“Elasticsearch is a free and open-source search and analytics engine. Elasticsearch is robust, with numerous tools and features for ingesting and visualizing data using Logstash and Kibana.
One of the best ways to secure your Elasticsearch cluster is to avoid exposing it to the internet. Therefore, blocking all HTTP requests is an excellent measure unless they are coming from localhost.
This tutorial will discuss two main methods of blocking remote requests from hitting your Elasticsearch cluster. If you want to access outside your local machine, consider an Nginx proxy to sit between the outside world and your Elasticsearch cluster.”
Method 1 – Restrict Host to Localhost
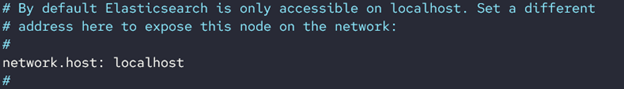
One of the best ways to block remote requests to Elasticsearch is to set the node address to localhost. In the elasticsearch.yml file, you will find the entry network.host.
This entry allows you to define the address under which the Elasticsearch cluster will run. In addition, this entry specifies the address for HTTP & transport traffic used in node communication.
You can specify an IP address or a hostname.
To disable remote requests, set the value to localhost or 127.0.0.1.
Set the value:
Save the file and restart the service. You have successfully ensured that requests outside your local machine cannot access the server.
Method 2 – Using Firewall
Like all networking concerns, we can implement a firewall to handle network security. The second method we can use is a firewall to allow only local connections to the Elasticsearch cluster.
For this tutorial, we will use the UFW firewall as its easy to use and configure.
To allow only localhost traffic to Elasticsearch, run the command:
This will allow UFW to allow any connection from localhost to go through to your Elasticsearch cluster.
If Elasticsearch runs on a different port, change the port value from 9200 to your custom port.
Termination
In this post, you discovered two main methods of blocking any requests that do not originate from localhost from reaching your Elasticsearch cluster.
We hope you found this article helpful. Thanks for reading, and catch you in the next one.