AppArmor is a Linux software security mechanism that is very effective and user-friendly. AppArmor is a core improvement that restricts the programs to specific resources. It connects the access control properties to the programs instead of users. AppArmor secures the Linux operating system and apps from numerous attacks by implementing the security policies which is commonly referred to as an AppArmor profile. The AppArmor profile comprises simple text files. When defining the file access, both file globbing and absolute paths can be applied.
We have two functional modes of AppArmor enforce and complain. The AppArmor production status is in enforced mode by default, but the complain mode is beneficial for logging violations and defining a rule set based on actual operation patterns. In contrast, to being a component of the framework, AppArmor is an add-on feature that can be added, modified, disabled, or uninstalled. We will explore the implementation of AppArmor in this tutorial to get more details about it.
Installation of AppArmor in Debian
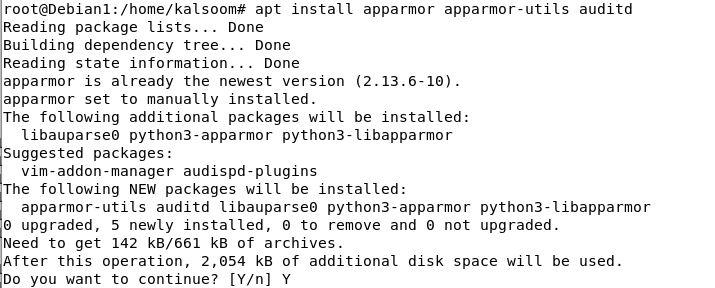
AppArmor is already set up and loaded in the Debian operating system. It leverages the profiles of the application which is required by the program to determine the files and permissions. Some utilities install their profiles, while the AppArmor-profiles package contains more profiles. The apt command is used to install the “audit” apparmor-utils in the Debian operating system which is shown in the following image. We can remove the “audit” utils from the command if we don’t require the tools to create the profiles. Note that we run this command as a root.
Enabling the AppArmor in Debian
Now, the AppArmor utility to generate a profile is installed. We enable the AppArmor Linux Security Modules from the Linux kernel command line. We follow the following given steps to enable the AppArmor in the Debian operating system:
Step 1: Create the directory.
Step 2: Generate the “ /etc/default/grub.d/apparmor.cfg” file and save the content that we echo in the following:
| sudo tee /etc/default/grub.d/apparmor.cfg
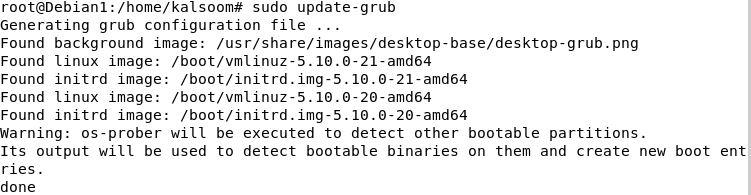
Step 3: Update the “grub” under the privilege of sudo command.
Step 4: Reboot the Debian operating system. Once the reboot is done, we can check if the status of AppArmor is enabled or not by executing the following command. It returns “Y” which indicates “Yes” because the AppArmor is enabled within the Debian system:
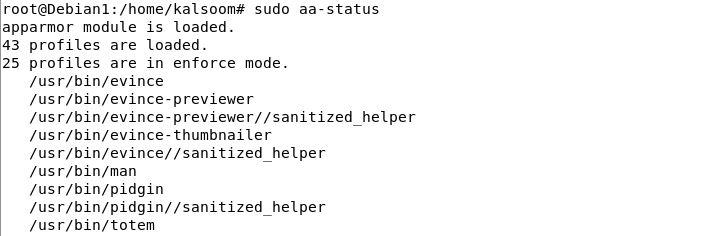
Step 5: Use the command to get the current status of each AppArmor profile that is loaded for applications and processes. We can see the mode compliance of each profile which is loaded in the following illustration. The output displays that “43” profiles are loaded as AppArmor profiles and the “25” profiles of AppArmor are in enforce mode by default. There exist two modes of the AppArmor profiles – some are in enforce mode and some are in complain mode. We can modify the execution mode for each profile that is defined.
Modifying the AppArmor Profile in Debian
As we mentioned earlier, the modes can be switched from the specified modes of the AppArmor profile. This means that the enforce mode can be changed with the complain mode and vice versa. We have an AppArmor profile as “dhclient” which is in an enforced mode. The complain mode can be accessed by running the following command. The output displays the message of setting the dhclient in complain mode:
To alter the complain mode in an enforce mode again, we have a command to achieve this. The command uses the “enforce” keyword with the dhclient profile.
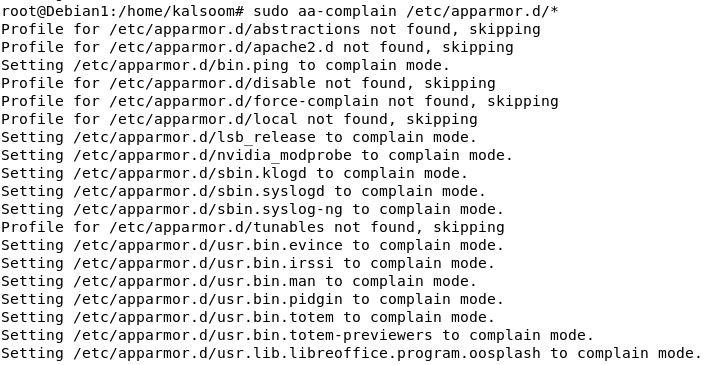
Furthermore, the execution mode configuration path is /etc/apparmor.d/* for all the AppArmor profiles. We can set the execution mode of all the AppArmor profiles in complain mode by applying the following sudo command in the terminal:
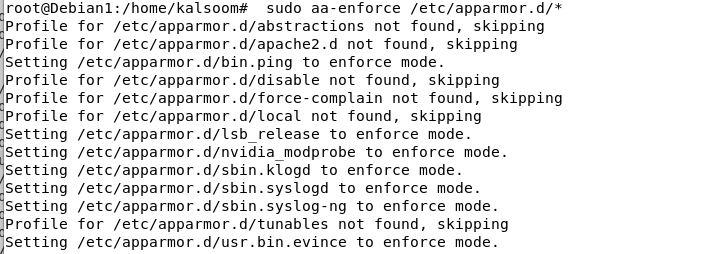
We can also set the path of the execution mode for all the profiles of AppArmor to the enforce mode using the following command:
Creating a New AppArmor Profile in Debian
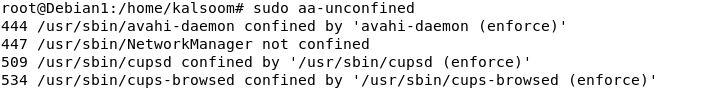
To establish a new profile, we must determine the applications that require security but are not affiliated with any other AppArmor profile. There are several commands to construct the AppArmor profiles. But we use the “aa-confined” command to list the profiles which are unconfined. The output indicates that one process is unconfined to any profiles, while the other three processes are confined by three profiles in enforced mode by default.
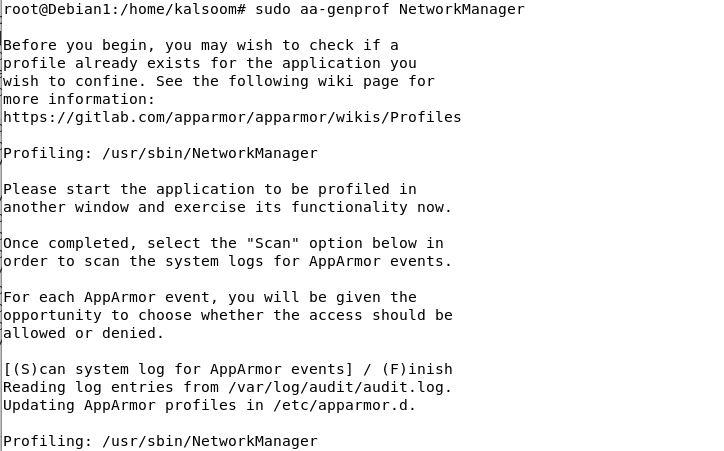
Now, we create the “NetworkManager” AppArmor profile which is not confined. For this, we utilize the “aa-genprof” command and specify the name of the unconfined profile with it. The generated profile is empty in the enforced mode by default. By pressing the “F”, the creation process of the profile is ended.
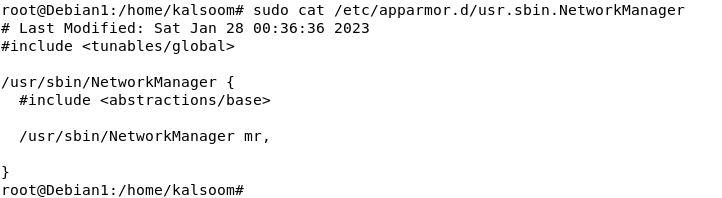
We can change their contents by modifying the following file as there are no such defined limitations for this profile which sets the constraints for the program. The “NetworkManager” profile is now updated as shown in the Debian terminal:
Reloading the AppArmor Profiles in Debian
The AppArmor profiles which we previously created and modified should be reloaded. To reload every active AppArmor profile, perform the following command:
Next, using the given command, the loaded profiles of AppArmor can be viewed. We can see that the created NetworkManager profile is mentioned in the output with the enforced mode.
Disabling the AppArmor in Debian
The AppArmor application is not allowed to be disabled because it is a security feature. If we disable or remove the AppArmor from our system, we have to follow these commands. First, we stop the AppArmor services using the systemctl:
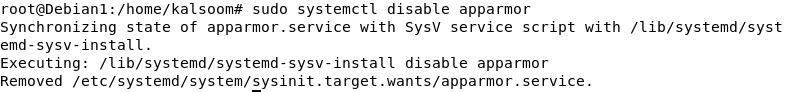
After that, we use another command which disables the AppArmor from running when the system boots:
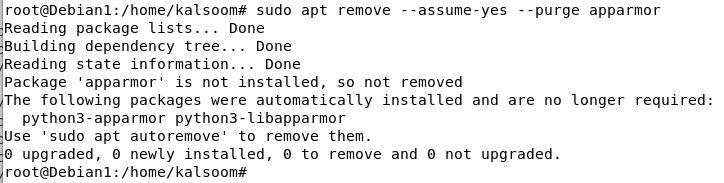
The next executed command uses the apt to remove the AppArmor package and dependencies from the system.
Conclusion
In this Debian AppArmor article, we explored the ways to work with the AppArmor profiles. We learned the installation command for the AppArmor profiles. After the installation, we enabled the AppArmor within the Debian system. Then, we modified the modes of existing profiles of the AppArmor. We also generated a new profile that is not confined to the AppArmor profiles. The AppArmor can also be disabled or removed from the system using the specific disabling commands which are executed in the last part of this tutorial.