This article will cover a guide on installing and using OpenSnitch Firewall in Linux. OpenSnitch is a free and open source port of a proprietary firewall solution called LittleSnitch and implements most of its functionality. It can apply firewall rules system wide and can be used to block hosts as well as individual applications.
Main Features of OpenSnitch Firewall
Apart from blocking certain URLs, hosts and applications, you can also use OpenSnitch to monitor and set rules for systemd services, running processes, IP addresses, open ports, and so on. It also includes an option to apply rules for a specific time period only so that you can block connections temporarily. If you are using a multi-user Linux system, it also includes an option to apply rules for certain users only. So you can use OpenSnitch to block activity of browser extensions, web apps, bug and crash reports uploaded by apps, analytics sent by apps and virtually anything that connects to a host from your Linux system.
Installing OpenSnitch in Linux
OpenSnitch provides “deb” and “rpm” packages for Ubuntu, Debian, Fedora and other such Linux distributions that can use these package formats to install apps. These packages for daemon and graphical user interface are available for downloading on its GitHub releases page. Note that you will need to install packages for both daemon and GUI for OpenSnitch to work correctly on your Linux system. You can also compile it from its source code available here. Further installation instructions can be found on its wiki page.
Using OpenSnitch Firewall Rules
After installing OpenSnitch, launch it from the main application menu of your Linux distribution. It is possible that you may not see its main window as it can start minimized on the system tray. Depending on your Linux distribution, the system tray applet or indicator of OpenSnitch may look like this:
You can left click on the applet or right click on it and click on the “Statistics” option in the dropdown menu to open the main application window of OpenSnitch.
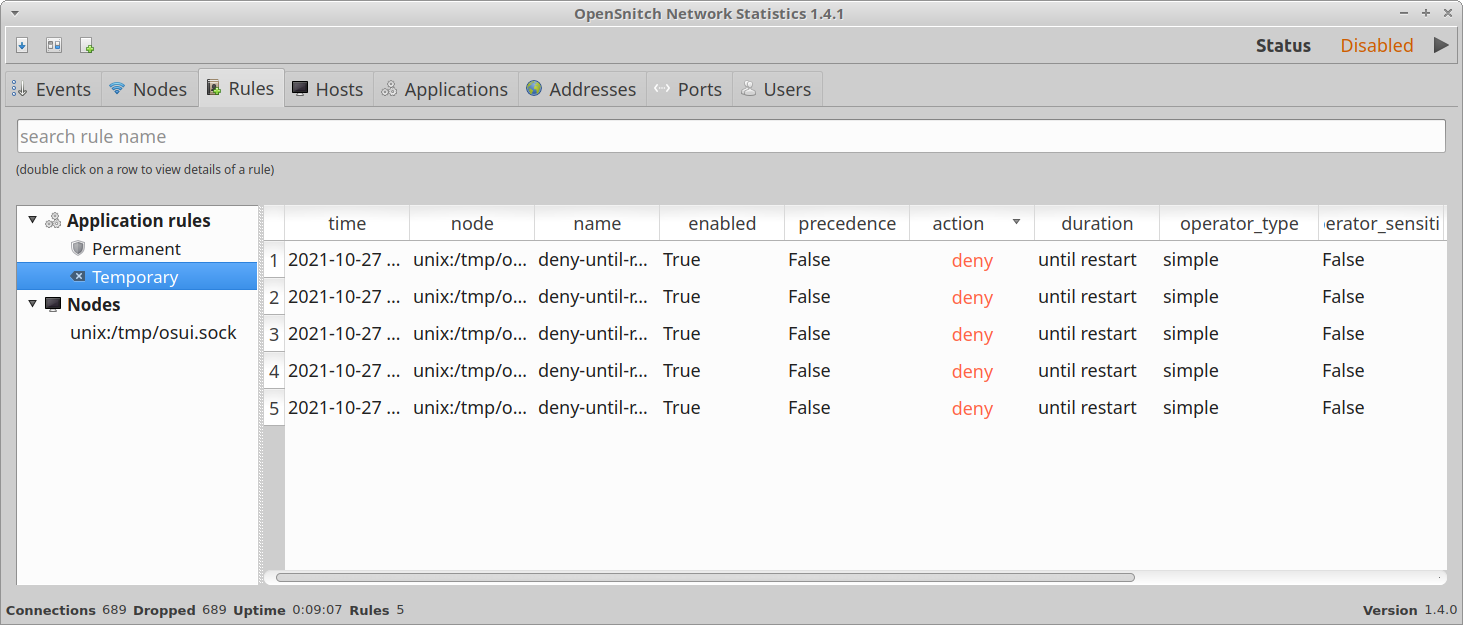
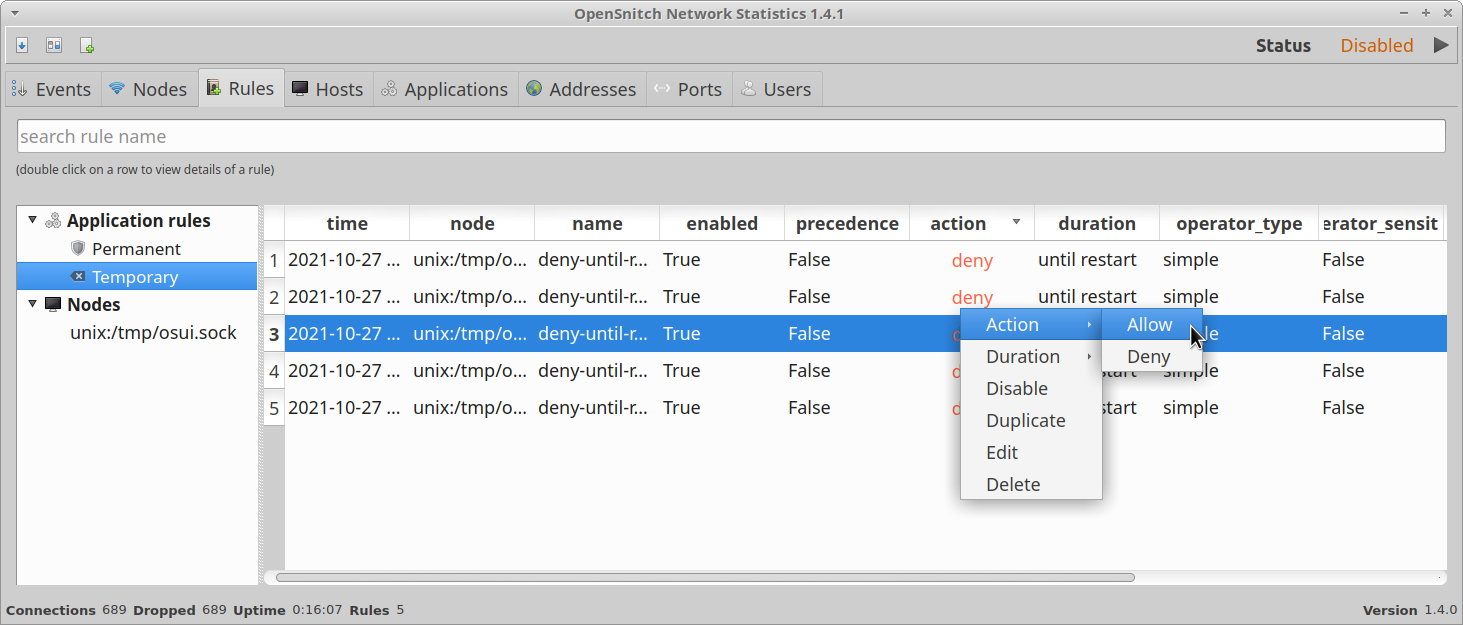
The various tabs in the top row allow you to access applications, hosts, and processes in neatly defined categories. From each of these tabs, you can manage editable entries under them by right clicking on them.
Note that you can sort and filter entries shown under various tabs to better manage them, especially when there are hundreds of such entries.
You will also be able to modify detailed rules about these entries under various tabs. OpenSnitch automatically identifies processes and hosts and defines rules for them with some user input. However, If an event doesn’t exist in its database or in GUI entries, it will show you a popup like this to manage its behavior on first detection:
Image SourceYou will have around 15 seconds to modify behavior of new events in the firewall, shown as a popup on first detection (as shown in the screenshot above). If you don’t take any action in this time frame, the process will be blocked and it will be denied access to internet connectivity. You can always manage it later from the main application window.
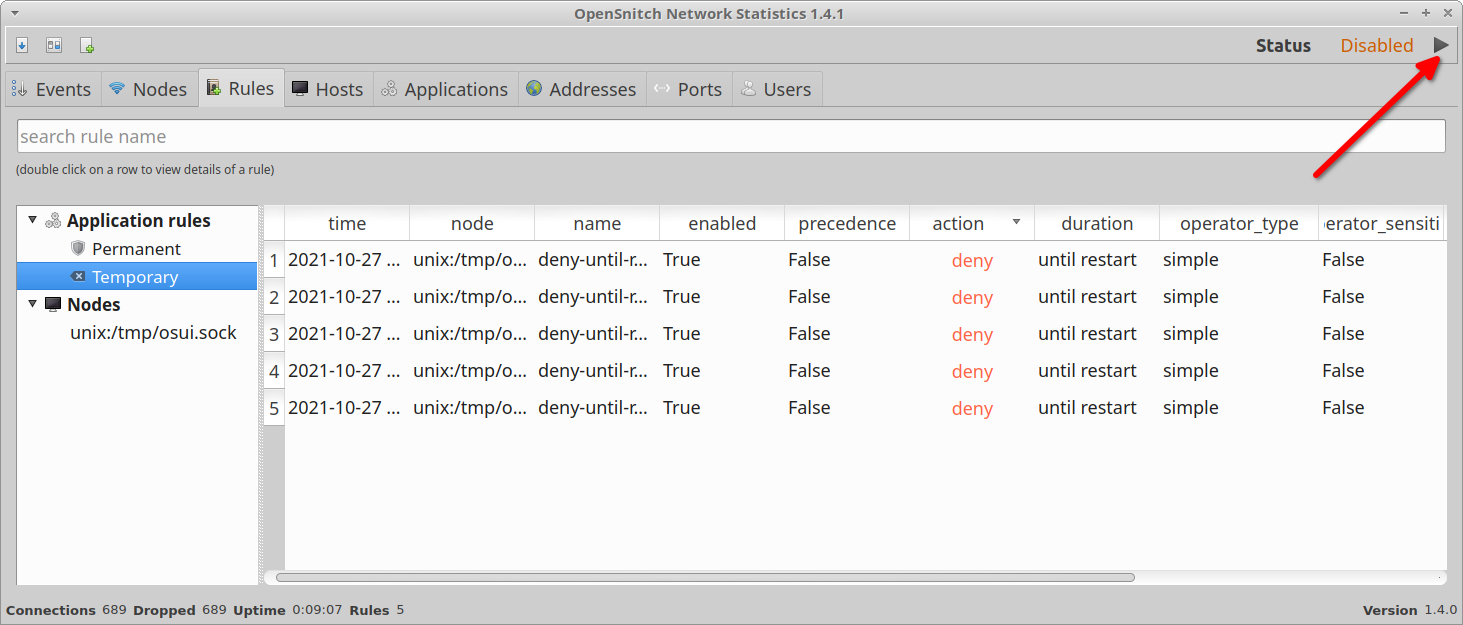
You can pause the OpenSnitch firewall anytime by clicking on a button located on the top right corner of the window.
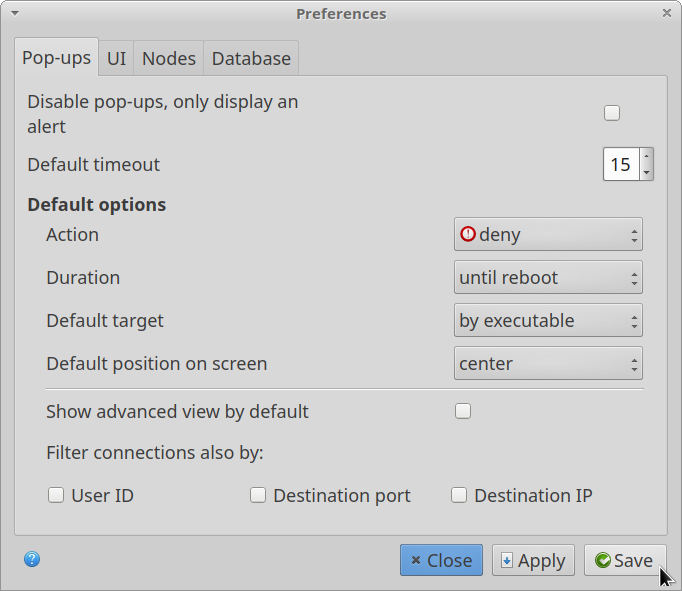
You can change the behavior of permission popup and other global settings by clicking on the second icon located on the top row (on the top left corner).
The main settings window of OpenSnitch has a lot of configuration options.
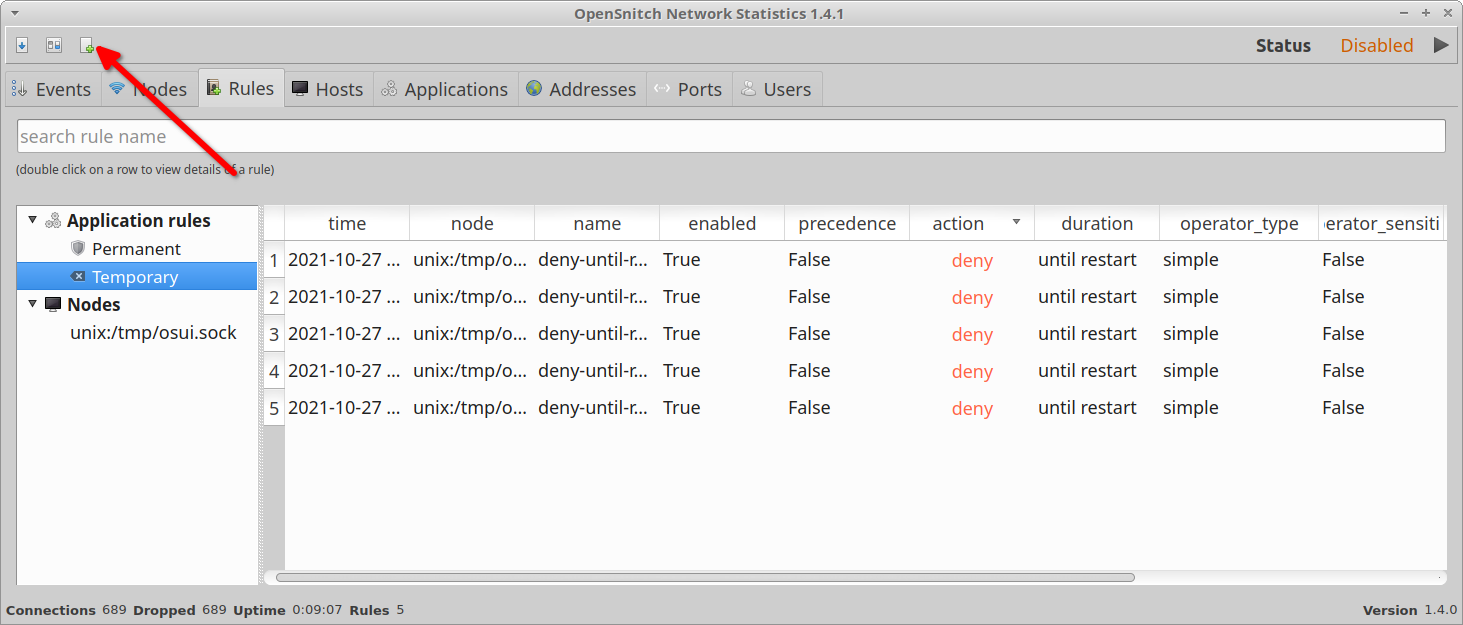
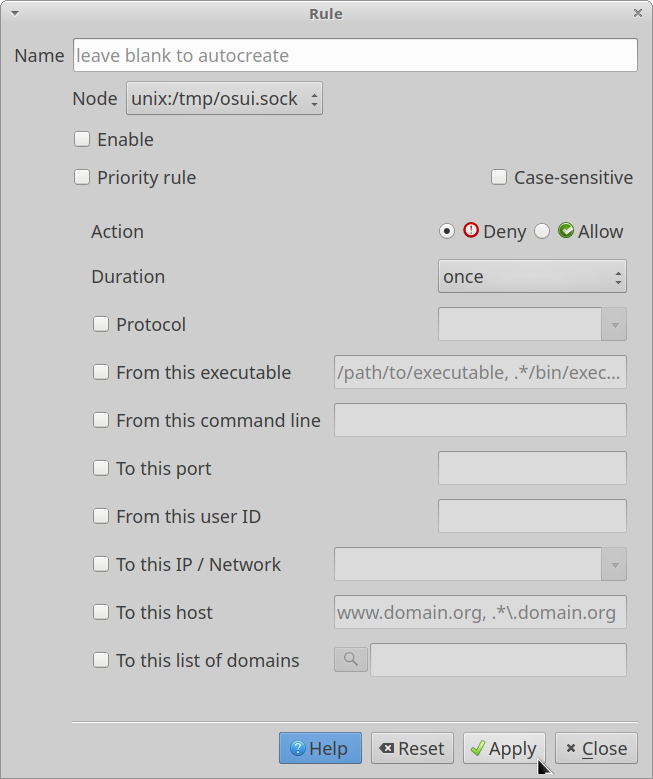
If you think that OpenSnitch has failed to detect a process or host, you can manually specify a detailed rule by clicking on the third icon located on the top row (on the top left corner).
From there, you will be able to define detailed rules for any event or process.
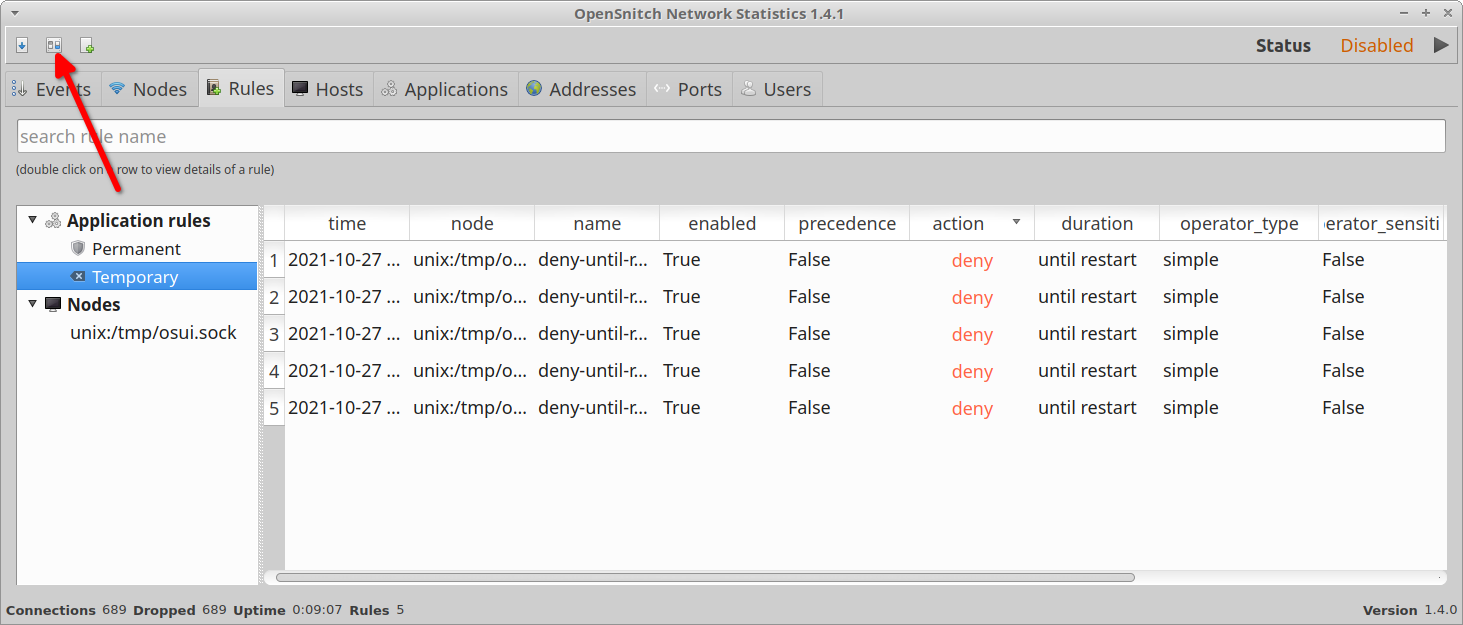
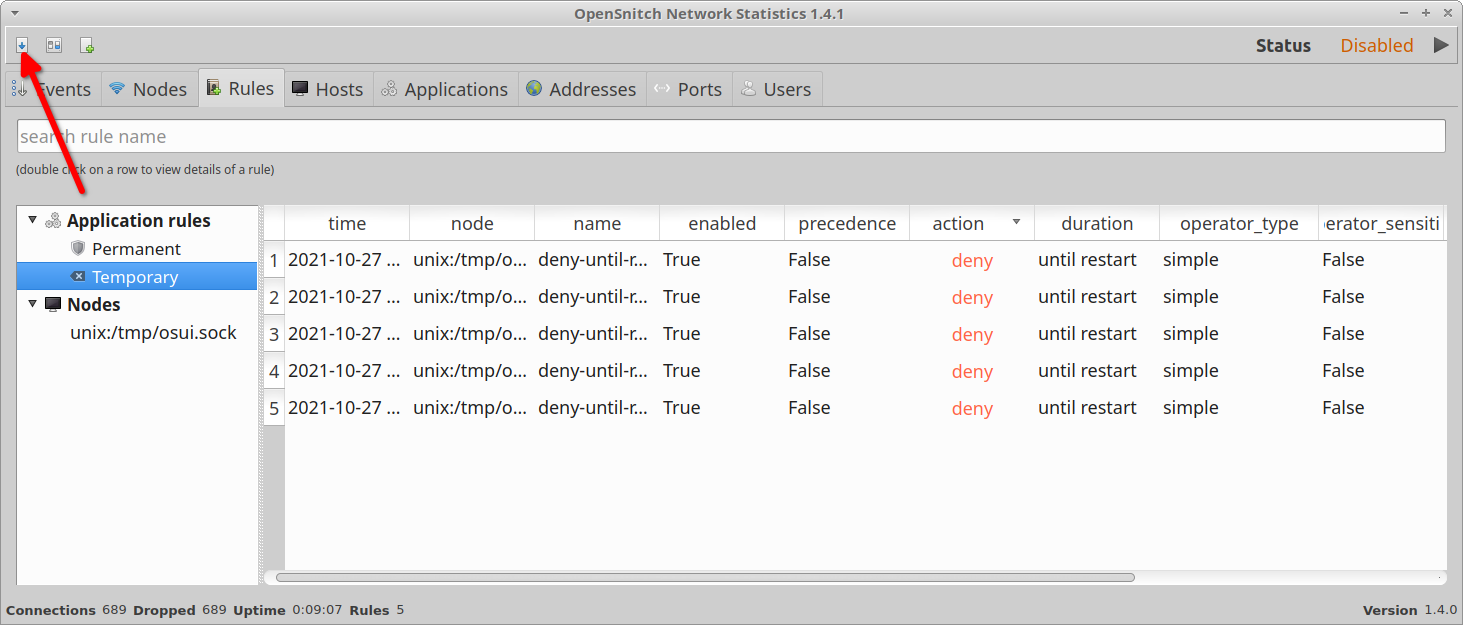
To export statistics and entries to an external CSV file, click on the first icon located on the top row (on the top left corner).
Data will be exported from the currently highlighted tab in the main OpenSnitch application window.
For further information about OpenSnitch and its usage, you can refer to official documentation available here.
Conclusion
OpenSnitch is a free and open source firewall application that can automatically identify hosts and processes running on your system and prepare appropriate firewall rules for them. This takes away much of the manual work from your hand. These automatically created rules are editable and you can modify them any time. A detailed rule creator is also available in OpenSnitch in case you want to manually define a firewall rule from scratch.