Aircrack-ng is a full set of software designed to test WiFi network security. It is not just a single tool but a collection of tools, each of which performs a particular purpose. Different areas of wifi security can be worked on, like monitoring the Access Point, testing, attacking the network, cracking the wifi network, and testing it. Aircrack’s key objective is to intercept the packets and decipher the hashes to break the passwords. It supports nearly all the new wireless interfaces. Aircrack-ng is an improved version of an outdated tool suite Aircrack, ng refers to the New Generation. Some of the awesome tools that work together in taking out a bigger task.
Airmon-ng:
Airmon-ng is included in the aircrack-ng kit that places the network interface card in the monitor mode. Network cards will usually only accept packets targeted for them as defined by the NIC’s MAC address, but with airmon-ng, all wireless packets, whether they are targeted for them or not, will be accepted too. You should be able to catch these packets without linking or authenticating with the access point. It is used to check the status of an Access Point by putting the network interface in monitor mode. Firstly one has to configure the wireless cards to turn on the monitor mode, then kill all the background processes if you think that any process is interfering with it. After terminating the processes, monitor mode can be enabled on the wireless interface by running the command below:
You can also disable the monitor mode by stopping the airmon-ng anytime by using the command below:
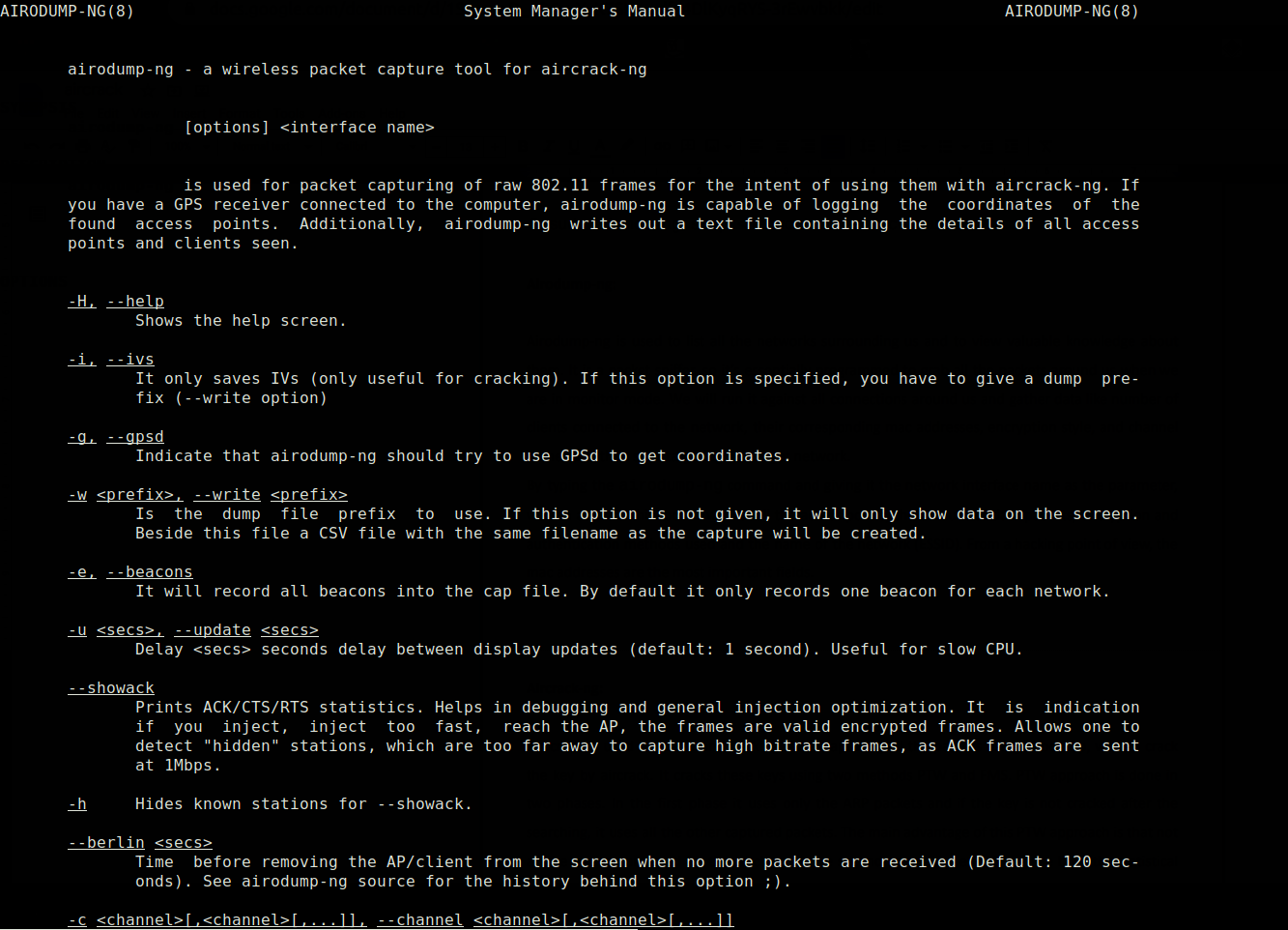
Airodump-ng:
Airodump-ng is used to list all the networks surrounding us and to view valuable information about them. The basic functionality of airodump-ng is to sniff packets, so it’s essentially programmed to grab all the packets around us while being put in the monitor mode. We will run it against all connections around us and gather data like the number of clients connected to the network, their corresponding mac addresses, encryption style, and channel names and then start targeting our target network.
By typing the airodump-ng command and giving it the network interface name as the parameter, we can activate this tool. It will list all the access points, the amount of data packets, encryption and authentication methods used, and the name of the network (ESSID). From a hacking point of view, the mac addresses are the most important fields.
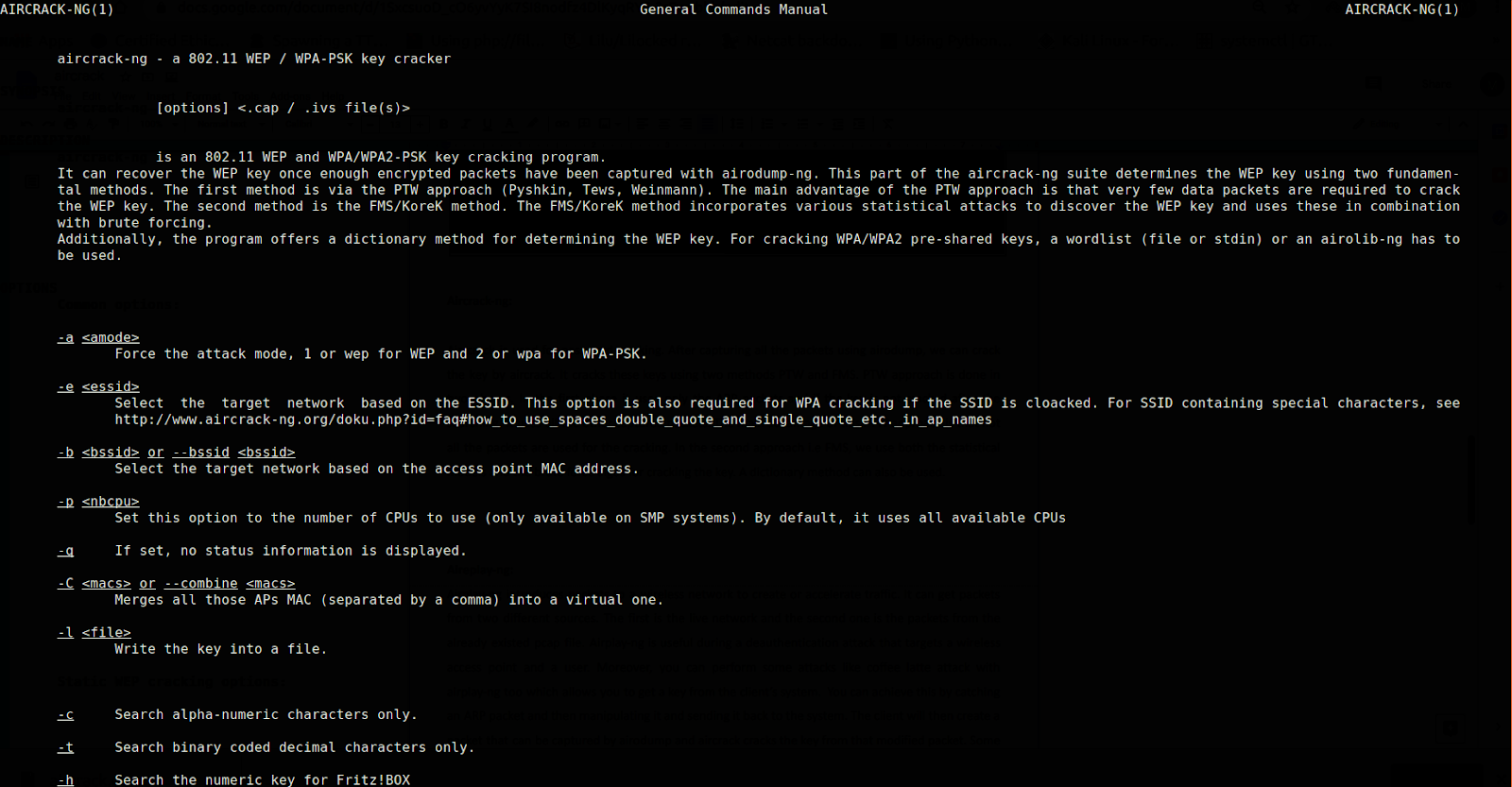
Aircrack-ng:
Aircrack is used for password cracking. After capturing all the packets using airodump, we can crack the key by aircrack. It cracks these keys using two methods PTW and FMS. PTW approach is done in two phases. At first, only the ARP packets are being used, and only then, if the key is not cracked after the searching, it uses all the other captured packets. A plus point of the PTW approach is that not all the packets are used for the cracking. In the second approach, i.e., FMS, we use both the statistical models and the brute force algos for cracking the key. A dictionary method can also be used.
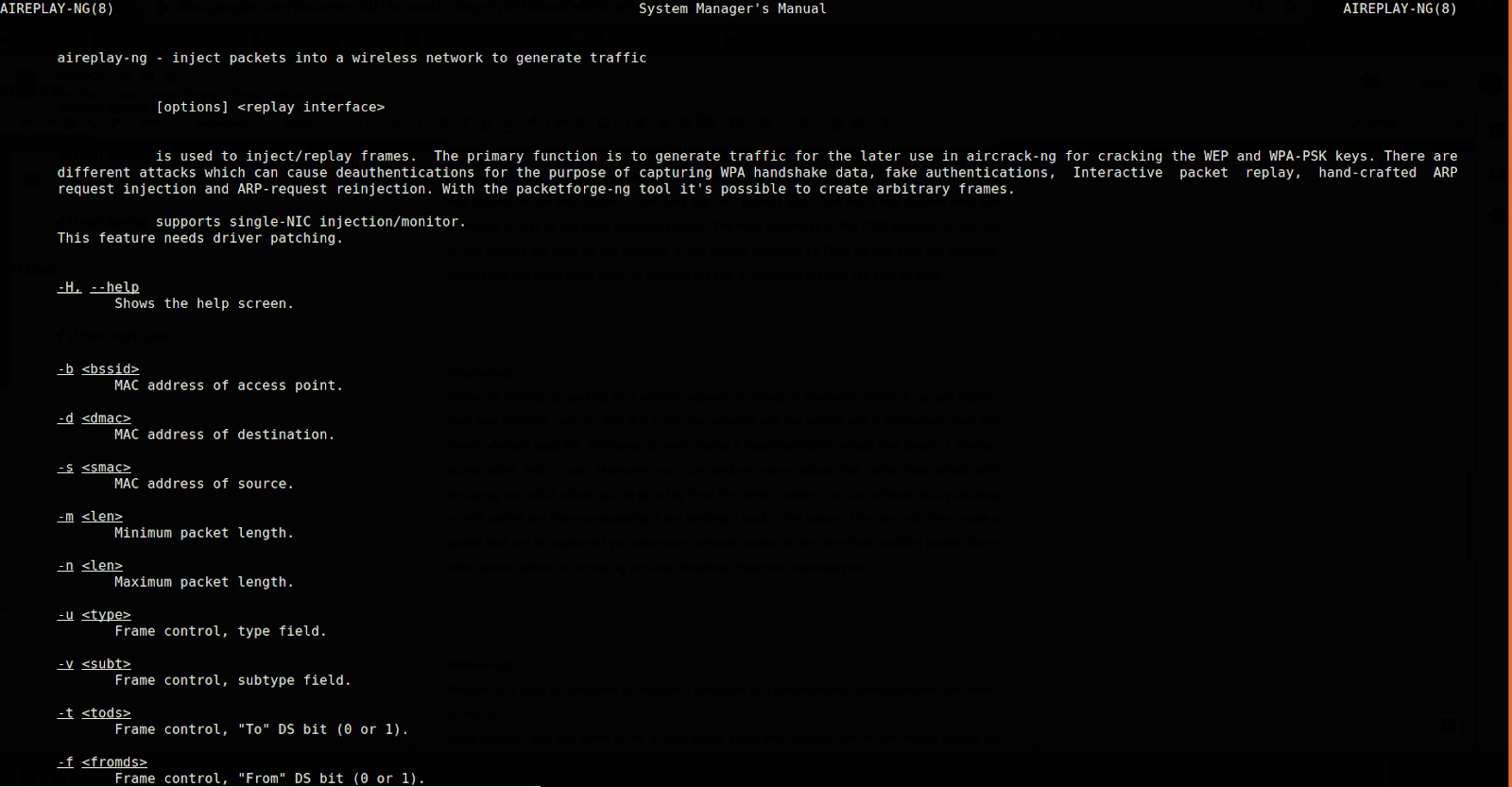
Aireplay-ng:
Airplay-ng introduces packets to a wireless network to create or accelerate traffic. Packets from two different sources can be captured by aireplay-ng. The first is the live network, and the second one is the packets from the already existed pcap file. Airplay-ng is useful during a deauthentication attack that targets a wireless access point and a user. Moreover, you can perform some attacks like coffee latte attack with airplay-ng, a tool that allows you to get a key from the client’s system. You can achieve this by catching an ARP packet and then manipulating it and sending it back to the system. The client will then create a packet that can be captured by airodump and aircrack cracks the key from that modified packet. Some other attack options of airplay-ng include chopchop, fragment arepreplay, etc.
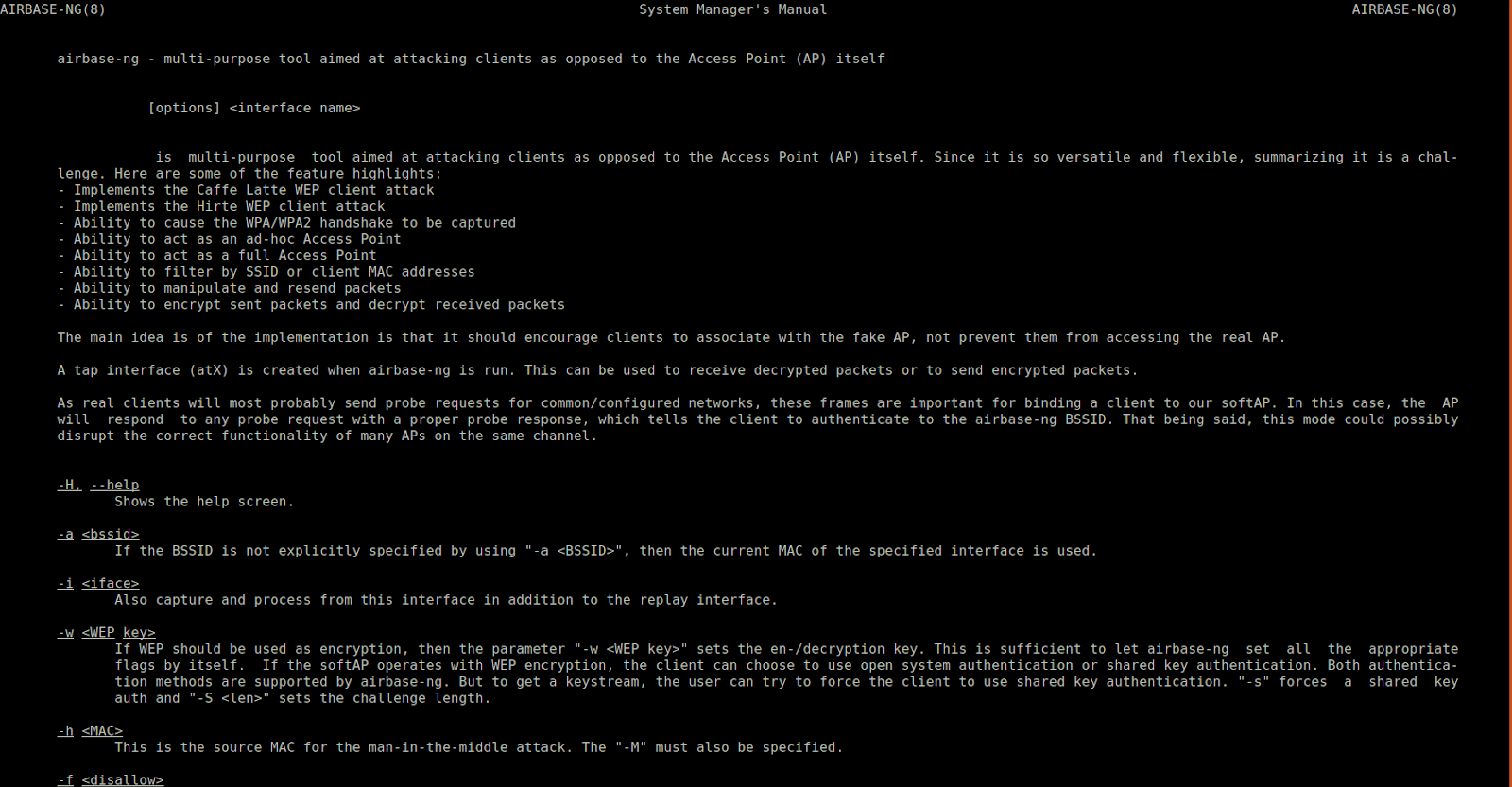
Airbase-ng:
Airbase-ng is used to transform an intruder’s computer to a compromised connection point for others to link to. Using Airbase-ng, you can claim to be a legal access point and conduct man-in-the-middle attacks on computers that are attached to your network. These kinds of attacks are called Evil Twin Attacks. It is impossible for basic users to discern between a legal access point and a fake access point. So, the evil twin threat is among the most threatening wireless threats we face today.
Airolib-ng:
Airolib speeds up the hacking process by storing and managing the password lists and the access point. The database management system used by this program is SQLite3, which is mostly available on all platforms. Password cracking includes the computation of the pairwise master key through which the private transient key (PTK) is extracted. Using the PTK, you can determine the frame message identification code (MIC) for a given packet and theoretically find the MIC to be similar to the packet, so if the PTK was right, the PMK was right as well.
To see the password lists and access networks stored in the database, type the following command:
Here testdatabase is the db which you want to access or create, and –stats is the operation you want to perform on it. You can do multiple operations on the database fields, like giving maximum priority to some SSID or something. To use airolib-ng with aircrack-ng, enter the following command:
Here we are using the already computed PMK’s stored in the testdatabase for speeding-up the password cracking process.
Cracking WPA/WPA2 using Aircrack-ng:
Let’s look at a small example of what aircrack-ng can do with the help of a few of its awesome tools. We will crack a WPA/WPA2 network’s pre-shared key using a dictionary method.
The first thing we need to do is to list out network interfaces that support monitor mode. This can be done using the following command:
PHY Interface Driver Chipset
Phy0 wlx0 rtl8xxxu Realtek Semiconductor Corp.
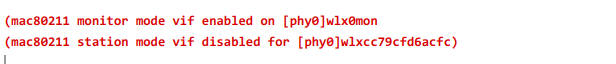
We can see an interface; now, we have to put the network interface we have found ( wlx0 ) in monitor mode using the following command:
It has enabled monitor mode on the interface called wlx0mon.
Now we should start listening to broadcasts by nearby routers through our network interface we have put in monitor mode.
CH 5 ][ Elapsed: 30 s ][ 2020-12-02 00:17
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
E4:6F:13:04:CE:31 -45 62 27 0 1 54e WPA2 CCMP PSK CrackIt
C4:E9:84:76:10:BE -63 77 0 0 6 54e. WPA2 CCMP PSK HAckme
C8:3A:35:A0:4E:01 -63 84 0 0 8 54e WPA2 CCMP PSK Net07
74:DA:88:FA:38:02 -68 28 2 0 11 54e WPA2 CCMP PSK TP-Link_3802
BSSID STATION PWR Rate Lost Frames Probe
E4:6F:13:04:CE:31 5C:3A:45:D7:EA:8B -3 0 - 1e 8 5
E4:6F:13:04:CE:31 D4:67:D3:C2:CD:D7 -33 1e- 6e 0 3
E4:6F:13:04:CE:31 5C:C3:07:56:61:EF -35 0 - 1 0 6
E4:6F:13:04:CE:31 BC:91:B5:F8:7E:D5 -39 0e- 1 1002 13
Our target network is Crackit in this case, which is currently running on channel 1.
Here in order to crack the password of the target network, we need to capture a 4-way handshake, which happens when a device tries to connect to a network. We can capture it by using the following command:
-c : Channel
–bssid: Bssid of the target network
-w : The name of the directory where the pcap file will be placed
Now we have to wait for a device to connect to the network, but there is a better way to capture a handshake. We can deauthenticate the devices to the AP using a deauthentication attack using the following command:
a: Bssid of the target network
-0: deauthentication attack
We have disconnected all the devices, and now we have to wait for a device to connect to the network.
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH E
E4:6F:13:04:CE:31 -47 1 228 807 36 1 54e WPA2 CCMP PSK P
BSSID STATION PWR Rate Lost Frames Probe
E4:6F:13:04:CE:31 BC:91:B5:F8:7E:D5 -35 0 - 1 0 1
E4:6F:13:04:CE:31 5C:3A:45:D7:EA:8B -29 0e- 1e 0 22
E4:6F:13:04:CE:31 88:28:B3:30:27:7E -31 0e- 1 0 32
E4:6F:13:04:CE:31 D4:67:D3:C2:CD:D7 -35 0e- 6e 263 708 CrackIt
E4:6F:13:04:CE:31 D4:6A:6A:99:ED:E3 -35 0e- 0e 0 86
E4:6F:13:04:CE:31 5C:C3:07:56:61:EF -37 0 - 1e 0 1
We got a hit, and by looking at the top right corner right next to the time, we can see a handshake has been captured. Now look in the folder specified ( /home in our case ) for a “.pcap” file.
In order to crack the WPA key, we can use the following command:
b :Bssid of the target network
-a2 :WPA2 mode
Rockyou.txt: The dictionary file used
Handshake.cap: The file which contains captured handshake
Aircrack-ng 1.2 beta3
[00:01:49] 10566 keys tested (1017.96 k/s)
KEY FOUND! [ yougotme ]
Master Key : 8D EC 0C EA D2 BC 6B H7 J8 K1 A0 89 6B 7B 6D
0C 06 08 ED BC 6B H7 J8 K1 A0 89 6B 7B B F7 6F 50 C
Transient Key : 4D C4 5R 6T 76 99 6G 7H 8D EC
H7 J8 K1 A0 89 6B 7B 6D AF 5B 8D 2D A0 89 6B
A5 BD K1 A0 89 6B 0C 08 0C 06 08 ED BC 6B H7 J8 K1 A0 89
8D EC 0C EA D2 BC 6B H7 J8 K1 A0 89 6B
MAC: CB 5A F8 CE 62 B2 1B F7 6F 50 C0 25 62 E9 5D 71
The key to our target network has been cracked successfully.
Conclusion:
Wireless networks are everywhere, used by each and every company, from workers using smartphones to industrial control devices. According to research, almost over 50 percent of the internet traffic will be over WiFi in 2021. Wireless networks have many advantages, communication outside doors, quick internet access in places where it is almost impossible to lay wires, can expand the network without installing cables for any other user, and can easily connect your mobile devices to your home offices while you aren’t there.
Despite these advantages, there is a big question mark about your privacy and security. As these networks; within the transmitting range of routers are open to everyone, they can easily be attacked, and your data can easily be compromised. For example, if you are connected to some public wifi, anyone connected to that network can easily check your network traffic using some intelligence and with the help of awesome tools available and even dump it.