Generally, different partitions are created on a hard drive and each partition needs to be encrypted using different keys. This way you have to manage multiple keys for different partitions. LVM volumes encrypted with LUKS solve the problem of multiple keys management. First, the entire hard disk is encrypted with LUKS and then this hard drive can be used as physical volume. The guide demonstrates the encryption process with LUKS by following the given steps:
- cryptsetup package installation
- Hard drive encryption with LUKS
- Creating encrypted logical volumes
- Changing encryption passphrase
Installing cryptsetup Package
In order to encrypt the LVM volumes with LUKS, install the required packages as follows:
Now, load the kernel modules used to handle encryption.
Encrypt Hard Drive with LUKS
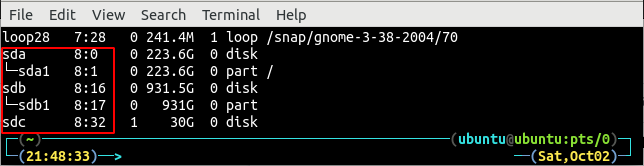
First step to encrypt the volumes with LUKS is to identify the hard drive on which LVM is going to be created. Display all the hard disks on the system using the lsblk command.
Currently, there are three hard drives attached to the system that are /dev/sda, /dev/sdb and /dev/sdc. For this tutorial, we will use the /dev/sdc hard drive to encrypt with LUKS. First create a LUKS partition using the following command.
It will ask for the confirmation and a passphrase to create a LUKS partition. For now, you can enter a passphrase that is not much secure as this will be used only for random data generation.
NOTE: Before applying the above command, make sure there is not any important data in the hard drive as it will clean the drive with no chances of data recovery.
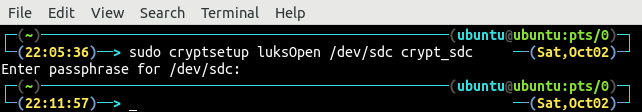
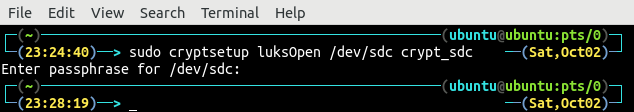
After hard drive encryption, open and map it as crypt_sdc using the following command:
It will ask for the passphrase to open the encrypted hard drive. Use the passphrase for encrypting the hard drive in the previous step:
List all the connected devices on the system using the lsblk command. The type of the mapped encrypted partition will appear as the crypt instead of part.
After opening the LUKS partition, now fill the mapped device with 0s using the following command:
This command will fill the complete hard drive with 0s. Use the hexdump command to read the hard drive:
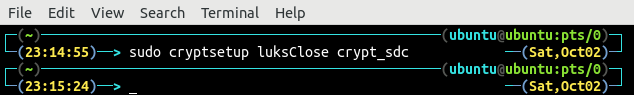
Close and destroy the mapping of the crypt_sdc using the following command:
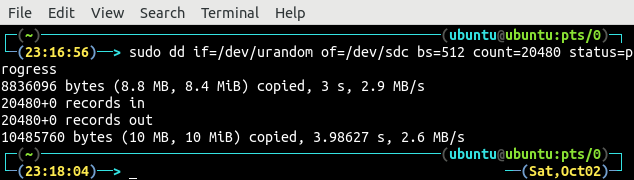
Override the hard drive header with random data using the dd command.
Now our hard drive is full of random data and it is ready to be encrypted. Again, create a LUKS partition by using the luksFormat method of the cryptsetup tool.
For this time, use a secure passphrase as this will be used to unlock the hard drive.
Again, map the encrypted hard drive as crypt_sdc:
Creating Encrypted Logical Volumes
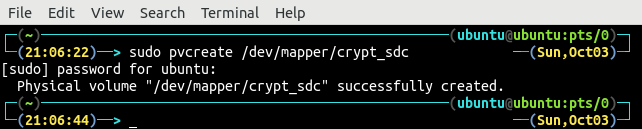
So far, we have encrypted the hard drive and mapped it as crypt_sdc on the system. Now, we will create logical volumes on the encrypted hard drive. First of all, use the encrypted hard drive as physical volume.
While creating the physical volume, the target drive must be the mapped hard drive i.e /dev/mapper/crypte_sdc in this case.
List all the available physical volumes using the pvs command.
The newly created physical volume from the encrypted hard drive is named as /dev/mapper/crypt_sdc:
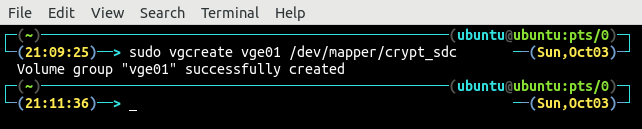
Now, create the volume group vge01 which will span the physical volume created in the previous step.
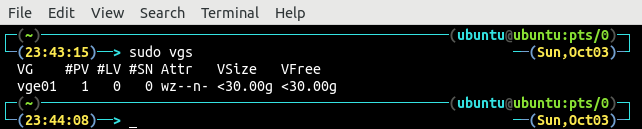
List all the available volume groups on the system using the vgs command.
The volume group vge01 is spanning over one physical volume and the total size of the volume group is 30GB.
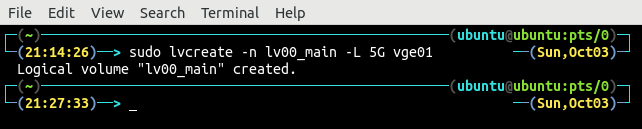
After creating the volume group vge01, now create as many logical volumes as you want. Generally, four logical volumes are created for root, swap, home and data partitions. This tutorial only creates one logical volume for demonstration.
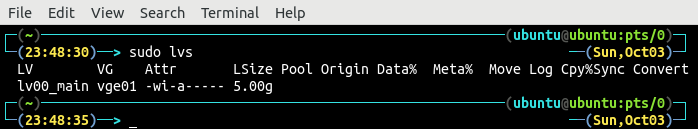
List all the existing logical volumes using the lvs command.
There is only one logical volume lv00_main which is created in the previous step with a size of 5GB.
Changing Encryption Passphrase
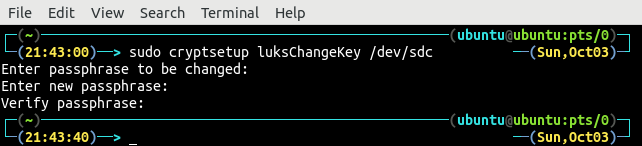
Rotating the passphrase of the encrypted hard drive is one of the best practices to secure the data. The passphrase of the encrypted hard drive can be changed by using the luksChangeKey method of the cryptsetup tool.
While changing the passphrase of the encrypted hard drive, the target drive is the actual hard drive instead of the mapper drive. Before changing the passphrase, it will ask for the old passphrase.
Conclusion
The data at rest can be secured by encrypting the logical volumes. Logical volumes provide flexibility to extend the size of the volume without any downtime and encrypting the logical volumes secures the stored data. This blog explains all the steps required to encrypt the hard drive with LUKS. The logical volumes then can be created on the hard drive that are automatically encrypted.