A Virtual Private Network (VPN) is one way of masking your identity and location over the internet. Also, if you are trying to connect to your workplace or home device remotely, a VPN comes in handy to route your traffic. You have the option to purchase VPNs from trusted sources or even create your own over SSH.
Outsourcing VPNs pose different security risks. However, you can create a VPN connection from a host machine and connect to a remote device via SSH with the sshuttle Linux command. You must have Python installed on the host machine and be connected as root for this to work. As for the remote machine, it doesn’t need to be root. Provided you have its password, sshuttle will work fine.
Moreover, once the connection gets established, sshuttle will upload the Python source code to the remote machine, eliminating the hassle of you having to install Python on it.
How To Install sshuttle
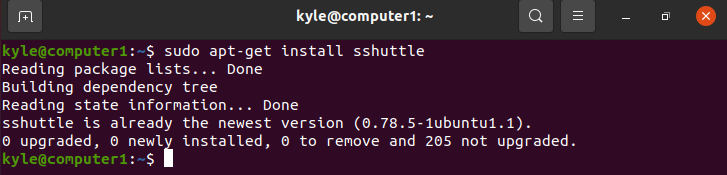
Installing sshuttle is straightforward. If you are on Debian or Ubuntu, use the following command to install it from the package manager:
1 | $ sudo apt-get install sshuttle |
Use the following command if you use Fedora, RHEL, or CentOS. Alternatively, you can clone its git repository and run the setup file.
1 2 3 4 5 | $ sudo dnf install sshuttle or $ git clone https://github.com/sshuttle/sshuttle.git |
Using sshuttle To Set Up a VPN
First, you must install sshuttle on the host machine to create a VPN connection. In addition, you need the hostname and the IP address of the remote device.
There are different ways to use sshuttle.
-
Proxying All Local Connections
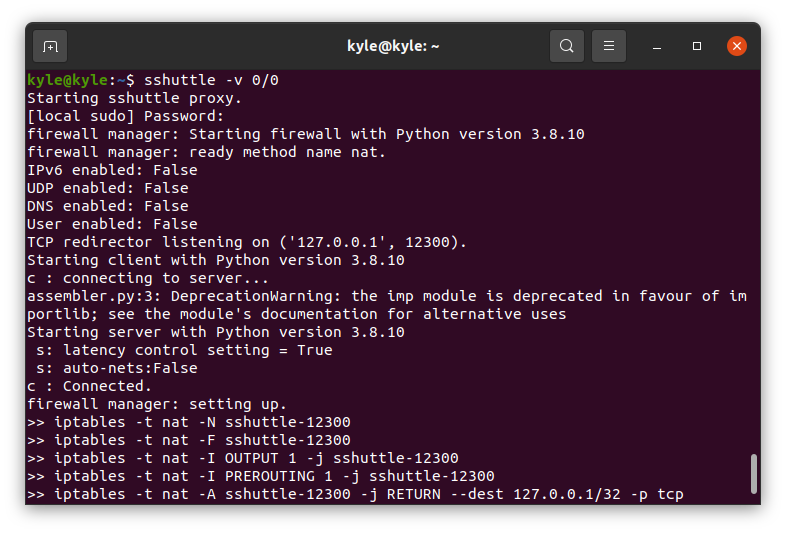
The best way to test sshuttle is by proxying all local connections without involving SSH. The command for this is:
1 | $ sshuttle -v 0/0 |
-
Testing Connection to the Remote Server
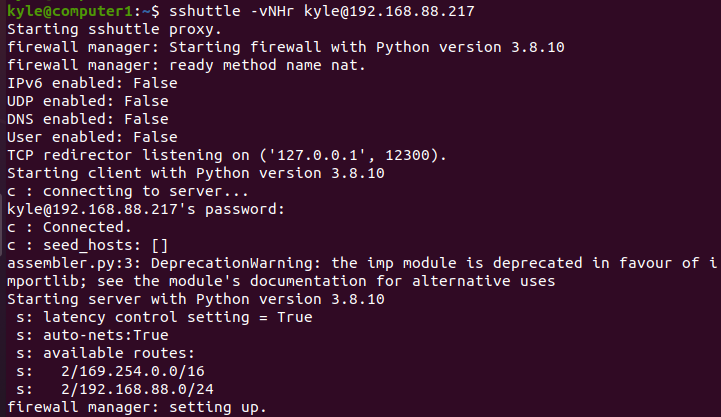
It’s possible to test your connection to the remote machine using sshuttle. We use the “-N” option to allow the server to decide the route and “-H” for auto-hosts. Our command will be:
1 | $ sshuttle -vNHr kyle@192.168.88.217 |
The IP is the remote machine we are testing.
-
Tunnelling All Traffic
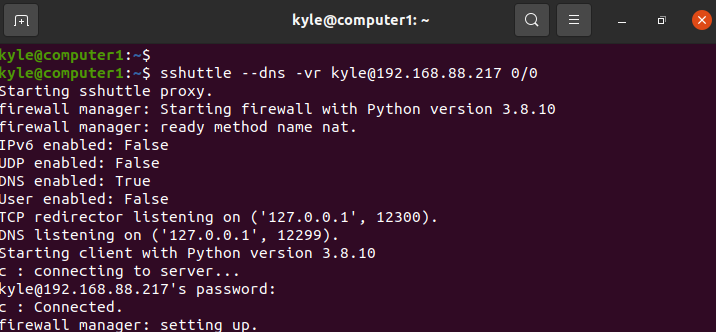
You can use sshuttle to tunnel all traffic to a remote SSH server. Note that sshuttle only forwards DNS requests and TCP traffic to the remote server. Other protocols, like UDP, are not supported.
1 | $ sshuttle --dns -vr kyle@192.168.88.217 0/0 |
The 0/0 is a shorthand for the DNS server 0.0.0.0, “kyle” is the username of the remote server, and 192.168.88.217 is its IP. Also, the connection should indicate it is “connected” to show that the created VPN is working.
-
Excluding Specific Traffic
The “-x” option excludes certain traffic when using sshuttle. Specify the IP address to be excluded in the tunneling. For instance, to exclude “192.168.88. 21”, the command will be as shown below:
1 | $ sshuttle --dns -vr kyle@192.168.88.217 -x 192.168.88.21 |
-
Tunnelling Specific Subnets
Similar to excluding specific traffic, you can choose which subnets to route over the created VPN. You can specify the IP address or the ranges for the subnets. For instance, to specify a given IP and a subnet range, the command will be:
1 | $ sudo sshuttle -r user@remote_host 192.168.88.2/24 192.168.0.0/16 |
The only traffic that will be tunneled is for the specified IP subnets, Class B and C. Specifying the subnets to tunnel works best when dealing with many hosts in an extensive network as not all connections require the VPN. You can also add the “–dns” option to forward DNS queries to the server.
Conclusion
There is a risk in purchasing or using publicly available VPNs to tunnel your connections. When working with servers and remote machines, you may need to route your traffic and keep it safe using a VPN. This guide covered how to install the sshuttle Linux tool, which enables you to create a VPN over an SSH connection. With sshuttle, you need not worry about VPN anymore. It will give you the protection you need for your traffic when using Linux systems.