The command is compatible with the Linux operating systems environment. It shows details in both the local credentials in the cache and key tab. It comes in handy after you modify the key tab files with ktab or change the credentials ticket using the Knit command.
You cannot use the Klist Linux command to modify the key tab or the credentials tickets. Instead, it comes in handy in verifying any changes made using the ktab or the Knit Linux commands. Thus, you can use Klist to view your ticket once you make a ticket request.
The basic synopsis of the Klist Linux command looks like the following:
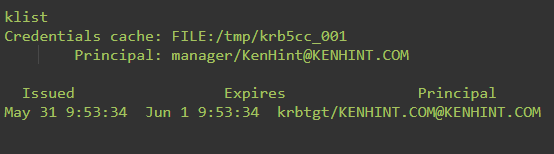
When you use the command to view your user credentials, your ticket resembles the following figure. Notably, the ticket always have a timeframe alongside your credentials.
Klist Linux Command Synopsis
Like every other command, understanding Klist Linux command starts with internalizing its synopsis. And as you will find out, this command has both short and long versions. The following syntax captures the synopsis from the command line or bash in shorter version:
The longer Klist command has the following denotation in the longer version;
Klist Options or Flags
The previous synopsis for this command represents flags. The flags are an array of options that print out the name of the credentials cache. It also identifies the name of the principal on whose name the ticket is printed. Finally, it specifies the date of issue and the expiry date of the ticket.
The options include:
- -e – displays all encryption types in the session key. It also shows each credential in the cache or keys in the key tab file.
- -c – lists tickets within the credentials cache. This is a default detailing if both –k and –c are not listed.
- -l – displays a summary of caches available in the collection
- -A – provides a display of all caches available in a collection
- -f – shows the flags available. Notably, common flags include F for forwardable tickets, f for forwarded tickets, P for proxiable tickets, p for proxies, D for postDatable tickets, and d for postdated tickets. Other flags include R for renewable tickets, I for Initial tickets, i for invalid tickets, H to show that the Hardware is authenticated, A for preAuthenticated tickets, T denoting Transit policy checked, O for Okay, and a for anonymous.
- -s – silences Klist and ensures that it runs without producing any output
- -a – displays addresses in the credentials
- -n – shows numeric addresses rather than reverse-solving addresses
- -k – provides a list of keys in the key tab file
- -v – shows the Kerberos version used and exit
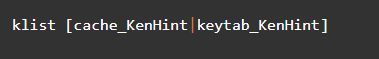
Of course, you will also have details about the [cache name| keytab_name] in a Klist command. But when there isn’t any specification of the cache name and the key tab name, if they are not indicated, the Klist command will configure the system by default. It will not use any specific identities to identify the default ticket. In our case, the cache name is KenHint, and its application is as follows:
Klist Command Examples
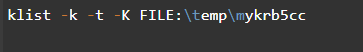
The following screenshot displays a Klist command example used for listing the entries existing in the key tab together with the entry time stamps and dynamic encryption system keys.
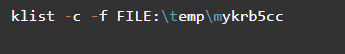
The second example lists the records in the credential cache that are declared using the associated flag and the list of addresses.
Conclusion
The primary way to confirm the changes executed on credentials is to view the credential cache or use the Klist command feature for the key tab or credentials cache.
The content above introduces you to one of the basic Kerberos Linux commands by providing a brief description, synopsis of the command, existing flags, and examples. It is also worth noting that the Klist Linux operates within the KRB5CCNAME environment variable.