Firejail is an SUID (Set User ID) program provided by linux which can be used to minimize the security issues of your system while running untrusted applications in a limited environment. Firejail uses the concept of sandbox to minimize security issues. In this blog we will see how to install and use Firejail in ubuntu.
Installing Firejail
Before using Firejail, we have to install it on our system using apt-get command. So run the following command in the Terminal to install Firejail
After installing Firejail, you can check whether it is installed on your system or not by running following command in the terminal
If this command gives the version of Firejail, then it has been installed.
Running Desktop Application
So far we have installed Firejail in our system, now we move onto how we can use it to run untrusted applications in a secured environment. We can run desktop applications by typing the following command in the terminal
In the following figure we can see how terminal window looks like when we run application with limited environment
Integrating Firejail with Desktop
So if we want to run an application from desktop manager icons in a limited environment what do we have to do?
We can run applications from the desktop manager icon by integrating Firejail into the desktop environment. Run the following command to integrate Firejail into the desktop environment
After running above command, logout and log back in
When you run the above command, it will configure some symlinks on your system as shown in the figure.
Now when you run any application from desktop icons or from terminal without using firejail command before it, it will automatically run in the limited environment.
Tracking Sandboxes
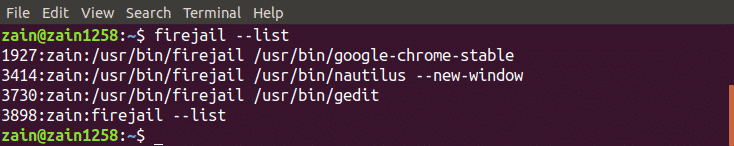
You can also check whether your application is running in a sandbox or not by listing all the sandboxed applications. Run the following command to list all the applications running in a limited environment
This command will list all the sandboxed applications
Alternatively, you can also run the top command along with firejail to display all the processes running under the firejail. Run the following command in the terminal window to display all the processes
Shutting Down Sandbox
In case a sandbox is not responding, you can shut it down from the terminal window by just typing a command. First of all run the firejail command with –list option to list all the sandboxes
After listing all the sandbox, note the PID of the sandbox to be shutdown and run the following command
When you run the above command, it will shutdown the sandbox specified by PID
Private Mode
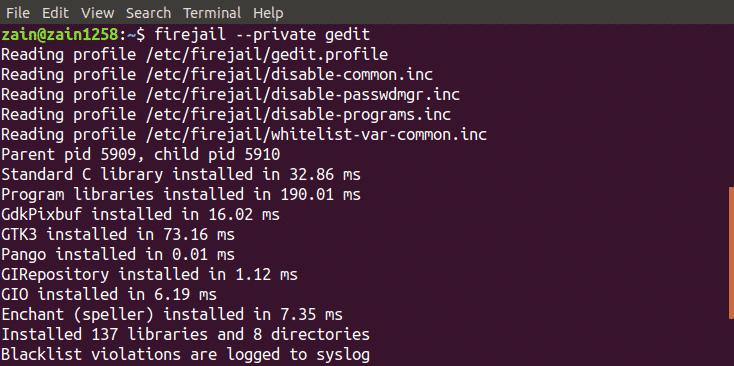
We can also use Firejail in private mode. Private mode is used to hide all the files in your home directory from sandboxed programs. We can enable private mode by typing following command in the terminal window
It will run the application in private mode. Firejail uses a temporary filesystem mounted on the home directory and any file which is created in this directory will be deleted when you close the sandbox. We can also use another directory for sandbox by running the following command
It will set the “my_dir” directory as the home directory of firejail.
Building Custom Profiles
We can also build our custom profiles in Firejail. In this section, we will create our own blacklisted profile in Firejail. Following is the process to create a blacklisted profile
Creating Blacklisted Profiles
Following are the steps to build a user defined profile. First of all move to the home directory and create “.config/firejail” directory in home directory. After creating directory move into this directory
Now copy the default security profile into this directory by running the following command
The name of the “app” file must be the same as that of application, with .profile extension. For example if you want to build a custom profile for firefox then the name of the file must be “firefox.profile”. Now open this file to modify by running the following command
Now if you want to black list Documents directory then add the following line in this file
To specify Downloads directory as read only, add the following line in this file
Now your profile is ready to use. Type the following command in the terminal to run the untrusted application in limited environment
Now your application can not use any kind of data from Documents directory and can not modify data in Downloads directory.
Firejail GUI Tool
Firejail also provides a user interface to use it more easily. All you have to do is to download the package and install it in your system. Following is the link to download the GUI tool for Firejail
https://sourceforge.net/projects/firejail/files/firetools/
Goto the link above and select the appropriate package that suits your system and install it.
Conclusion
Firejail is a very powerful tool to run untrusted applications securely on your system. In this blog all the steps to use this tool have been explained. First of all, installing Firejail has been discussed, then how to use it using a terminal in ubuntu has been explained. At the end, creating your own custom profiles in Firejail has been discussed in detail. After reading this blog, it will be much easier for you to use Firejail.