To understand our topic in a much better way, we first need to discuss what SSH keys are. An SSH key, also known as a Secure Shell key, is a network protocol access credential for SSH. It is authentic and encrypted which provides an extremely secure protocol. It is used to make the different machines communicate with each other on an unsecured open network. Due to its authentication, it makes the communication encrypted and secure. This protocol is used for the remote transfer of files and access the operating systems remotely.
To find the SSH key, we have to open the terminal on our device and type the “ls -al ~/.ssh” command. This command tells us whether the existing SSH keys are present there or not. In the same way, we can use a command while working with the SSH keys. The command is called the ssh-copy-id command. This command helps us in the installation of the SSH keys on a remote machine or the server’s authorized keys. It helps us with SSH key login, thus removing the need of entering the login ID and password every time. The SSH command is a subpart of the OpenSSH tool which is used to perform the administration services on remote devices with the help of encrypted connections.
Copying the SSH Key
It’s essential to keep in mind that the SSH keys are comprised of a public key and a private key before you begin. The public key is shared with the remote server and is used to encrypt the connection while the private key is kept on your local machine and is used to decrypt the connection.
To copy an SSH key in Ubuntu, you need to have an existing SSH key pair. If you don’t have one, you can generate one with the ssh-keygen command. Now, using the SSH keygen command, we create a key pair using the -t option to specify the type of key to generate (e.g. rsa, dsa, etc.).
Press “Enter” to execute the command. After specifying the file location and name, it gets a passphrase from you. To safeguard your private key, you can use a passphrase as an additional security step. If you enter a passphrase, you will be prompted for it whenever you use the key to connect to a remote server. It is important to use a strong passphrase that is difficult to guess. You can enter any phrase according to your desire. In our case, we keep it empty. For that, we enter “empty” into it. After entering those details, we get the following displayed output:
Enter file in which to save the key (/home/linux/.ssh/id_rsa): /home/linux/key.txt
/home/linux/key.txt already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Passphrases do not match. Try again.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/linux/key.txt
Your public key has been saved in /home/linux/key.txt.pub
The key fingerprint is:
SHA256:zCpQ+8kEraxbmY90qq9m3JNNt+CEw905MfvSuJbyrps linux@linux-VirtualBox
The key's randomart image is:
+---[RSA 3072]----+
| |
| . |
| o . |
| o + oo |
| ..+o..S= |
| o+*=o* |
| ...*B*o B |
| +++*+.* o |
| o+++.EB+o |
+----[SHA256]-----+
The ssh-keygen command generates two files: a private key file (with a .pem or .ppk extension) and a public key file (with a .pub extension). It can be seen in the following snippet files named “key” along with its extension which is saved in the home directory.
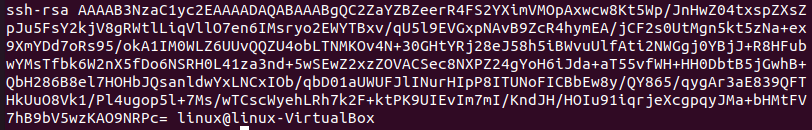
Once the pair of keys are created, you can use the cat command to see what the public key contains. The home folder contains the public key which has the “key.pub” filename. To view the contents of the public key, enter the following command:
The public key file’s contents should be copied to your clipboard. You can do this by highlighting the contents of the file and pressing the Ctrl+C keys, or by right-clicking on the terminal window and selecting the “Copy” option.
Connect to the remote server where you want to copy your key to using the SSH command by specifying the username and hostname of the server. For example:
You can also manually log in to the remote server. It should be made sure that you use the same user. Open the authorized keys file on the remote server after establishing a connection. This file is in the ~/.ssh directory on the server.
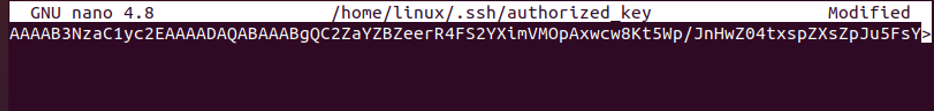
Paste the contents of your clipboard into the authorized_keys file by pressing the Ctrl+V keys. Make sure that the key is on a single line and that there are no extra spaces or line breaks.
As we can see in the previous snippet, we did not add the extra spaces in the file because it gives an error message while authorizing. Save the authorized_keys file by pressing the Ctrl+X keys. Then, press the Y key and then the Enter key.
The /.ssh directory and the /.ssh/authorized_keys file need to have the proper permissions set after the public key is copied to the server to make sure that only the authorized users can access them. This command sets the permissions on the ~/.ssh/authorized_keys file so that only the owner (user) has read and written the permissions.
It is essential to note that the permissions on the ~/.ssh directory should be set to 700 and the permissions on the ~/.ssh/authorized_keys file should be set to 600 to ensure that the private key remains secure. For that, we run the command that is displayed in the following:
kalsoom@linux-VirtualBox:~$ chmod 600 ~/.ssh/authorized_keys
The chmod command is used to change the permissions on a file or directory in Linux. These commands change the permission of the files and folder in the specific directory and authorized_keys, respectively, and make sure that only the owner has access to the files.
Make another attempt to connect through SSH to the server by providing the username and hostname of the server:
If you set a passphrase while creating the SSH key, it is prompted for it. If everything is configured properly, you should be able to connect to the server.
Conclusion
We learned how to copy an SSH key in Ubuntu. This process is useful when you want to set up the passwordless login to a remote server, or when you want to share your SSH key with a friend or colleague. Remember that there are numerous variations of this procedure depending on the demands of your scenario.