Installing LUKS
LUKS is a part of the “cryptsetup” package, you can install it in Ubuntu by running the command below:
You can install cryptsetup on Fedora by running the command below:
Cryptsetup can be installed on ArchLinux using the following command:
You can also compile it from its source code available here.
Finding Connected Storage Drives on a Linux System
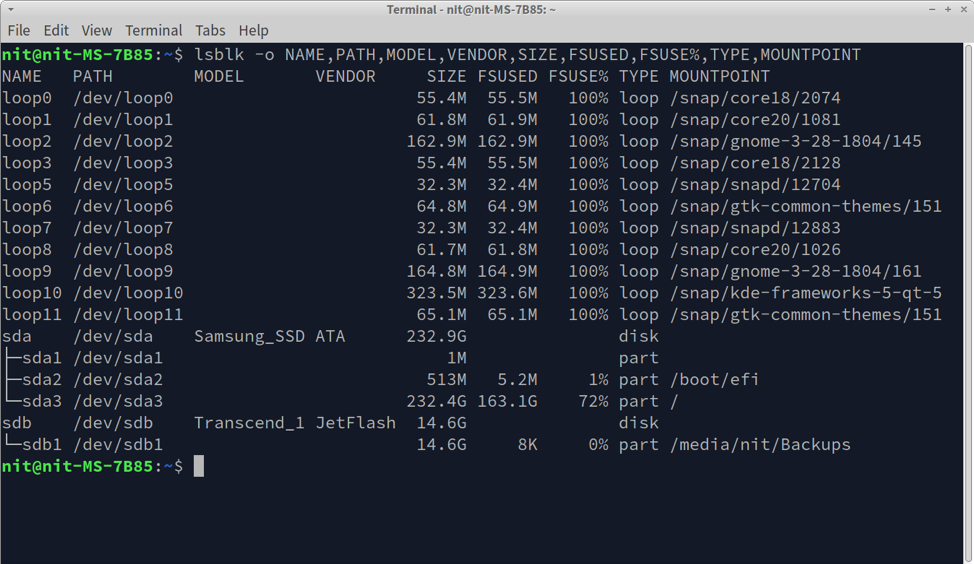
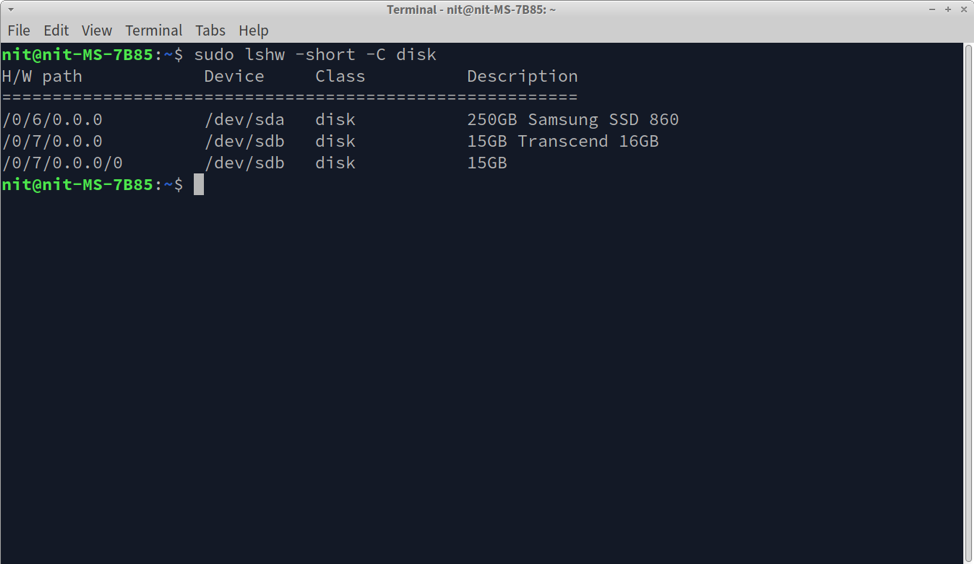
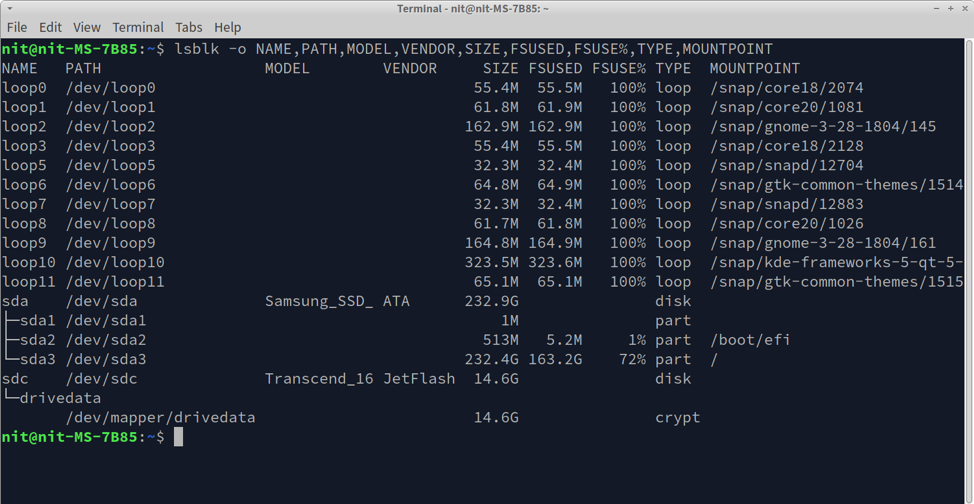
To encrypt a drive using LUKS, you will first need to determine its correct path. You can run the command below to list all storage drives installed in your Linux system.
You will see some output similar to this in a terminal:
If you look at the output and drive metadata, you can easily find a path for connected drives (listed under “PATH” column). For instance, I have connected an external thumb drive made by Transcend. Looking at the screenshot, it can be inferred that the path for this drive is “/dev/sdb”.
Alternatively, you can run the command below to find the correct path for any connected storage drive.
You will get some output similar to this.
Whatever is the drive path in your case, make a note of it as it will be used during LUKS encryption.
Encrypting a Drive Using LUKS
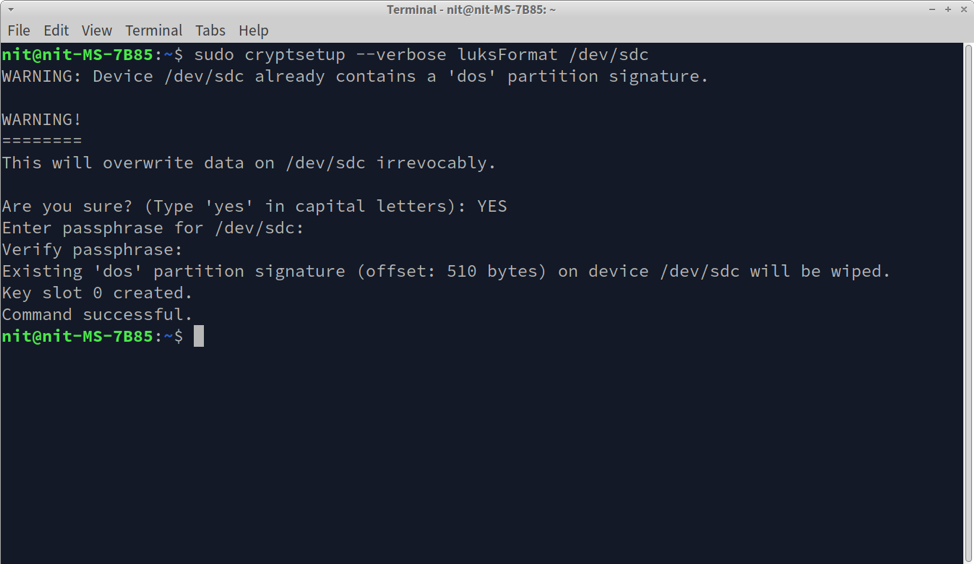
Before moving ahead, you should know that LUKS encryption will remove all existing data on the drive. If there are important files on the storage drive, make a backup beforehand.
Now that you have the drive path from the previous step, you can encrypt a drive using LUKS by running the command below. Make sure to replace “/dev/sdc” with the drive path you found in the previous step.
Follow on-screen instructions and enter a password.
In the end, you should get a “Command successful” message indicating that encryption has been successful.
You can also dump the encryption metadata and verify that drive has been encrypted successfully by running the command below (replace “/dev/sdc” as needed):
Decrypting and Mounting a LUKS Encrypted Drive
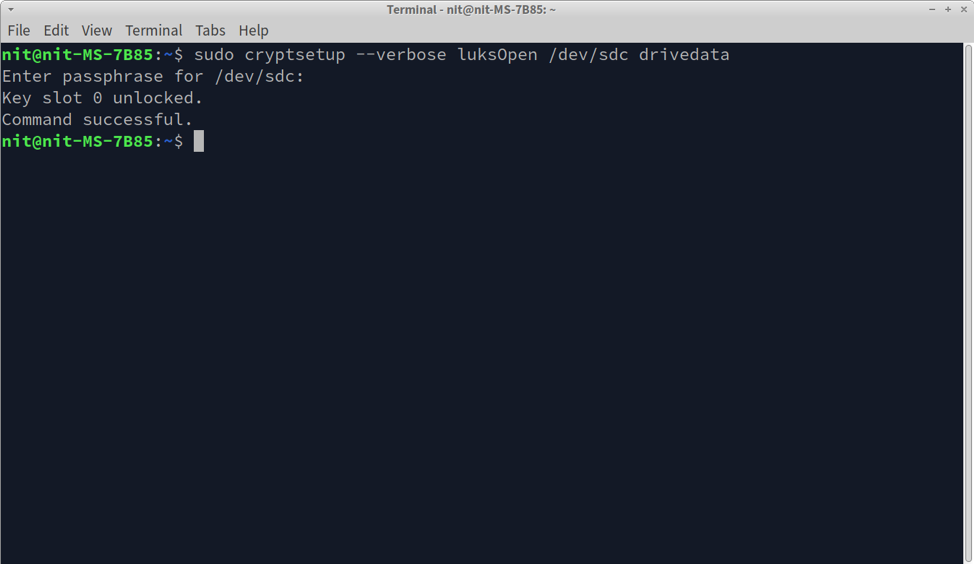
To decrypt a drive encrypted using LUKS, run the command below while specifying the path of the encrypted drive connected to your system. You can replace “drivedata” with any other name, it will act as an identifier for the decrypted device.
The “Command successful” message indicates that the drive has been decrypted and mapped as a new storage device called “drivedata” on your system. If you run the “lsblk” command, the mapped drive will appear as a new storage drive connected to your Linux system.
Upto this point the LUKS encrypted drive has been decrypted and mapped as a device, but not mounted. You can check information about mapped drive by running the command below (replace “drivedata” as needed):
The mapped drive acts as a real storage device connected to your system. But it doesn’t contain any partitions with file-systems yet. To read and write files in the mapped drive, you will need to create a partition. To create an EXT4 partition, run the following command while specifying the path of the mapped drive.
Wait for the process to finish. This step needs to be done only once or when you need to force wipe the whole partition. Do not perform this step everytime you connect the encrypted drive as it will wipe the existing data.
To manage files on the mapped drive formatted as an EXT4 partition, you will need to mount it. To do so, run the following two commands in succession.
$ sudo mount /dev/mapper/drivedata /media/mydrive
The first command creates a new mount point for the mapped drive. You can supply any path to it. The next command mounts the mapped drive so that you can access it from the path specified in the previous command.
Once mounted, you will be able to access the mapped drive from a graphical file manager or from the command line like any other storage drive. To unmount, run the following command while specifying the full path of the mount point.
Conclusion
LUKS provides a way to encrypt an entire storage drive which can only be accessed using the password created during the encryption. Since it is an on-disk encryption system where encryption information is stored on the encrypted device itself, you can just plug the encrypted drive on any Linux system and decrypt it using LUKS to get immediate access to encrypted data.