An access violation happens when the CPU tries to the instruction set outside of its memory area or reads or writes to a reserved location that does not exist, resulting in a segmentation fault. The present application is halted as a result of this action, and an outcome designated as Segmentation Fault is generated. Because data is frequently shared across memory regions on a system, and program storage space is shared among applications, this issue occurs.
Some machines may experience Segmentation Fault, while others do not. If that happens, it usually means you have an issue with your code, and we managed to get away with it on that system by luck. It all relies on how memory is organized and whether or not it is zeroed. We’ll examine how to identify the program’s segmentation problem in this article.
What is the Segmentation Fault?
A segmentation fault, often known as a segfault, is a sort of computer error that happens when the processor attempts to access a memory address outside of its program storage region due to an unanticipated condition. The term “segmentation” refers to a virtual memory operating system’s memory protection method. When working with pointers in C++/C, we frequently run into this issue.
Using GDB Compiler for Segmentation Fault
To discover why the C programs create a segmentation fault, we’ll use GDB. The GDB is a C (and C++) debugger. It enables the program to run up to a specific point, then halts and reports the values of specified variables at that moment, or steps through the program one line at a time, printing the values of each variable after each line is executed. The GDB debugger will help us to figure out which lines are responsible for the segmentation issue.
Key Points to Prevent Segmentation Faults
While memory access failures cause the majority of segmentation faults, it’s critical to ensure that pointers used in a program always refer to acceptable data locations. The following are the ways to prevent segmentation faults.
- As memory access failures cause the majority of segmentation faults, it’s critical to ensure that application pointers always point to valid data locations.
- Before dereferencing a susceptive reference, such as one embedded in a struct that is kept in a list or an array, we should invoke Assert().
- Always remember to correctly initialize pointers.
- A mutex or a semaphore can be used to protect shared resources from concurrent access in multithreading.
- We should use the free() function
Example 1: Program of Segmentation Fault by Dereferencing Pointer from Memory Block in C
We have an illustration of a segmentation fault where we are trying to get access to the address of the pointer that has freed up. In the following C program main function, we have pointer variable declaration “int* a” and we have allocated the memory to the pointer variable “a”. A segmentation fault will be generated when the program tries to read from the dereferencing pointer *a.
int main(int argc, char **argv)
{
int* a ;
*a = 50;
return 0;
}
On the compilation of the above code seen on the screen below, the line *a=50 causes a segmentation fault.
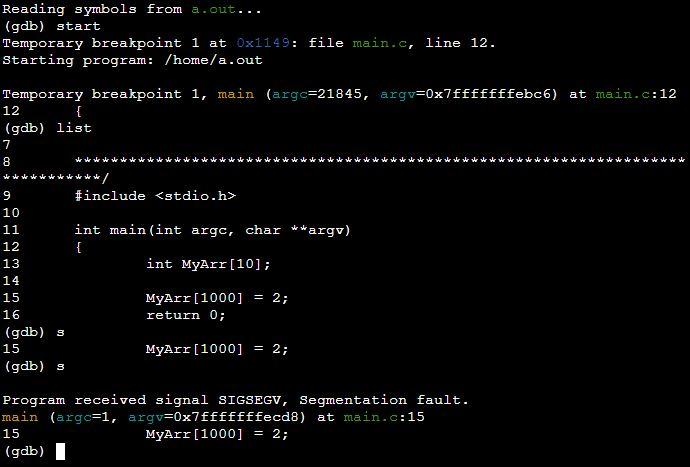
Example 2: Program of Segmentation Fault by Accessing Array Out of Bond in C
A segmentation fault occurs in most cases when a program tries to read or write memory beyond its bounds. In the following program, we have declared an array of index “10” Then, we are attempting to fetch the index of an array that is out of bound and initialized it with the numeric value. This is the point where we will get segmentation faults after executing the out-of-bound line of the program.
int main(int argc, char **argv)
{
int MyArr[10];
MyArr[1000] = 2;
return 0;
}
We are in the GDB compiler where we have used the GDB list command. The GDB list command has printed the line of code from the valve program. From the line “MyArr [1000] =2”, we have got a segmentation fault. You can see it in the following GDB console.
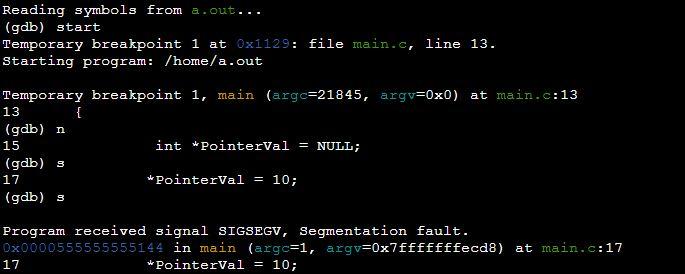
Example 3: Program of Segmentation Fault by Dereferencing Null Pointer in C
References are pointers in programming languages that indicate where an item is stored in memory. A null pointer is a pointer that points to no valid memory location. In the below program, we have declared a pointer variable “pointerVal” and assigned it a null value. The Null pointer exception is thrown or segmentation fault occurs when a null pointer is dereferencing at the line “*pointerVal=10”.
int main(int argc, char **argv)
{
int *PointerVal = NULL;
*PointerVal = 10;
return 0;
}
The outcome of the above program has thrown segmentation fault upon execution on line “*PointerVal= 10” shown below.
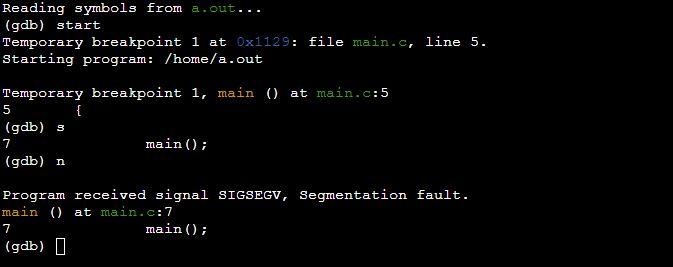
Example 4: Program of Segmentation Fault by Stack Overflow in C
Even if the code doesn’t have a single pointer, it isn’t a pointer issue. The stack overflow then occurs when the recursive function is invoked repeatedly, consuming all of the stack memory. Memory corruption can also happen when the stack runs out of space. It can be fixed by returning from the recursive function with a base condition.
Here in the program, we have the main function and in the body of the main function, we have invoked another main function. This leads to segmentation fault because of stack overflow.
int main(void)
{
main();
return 0;
}
You can see the GDB compiler gives the segmentation fault on line where we have invoked the main function in the program main function block.
Conclusion
The article shed some light on what is segmentation faults and how we can debug them by using the GDB compiler. The GDB compiler determines which lines are responsible for the segmentation failure. The debugging session of segmentation faults is very easy to handle with a GDB compiler in C programming. Then we have taken different scenarios where segmentation faults may occur. I hope this article clarified the segmentation fault problems.