A quick introduction to Fierce
Today, we will be introducing Fierce, a fantastic network mapping, and port scanning tool. Often used to locate non-contiguous IP space and hostnames across networks, Fierce is far more than just a simple IP scanner or a DDoS tool. It is a great reconnaissance tool that is used by whitehat communities all over the world.
Fierce is specifically designed for corporate networks and is used to discover likely targets in the networks of their systems. Capable of scanning for domains within minutes, Fierce is becoming the preferred tool for performing vulnerability checks in large networks.
Attributes
Some of it’s defining features include:
- performs reverse lookups for the specified range
- Internal and external IP ranges scanning
- Capable of performing entire Class C scan
- enumerates DNS records on targets
- Excellent Brute force capabilities coupled with reverse lookups should brute force fails to locate multiple hosts
- Name Servers discovery and Zone Transfer attack
To see more details on the functionalities and utilities of this software engineering marvel, run the -h flag on it.
How Fierce performs Scanning
Despite being such a resourceful and effective recon tool, it’s working is relatively simple. It starts the scanning process with brute force attacks if it is not possible for it to readily perform zone transfer of the target domain. Fierce uses a predetermined wordlist that contains possible subdomains it can detect. If a subdomain isn’t on the list, it will not be detected.
Performing a basic scan with Fierce
Let’s demonstrate how Fierce works with a simple scan with default settings. Here, we’re performing a basic scan on (websitename.com). To initiate scanning, type:
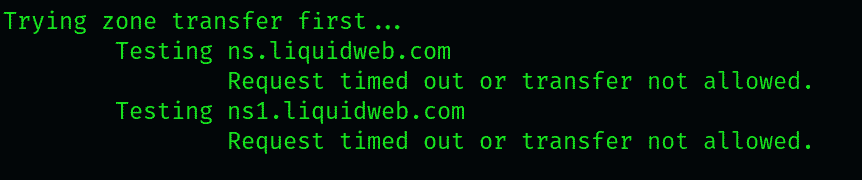
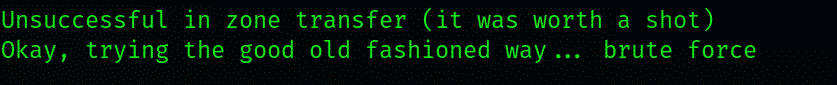
The scan inquires the names of the servers the target website is hosted on. Next, it will attempt a zone transfer against those servers, which is most likely to fail but, on rare occasions, may work. This is mostly because DNS queries made by the scan terminate against the third-party servers.
If the zone transfer fails, whe scan would attempt to locate the wildcard A record, which is relevant as it lists all the subdomains that are automatically assigned to an IP address. DNS A records look something like:
These records may or may not exist for a particular website, but if they do (let’s say for a website called our website), they will look something like:
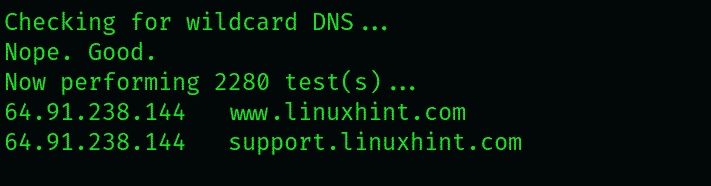
Notice how it shows the temp resolved to a.b.c.d. This is in part due to the fact that in DNS, a value of *, resolve a subdomain to its IP address. The attempts at brute-forcing subdomains performed are usually endured and neutralized by this type of record. Still, we can procure some relevant data by searching for additional values.
For example, you can tell whether a subdomain is legit by looking at the IP it is resolved to. If several URLs resolve to a specific IP, they’re likely forfeited to protect the server from the scans such as the one we’re performing here. Usually, websites with unique IP values are real.
Moving on to other scan results, you’ll see that 11 entries were detected from the 1594 words we checked. In our case, we found one entry(c.xkcd.com ) that contained vital information after thoroughly checking. Let us see what this entry has for us.
Looking at some of the information here, one can tell that some of them could be subdomains that Fierce couldn’t detect. We can use snippets from here to improve our wordlist that the scan uses to detect subdomains.
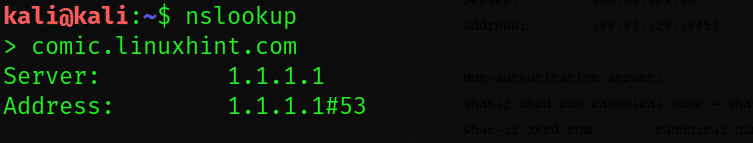
Let us instruct Fierce to perform fwd and reverse DNS lookups with the nslookup command.
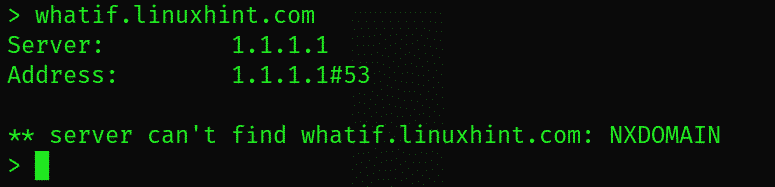
The nslookup utility has checked the comic.linuxhint.com subdomain and failed to get any results. However, it’s the inquiry of checking the whatif.linuxhint.com subdomain has yielded some substantial results: namely a CN and A record response.
Let us have a good look at the “whatif.linuxhint.com” subdomain results
Pay attention to the CNAME record, which is, in essence, a redirect. For example, if CNAME receives a query for whatif.xkcd.com, it’ll redirect the request to a similar dummy subdomain. There are then two more CNAME records, which ultimately land the request at prod.i.ssl.global.fastlylb.net, which is at IP address, as seen by the last A record.
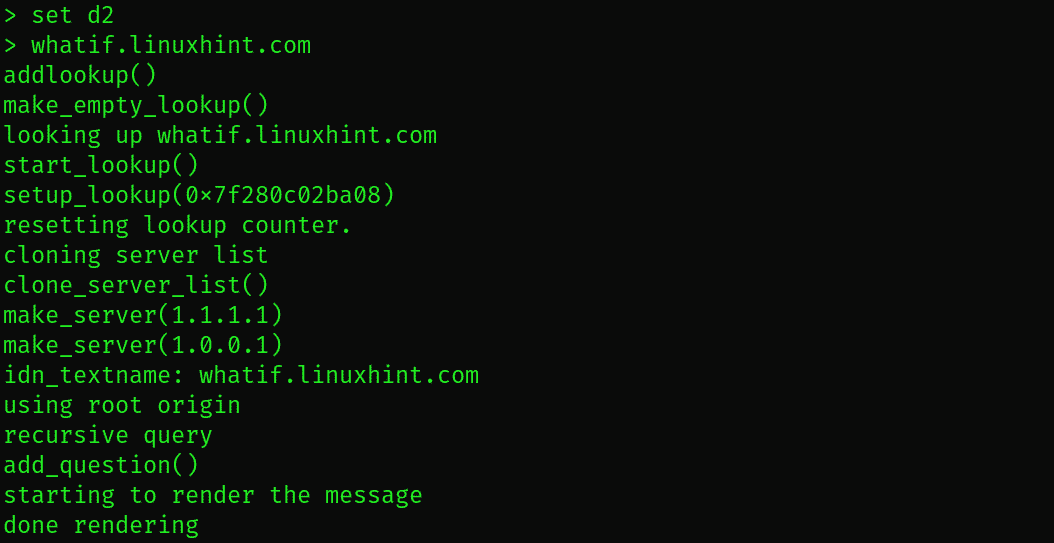
You can enter nslookup’s verbose mode by typing nslookup type set d2 to see the results in much more detail.
$ nslookup > whatif.linuxhint.com
We highly recommend that you familiarize yourself with the nslookup command. It is available on all popular operating systems, and it saves you a whole lot of your time when you’re probing a server for subdomains.
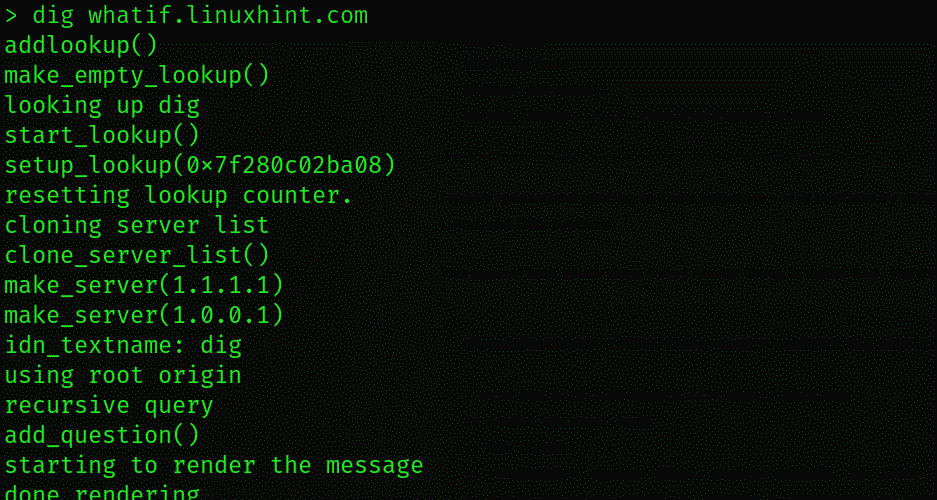
There’s another great tool called dig, which has a similar function. Activate dig, and you’ll be presented the following:
With the IPs returned, we can get our hands on some more useful stuff about the networks we have been scanning. If we were conducting a pentest for a company, we might have got some idea about their public IP space and could warrant investigating related Ips for investigation.
To sum up:
As we’ve previously mentioned, Fierce is much more than a simple network scanner. We have listed below some of the commands and their uses; I recommend you try out next.
- Wordlist –lets you specify a wordlist file which to search a server for subdomains.
- connect – This feature establishes a connection with identified subdomains during the scan
- delay – specifies a delay in seconds between queries to the server
- dnsserver – send dnsserver requests
- file – downloads the scan results to a specified directory