Like most authentication protocols, LDAP comes with an array of commands that enable users to meet the various LDAP objectives. Notably, the ldapsearch command is arguably the most critical LDAP command.
This article discusses ldapsearch command, a utility that features a shell-accessible interface. It opens a connection to an LDAP server to help with entry management. Besides, it binds and performs various searches based on pre-determined and specified search parameters.
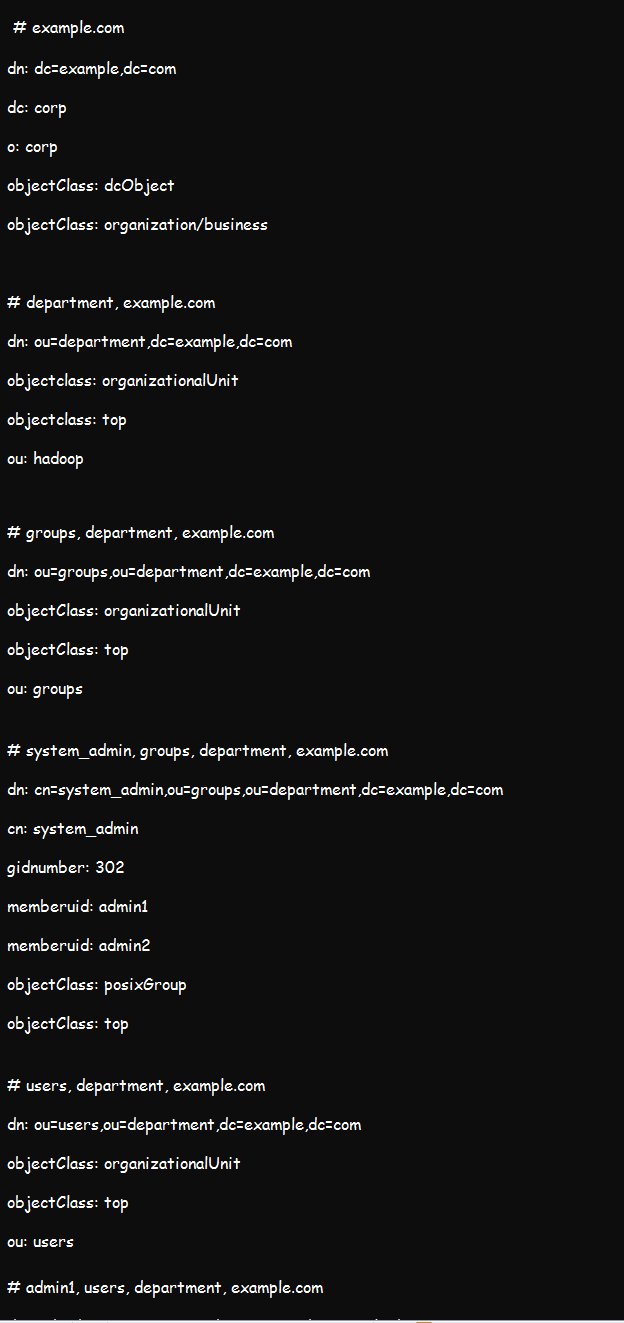
But before you begin trying out this utility, ensure that you have LDAP correctly installed and configured in your system. You can then use the ldapsearch command to perform the following functions:
a. Query LDAP Server for Information
Ideally, the ldapsearch tool is a specific search tool that can help you find information from your systems. These three illustrations should help you query and get entries from the LDAP server:
In this command, -x means simple authentication devoid of SASL, -h is the hostname, and –p is the port number or location.
In the above command, -D defines the band distinguish name, which is your authentication user from ldap.conf file. On the other hand –W will prompt for the bind password.
Finally, -w in the command specifies the need to use the password provided from the command line.
Interestingly, all the three commands will deliver the same result as shown below:
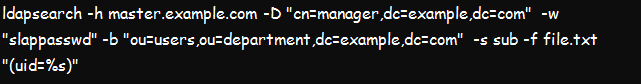
b. Using ldapsearch To Read Operation Using a File
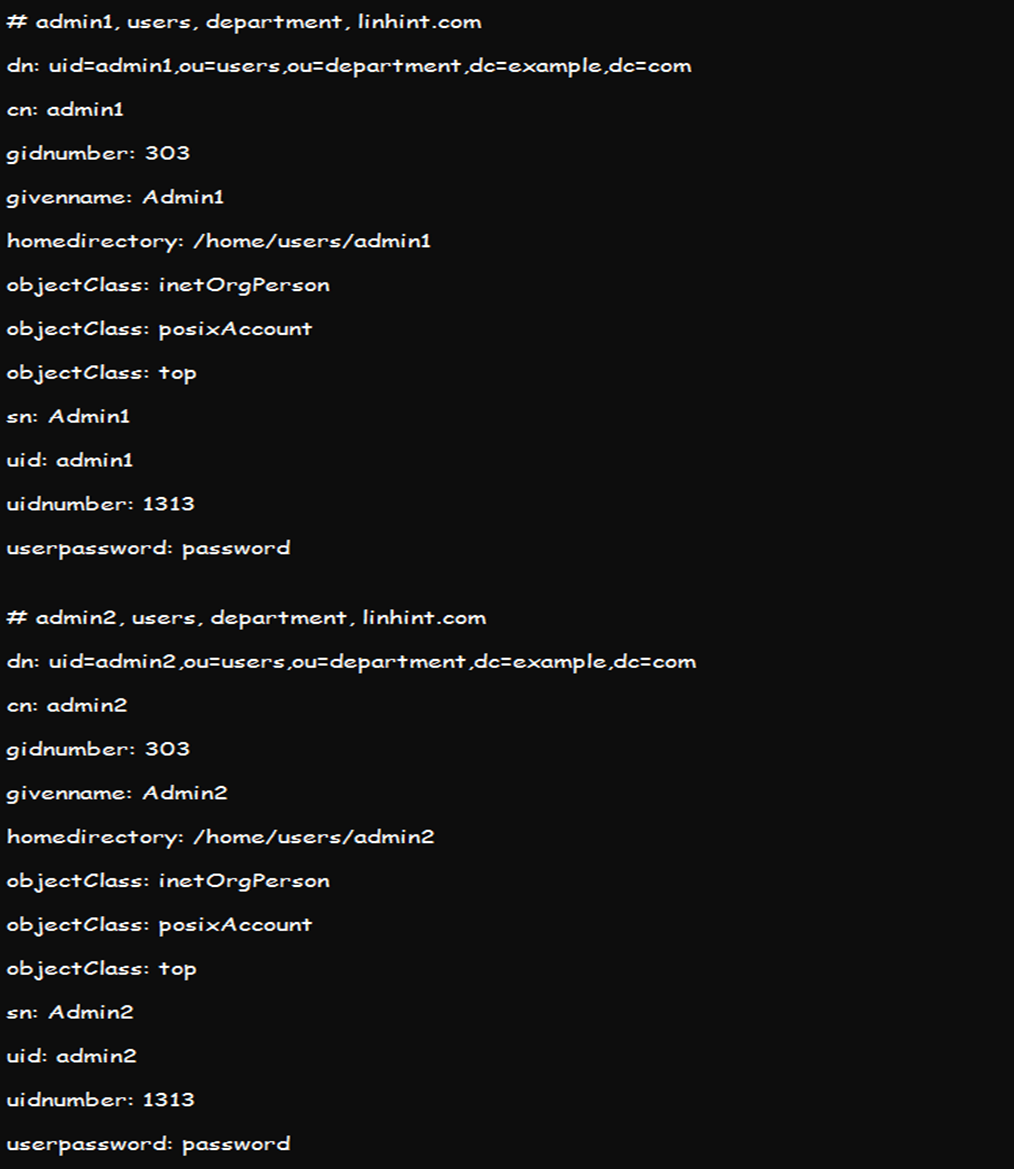
As an admin, the below command should help you read the operation using the vi file. Note that you should first create a file with both vi file and admin1 content and run the below command. The –f in the tool will read operations from the file. It is useable for multiple filters, and if the file also contains numerous filters, it will be presented with one filter in each line,
The query gives the same result as:
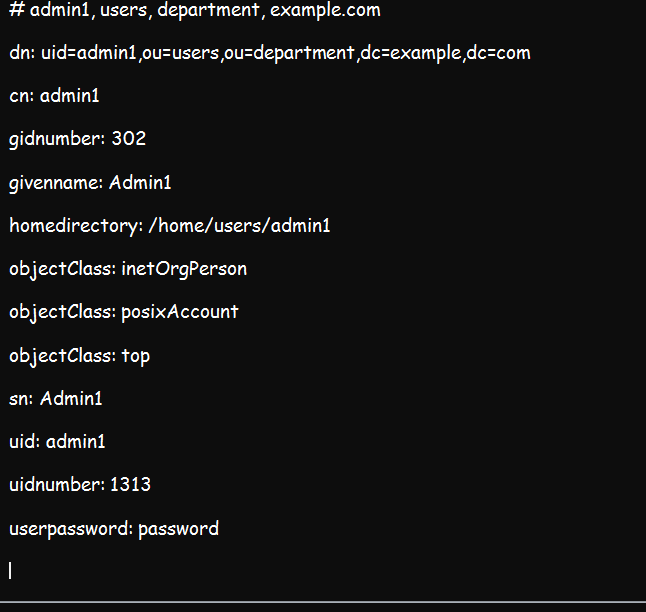
And the result should be similar to what is indicated below:
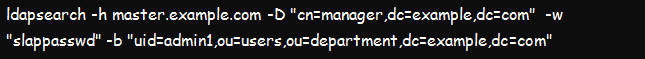
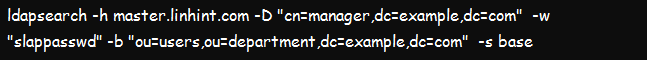
c. Using ldapsearch to Find Specific Base DN or Scope
Let us now find the base distinguish name/domain name and scope using the command below. In the tool, -b signifies the distinguish name bound for our search, while –s defines the scope of our investigation. The output of the command should provide us with the details of our base DN and the scope.
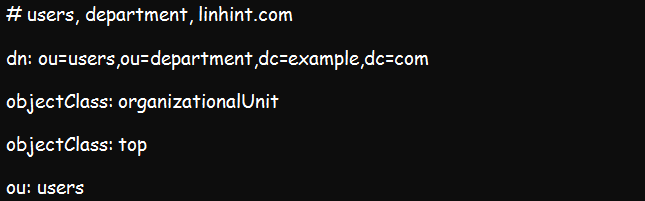
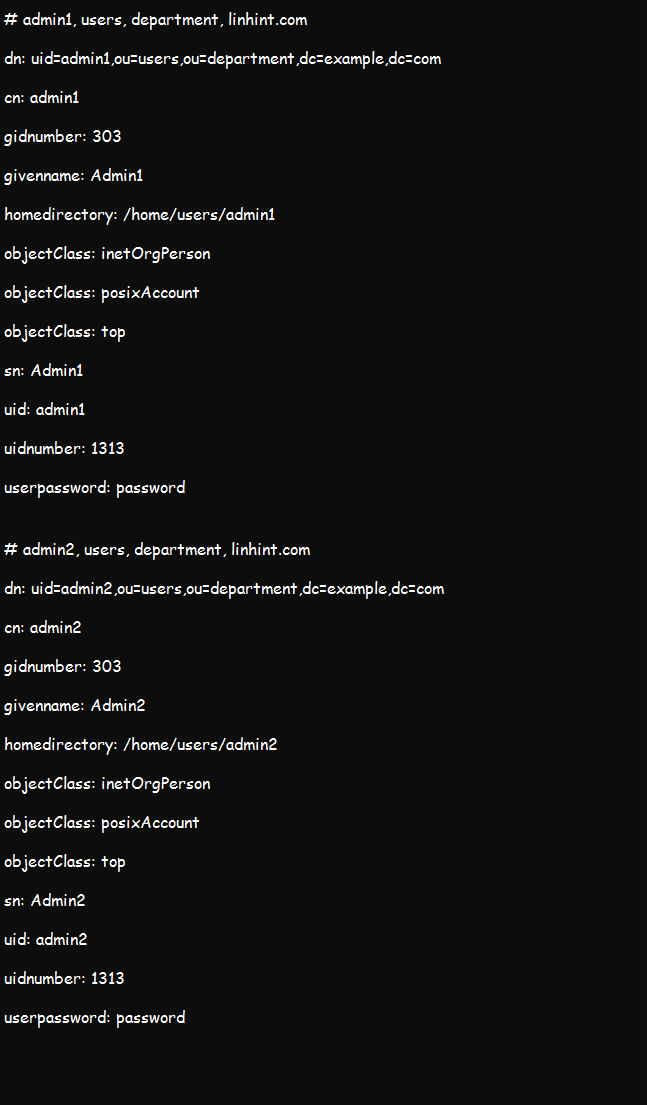
The result of this search should provide us with the base DN values of ou=users,ou=department,dc=example,dc=com, and the scope as shown in the figure below.
You can also use the same command to get the information on entries under each admin in case they share the same base DN.
d. Using ldapsearch to Query SSL/TLS
The –H flag often comes in handy in querying SSL/TLS. It is vital when using the LDAP uniform resource identifier (URI). You can also specify the port in your command or use the utility without the utility, as it will use the default command.
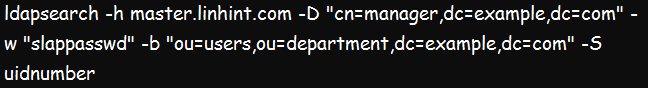
e. Sort the Result of a Query Using ldapsearch
We can also use the ldapsearch command to sort the result of a query by considering the main input and the output options. So, we will sort the results of our query using the ‘’uidnumber’’
In the below command, the –S flag in the utility sorts the result using the defined attribute. And since we only have two entries, in this case, they will assume uidnumber 6020 and 6021. The output for the above utility will be as indicated below.
f. Using ldapsearch to Do a Persistent Search
Persistent searches often leave the search intention open after you receive the command output. This action will allow your search result to remain cached and the system will transmit updates as they occur. You can leave the search open until you decide to close it using the CTRL-C Keny. Of course, the –C flag will run this utility as a persistent search.
The result will be as shown below.
Conclusion
This tutorial focused on searching an LDAP directory tree using ldapsearch on a Linux environment. This command is useable in various ways. I just highlighted how to search primary attributes and entries. The tutorial also discusses the process of building complex filters to match the operators.