SSH is known, as Secure Shell, is the most popular network protocol that helps establish a secure connection between a server and client. Using the SSH, users can safely run commands on remote servers, forward ports, create tunnels, and perform other actions. The SSH supports different kinds of authentication techniques. One of the most common mechanisms is password authentication, and the other one is public-key-based authentication. In both, the public key-based authentication is more secure and convenient than the password authentication method and based on digital signatures.
This article will provide you a step-by-step SSH key generation guide for the Ubuntu system. We will discuss how to generate an SSH key and set up SSH key-based authentication on Ubuntu 20.04 system. Let us dive into the details!
Prerequisites
Root user privileges are required to run the administrative command on Ubuntu 20.04 system.
Generate SSH Key on Ubuntu 20.04 system
By following the below-mentioned procedure, you can easily generate the SSH key on Ubuntu 20.04 system:
Step 1: Create SSH Key Pair
First, generate the SSH key on the Ubuntu client machine. This machine connects with the server.
Verify SSH key pair if exist
Before creating the SSH key, ensure that you don’t already have the SSH key on your client system. Sometimes, you already have an SSH key pair on your Ubuntu system. Therefore, when you create a new key pair, it will be overwritten on the old one. To verify that either the SSH key file exists on your client machine or not, type the following command:

Generate new SSH key pair
If you will receive an error saying “No such file or directory” then, it means you don’t have an SSH key on your machine. So, move to the next step. Generate the SSH key pair on the Ubuntu client machine. To generate a new 4096 bits key pair with a user email address as a comment, execute the following command:
Or
If you run the above command “ssh-keygen”, it generates a default 3072-bit RSA key pair. To save the SSH key on the default location in the ‘.ssh/ ’ sub-directory, hit ‘Enter’.
Now, it will be asked to enter the passphrase. The passphrase includes an extra security layer. However, you need to enter each time when you log in on a remote machine. So, leave it as the default empty by pressing ‘Enter’. After that, the following whole output screen shows on the terminal:
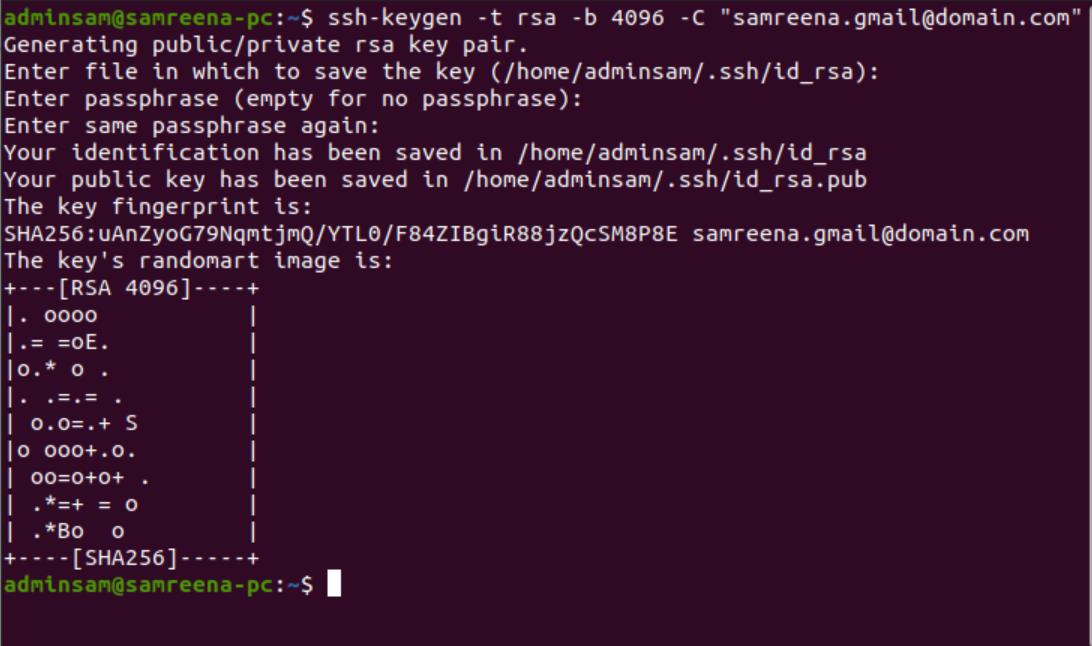
Verify SSH key pair generated
To check the ssh key pair is successfully generated on the client machine, use the below-mentioned command:
The following result displays on the terminal:

That means you have generated the SSH key pair successfully on the Ubuntu client system.
Step 2: Copy the public key to Ubuntu remote server
This step will copy the generated SSH public key to the remote Ubuntu server that you want to manage. Use the “ssh-copy-id” tool that is the recommended way to copy the public id to the remote server. Issue the below-mentioned command on the client machine to easily copy the public key on your remote Ubuntu server:
Replace the server_ipaddress with your system IP_address.
When you connect the first time your system, the following message may display on your terminal:
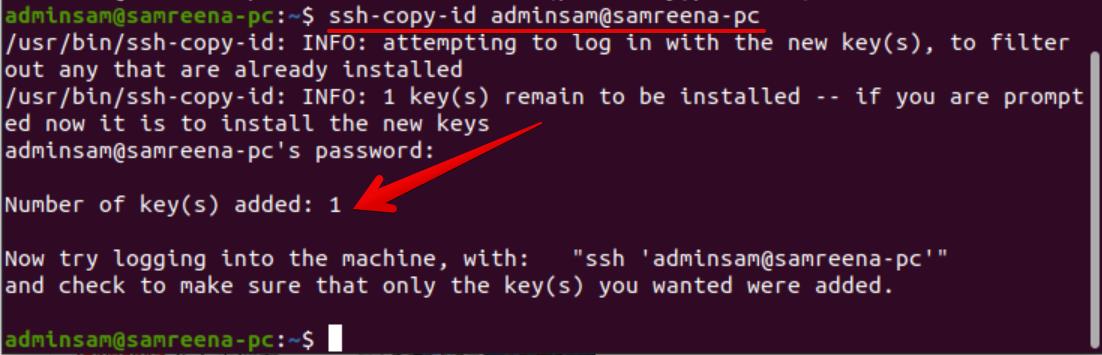
Type ‘yes’ and then press ‘Enter’ to continue the process. The server will check and verify the previously generated SSH key on the client machine. In the next step, you will be prompted to enter the user password for the server account and then hit the ‘Enter’ key from the keyboard. The following output receives on the terminal window:
Sometimes, you get an error using the ssh-copy-id method. In this case, an alternatively manual copy ssh key method is available. Use the below-mentioned command to copy the SSH public key on a server manually:
Replace user_name and server_ipaddress with details of your machine.
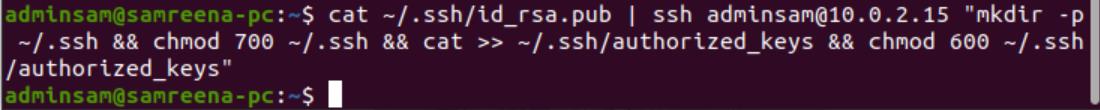
Step 3: Log in with the SSH key on a remote server
In this step, you will log in via ssh on your remote server by running the following command:
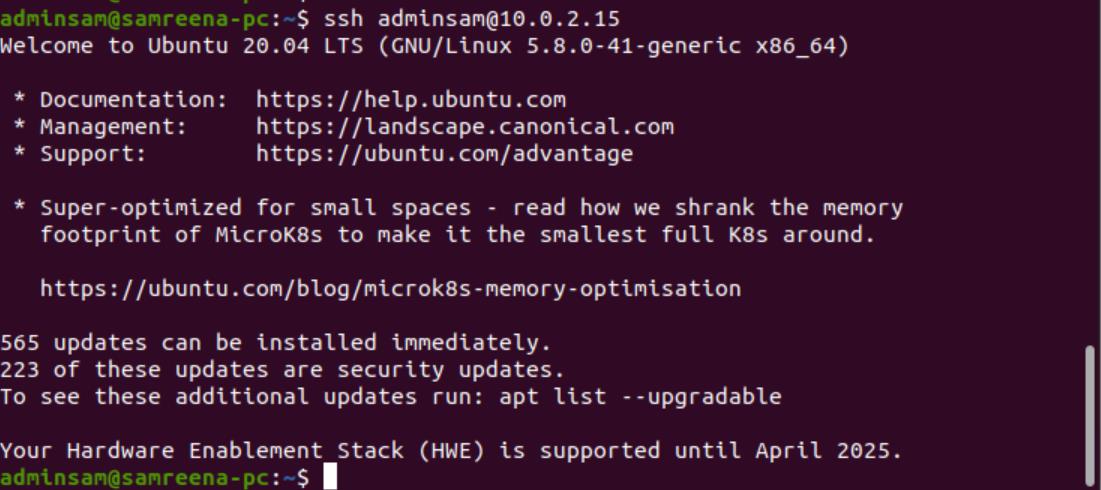
If you haven’t used the secure passphrase for the private key, you will be logged in immediately on a remote server. In another scenario, you will be asked to enter that secure passphrase you set previously.
Step 4: Disable SSH password authentication
In this step, you will disable the SSH password authentication to add an extra layer of security. Before disable, make sure that the user, which is login, has sudo privileges or a root account on this server. First, login into your remote server with a root account or sudo privileges. Now, open the ‘/etc/ssh/sshd_config’ SSH configuration file by executing the below-given command:
Find the following configuration line and set it with a ‘no’ argument.
Save the above configuration and exit from the file.
It’s time to restart the service of SSH on your server by running the below-mentioned command:
It would be best to verify that SSH is still working on your server before closing the current session. If everything is normally working, then the SSH password-authentication is disabled on your server.
Conclusion
By following the step-by-step guidelines of this article, you can generate the SSH key Ubuntu 20.04 system easily. Furthermore, we discussed how you could copy the SSH key to your remote server and disable the password-based authentication. I hope this guide will be simple and descriptive for solving your SSH key problem.
