AWS is an online computing platform. Hence, it is only natural that security becomes one of the major concerns of developers and IT Experts. Catering to this need of its users, AWS has eliminated the traditional practices of hard-coding the values within the code by introducing the “AWS Secret Manager”.
Quick Outline
This article presents information on the following aspects:
- What is AWS Secret Manager?
- How to Create And Modify a Secret in AWS Secret Manager Using CLI?
- Conclusion
What is AWS Secret Manager?
AWS Secret Manager shines in its ability to protect and secure the sensitive information of resources such as OAuth tokens, Database credentials, API keys, etc. Such confidential information is stored in the encrypted form known as “secrets”. Secret Manager ensures that all the confidential information of the user is encrypted and only accessed by authorized bodies. These secrets can be accessed and modified by using AWS Console or CLI.
How to Create And Modify a Secret in AWS Secret Manager Using CLI?
AWS Secret Manager allows users to control the authentication and access management. Aside from storing and retrieving the secrets, users can schedule the rotation of the secrets that replace long-term secrets with short-term ones. This leads to the improved security posture of the application and prevents the possible compromise of functionality by anyone.
Amazon Web Service is a well-architected and secure platform that strives to provide the best facilities and resources to its users. In this blog, we will learn about the implementation of the following methods with secrets using AWS CLI:
- Method 1: Create a Secret
- Method 2: Update the Value of the Secret
- Method 3: Edit Description
- Method 4: Change Encryption Key
- Method 5: Delete a Secret
- Method 6: Restore Secret
- Method 7: Tag a Secret
- Method 8: Filter the Secret
- Method 9: Replicate a Secret
Learn more about Modifying the Secret using AWS Console by referring to this article: “How to Modify Secrets With AWS Secret Manager Using AWS Console”.
Method 1: Create a Secret in IAM Using AWS CLI
To create a secret in AWS Secret Manager, log into the AWS account using the following command:
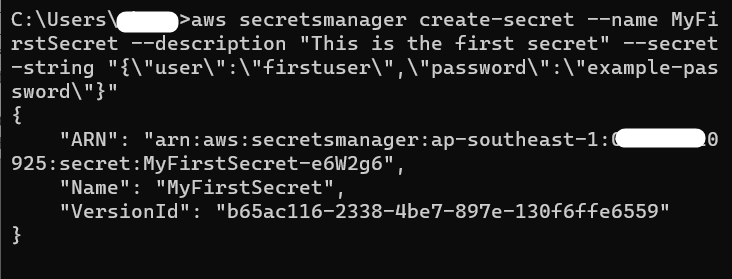
Next, provide the following command and hit the “Enter” button from the keyboard:
–name: is used to input the name for the secret.
–description: provide a short description about the secret.
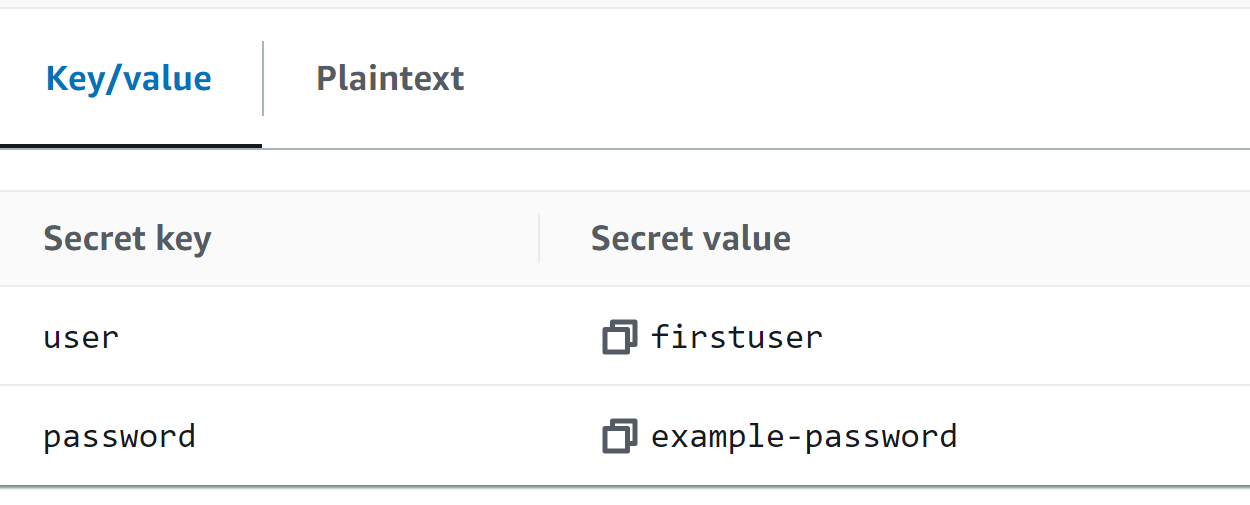
–secret-string: is used for specifying the key-value pairs. In the above-mentioned command, “user” and “password” are the two keys. Similarly, “firstuser” and “example-password” are the two values for the keys:
To learn about creating a secret in AWS Secret Console, refer to this article: “How to Store Amazon RDS Credentials Using Secrets Manager?”
Output
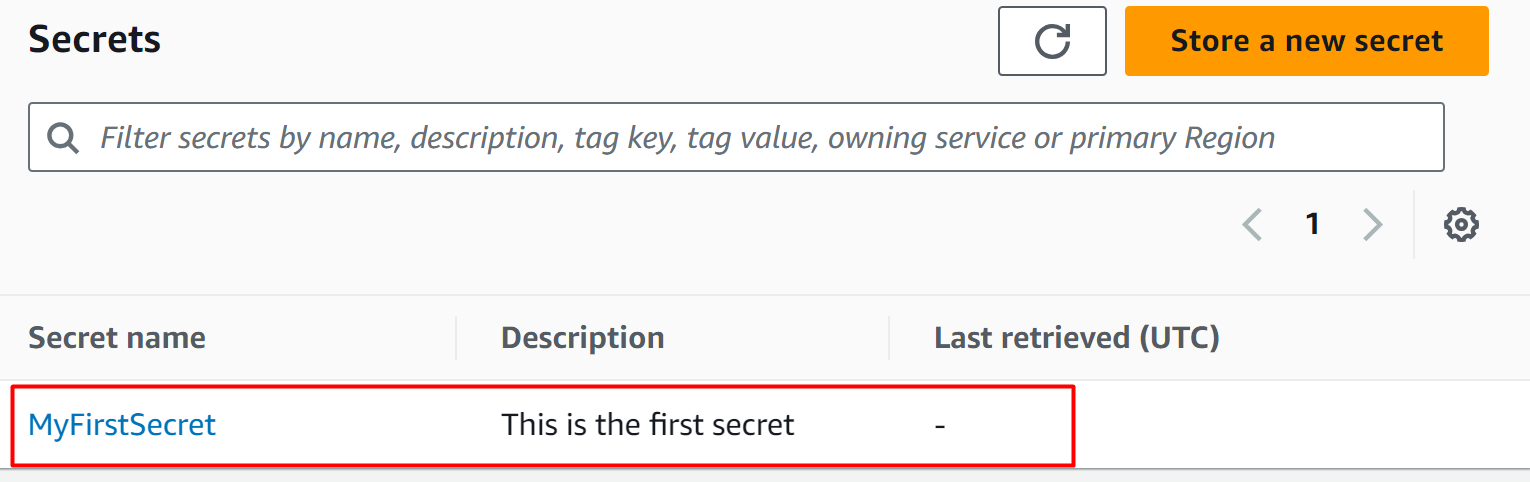
However, the output can also be verified from the Secret’s Manager Dashboard where the secret is created by CLI :
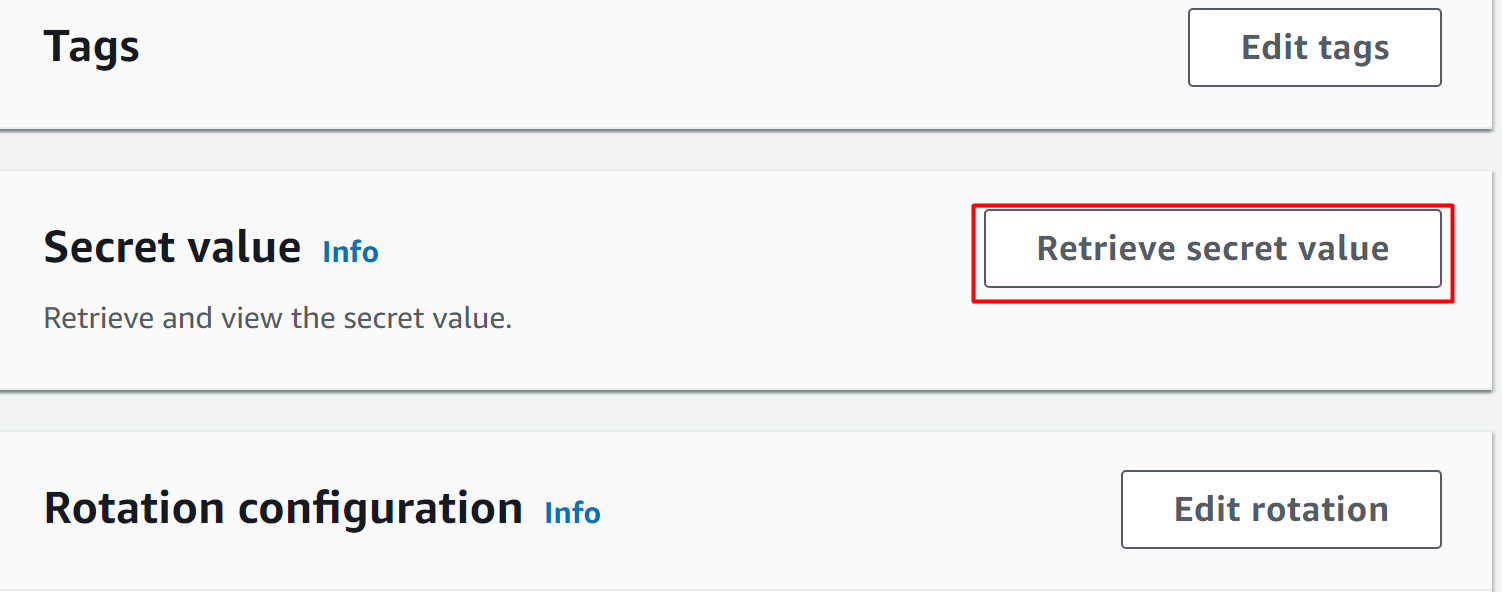
Click on the Secret’s name. Scroll down the next interface to the “Secret value” section. Tap the “Retrieve secret value” button to view the key-value pairs:
The key-value pairs displayed are the same as that we have provided in the above-mentioned command:
Method 2: Update the Value of the Secret
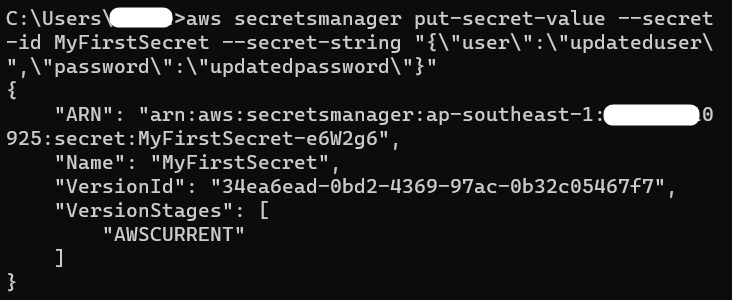
To update the values of the keys in a secret, provide the following command. The “–secret-string” in the command contains the updated value for the “user” and “password” keys.:
Output
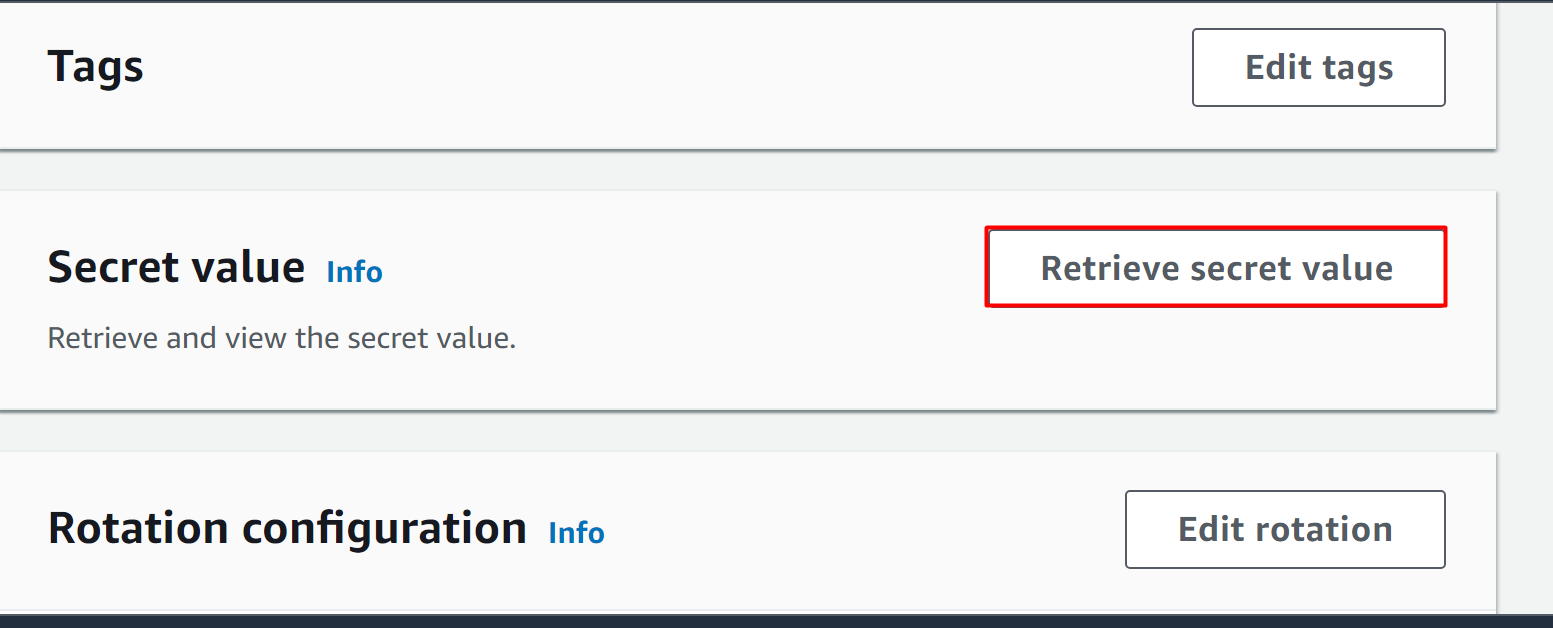
By visiting the Secret’s Manager Dashboard, tap the name of the secret to view the specifications. In the “Secret value” section on displayed interface, tap the “Retrieve secret value” button:
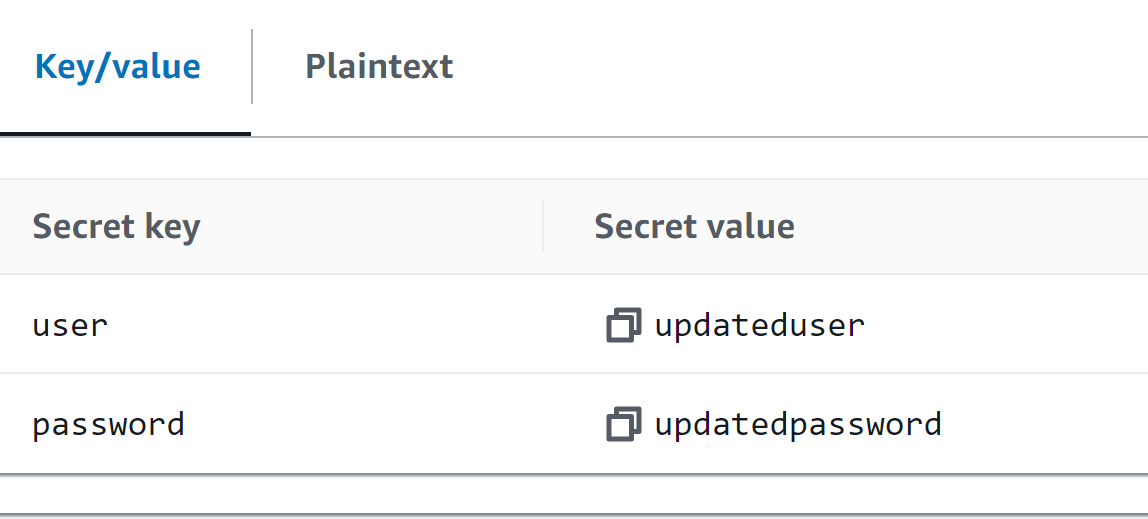
This will display the key-value pairs. From here, the values for the keys are successfully updated:
Method 3: Update the Description of the Secret
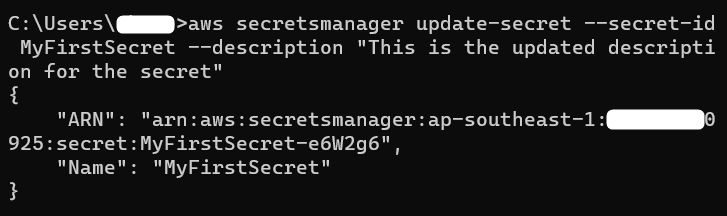
Apart from the values, we can also edit the description of the Secret. For this purpose, provide the following command to CLI:
Output
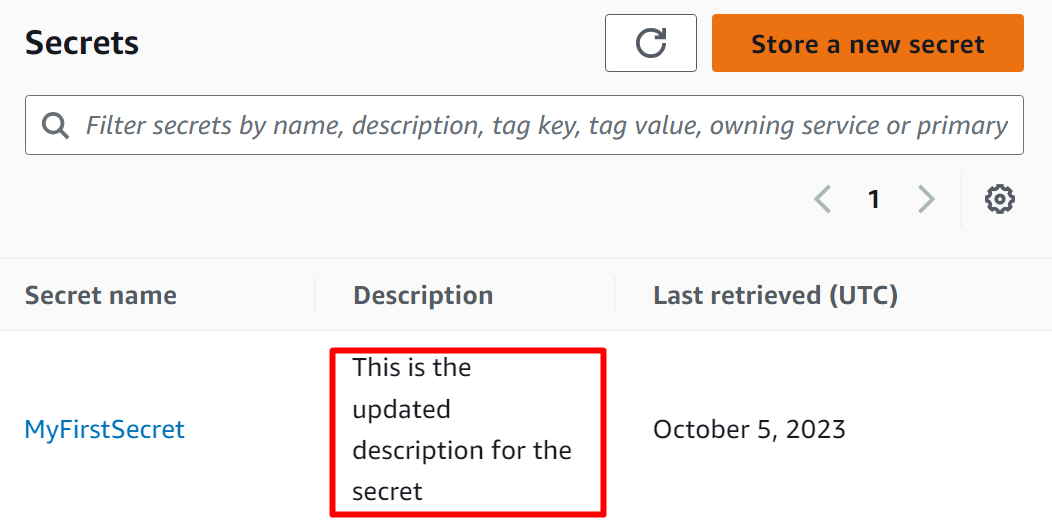
For verification, visit the Secret’s Manager Dashboard. On the dashboard, the secret description is provided:
Method 4: Change Encryption Key
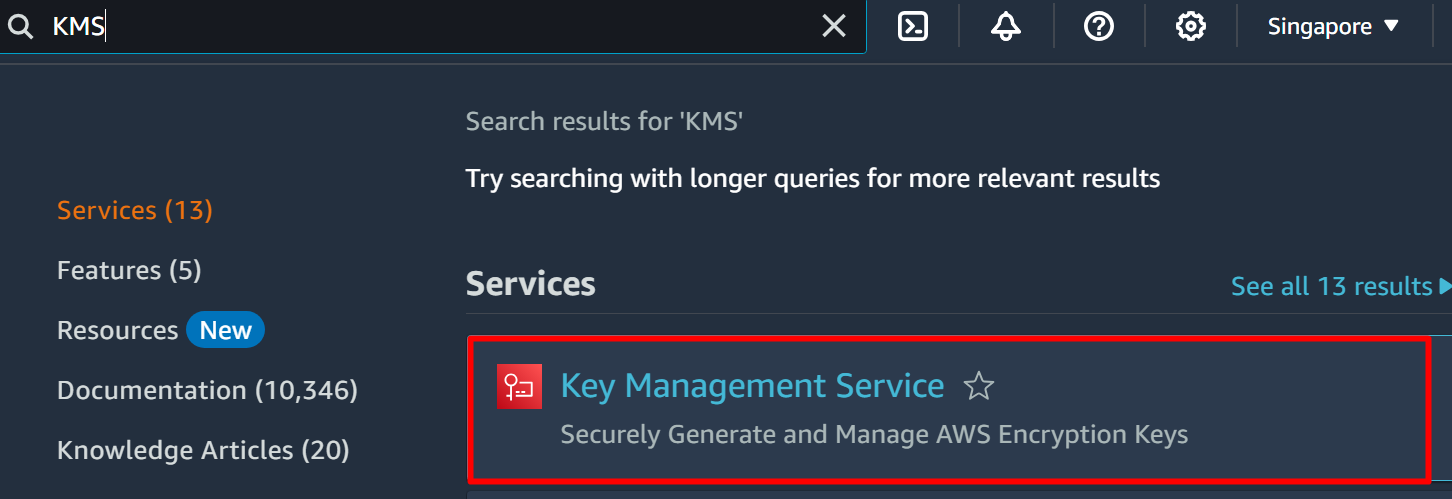
One of the other modifications that a user can perform with the AWS Secret Manager is to “Change the Encryption Key” of the secret. For this purpose, search and select the “KMS” service from AWS Management Console:
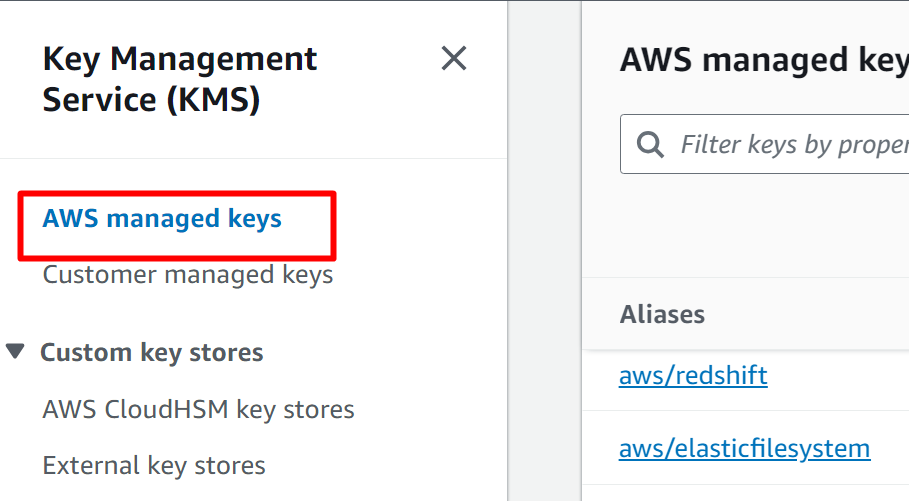
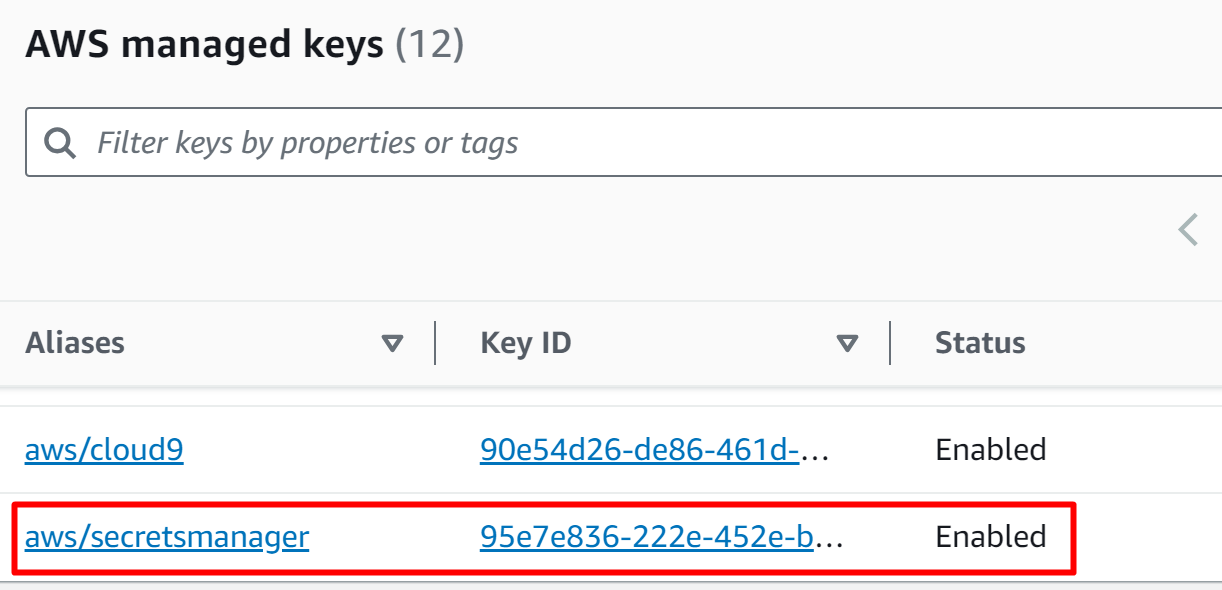
AWS will provide a default key for the encryption when creating a secret. Users can also select a “Customer managed key” but the recommended practice is to use the default key provided. As the default key is being used for this demo, therefore, click on the “AWS managed keys” option from the left sidebar of KMS:
Scroll down the AWS managed keys interface and locate the “aws/secretmanager” key. This key is associated with the secret created earlier. Click on the key’s name to view the configurations:
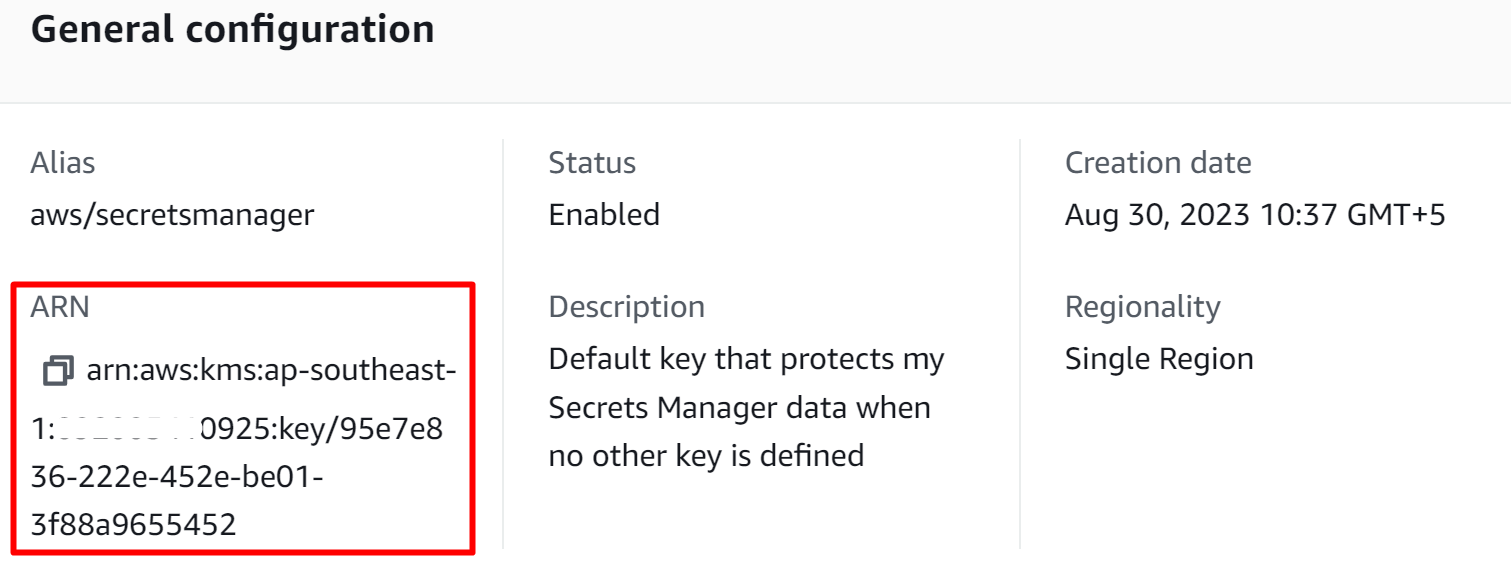
From the General configuration’s interface, copy the “ARN” as it is required for identifying the secret and changing the encryption key:
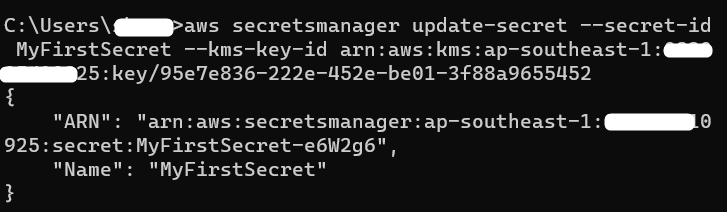
Coming back to the CLI, provide the following command with the copied ARN:
–kms-key-id: provide the copied ARN for changing the encryption key of the secret.
–secret-id: Provide the name of the secret for which the key is to be changed:
Method 5: Delete a Secret
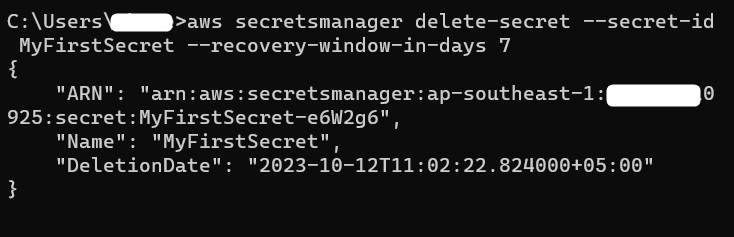
A user can also delete the secret by using the command-line interface. Before a secret is deleted, it is scheduled for a minimum of 7 days to a maximum of 30 days. The following command is used for deleting a secret from the Secret Manager Dashboard:
–secret-id: provide the name of the secret which is to be deleted.
–recovery-window-in-days: refers to deletion schedule. The secret will be deleted after the specified time in the “recovery window”. The secret will be permanently deleted and cannot be restored.
Output
For verification, visit the Secret Manager Dashboard and click on the “Reload” button. An interface similar to the attached image will be displayed:
Method 6: Restore a Secret
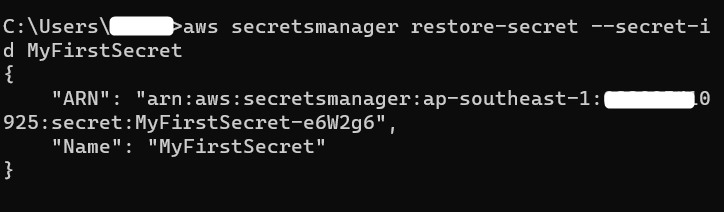
With AWS Secret Manager, we can also restore the secret that is accidentally deleted. On the command-line interface, provide the following command:
–secret-id: provide the name of the secret which is to be restored.
Output
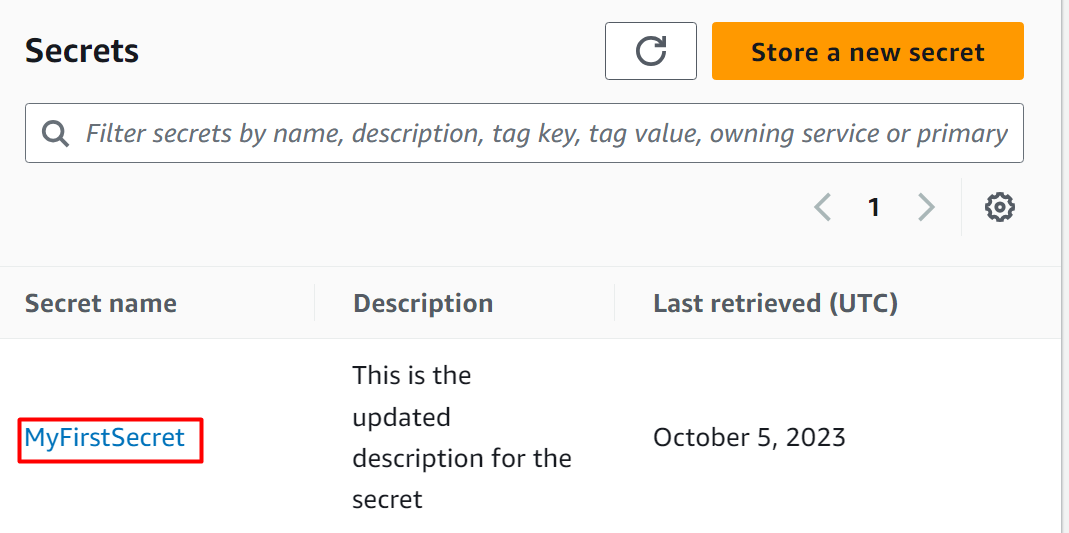
On the Secret Manager Dashboard, the specified secret has been successfully restored:
Method 7: Tag a Secret
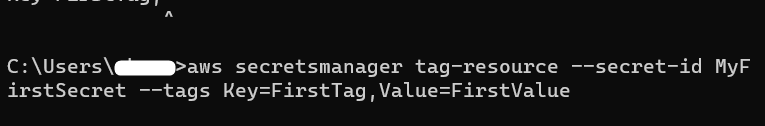
Tags are an efficient way to manage the resources. Users can add 50 tags to a secret. For tagging a secret, provide the following command to AWS CLI:
–secret-id: refers to the name of the secret for which the tags are to be added.
–tags: Tags are the combination of the keys and values. Using the keyword “–tags”, specify the key and value pairs.
Output
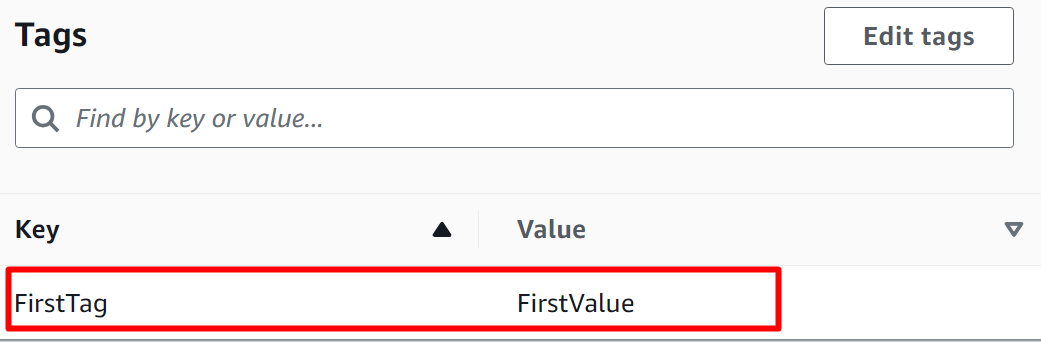
For verification, choose the secret from the Secret Manager Dashboard. Scroll down to the “Tags” section to view the added tag:
Method 8: Filter a Secret
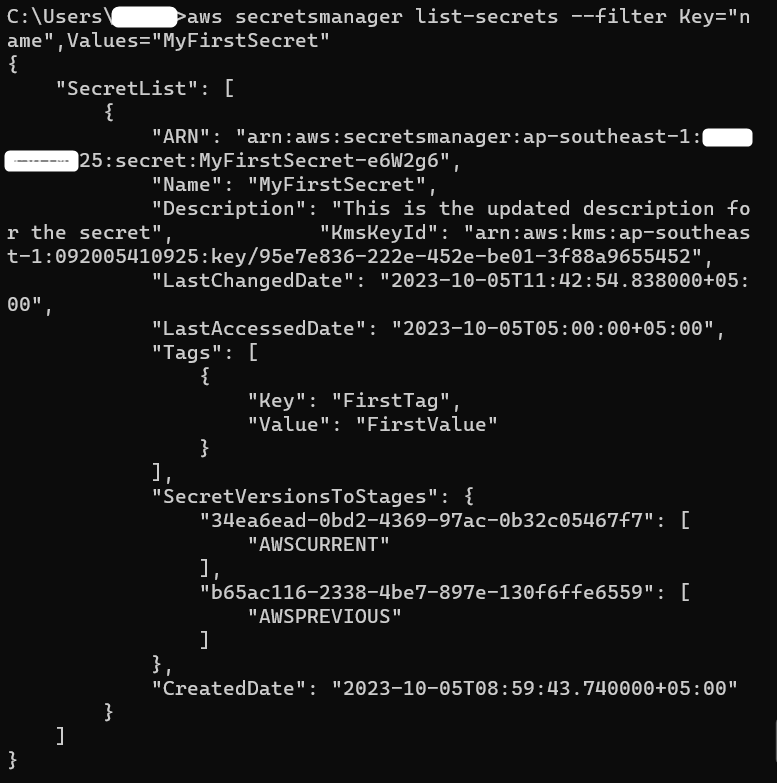
AWS allows users to search the stored secrets by using the “Filter” keyword. User can filter secrets based on their tags, name, description, etc. For filtering the secrets, use the following command:
Key: specify the field by which the secrets should be filtered.
Values: provide the name of the secret to uniquely identify the secret
By executing the above-mentioned command, the Secret Manager will display the key’s information:
Method 9: Replicate a Secret
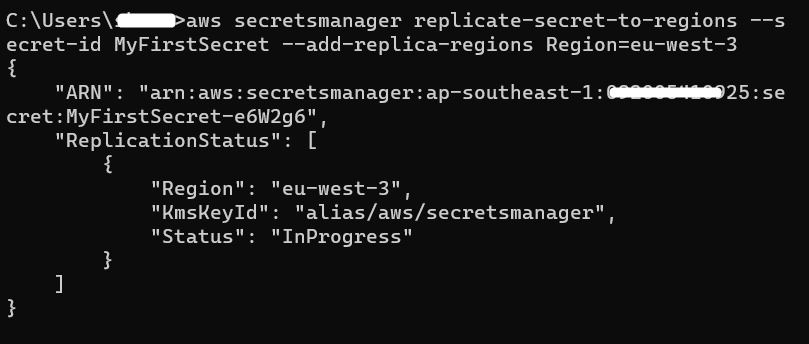
Secret Manager also enables its users to replicate their secrets in other regions of AWS. For deleting the secret, it is important to first delete the replica of the secret. To configure the replica of a secret in a different AWS Region, use the below-mentioned command:
Region: refers to the area of AWS where the secret has to be replicated.
Learn more about replicating a Secret in AWS Secret Manager by referring to this article: “How to Replicate a Secret to Other Regions in AWS Secret Manager?”.
Output
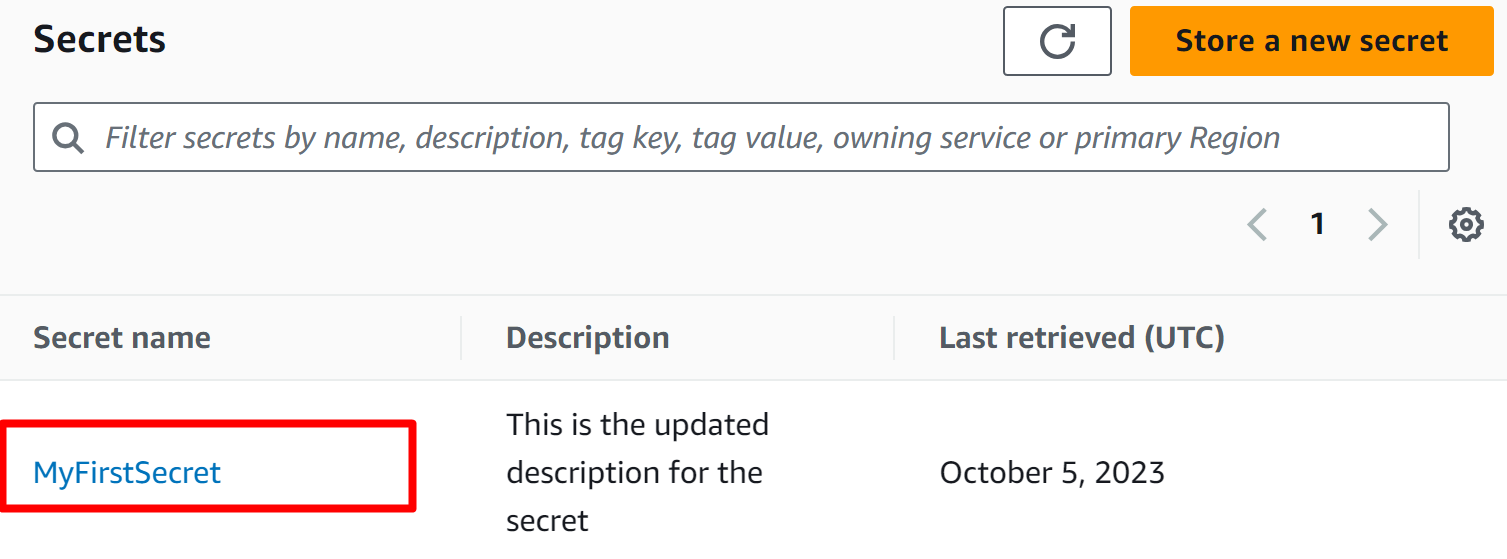
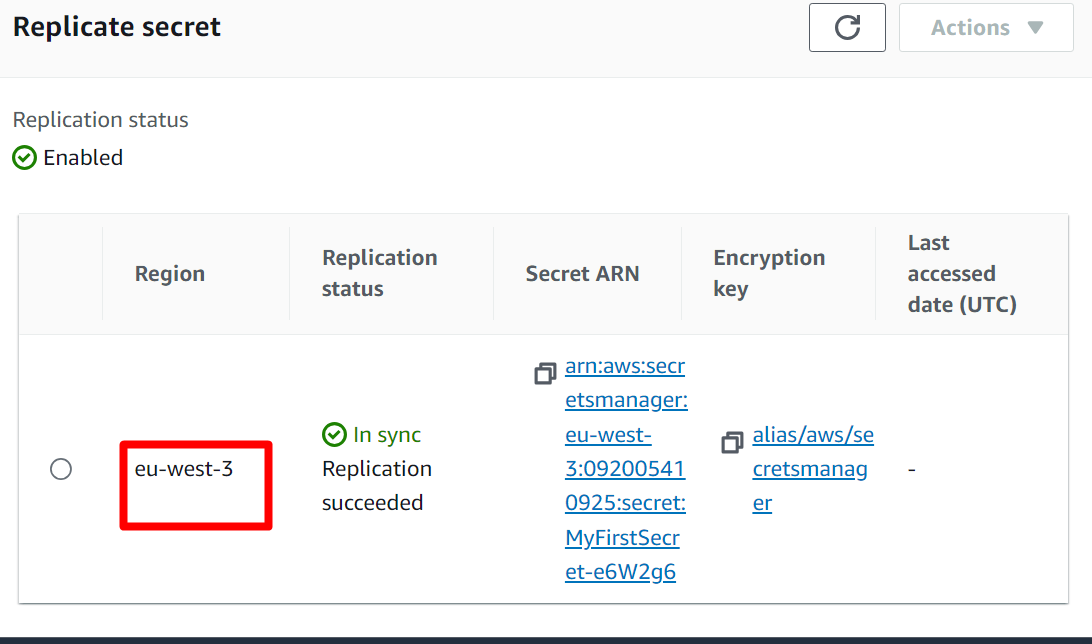
To verify if the secret has been replicated successfully or not, visit the Secret Manager Dashboard and choose the secret:
Scroll down to the Replicate secret section. The replication has been enabled successfully:
That is all from this guide.
Conclusion
To create and modify the secret using CLI, enter the mentioned commands and specify the action, secret ID, and key-value pairs to uniquely identify the secret. By using these commands, the users can execute all the operations of secrets that were performed using the AWS Console such as deleting, updating, creating, replicating, or restoring, etc. This article is a complete tutorial with a step-by-step description of how to create and modify a Secret in AWS Secret Manager using CLI.