This tutorial explains how to use hashcat to break over 250 hash modes through different attack methods.
After reading this tutorial, you will know the most important Hashcat features and how to implement them to break hashes.
Functional introduction to Hashcat
Hashcat is a very potent tool. It is worth taking it into account and learning its features. Before starting with examples, let’s see some of the hashcat functionalities, including attack types, breakable hashes, and charset settings.
Hashcat is a very flexible tool allowing the user to optimize and customize attacks for over 250 hash modes classified by categories. Some of these categories are shown in the following table.
| CATEGORY | HASH MODE SUPPORT |
|---|---|
| Raw Hash | MD4, MD5, SHA1, SHA2, SHA3, etc. |
| Network Protocols | WPA, Skype, MySQL CRAM (SHA1), DNSSEC (NSEC3), etc. |
| Forums, CMS, Frameworks | phpBB3 (MD5), vBulletin, WordPress (MD5), Joomla(MD5), etc. |
| Database Server | PostgreSQL, Oracle, MySQL, etc. |
| HTTP, SMTP, LDAP Server | Apache $apr1$ MD5, md5apr1, MD5 (APR), nsldaps, SSHA-1(Base64), Netscape LDAP SSHA, etc. |
| Operating Systems | Samsung Android/Windows Phone 8+ Password/PIN, GRUB 2, Cisco, macOS, etc. |
| Archives | 7-Zip, Winzip, RAR, etc. |
| Full Disk Encryption | LUKS, Android FDE, Veracrypt, eCryptfs, etc. |
| Documents | PDF, Microsoft Office, Apple Secure Notes. |
| Password Managers | LastPass, Bitcoin/Litecoin wallet.dat, Blockchain, My Wallet, KeePass, etc. |
Note: You can see the full categories list at https://gist.github.com/dwallraff/6a50b5d2649afeb1803757560c176401 or by runningthe command hashcat –help
Hashcat Charsets:
Hashcat allows you to control charsets for brute force attacks. When brute-forcing, you can apply the following built-in charsets on each password position.
| Flag option | Charset |
|---|---|
| ?l | abcdefghijklmnopqrstuvwxyz |
| ?u | ABCDEFGHIJKLMNOPQRSTUVWXYZ |
| ?d | 0123456789 |
| ?h | 0123456789abcdef |
| ?H | 0123456789ABCDEF |
| ?s | !”#$%&'()*+,-./:;<=>?@[\]^_`{|}~ |
| ?a | ?l?u?d?s |
| ?b | 0x00 – 0xff |
For example, you can define the first password character as an upper case character by specifying ?u followed by 5 lowercase characters (?l?l?l?l?l) and four last numbers by specifying ?d?d?d?d. This will seem like this:
You also can specify four custom charsets combining different possibilities. You specify each custom charset by adding 1, 2, 3, and 4. For example, to specify a charset that includes 5 lower case letters and numbers, the command seems as shown below, because ?l specifies lowercase characters and ?d specifies numbers.
Hashcat customization and optimization options also include hardware device selection to various attack modes, including the explained below.
Hashcat attack modes:
- Brute-Force attack (3): This type of attack consists of massive character combination tries. This attack technique was discontinued on Hashcat and was replaced by Mask attacks.
- Combination attack (1): This mode allows to append each word contained in a wordlist to the end of each word container in a second wordlist.
- Dictionary attack (0): This mode, also called “Straight mode,” tries all lines contained in a file as a password. This is a simple wordlist attack.
- Hybrid attack: The Hybrid attack mode allows combining a dictionary attack with a brute force attack. By using this mode, you can append or prepend wordlist elements to a bruteforce attack.
- Mask attack (6 or 7): The Mask attack is an improvement of the brute force attack, aiming to design “intelligent” brute force attacks in which the user has control over the password candidate generation process. For example, the Mask attack allows users to define patterns like a capital letter for the first position of the password candidat only, or append dates at the end of the password candidate, or before, etc. The 6 mode enables Hybrid Wordlist + Mask, while the 7 mode enables Hybrid Mask + Wordlist.
This attack results in more accurate attempts and the omission or reduction of improbable password candidates.
- Rule-based attack: This is described by Hashcat developers as the hardest type of attack because it consists of programming the password candidate generation with functions to cut, modify, extend password candidates.
- Toggle-Case attack: This attack type works if the Rule-based attack is enabled. It allows you to try all upper and lower case possibilities for password candidates.
Getting started with Hashcat:
To begin on Debian-based Linux systems, run the command below to install Hashcat.
For other Linux distributions, you can download and extract the compressed 7zip file from https://hashcat.net/hashcat/.
For the first example, I will use a file called a hashlist containing two hashes and a wordlist called a wordlist.
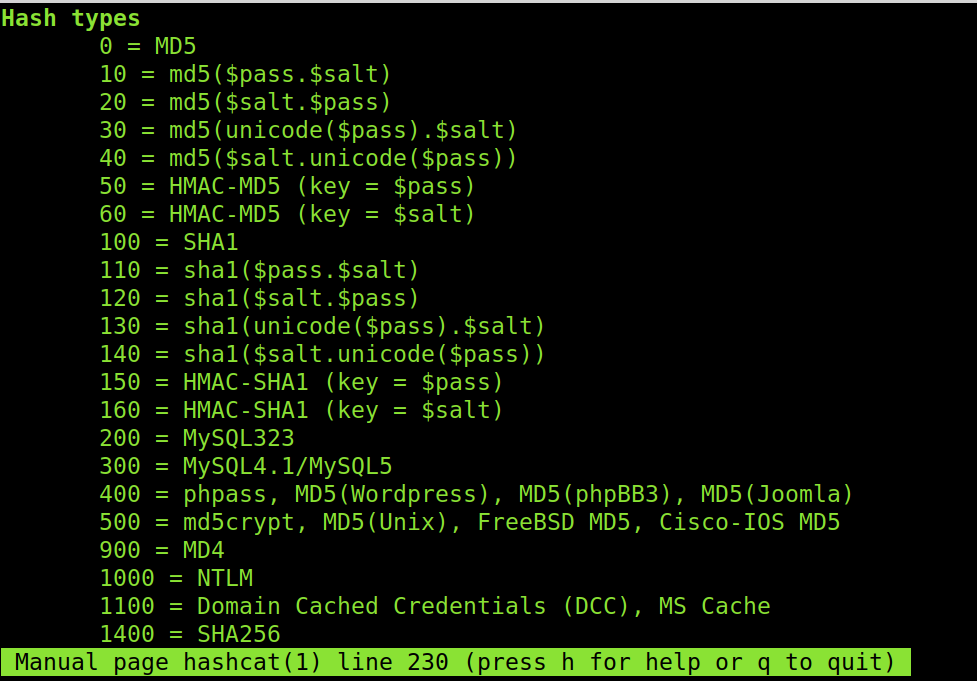
The -m flag is used to define the hash type. The hash I want to break is MD5; it is a type 0. You can check how to define each hash type by reading the man page as shown below and scrolling down to the Hash types section.
You can also learn all attack types, and how they are defined on the man page, this was previously explained in the Hashcat attack modes section in this tutorial.
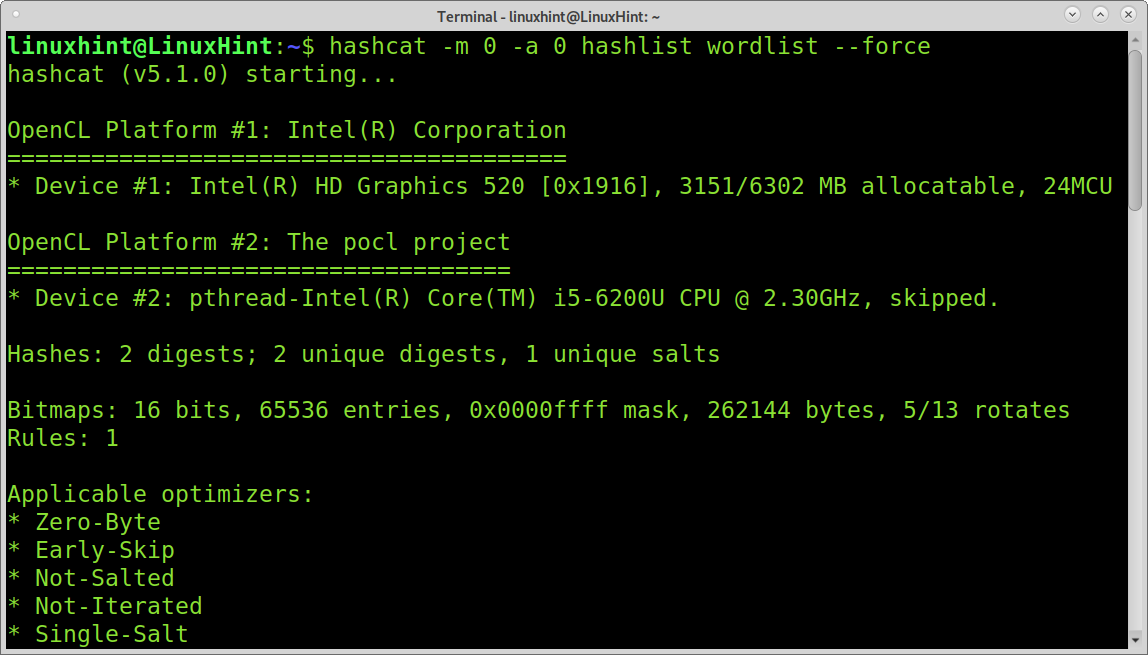
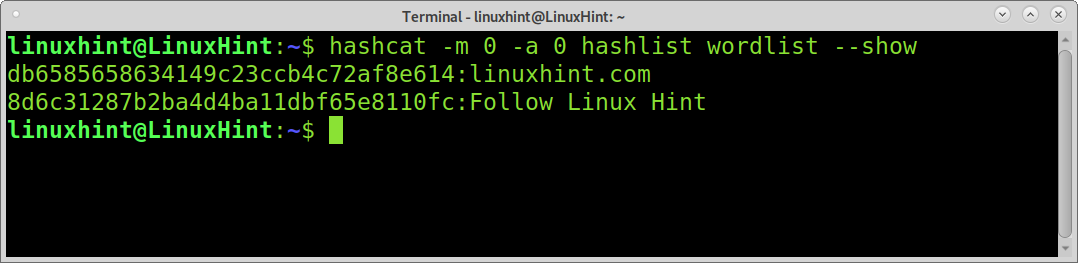
The first attack example targets an MD5 hash (-m 0) using a dictionary attack (-a 0) to break hashes contained in the hashlist, followed by the wordlist.
Hashcat will start running; in my case, I’m using a dummy wordlist containing the correct wordlists, thus as you can see below, Hashcat warns my wordlist is small.
Note: the hashes used in this tutorial are:
8d6c31287b2ba4d4ba11dbf65e8110fc
As you can see, Hashcat managed to decrypt hashes containing “linuxhint.com” and “Follow Linux Hint“.
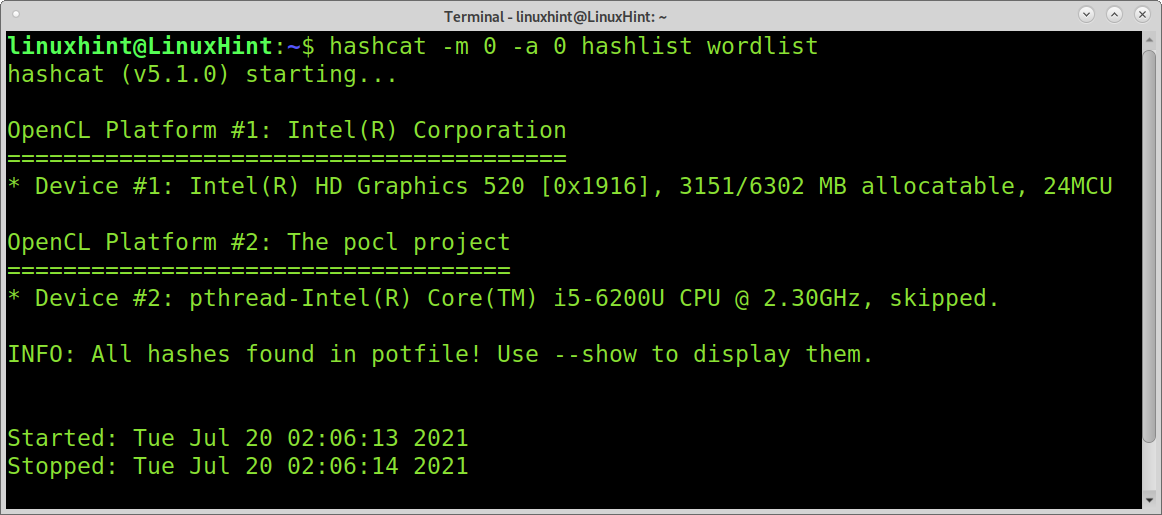
Let’s see what happens if we run the same attack again.
As you can see before starting the attack, Hashcat informs us the result is already present in the Potfile because we already decrypted it previously.
Potfile is where Hashcat stores broken hash results; by default, the hashcat.potfile is located in the hidden directory .hashcat within the user’s home (~/.hashcat/hashcat.potfile).
In this case, you need to add the –show option, as shown in the example below.
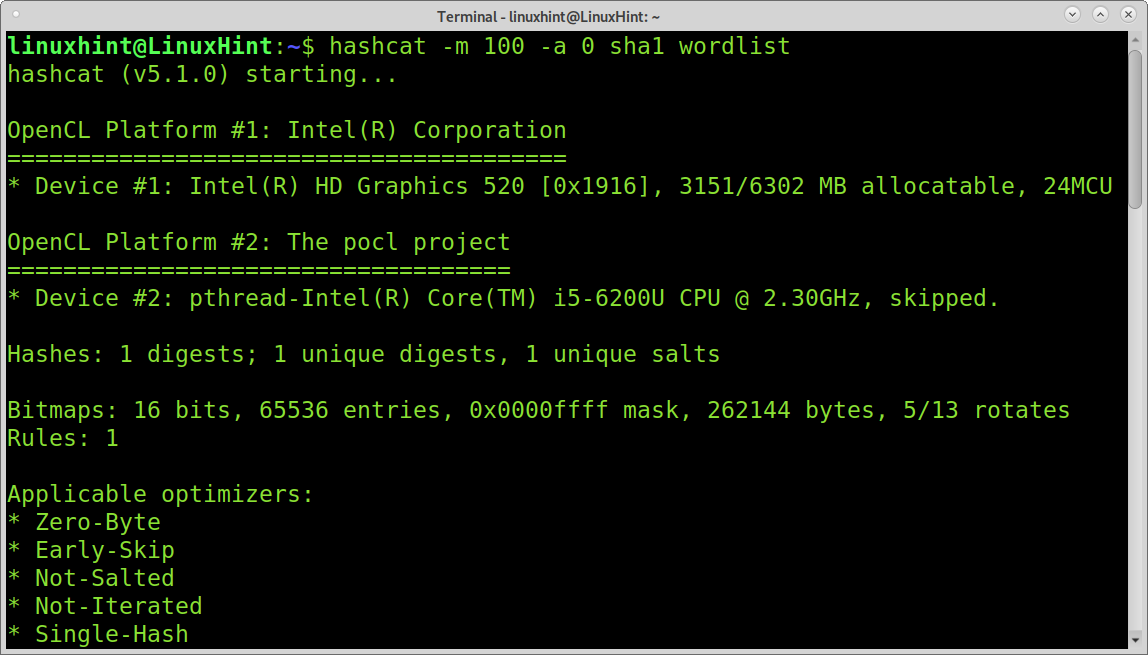
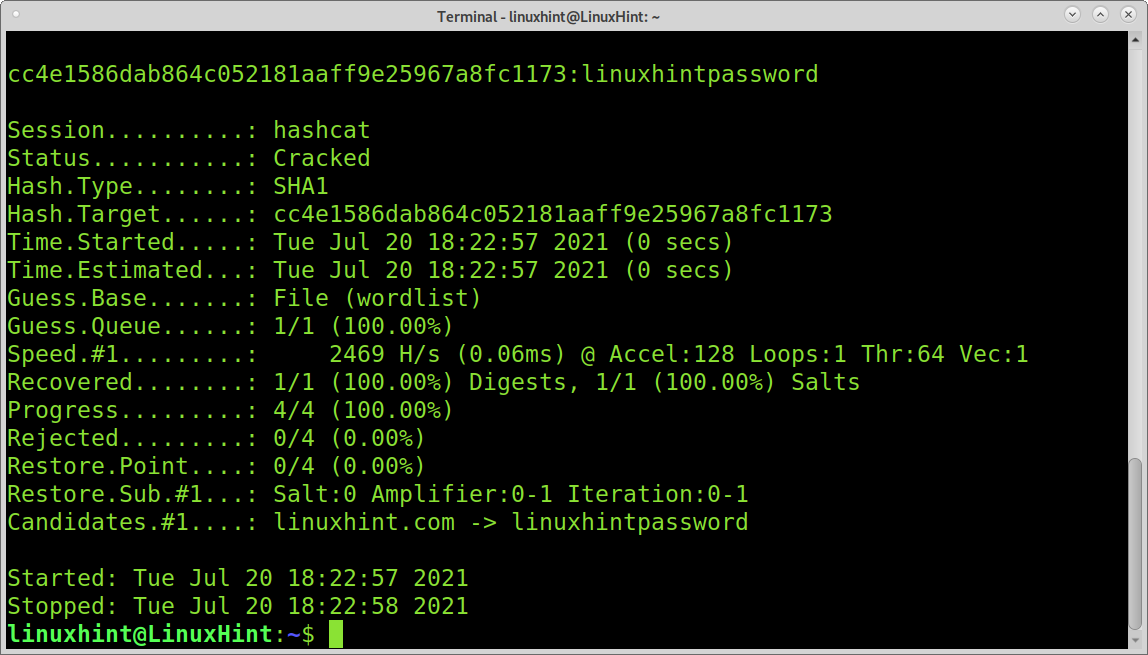
The following example shows how to decrypt a sha1 hash. The file called sha1 contains a SHA1 hash. As you can see, in addition to a different name, the only difference is the hash mode, changed to 100 (SHA1). The attack is a dictionary attack as the previous.
As you can see, the decrypt SHA1 hash is linuxhintpassword.
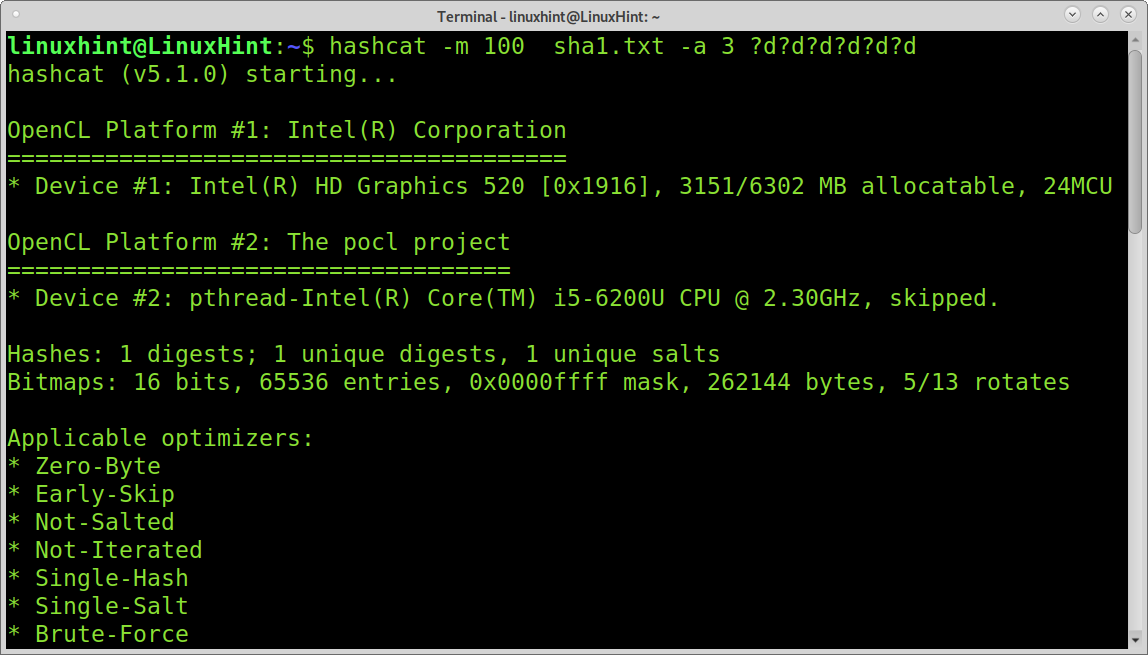
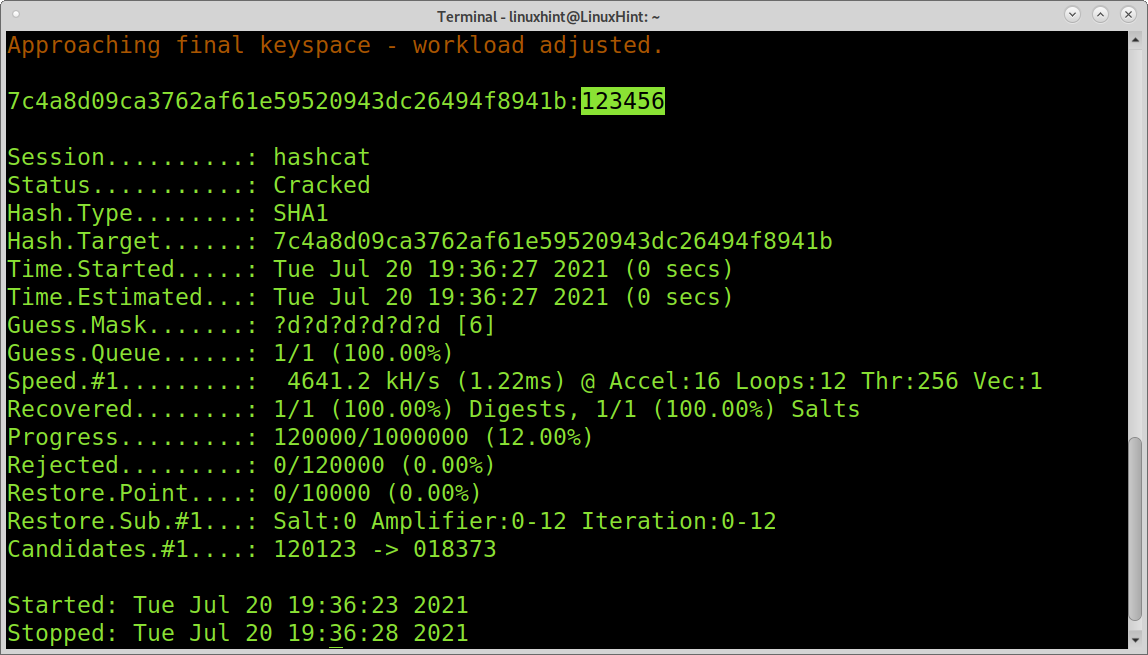
This last example shows a brute force attack using a hashcat charset to decrypt a numerical password. In this case, I know it is a numerical password 6 characters long. Using the -3 I’m instructing hashcat to execute a brute force attack, and by implementing 6 times the ?d charset, I specify to try all numbers 6 times, one for each character.
As you can see, the password 123456 was correctly decrypted.
Conclusion:
Hashcat is a simple but powerful tool to decrypt hundred hash types in a few steps. It is a multiplatform tool that can help us recover protected zip files, documents, wpa .pcap files, and over 250 different encryption modes. Its features, like mask attacks, make hashcat a smart tool to carry out intelligent attacks fully customizable by the user.
I hope this tutorial showing how to use hashcat was useful to you.