eBPF stands for extended Berkeley Packet Filter. When you work with Linux and you want to interact with the kernel, you need a framework like eBPF to help you. The eBPF is a framework that is designed to help the developers run the low-level kernel programs without hindrance.
With eBPF, you can quickly load and run the software with minimal overhead configuration. If you are new to eBPF and you’re working with kernel programs, this guide will help you in understanding about eBPF and how to use it. We will present a few instances of injecting the code to the kernel using eBPF.
Let’s begin!
What Is eBPF
eBPF is an acronym for extended Berkeley Packer Filter. It acts as an interface in the Linux kernel that lets the developers to inject the code to interact with the kernel such as modifying its behavior or observing it.
eBPF was first released as a packet tracer but was later extended in 2014 and integrated into the Linux kernel. Although it mainly helps with tracing tasks, it has plenty of functionalities including allowing the user space applications to execute the programs in the kernel space.
A computer’s memory has the user space and kernel space. The user programs run in the user space while the kernel space is reserved to run the drivers and the kernel. The user programs can’t run in the kernel space. The aim is to ensure that the unsafe programs or other vulnerabilities can’t be inserted into the kernel and crash it.
However, eBPF offers a pathway for you to run the user programs in the kernel space as bytecode. Since byte codes are hard to write, you need the development frameworks like BCC or Bpftrace to write the eBPF programs. These frameworks are open-source, and anyone can use them. You can install the BCC or the Bpftrace frameworks and the create eBPF programs.
Installing BCC
The BCC is a collection of BPF compiler collection tools that help with writing and running the eBPF programs.
Start by updating your apt repository:
Install the BPF compiler collection tools with the following command:
The appropriate BCC tools for your kernel architecture are fetched and installed. Press “y” to confirm the installation.
You can verify that BCC is installed and working by running one of its tools to get the PID of any command that you run on the terminal.
Open two terminal windows. Run the following bpfcc command on the first terminal:
Run a few commands like in the following image on the second terminal:
If BCC and eBPF are working on the first terminal, you will see the PIDs of the commands that you entered on the second window and the timestamps.
Your BCC is installed. You can now execute the different eBPF programs to inject the code into the kernel for different purposes.
Installing Bpftrace
Aside from using the BCC framework, you can use the Bpftrace framework. It is ideal for different tasks and offers a command-line utility that lets the users execute the eBPF commands directly.
Install it with the following command:
With the Bpftrace installed, you can deploy your eBPF programs. Let’s have a few examples of deploying various programs using the command-line utility.
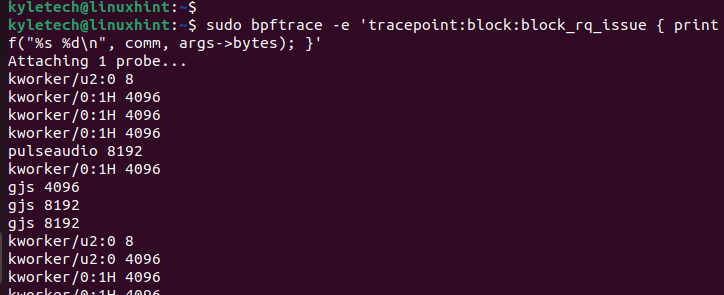
From the Bpftrace GitHub repo, you can deploy the different “one-liners” programs. For instance, you can list the disk consumption by different processes by running the following program:
From the output, you will notice that the columns display the process name, the disk size, and the disk size.
The output displays all processes in your kernel.
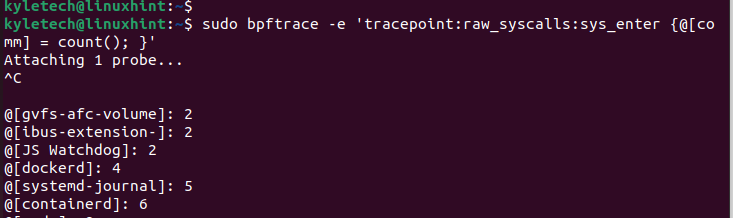
If you also want to check the syscall counts by process, you can utilize the Bpftrace one-liners program with the following command:
The syscalls are displayed after pressing Ctrl + C to kill the command. The output displays the process name, and a report that contains the map is displayed like an associative array.
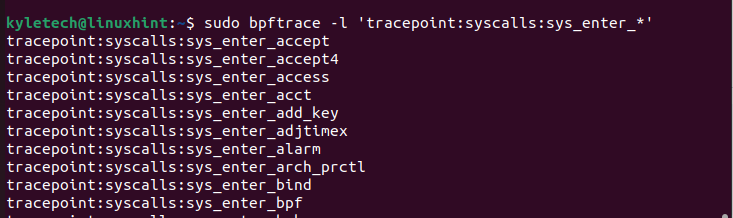
The count() populates the count of the frequency of times that the system calls for each process to happen. If you want to list all probes, you can use the bpftrace -l command to list them as illustrated in the following:
That’s how you work with the eBPF program on Linux.
Conclusion
eBPF is a way of inserting the code into the Linux kernel. You can use the frameworks like BCC and Bpftrace to create and run the eBPF programs. This post introduced eBPF and the framework for writing and running the eBPF programs. Moreover, we presented a few examples of the eBPF programs that you can run. That’s it!