In order to protect your AWS account, AWS also provides different ways to enable multi-factor authentication. This blog will discuss how multi-factor authentication can be enabled on your AWS account for enhanced security.
MFA Devices for AWS
There are several ways available for MFA which can be applied to achieve better account protection. AWS supports major two types of multi-factor authentications, which are as follows
- Virtual MFA Devices
- U2F Security Key
- Hardware MFA Devices
Virtual MFA Devices:
You can use your smartphone as a virtual MFA device for your AWS account. For this, you just need to install a software application (Google authenticator or Authy) on your smartphone. Every time you try to login into your account, you will be asked to provide a six-digit code generated on your mobile application. The code is unique and just for one-time usage, which means a new code will be generated each time you login to your account. Each virtual MFA device works only for the account for which it is authenticated.
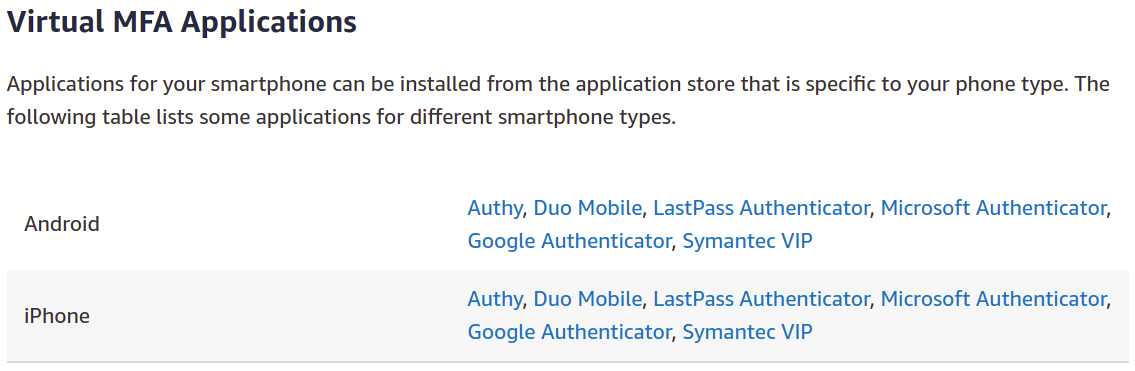
There are multiple apps available for MFA authentication on AWS; you can use any of them according to your device compatibility.
You can use any of them according to your device compatibility.
Enabling Virtual MFA Device on AWS
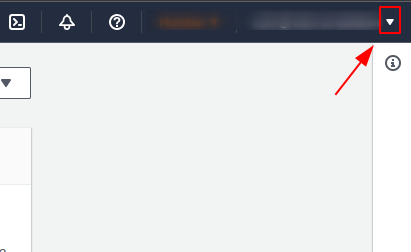
To use MFA on your account, just login to your management console using AWS credentials. From the management console, click on the menu icon in the top right corner adjacent to your account ID.
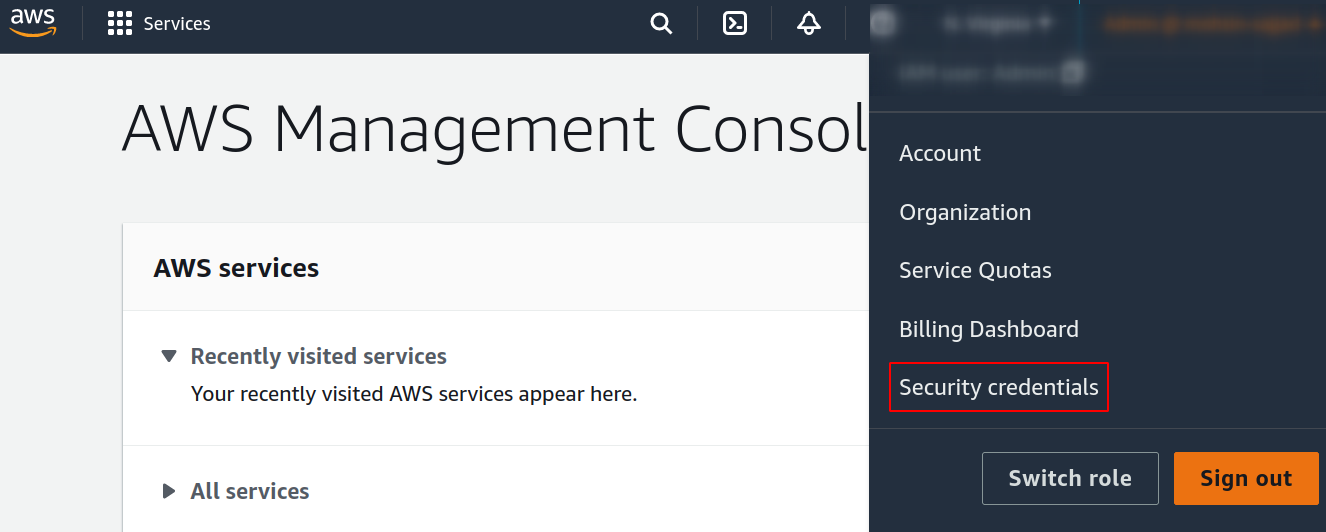
From the drop-down menu, click on the Security credentials option.
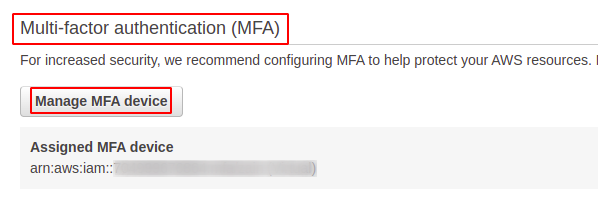
In the AWS IAM credentials tab, scroll down to the Multi-factor authentication (MFA) section and click on the Manage MFA device button.
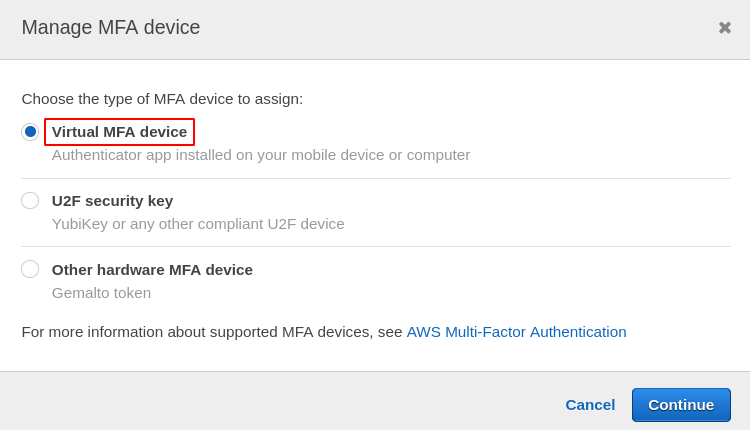
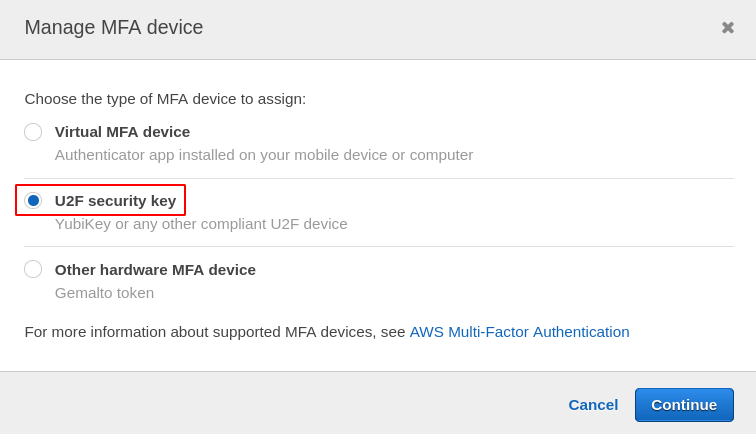
From the dialog box that appears, you need to choose the device type for MFA. For this demo, we will use a Virtual MFA device for enabling multi-factor authentication.
At this point, you need to have or install your MFA application on the device you want to attach as an MFA device. For this demo, we will use Authy as a virtual MFA device. Go to the following link to install the Authy from the Google play store on your Android device.
https://play.google.com/store/apps/details?id=com.authy.authy&hl=en&gl=US
If you are using the MFA application for the first time, you have to set up an account.
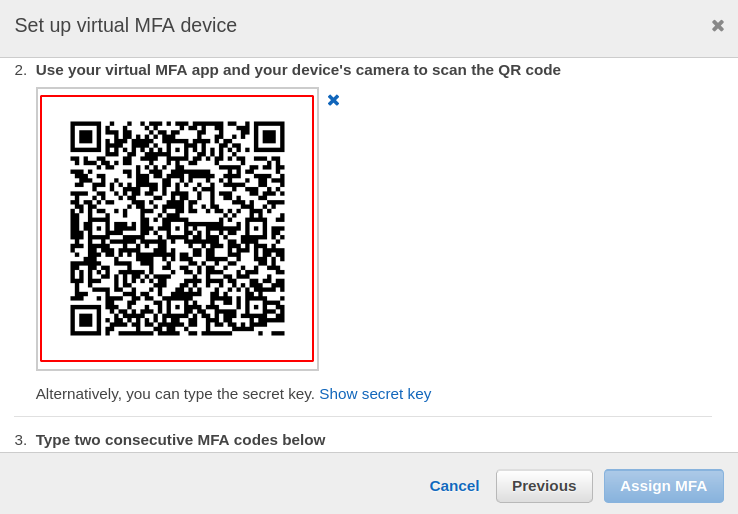
Now you need to attach AWS users with a device for which you need to scan the QR code provided by AWS, or you can either enter the security key manually.
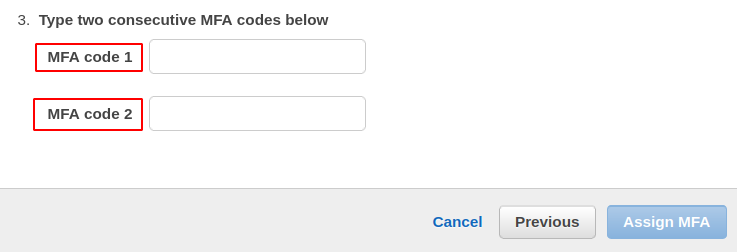
After you have scanned the QR code or entered the security key, the application will provide two MFA codes to authenticate the device.
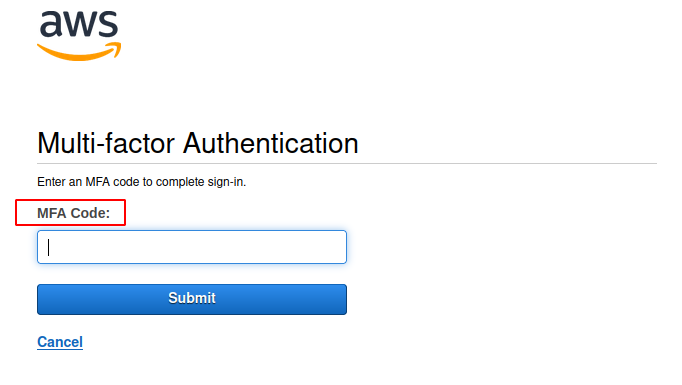
Next time when you try to login to your user, AWS will ask to enter the MFA code from your device.
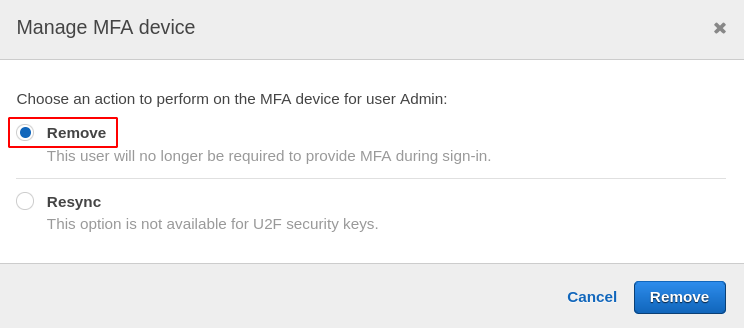
Now, if you plan to remove the MFA device from your account, simply go to the MFA tab and select remove, so next time you will not require your device for login.
So now you have successfully set-up MFA on your AWS account.
Enabling Virtual MFA Device using CLI
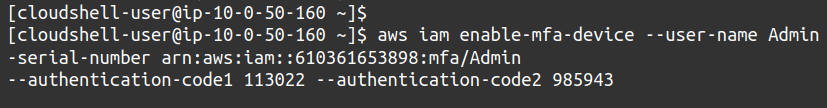
You can also enable an MFA device using the command line interface, and you definitely need to learn to use CLI for MFA because there are some cases like MFA delete on S3 where you cannot use the management console and require CLI.
To enable MFA using CLI, you need to provide the AWS user account ID on which you want to enable the MFA, the serial number of the hardware device or ARN of a virtual MFA device and two MFA codes from your device. The commands you need are as follows.
--user-name <AWS user name> \
--serial-number <MFA device Serial number> \
--authentication-code1 <MFA code> \
--authentication-code2 <MFA-code>
So this way, you can easily enable MFA using CLI on a user account.
U2F Security Key
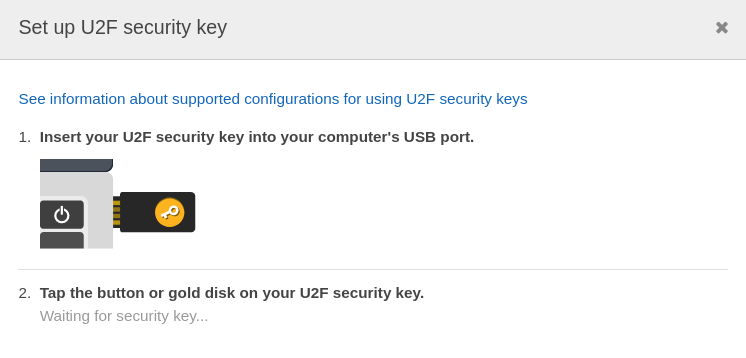
Universal 2nd factor (U2F) security key is a hardware device by Yubico which you need to purchase yourself from the market. This is simply a USB device you need to plug-in into your system.
To set up a U2F device on your AWS account, go to the manage MFA device tab and select the U2F security key while enabling multi-factor authentication.
Now attach a security key to the system and press the button on the device, and you are good to go.
So you have successfully set-up MFA on your account using a U2F security key.
Hardware MFA Devices
Other types of hardware MFA devices can generate unique 6-digit codes based on a one-time password algorithm. These devices can work even without an internet or smartphone connection; you just need to enter the code shown on the small LCD on the device.AWS supports hardware MFA devices to provide additional security and privacy for its users. You have to purchase these devices yourself.
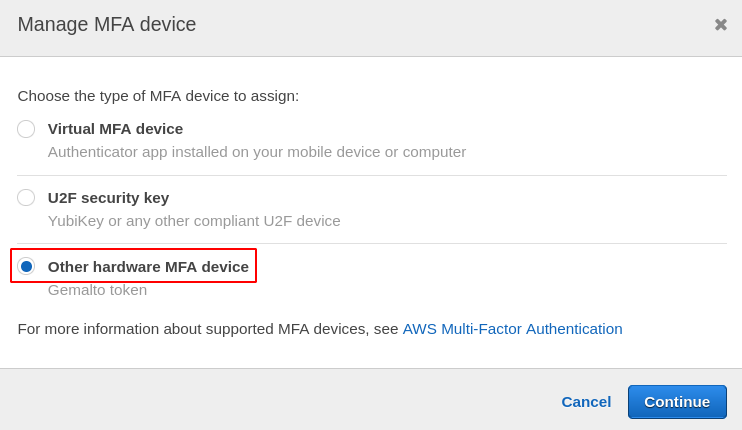
To enable it on your AWS account, just open the manage MFA tab and choose other hardware MFA devices.
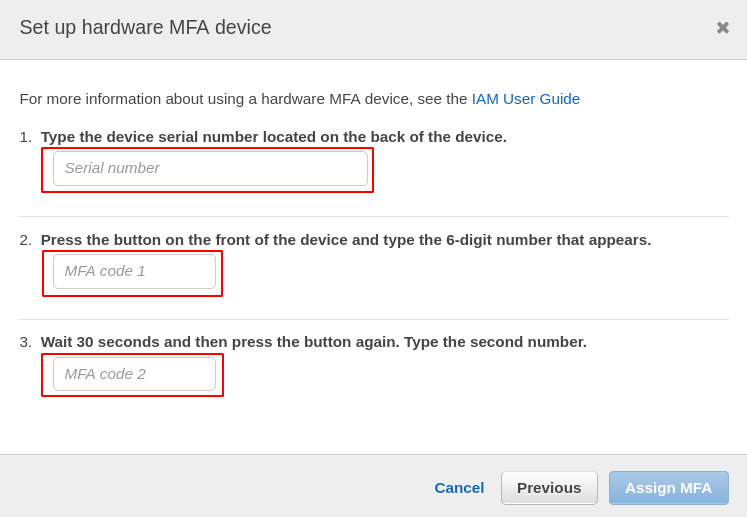
Now all you need is to enter the serial number of the device you have purchased and then press the button on the device to reveal a new MFA code for you. You will be asked twice to enter the MFA code from your device, and the process is complete.
After this, click on assign MFA in the bottom right corner, and you will have your MFA activated on your account.
Conclusion:
Multi-factor authentication (MFA) has become very common these days to keep your accounts secure from unauthorized access if your login credentials get leaked due to any system breach or hackers attack. MFA provides an additional layer of security, and there are multiple ways you can use this to secure your accounts. You can either use a virtual MFA device like your smartphone or buy yourself a hardware MFA device. You can also set up a single MFA device for multiple accounts, but you need to keep your devices safe and secure because you may get into trouble if you lose your MFA devices. This blog describes the detailed procedure to enable multi-factor authentication on your AWS account.