A storage device can be encrypted with LUKS in 2 different methods:
Key-based encryption
An encryption key (stored in a file) is used to encrypt the storage device. To decrypt the storage device, the encryption key is required. If a device is encrypted this way, you can automatically decrypt the storage device at boot time and mount it. This method is good for servers.
Passphrase-based encryption
The storage device will be encrypted with a passphrase. You will need to type in the passphrase every time you want to decrypt the storage device and use it. If you encrypt your system storage device this way, you will be asked for the passphrase every time you boot your computer. You won’t be able to automatically decrypt and mount the storage device at boot time. So, this method is good for desktop computers.
You can also use this encryption method for your external storage devices (external HDDs/SSDs and USB thumb drives). As these devices won’t be connected to your computer all the time and you won’t need to mount them automatically, this method is very appropriate for these types of storage devices.
In this article, I am going to show you how to install cryptsetup on your computer and encrypt a filesystem with LUKS passphrase encryption. For key-based encryption, take a look at the article How to Encrypt a Btrfs Filesystem. So, let’s get started.
Installing cryptsetup on Ubuntu/Debian
cryptsetup is available in the official package repository of Ubuntu/Debian. So, you can install it easily on your computer. First, update the APT package repository cache with the following command:
Then, install cryptsetup with the following command:
To confirm the installation, press Y and then press <Enter>.
cryptsetup should be installed.
Installing cryptsetup on CentOS/RHEL 8:
cryptsetup is available in the official package repository of CentOS/RHEL 8. So, you can install it easily on your computer. First, update the DNF package repository cache with the following command:
To install cryptsetup, run the following command:
cryptsetup should be installed.
In my case, it is already installed.
Installing cryptsetup on Fedora 34:
cryptsetup is available in the official package repository of Fedora 34. So, you can install it easily on your computer. First, update the DNF package repository cache with the following command:
Run the following command to install cryptsetup,:
cryptsetup should be installed.
In my case, it is already installed.
Installing cryptsetup on Arch Linux:
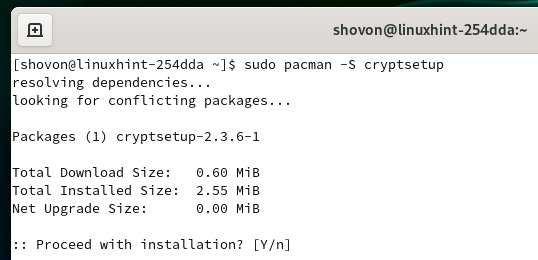
cryptsetup is available in the official package repository of Arch Linux. So, you can easily install it on your computer. First, update the Pacman package repository cache with the following command:
Run the following command to install cryptsetup,:
To confirm the installation, press Y and then press <Enter>.
cryptsetup should be installed.
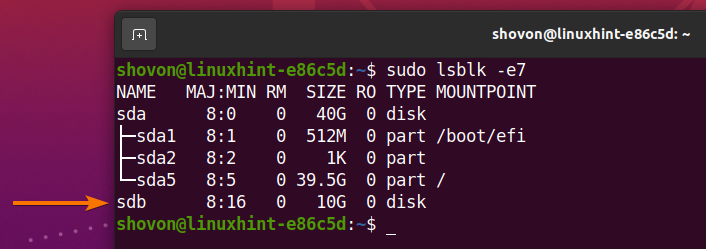
Finding the Name of your Storage Device:
To encrypt a storage device, you need to know the name or ID of that storage device.
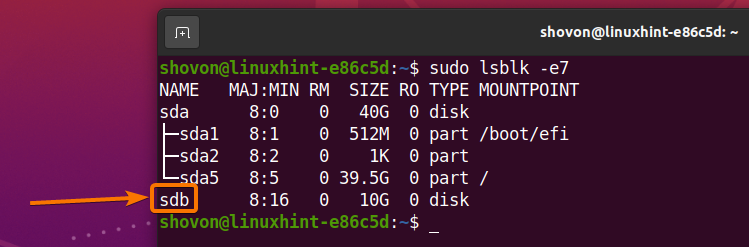
To find the name or ID of the storage device, run the following command:
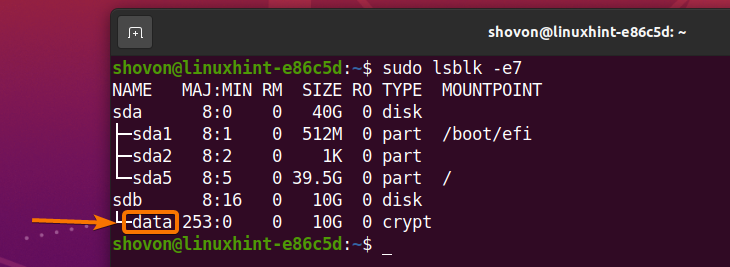
All the storage devices installed on your computer should be listed as you can see in the screenshot below. You should find the name or ID of the storage device you want to encrypt from here.
In this article, I will encrypt the sdb storage device for the demonstration.
Encrypting Storage Devices with LUKS:
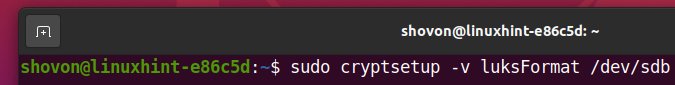
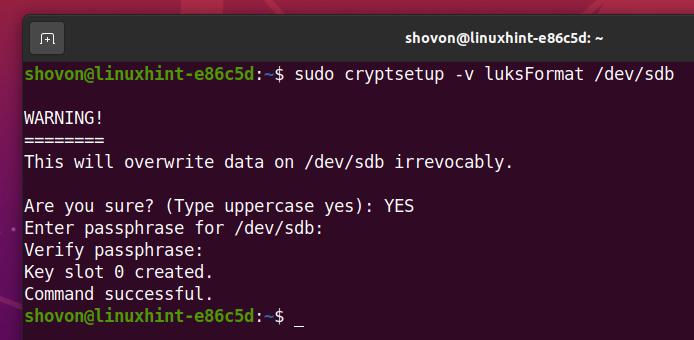
To encrypt the storage device sdb with LUKS passphrase, run the following command:
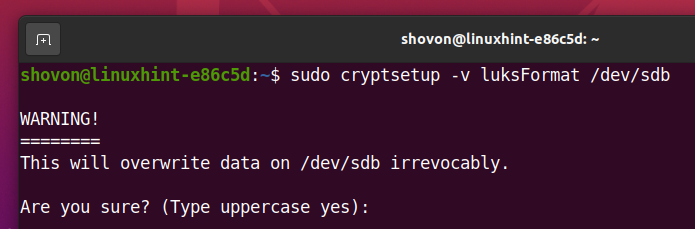
Type in YES (must be in capital letters) and press <Enter>.
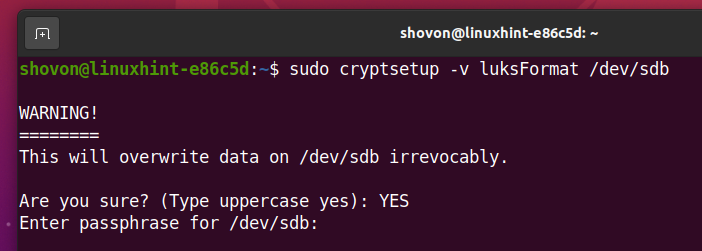
Type in a LUKS passphrase and press <Enter>.
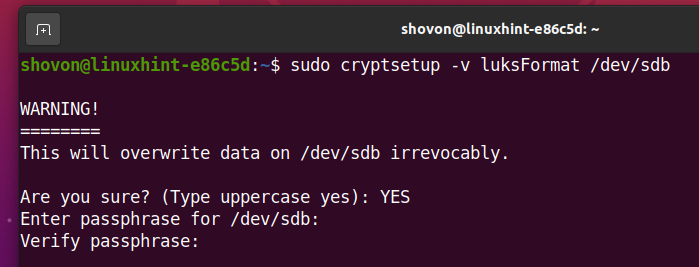
Retype the LUKS passphrase and press <Enter>.
Your storage device sdb should be encrypted with LUKS and your desired LUKS passphrase should be set.
Opening the Encrypted Storage Device:
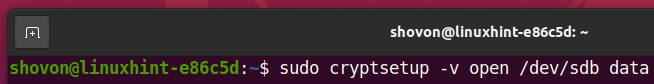
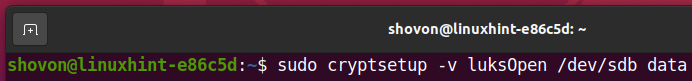
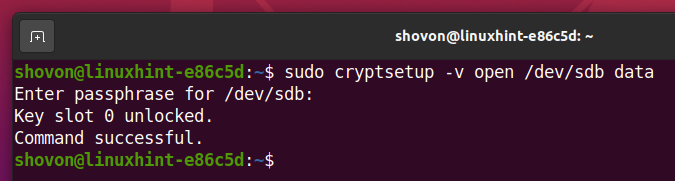
Once your storage device sdb is encrypted, you can decrypt it and map it as data on your computer with one of the following commands:
Or,
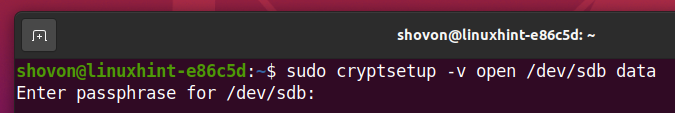
Type in the LUKS passphrase that you’ve set earlier to decrypt the sdb storage device.
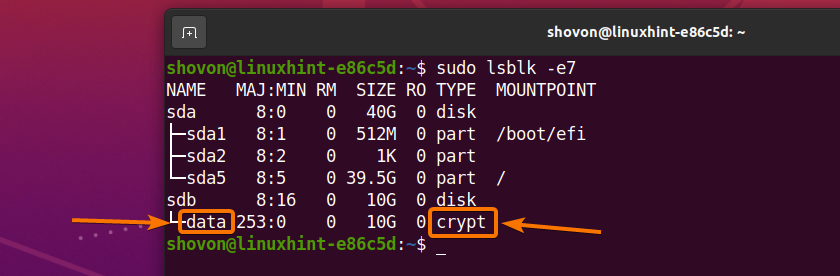
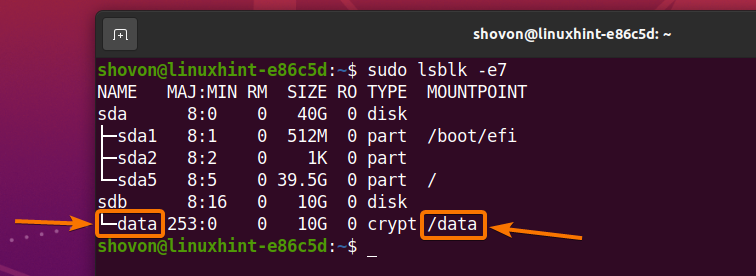
The storage device sdb should be decrypted and it should be mapped as a data storage device on your computer.
As you can see, a new storage device data is created and it is of the type crypt.
Creating a Filesystem on the Decrypted Storage Device:
Once you’ve decrypted the storage device sdb and mapped it as data storage device, you can use the mapped storage device data as usual.
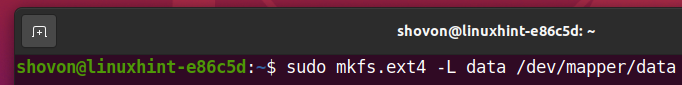
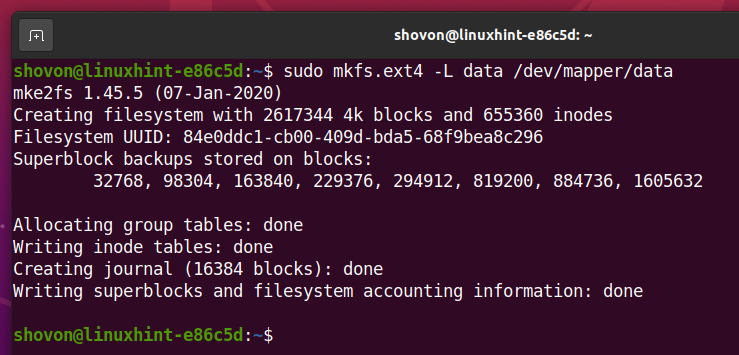
To create an EXT4 filesystem on the decrypted storage device data, run the following command:
An EXT4 filesystem should be created on the decrypted storage device data.
Mounting the Decrypted Filesystem:
Once you’ve created a filesystem on your decrypted storage device data, you can mount it on your computer as usual.
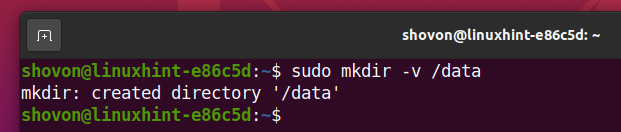
First, create a mount point /data as follows:
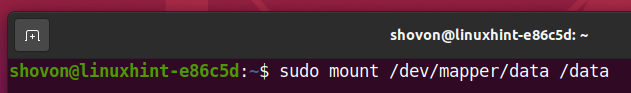
Then, mount the decrypted storage device data on the /data directory as follows:
As you can see, the decrypted storage device data is mounted on the /data directory.
Unmounting the Decrypted Filesystem:
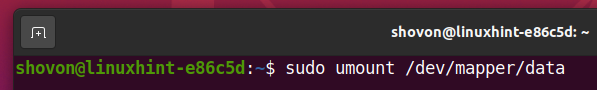
Once you’re done working with the decrypted storage device data, you can unmount it with the following command:
As you can see, the decrypted storage device data is not mounted on the /data directory anymore.
Closing the Decrypted Storage Device:
You can close the decrypted storage device data from your computer as well. The next time you want to use the storage device, you will have to decrypt it again if you close it.
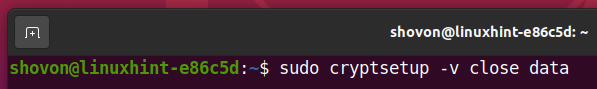
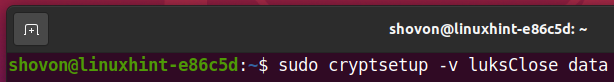
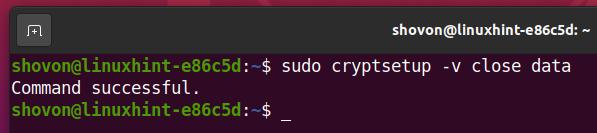
To close the decrypted storage device data from your computer, run one of the following commands:
Or,
The decrypted storage device data should be closed.
As you can see, the decrypted storage device data is not available anymore.
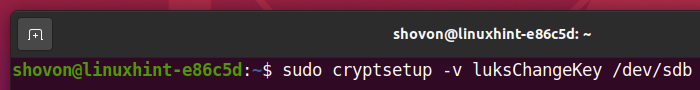
Changing LUKS Passphrase for the Encrypted Storage Device:
You can change the LUKS passphrase of your LUKS encrypted storage devices as well.
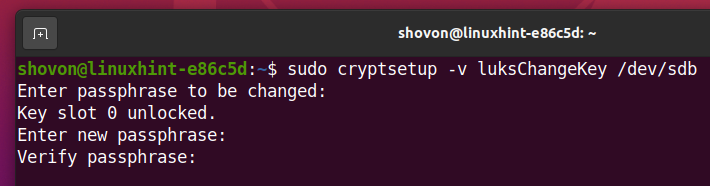
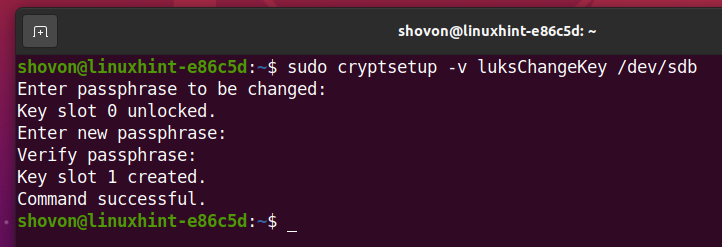
To change the LUKS passphrase of the encrypted storage device sdb, run the following command:
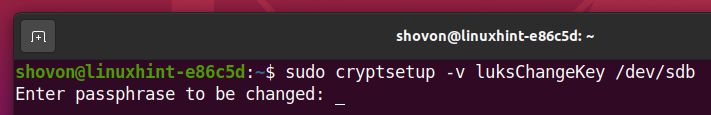
Type in your current LUKS passphrase and press <Enter>.
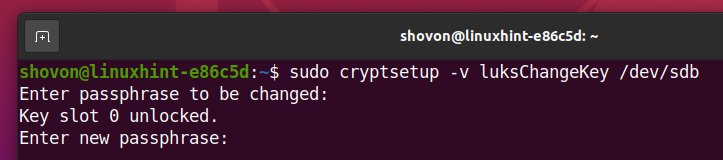
Now, type in a new LUKS passphrase and press <Enter>.
Retype the new LUKS passphrase and press <Enter>.
The new LUKS passphrase should be set as you can see in the screenshot below.
Conclusion
In this article, I have shown you how to install cryptsetup on Ubuntu/Debian, CentOS/RHEL 8, Fedora 34, and Arch Linux. I have also shown you how to encrypt a storage device with LUKS passphrase, open/decrypt the encrypted storage device, format it, mount it, unmount it, and close it. I have shown you how to change the LUKS passphrase as well.