In this tutorial, we will use different command-line methods on Linux to remove the iptables rules unrelated to the desired configuration.
Note: It is highly recommended not to lock the server by blocking SSH traffic (by default, port 22). Suppose you accidentally lose your access because of firewall settings. In that case, you can connect back to it by recovering access via the out-of-band console.
Before removing iptables rules, we will first list the rules. There are two ways to view iptables rules in which the rules can be viewed either in specifications or as a list in a table. They both display similar information in different ways.
Method 1: Listing by Specifications
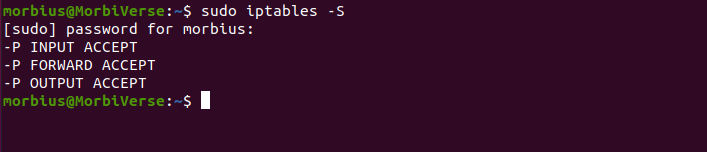
With the -S option, iptables lists all of its active rules.
You can see that output is like the commands used to create them without preceding the iptables command. Also, it looks similar to iptables rule configuration files if you use iptables save or iptables-persistent.
Listing a Specific Chain
Suppose you want the specific series in output. Following the -S option, the chain name can be put directly after it to specify the series name.
Here, for example, we will run the following command in the terminal to see all the rule specifications in the “output” chain.
Method 2: Listing as Tables
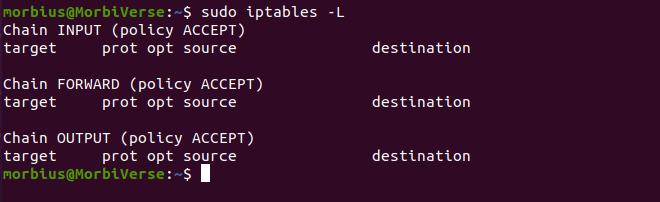
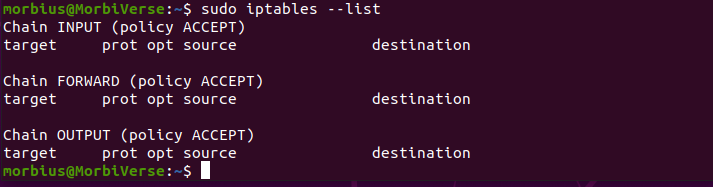
Now, we will discuss another alternative way to view active iptables, in which we will see them as a table of rules. Listing iptables rules in a table view proves to be very useful for comparing other rules with each other. Using the -L option of the iptables command, you can display all active iptables rules in a tabular format.
OR
This will output all existing rules by series. Suppose you want to see a limited specific series as output. In that case, you can specify the name of that series directly after the -L option.
Here, we go back to the example. We will run a command in the terminal by specifying the “output” chain to see all the rule specifications in the series.
Showing Packet Counts and Aggregate Size
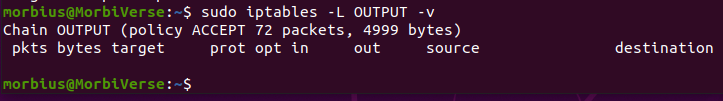
It is possible to show or list iptables rules as bytes showing the total size of packets and the number of packets that match each rule. This proves useful when you guess which rules match against the packet. It would be best to use the – L and – V options together in the terminal. The OUTPUT chain, for instance, will be reviewed again with the -v option.
Bytes and pkts, two additional columns now exist in the listing. The next step will involve resetting the counters for byte and packet data after we have listed the active firewall rules.
Resetting Packet Counts and Aggregate Size
You can set the byte and packet counter to zero or empty for your rules by using the -Z option in the command. On reboot, it is also reset again. This proves useful when you want to see whether your server is getting new traffic matching your rules or not. You can clear Counters from all rules and chains with the -Z option.
For example, we will run the below command in the terminal to clear the OUTPUT chain counter.
Specifying the rule number and chain name can clear the counter for a specific rule. For this, run the following command.
By now, you must know how to reset iptables byte counters and packets. Now, we will shed light on how these are removed. To overcome these, mainly two methods are used, which we will discuss further.
Deleting Rules by Specifications
Rule specification is one way to remove iptables rules. It would help if you used the -D option when running the IP table command to run this rule. You can select some of the specific rules for output using iptables -s and remove them by using the following command.
The -A option showing the position of the rule at the time of creation is excluded from here.
Deleting Rules by Chains and Numbers
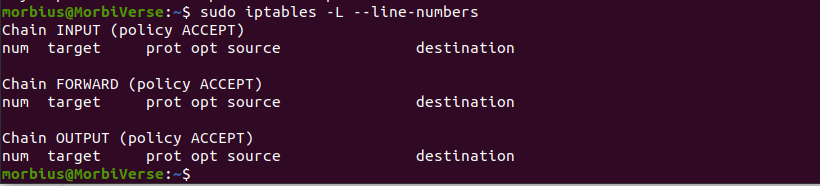
Its line number and chain can also remove the iptables rules. The –line-numbers option is added to set the row number of any rule by listing the rules in a table format.
By using this number, the system will add the row number to the num header for each rule row.
When you decide which rule you want to remove, it’s best to note the line number and chain of the rule. After this, run the -D command after the rule number and chain. Here, for example, we will remove the input rule that dropped invalid packets. We will run the following command according to whichever rule the INPUT chain is on.
Once the firewall rules are removed, we will see how to flush the chain of rules.
Flushing Chains
Iptables provide a way for you to remove all rules from a chain or flush a chain separately. Let us now see how to flush the iptables chain in different ways.
Note: Not flushing a chain with a default policy of dropping or denying can lock you out of your servers via SSH. You can connect to it by fixing your access through the console if you do this.
Flushing a Single Chain
You can use the chain and the option name with -F or the equivalent –flush to flush any specific chain you want to remove. To remove all input chain rules, run the following command.
Flushing All Chains
You can remove all firewall rules using the F or equivalent, –flush option.
sudo iptables --flush
Delete all chains, flush all rules, and accept all. Let’s see how to allow all network traffic by flushing all chains, tables, and firewall rules.
Note: Take special care that this effectively disables your firewall. The only reason to follow this section is if you only need to start the firewall configuration.
To not lock your server via SSH, you must first set the default policies to ACCEPT for each underlying chain.
sudo iptables -P FORWARD ACCEPT
sudo iptables -P OUTPUT ACCEPT
Flushes all mangle and net tables, (-X) deletes all non-default chains, and (-F) flushes all chains.
sudo iptables -t mangle -F
sudo iptables -F
sudo iptables -X
Now, your firewall will allow all network traffic to you. If you have listed all the rules, you see no rules left except the three default chains (OUTPUT, FORWARD, INPUT).
Reset All Iptables Configuration
You can reset all iptables configurations to default by using all the following commands in conjunction. It clears all rules from each table and resets your default chain policies, along with removing all empty chains from each table.
sudo iptables -P FORWARD ACCEPT
sudo iptables -P OUTPUT ACCEPT
sudo iptables -F
sudo iptables -X
sudo iptables -t nat -F
sudo iptables -t nat -X
sudo iptables -t mangle -F
sudo iptables -t mangle -X
Conclusion
After reading this tutorial, you must have known how iptables remove and list firewall rules. Under the simplest tasks, learning to remove any rule in iptables is considered a learning curve. We can use multiple options to delete just one rule and individually clear all rules for series or particular tables.
Note that any changes to iptables made via the iptables command are transient and will have to be saved for them to persist upon a server restart. The tutorial also covered the save rules section and general firewall rules.