characters #! with the path to the interpreter (/bin/bash) in the above script are called bang or shebang. Save the script with the .sh extension, and to run the script, used the Bash command as follows:
The script can be made more advanced by adding user interactivity, conditional statements, and loops.
6.1 Creating a Variable in Shell Scripting:
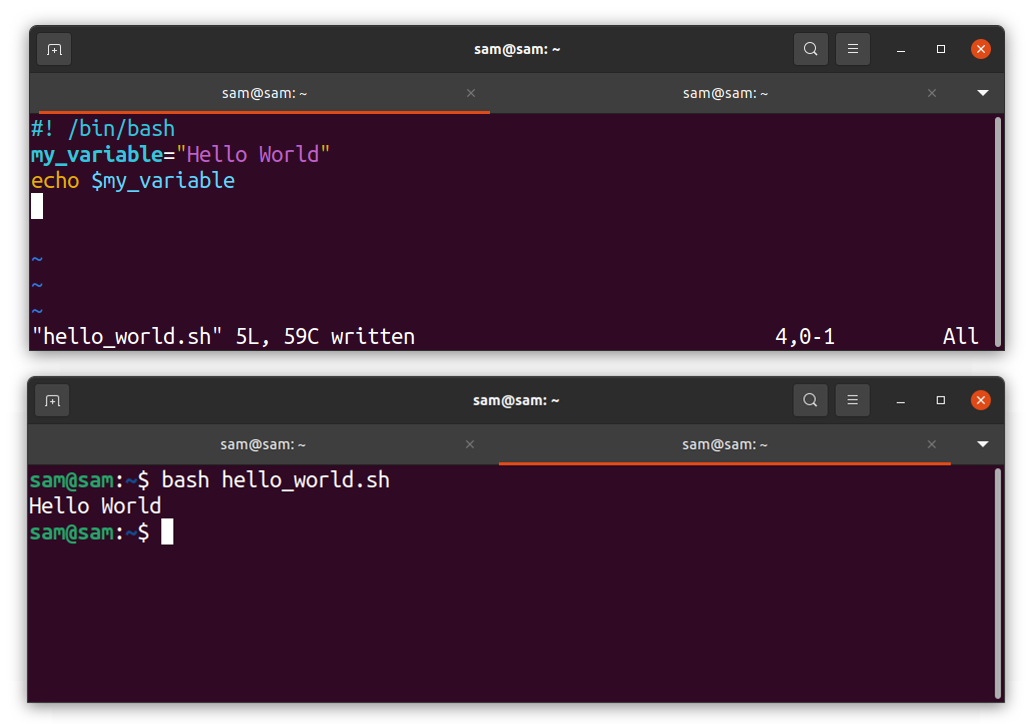
Variables are the key element of any programming language. Variables are used to hold information that can be modified in the code, which can be a word, a string, or a character.
Mentioning data type is not mandatory:
my_variable = “Hello World”
echo $my_variable
Variable can be accessed using the dollar sign “$”:
6.2 Conditional Statements in Shell Scripting:
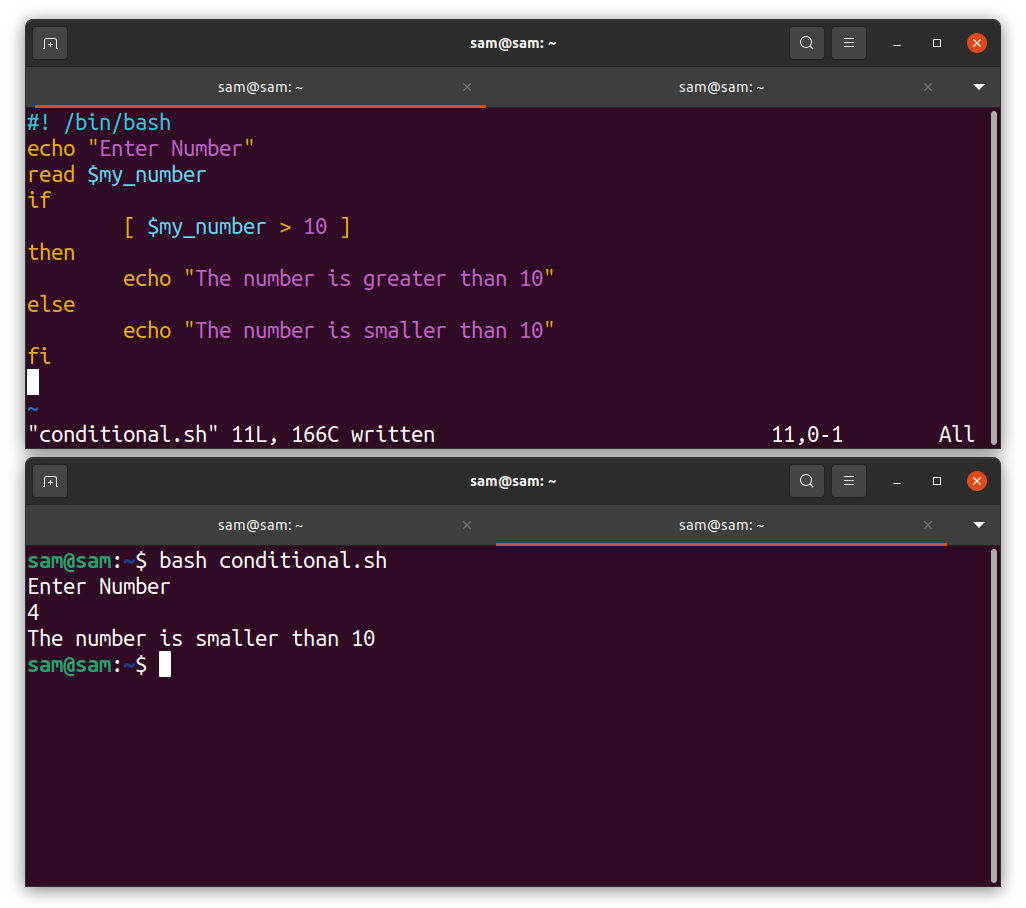
Like any other programming language, Bash also comes with the support of conditional statements. In addition, Bash supports both if-then and nested if-then:
echo “Enter Number”
read my_number
if [ $my_number > 10 ]
then
echo “Number is greater than 10”
else
echo “Number is smaller than 10”
fi
Provide the condition in the square brackets after “if”. Note the if statement must end with “fi”. If the condition is true, the “Number is greater than 10” will be displayed. Otherwise, the “Number is not greater than 10” will be printed. The conditional structure used in Bash are given in the table below:
| Conditional Statement | Action |
| if command
then statement fi |
If the check command is true, the if will execute |
| if command
then statement else statement fi |
if-then executes if the check command is true; otherwise else action will be executed |
| if command
then statement elif command else statement fi |
Nested if structure: enables to add multiple check commands |
A list of commonly used operators are given in the table below:
| Comparison | Action |
| For Integers | |
| -eq | Equal |
| -gt | Greater than |
| -lt | Less than |
| -ge | Greater than and equal |
| -le | Less than, and equal |
| -ne | Not equal |
| For Strings | |
| = | Checks if the strings are equal |
| -z | Checks if the strings are empty |
| != | Check if the strings are not equal |
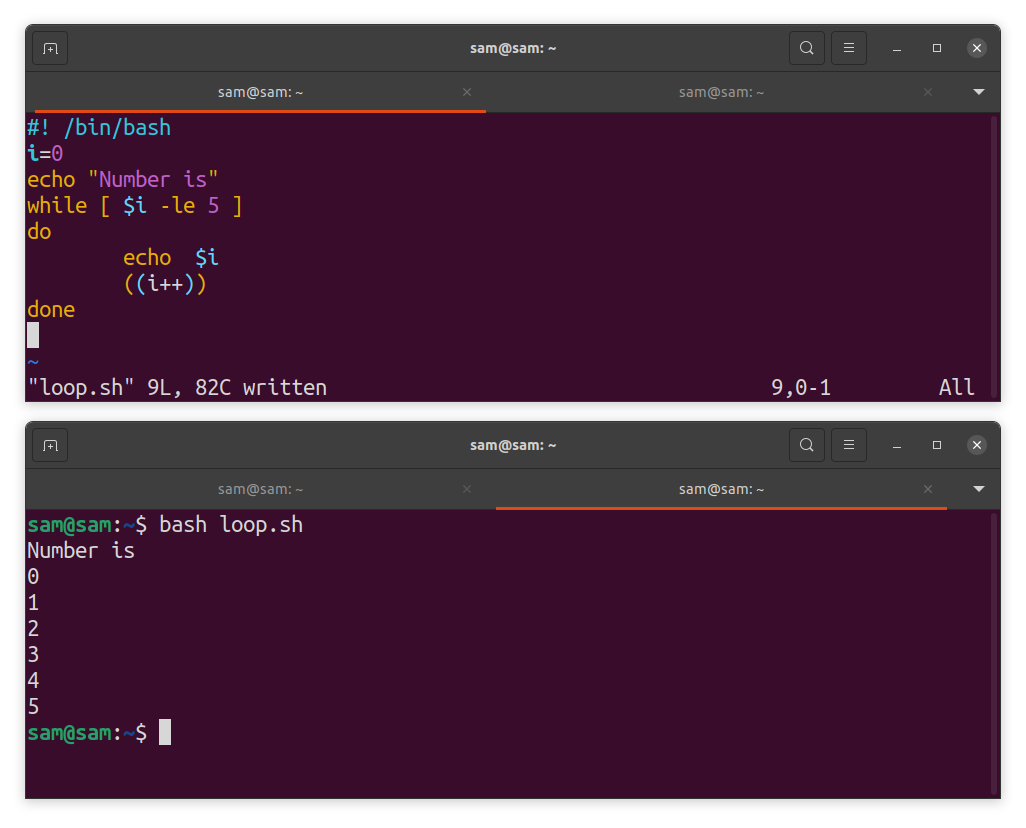
6.3 Loop Structures in Shell Scripting:
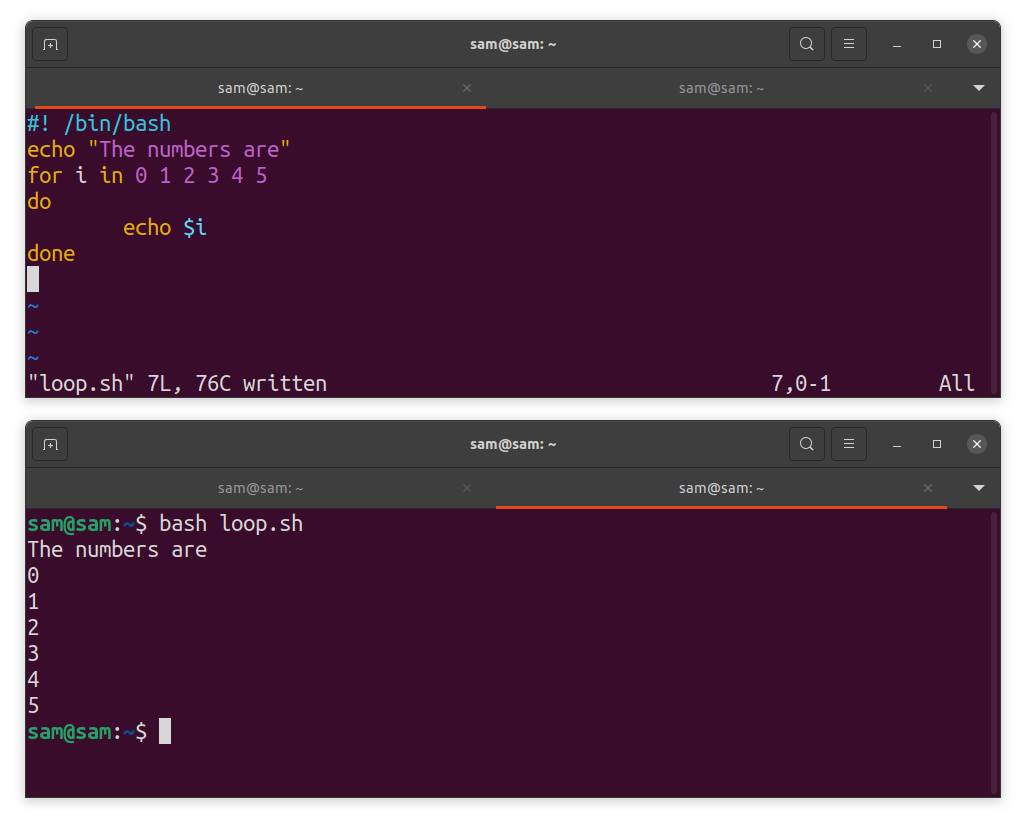
Loops are another useful programming structure in Bash scripting. Commonly used loop structures are for loop and while loop and Bash support both:
echo “The numbers are”
for i in 0 1 2 3 4 5
do
echo $i
done
The program will print numbers 0 to 5.
i=0
echo “Number is”
while [ $i -le 5 ]
do
echo $i
((i++))
done
The above program is implemented with a while loop.
| Loop Structure | Action |
| for variable in list
do statement done |
for-in design to loop through a list of values |
| while condition
do statement done |
while-do designed to loop until a specified condition is met |
| select variable in list
do statement done |
Creates a menu |
7 Linux Files and Directories:
In Linux, files are organized in a hierarchical structure. The file can be referenced not only by its name but by the path as well. There is no restriction, and a user can make as many folders as he or she intends. Furthermore, a user can perform various operations such as moving, copying, erasing, etc. Desktop environments like KDE and GNOME both provide the functionality to perform the actions formerly mentioned.
A directory can be created using the command “mkdir”; you can name it anything. It is a better practice to join directory name words using underscore “_”, though you can use quotes or escape sequences to mention the path of a directory with space in its name.
7.1 Hierarchy of System Directories:
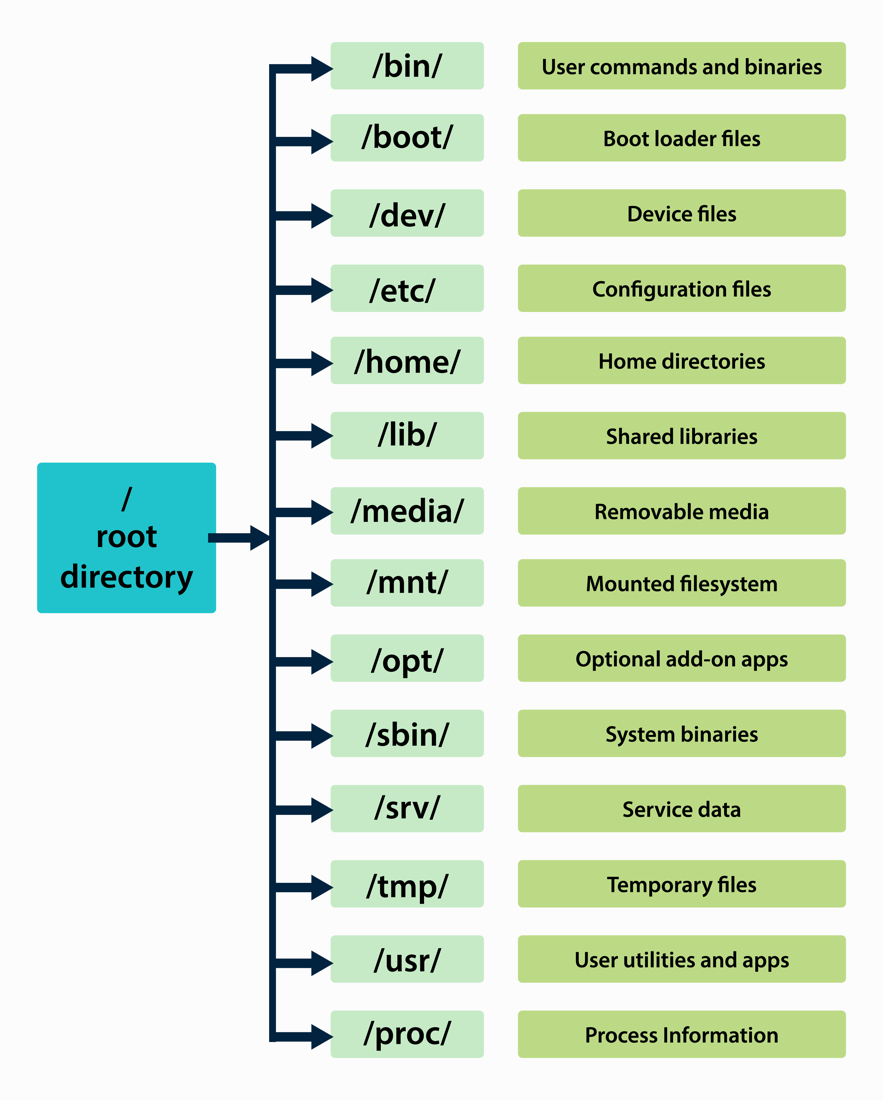
Everything in Linux is located under the root directory “/”; the root directory contains all the files needed for the system. For example, boot files, packages, temporary files, libraries, etc.
To view and display a file, the “cat” command is used. The “cat” command spreads the entire text on the screen to overcome this issue. In addition, the “less” and “more” commands are used. A list of commands that are used in managing files in Linux is given below:
| Command | Action |
| mkdir | Creates a directory |
| rmdir | Deletes a directory |
| ls | Lists directories |
| cd | Changes directory |
| pwd | Display path of the current directory |
| ~/path | Tilde (~) is a unique character that represents the pathname of the home directory |
| Command | Action |
| ls | Lists the file and directory names |
| cat file | Displays file in the standard output |
| less file | Displays the file screen by screen, use “space bar” key to move to the next page |
| more file | Displays the file screen by screen, use “space bar” key to move to the next page |
| lpr file | Sends the file to the printer |
| lpq | List the printing jobs |
| lprm | Delete a job in the printing queue |
| cp | Copying the files |
| rm | Remove the files or directory |
| mv | Moving the files |
7.2 Archiving the Files:
The process of collecting multiple files into one file is called archiving the files. In Linux, there are numerous archiving utilities. You also can compress the archives. Archiving and compressing files are quite handy when making a backup or sending files through FTP over the internet. Compressing files decreases the file size, making it easy to download even on a slower internet connection. The commonly used archiving and compression utilities are zip, gzip, tar, and bzip.
The tar is a well-known archiving utility, which stands for Tape Archive. And to compress tar archives such as zip, gzip, bzip2, and xz, use the following commands for the desired actions:
| Command | Action |
| tar -cf filename | To archive the file |
| tar -xf filename | To extract the archive |
| gzip filename | To compress the file with gzip |
| bzip2 filename | To compress the file with bzip2 |
| zip filename | To compress the file with zip |
To get more information about tar utility, type “man tar” in the command line interface.
8 Linux Desktop Environments:
The desktop environment combines interactive windows and various graphical elements such as icons, widgets, and toolbars to provide a graphical user interface (GUI). It is a desktop environment that determines how the operating system will appear.
Linux has numerous desktop environments that are graphical interfaces used to communicate with the kernel. It is optional, and you can perform all the tasks in the command line interface (CLI), a minimalist program to command the kernel. However, the GUI makes these interactions with the system more straightforward and easy. A desktop environment has now become essential for every operating system.
A combination of kernel, set of utilities, and a desktop environment makes an operating system, and any Linux distribution does it all without costing you a single penny. Many people are ambiguous about the Linux naming convention. Linux is just a kernel that is useless without software interactivity. However, bear in mind an operating system is incomplete without a kernel. Linux is a kernel, whereas the operating systems that are using Linux kernel are called Linux distributions.
The open-source community has made various flavors of Linux distributions. Most of the Linux distributions are similar with minor differences. For instance, many Linux distributions would have the same functionalities and capabilities, but the only difference they offer is the desktop environment appearance. Too many distributions of the same operating system sometimes cause users to be perplexed. But on the bright side, it gives the freedom to choose a distribution that is comfortable to use. Unlike proprietary operating systems, in Linux distributions, you can change the desktop environment anytime. So you don’t have to deal with a similar look all the time.
A desktop environment is made up of a window system and a graphical user interface. The window system in Linux is called X window system, and the common environments are GNOME and KDE.
8.1 X Window System:
The window system of any operating system provides a fundamental framework for drawing and displaying windows with keyboard and mouse interactivity. Linux and Unix use the same X window system, or simply X. The X windows systems are reasonably flexible when it comes to configuration. Almost all video cards support it. X window system is not specific to any particular interface. It provides sets of tools such as window managers or file managers to be utilized and modified according to any operating system settings.
The three main components complete the X window system. The X server, Window System, and X client. The X server maintains the windows and hardware interactivity. It receives inputs from the hardware, passes them to the client applications, and displays the output. The X client is a program that communicates with the X server, Xterm, Xclock, and Xcalc. To get the X window system, it is required to install the X window server. The X window server can be downloaded from either xfree86.org or ww.x.org.
8.2 GNOME:
GNOME is a well-known desktop environment, and it is being used by many Linux distributions. This easy-to-use and powerful graphical environment abbreviates as GNU Network Object Model Environment. GNOME is a free desktop environment and the default DE of Red Hat, Fedora, and Ubuntu.
GNOME contains all the components that an environment needs, such as window manager, web browser, and file manager. The file manager GNOME uses is called Nautilus. As far as the window manager is concerned, any window manager can be used that is compatible with GNOME. The notable features of GNOME are mentioned below:
- Each and every element of GNOME is designed to make it user-friendly. Everything is in place and easily accessible, whether it is a file, directory, or any application
- It is more intuitive with a powerful search system and the side-by-side windows
- Clean notifier for notifications
- Multi-desktop support
8.3 KDE:
KDE is also known as K Desktop Environment, and it also includes all the standard desktop features. KDE is a combination of experience with both macOS and Windows operating systems. The KDE project distributes it under the GNU general public license. It is designed to work on any Unix-based operating systems, including Linux, Solaris, HP-UX, and FreeBSD. It uses the Qt library for GUI tools which Trolltech develops.
KDE has its own window manager known as Kwin and Dolphin file manager in its latest release. The desktop panel used in KDE is called Kicker. KDE is a combination of multiple applications, which makes it a proper desktop environment. These applications are mentioned below:
- KDE allows you to handle multiple workspaces, also known as Activities
- The app used for RSS is called Akregator, which lets you read the latest articles from various blog websites
- To play an audio file, the Amarok application is used, and the media player of KDE is called Dragon
- To manage personal information, KDE comes with an app called Kontact
- Network-related options such as FTP, SSH are managed through KNetAttach, a network wizard
Just like other desktop environments, KDE is also highly customizable. Every element of the environment is customizable.
Apart from these well-known desktop environments, there are many lesser-known desktop environments, such as Mate, Xfce, LXDE, Cinnamon, LXQt, Pantheon, Budgie, Fluxbox, Sugar, i3, and Enlightenment. Moreover, Linux provides the flexibility of customizing the desktop environment. Many modern Linux distributions even give a list of desktop environments to select from during installation.
9 Linux Software Management:
Applications are core to any operating system. Installation and uninstallation of applications in Linux have always been relatively easy. There are various package management tools. Packages in Linux are packed into special formats, which are managed through package management tools. The commonly used package management tools are the Red Hat Package manager (RPM) and the Debian Package Manager (DEB). They are the special archives for packages and contain all the package-related files, dependencies, and libraries. To install any package, package managers also track the libraries and dependencies of other installed packages while installing a new package to run without any error.
Software of Linux distributions is kept in repositories. Repositories are storage locations where packages and updates are stored. So, when you try to install any software package on Linux, you pull the software files from the respective repository. Unlike other operating systems where software has specific extensions and can be installed by clicking on it, Linux has a different approach. Package managers simplify installing, removing, and updating the software packages.
The commonly used package managers are listed below:
- Synaptic package manager (Snap)
- DPKG — Debian Package Management System
- RPM — Red Hat Package Manager
- Pacman Package Manager (Arch Linux)
- Zypper Package Manager (openSUSE)
- Portage Package Manager (Gentoo)
9.1 What is Open-Source Software?
The advancement of Linux is a collective effort of the community support and developers who helped in the creation of numerous key components that an operating system needs. Anyone can develop an application for Linux and publish it on a website to make it available to download for anyone. Linux development has always been managed on the internet.
Most of the software developed for Linux is open-source, which means the program’s source code will be available for access. That means any programmer can contribute to improve the program and add new features to the existing software. SourceForge is the largest online source that provides open-source applications. Most developers use this platform to publish their software.
Open-source software is released under public license, which ultimately prevents any other source from utilizing the code and selling it commercially. The most well-known license is the GNU GPL. It retains the copyright of freely distributed software. Some other licenses, such as Lesser General Public License (LGPL), allow commercial companies to use some software libraries under GNU license. Similarly, the Qt public license (QPL) allows open source developers to use Qt libraries; for detailed information about open-source licensing, visit opensource.org.
Linux currently falls under the GNU license. Many applications that come with Linux distributions, such as Vim, Bash terminal, TCSH shell, TeX, and C++ compilers, are also a part of open-source software under GNU license.
According to the GNU licensing term, the original developer retains the copyright and can modify the source and redistribute it with source code. Many tech companies are natively releasing their major applications for Linux.
9.2 Linux Applications:
On Linux, you can get almost all types of applications, whether it is Office Suite, graphics tools, development tools, web, and network tools. There are many applications from Windows and macOS that are now natively available in Linux. But you will get a free alternative to every app on the Linux operating system. Some well-known Linux applications are mentioned in the list below:
| Office Suites |
| LibreOffice |
| FreeOffice |
| Apache OpenOffice |
| Calligra |
| OnlyOffice |
| Multimedia and Graphics Apps |
| Gimp |
| digiKam |
| Krita |
| Inkscape |
| Rhythmbox |
| VLC Media Player |
| Mail Apps |
| Thunderbird |
| Evolution |
| Geary |
| Sylpheed |
| Claws Mail |
| News Apps |
| Akregator |
| RSSOwl |
| QuiteRSS |
| FreshRSS |
Apart from the apps mentioned above, you will get many apps related to the web, tools, and utilities related to databases and networks.
10 Security:
Security is an essential aspect to keep in mind while using any operating system. Linux has a good reputation when it comes to security because it offers many tools for encrypting data, integrity checks, and digital signature. GNUPrivacy Guard (GPG) encryption package allows you to encrypt your message or data and be used for integrity checks. The tool was introduced by Pretty Good Privacy (PGP) and later became a part of PGP and OpenPGP. Any project can use OpenPGP for security.
10.1 Public-Private Keys for Encryption:
The public key is a large number of numeric characters used to encrypt data and generate any software or utility. Encryption cipher the data in such a way that it generates a corresponding decrypt key. Previously, there used to be only one key for encryption and decryption. At present, there are two discrete keys. The public key encrypts data, while the private key is utilized to decrypt it. The host and the client both have a pair of public and private keys.
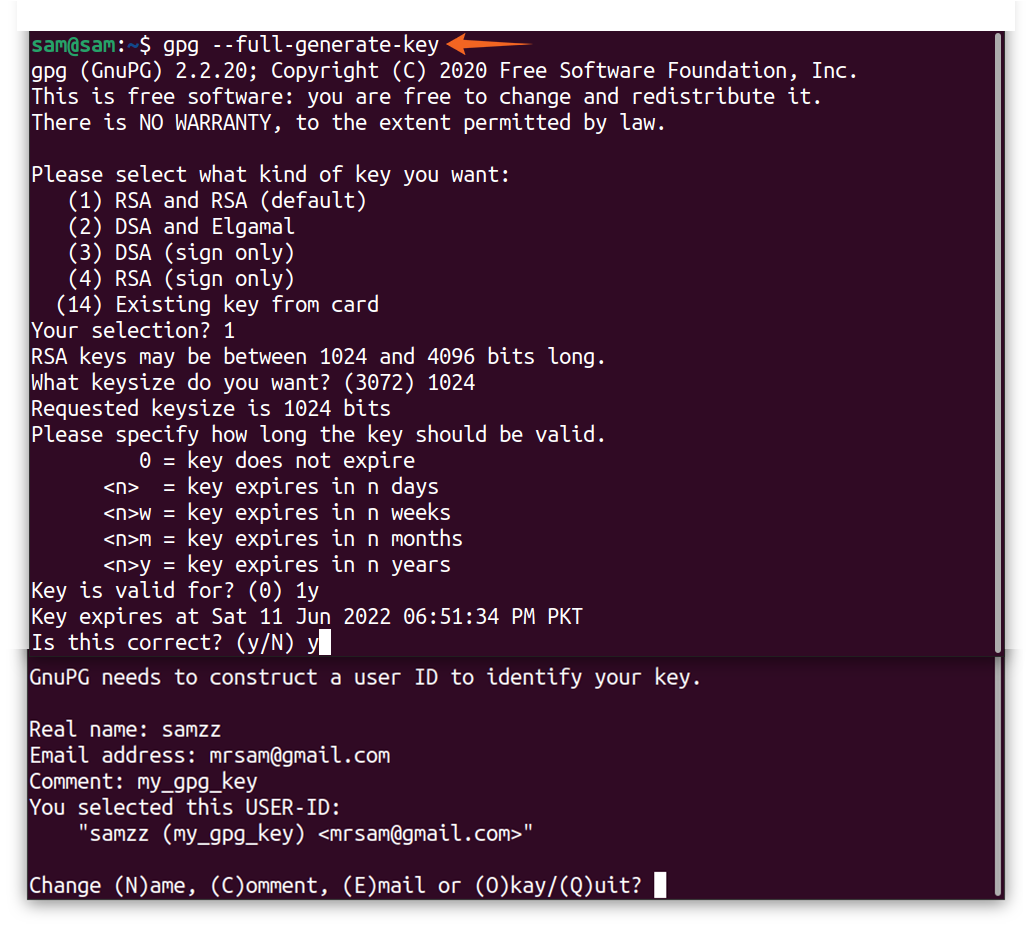
To send an encrypted message to a receiver, first, you need the public encryption key of the receiver. Then the receiver will use his or her private key to decrypt the message. In Linux, every user can have a public and private key. The “gpg” utility is used to create public and private keys.
10.2 Digital Signature:
Digital signatures are used to check the integrity of the message a user received. It makes sure that the data is not compromised while routing. Thus, digital signature enhances the security of data transfer.
Digital signing a message means generating a checksum using a hash algorithm such as MD5, SHA2, or SHA3. The checksum hash algorithm will generate a unique value that accurately represents the message. Any changes in the message will change the value.
10.3 GNU Privacy Guard (GPG):
Most of the Linux distributions use GNU privacy guards to protect communication. The GnuPG encrypted and digitally signed the message. While the KMail and Thunderbird both use GnuPG for encryption. To perform any GnuPG operation, the “gpg” utility is used. To generate your key, use the command mentioned below:
As mentioned above, to send a message to a user, you need their public key. Thus, to get the public key, the following command will be used:
The “user-public.key” is the file name. The key file would come with a “.key” extension. Other commonly used commands of the “gpg” are given in the following table:
| GPG Command | Action |
| gpg –edit-key name | Edit the keys |
| gpg –sign-key name | Sign public key with the private key |
| gpg –delete-key name | Delete the public key from the public keyring |
| gpg –delete-secret-key name | Delete both public and private key from the both public and private keyrings |
| gpg –export name | Export a specific key from your keyring |
| gpg –import name | Import keys into your public keyring |
10.4 Security-Enhanced Linux (SELinux):
In Linux, there were multiple utilities and tools to protect the specific service, but there are no particular tools to protect the entire environment at the administrative level. To protect Linux, a project was initiated by NSA (National Security Agency) and Red Hat developers called Security-Enhanced Linux or SELinux. Not just Red Hat, various other distributions also implemented SELinux such as Debian, Fedora, Ubuntu, etc.
SELinux is a kernel security tool that facilitates in implementing protection against misconfiguration and compromised daemons.
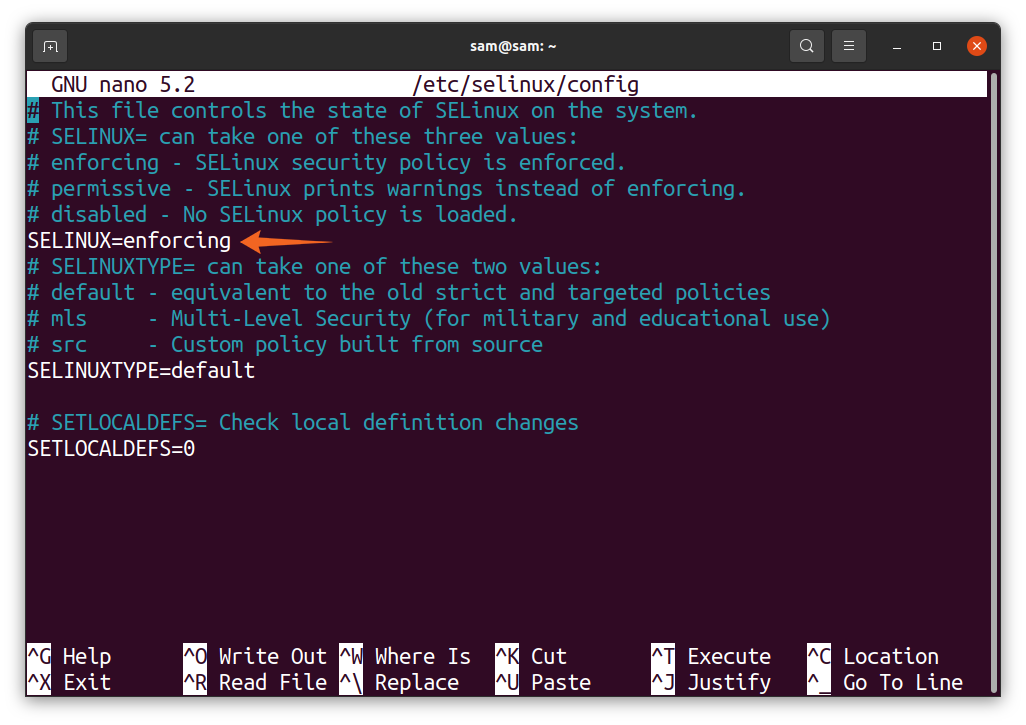
Modification in the SELinux configuration file is required to enable it. To disable it, open its configuration file, which is “/etc/SELinux/config” in any text editor and set the SELINUX variable to “disabled”:
To turn off the SELinux temporarily, use:
And to turn it back ON use:
Both Linux and Unix use Discrete Access Control or DAC for access restriction to the system. In DAC, users have access to the permission of files and programs. However, there is a weakness in this approach if an attacker gains access to a user account with administrative rights to access the entire system. To rectify this weakness, the National Security Agency (NSA) formed a Mandatory Access Control (MAC), which restricts the other users from accessing the objects in the operating system, where subjects are the running processes while objects are files or directories.
10.5 Multi-Level Security(MLS) and Multi-Category Security(MCS)
Multi-level security which is also known as MLS, is a refined form of access control. As the name suggests, MLS adds security levels to the different resources in Linux. A user with a specific security level can access specific files and folders.
On the other hand, MCS (Multi-Category Security) allows users to set categories and restrict access control to the files and folders by category.
10.6 Internet Security:
Internet security includes the security of web browsers, websites, and networks. It is essential not only for homes but for large businesses as well. Hackers continuously look for vulnerabilities on the internet to exploit. The data on any server is not safe until it gets secured by implementing proper security protocols. Therefore, internet security is needed. Internet security has preventing measures to protect the network from unknown access, malfunction, and modification. The proper network security assists in protecting communication over the internet and other valuable data on servers.
10.6.1 Internet Security Protocol:
IPsec is a protocol used to encrypt communication over the internet and protect the IP, which is a part of IPV6 and can be implemented on IPV4 also. IPSec is a combination of three protocols, AH (Authentication Header), ESP (Encapsulating Security Protocol), and IKE (Internet Key Exchange). It can be used for ciphering data and verification of the host and the host network. Through IPsec, the kernel automatically encrypts and decrypts incoming and outgoing traffic.
The AH (Authentication Header) ensures that the packet is from the original user, not from someone else; ESP encrypts and decrypts the communication while IKE exchanges the keys between sender and receiver.
10.6.2 Firewalls:
Systems are vulnerable, and there is always a threat of attack by external users. To protect the system from an attack by an external user, a Firewall is installed. A firewall is a protective wall or a security setup that supervises the network traffic in our system through rules defined by the user. A firewall is a fence between trusted and unknown networks.
Firewalls and ciphering data are the approaches to protect internet connection and prevent any direct unverified access. While encryption prevents data from being compromised, authentication ensures communication between the correct sender and the receiver. And to protect remote communication, the transmission of the data can be encrypted. Secure shell SSH tools can be used for encryption, while Kerberos is used for user authentication.
10.6.2.1 IPtables:
The IPtable is a utility used for packet filtering which is a robust method to swiftly configure the firewall for the system. Iptables are the combination of Tables, Chains, and Rules. There are five tables, and three main tables are Filter Table, NAT Table, and MANGLE Table:
- Filter Table: This is the default table and used to filter the packets. It decides whether a packet is allowed to reach its destination or to discard it.
- NAT Table: Termed as Network Address Translation, determine the rule to modify the source and destination addresses of the packet to route it according to NAT setup.
- MANGLE Table: This table is used to change the IP header of the packet by modifying the TTL (Time to live) of the packet.
- RAW Table: These tables are for connection tracking.
- SECURITY Table: This table is used to set the SELinux and tagging of the packet.
10.6.2.2 Rules:
Rules are commands that are used to modify the network traffic. Each packet will be checked based on the rule.
10.6.2.3 Chains:
Chains are rules that process in order. There are five chains in IPtable:
- Pre-routing: This chain is applied to a packet even before entering the routing
- Input: Packet enters the routing system
- Forward: Forward chain is applied when the packet route through your system
- Output: Output chain applied on all outgoing packets
- Post-routing: Post-routing chain is applied when the packet completes its routing
Every packet has to pass through the chain rules from pre-routing to post-routing in order.
10.6.3 UFW (Uncomplicated Firewall):
UFW is the front-end for managing the firewall rules in many Linux distributions. It is quite a simple, user-friendly utility and also available in GUI form. The primary purpose of designing the UFW is to make IPtables easy to use. It provides both IPV4 and IPV6 host-based firewalls.
11 Linux System Administration:
Linux is developed in such a way that it can manage multiple users. Users can have their own shells by which they can interact with the operating system, and it can be achieved by configuring the operating system. For example, you require to add new users, files system, devices, etc. Such operations are controlled through the System Administration. Only the system administrator or a superuser can provide such access. So there would be two different types of interaction: a regular user and a system administrator who performs the administrative operations.
11.1 Superuser(Root User) in Linux:
Root user or a superuser is a special account used for managing system administrative tasks. A root user has maximum permissions and can perform any operation. For example, as a superuser, you can change the password, add and remove new users, add and erase the whole filesystem, back up, and even restore files.
If you are using a system as a regular user, then switch to the root user to perform any system administrative task. For that, there is the “su” command, also known as “switch user” or “sudo”, which stands for “superuser do“.
11.2 Linux System Administrative Tasks:
Other system administrative tasks are mentioned below:
- Users: A root user can manage all the users connected to a system. Root users also manage the access right of each user.
- File Systems: Files are stored on your storage devices such as hard drives, CD-ROM, and USB Flash drives. Managing file systems includes mounting storage devices, creating partitions, backing up, formatting, and checking the issues of a file system.
- Devices: All the devices such as printers and DVD-ROMS are connected to the operating system through a special file called device files. A device file is a device driver placed in the “/etc/dev” directory, and to manage the device, you need to configure the “udev” rules, a device manager to add or remove devices in the “/dev” directory.
- Kernel: Kernel also manages the interaction of I/O devices and operating systems and protects the system from malfunctioned hardware. The kernel handles most of the tasks automatically. However, to add a new device, you may need to configure the kernel, which is also called compiling the kernel.
12 Programming on Linux:
Linux supports all the programming languages, most of the languages have native support, and some are ported. The primary tool to build Linux applications is called GNU Compiler Collection (GCC). GCC supports Ada, C, C++, Go, and Fortran programming languages. Languages that have cross-platform implementation are PHP, Ruby, Python, Java, Perl, and Rust.
The “Integrated Development Environments” IDEs Linux supports are mentioned in the following list:
- CodeLite
- Eclipse
- ActiveState Komodo
- KDevelop
- Lazarus
- MonoDevelop
- NetBeans
- Qt Creator
13 Uses of Linux:
Linux runs almost everything, such as your smartphone, car, laptop, supercomputer, or server. Linux operating system is the top choice for server setups.
The primary areas in which Linux is quite popular are mentioned below:
- Web Serving: A considerable percentage of websites on the internet use Apache server, an open-source server, and mostly run on Linux. According to an estimation, 60% of web servers use Linux.
- Networking: Linux is the preferred choice for networking in many small and large organizations.
- Databases: The secure and reliable nature of Linux makes it the perfect choice for databases.
- Desktops: Though the large market of desktop computers is dominated by the Windows
operating system, the paradigm shifts. Linux is becoming popular, and its market share is also growing. - Mobile Device: Android, the most popular and widely used smartphone operating system, is also Linux-based. The market share of Android is above 70%, which adds Linux to the list of the widely used operating system.
Apart from that, Linux has been a preferred operating system of the film industry. Animation studios like Pixar and Dreamwork Animations are using Linux.
14 Gaming on Linux
Gaming is a form of entertainment, and approximately there are 2.8 billion gamers in the world with over two thousand game-developing companies. The gaming market is dominated mainly by Windows-based personal computers and gaming consoles such as PlayStation and Xbox.
However, the paradigm is changing; Linux is also getting attention from game developers. As a result, many developers have published games that natively support Linux.
Steam, which is a popular online platform for PC game distribution, is natively available for Linux. Many games are native, and many are being ported on Linux. In 2018, Valve, the developers of Steam, released another platform for Linux called Proton. Proton provides a compatibility layer so that Windows games can easily be played on the Linux operating system. On ProtonDB, an entire list of supported games can be checked.
GPU is a requirement for many modern games, and Linux supports almost all GPUs from well-known manufacturers such as Nvidia and AMD. Thus, Linux with a powerful CPU and GPU can serve as a gaming PC with many games that natively support Linux.
14.1 GPU Drivers Support for Linux:
There are many graphics cards, but the market is dominated by two GPU manufacturers, Nvidia and AMD. Drivers for AMD GPUs are readily available because there are two different versions of AMD drivers. One is an open-source Radeon driver, and the other is a closed-source Catalyst driver. On the other hand, intel’s integrated graphics drivers are completely open-source. But when it comes to Nvidia, the drivers are proprietary and not available for Linux. The Linux open-source community of developers has made its own drivers that support Nvidia GPUs called nouveau. Nvidia is also supporting the nouveau development by releasing supporting documents.
Conclusion:
In 1991, an operating system kernel called Linux was released by a Finnish-American software engineer Linus Benedict Torvalds, originally designed for PCs with x86 processors. It was a personal initiative of Torvalds. The goal behind creating Linux was to provide a free operating system because, at that time, a proprietary operating system, Unix, was dominating the market.
The beginning of the development of an operating system is linked to a project called MULTICS by MIT, General Electronics, and AT&T Bell Labs in the mid-1960s. AT&T’s Bell Labs left the MULTICS project, and later Ken Thompson and Dennis Ritchie, who were a part of the MULTICS project, created a new operating system called Unix. Unix was a huge success and widely adopted by many businesses and education institutions. The University of California, Berkeley, in 1977, released an operating system called Berkeley Software Distribution (BSD) based on Unix code and later got sued by AT&T. Richards Stallman’s GNU project failed to get attention from the developer’s community. In 1987, Andrew S. Tanenbaum released his own Unix-like operating system called Minix for education purposes. The source code of Minix (Mini-Unix) was public, but any modification and redistribution were prohibited. Moreover, Unix was too expensive, which pushed a University of Helsinki computer science student, Torvalds, to kick off the development of Linux Kernel. Finally, on August 25, 1991, he successfully created an operating system kernel and released it on the internet.
Linux got unprecedented support from the open-source community. The community support helped in the growth of Linux because a mere kernel was not enough. An operating system is a combination of kernel, environment, and file structure. Therefore, the developers worked on its graphical environments, window system, and display managers. The open-source software helped Linux to receive tons of free apps. Moreover, many applications from other platforms were ported to Linux.
Linux kernel is public, which means anyone can use that kernel, modify it and make a brand new operating system. Currently, there are more than 600 Linux distributions. Linux is now a widely adopted operating system. Whether it is your desktop computer, laptop, smart home appliance, or smartphone, Linux is everywhere.
Linux can be accessed either through CLI (Command Line Interface) or through GUI (Graphical User Interface). The key component of the Linux operating system is Shell, a small program that helps a user interact with the kernel through commands. There are various types of shells; the commonly used shell is Bourne Again Shell, also known as Bash. Bash includes the features of other shells as well, such as Korn Shell and C Shell. Shell interface is used to command the kernel to perform tasks like managing the files, creating and deleting the directories, modifying internet settings, viewing files, etc. And if you want to perform a task by multiple commands, then shell scripting can assist there. A shell can be used through CLI and GUI.
For many users, CLI would be a bit complex to handle. In these cases, the desktop environments help. A desktop environment merges graphical elements such as icons, widgets, docks, etc., and the window system. The widely used desktop environments are Gnome and KDE.
Linux is well-reputed when it comes to security. Linux provides many tools to protect user’s data. The most commonly used tool is GNUPrivacy Guard, also known as GPG. In addition, to protect the entire Linux at the administrative level, SELinux is used, which is a kernel-level security module, and protects it from misconfiguration. Apart from that, various protocols are followed to safeguard internet communication, such as IPsec, IPtables, and firewalls.
Linux comes with multiple user administrative tools. It is a multi-user operating system, and it is widely used in large organizations to connect to a shared server. To manage users and protect valuable data, Linux provides various utilities. A superuser or root user can manage all the regular users. Apart from that, tasks related to file structure, attached devices, and the kernel can also be controlled through different utilities.
Linux is consistently growing. Even though the desktop computer market share is small, Linux is dominating the mobile operating system market. Linux has almost all types of applications, whether it is related to development, graphics designing, or post-production. You will get a free alternative to every app, thanks to the open-source developer’s community.
Various factors make Linux a preferable operating system. Most significantly, it is costs less, flexible to modification, and easily redistributed. Linux is not entirely secure but a lot less susceptible to attacks by unauthorized persons compared to other proprietary operating systems. Therefore, it is one of the prioritized operating systems when it comes to server setup and development. It is also a lightweight operating system and not as resource-intensive as other operating systems. Flexibility to customization, free software, and tons of security tools make Linux an operating system of the future.