Getting Started
Who would have thought generating a random number would be such a mess, it is supposed to be just as straight-forward as guessing a number anywhere between a given range. But it is not as simple as it seems and also till now all the machines are proven to be unable to generate a true random number on its own.
Why machines can not generate true random number on its own?
Machines yet are just instructed sets of mechanisms and circuits, and hence they can not be instructed to think of a random number on its own without any help. And that’s why till now and further, we have been involving nature or humans with machines to generate a true random number. We will not discuss here how to generate a true random number but we will discuss about the already implemented random number generators and their working and weaknesses.
Why is generating a true random number is so important?
The question arises that why are generation of true random numbers important and the answer to that is because of security concerns. Most cryptographic algorithms are based upon the generation of random numbers as these random numbers are used to create cryptographic keys and if the random numbers generated are not truly random in nature, these make whole of those cryptographic techniques weaker and those keys can be predicted relatively easier using the algorithm that was used to generate those random keys. This is the most important reason for a true random numbers, other than applications like gambling.
Random Number Generator in Linux Kernels:
The topic for our discussion today is based upon Linux Random Number Generator, on what factors is this generator based on and is it really that random or is it just another typically unreliable random number.
Linux uses Pseudo Random Number Generator (PRNG) or Cryptographically Secure Pseudo Random Number Generator (CSPRNG) which means it uses complex mathematical formulas and environmental properties to achieve maximum randomness. Linux was the first OS to include PRNG in its kernel space. This was implemented by Theodore Ts’o in 1994.
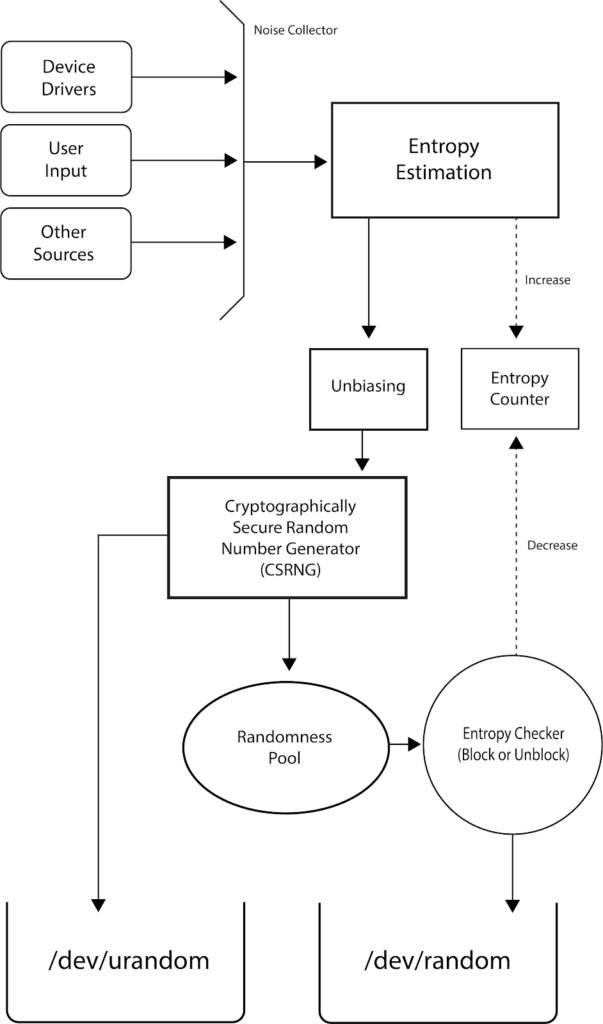
Linux has three categories of random number generators, /dev/random, /dev/urandom, /dev/arandom. These all three are the files in which Linux stores random numbers. The random numbers in these files are generated using the environmental noise from the device drivers and other sources. Also, to ensure randomness in its random numbers, linux uses entropy which is the extent of uncertainty or disorder between them. You can also find the manual page for Linux Random Number Generator (RNG) here:
http://man7.org/linux/man-pages/man4/random.4.html
/dev/random versus /dev/urandom versus /dev/arandom:
The main differences between /dev/random, /dev/urandom and /dev/arandom is that /dev/random blocks if the entropy is not indicating sufficient randomness, /dev/urandom does not block ever, even when the pseudo random number generator is not fully seeded when booted and lastly /dev/arandom blocks only when pseudo random number generator is not yet fully seeded. In short, /dev/random is the safest of all, then comes /dev/arandom and the least safest is /dev/urandom. Normally /dev/random and /dev/urandom are used because /dev/arandom in many terms is similar to /dev/urandom. The entropy estimation for the random number pool in short is used to determine the randomness of numbers generated. The more entropy is, the more randomness is achieved and better it is. The current amount of entropy and size of its entropy pool are available at /proc/sys/kernel/random/ named as entropy_avail and pool_size, respectively, which can be displayed in terminal by using commands:
And:
Both urandom and random are used in different scenarios. ‘Urandom’ is used where there is constant need of random numbers and its randomness is not much important while ‘random’ is used where there is a security concern and its randomness should be reliable as it blocks outputting random numbers if entropy is not up to the mark. Although entropy for urandom(Unlimited Random) is not much weaker but it is recommended to use random when more security is required because of the possibility of attacks on number generated by urandom.
Weaknesses in Linux Random Number Generators
For Non-volatile Memory Hardware:
For Linux kernels, the random number generator is not good for embedded hardware such as routers, in which bootable state is predictable and the source for enough entropy are limited. For this kind of hardware, it is recommended to save and use Random Number Generator (RNG) state before shutdown which will be used on the next boot. In such cases of routers, the attackers can only compromise and predict the generated random numbers if they have access to all the router links and they are eavesdropping on its communication links or if they have directly accessed the saved RNG state from the router itself.
For this flaw of RNG in case of hardware, third party entropy generators comes to the rescue. These entropy generators such as ‘haveged’ uses processor cache timing, external audio and video input devices to increase the entropy to an acceptable degree.
Entropy Estimation:
As mentioned before the Linux kernel determines randomness in terms of entropy but it does not actually calculate entropy each time and instead uses entropy estimations. Several researches have also revealed that the entropy estimation of random numbers used in Linux are not suitable or closer estimations, thus making the overall randomness of the numbers weaker.
Although there are some weaknesses in Linux Random Number Generator, but it is far better option compared to other RNGs, not to forget the ongoing patches that are provided by Linux contributors and developers.
Concluding:
This was all from my side about the Random Number Generator in Linux kernel. I had a good time in spreading this knowledge with you. Hope you learned something new through it and also that you will share the knowledge further to the world. Lastly, thanks for investing time in this article.